Threat Actor ID
| Country | Vietnam |
| Sponsor | State-sponsored1 |
| First Seen | 2014 |
| Motivation | Information theft and espionage |
| Methods | Watering Hole, Malware, Spearphishing |
| Other Names | APT32 (Mandiant)Ocean Lotus (SkyEye Labs) Ocean Buffalo (Crowd Strike) Tin Woodlawn (SecureWorks) |
Group’s Mission and Vision
The Ocean Lotus APT group is a hacker group operating against both private and government organizations and their opponents since 2014. The primary motivation behind the attacks carried out by the Ocean Lotus group is information theft and espionage – given the private information sought to be obtained in the attacks and the high-profile individuals targeted.
The targets of the Ocean Lotus group are generally foreign companies with sure success and interests in Vietnam’s hospitality, manufacturing, and consumer goods sectors. As well as the private sector, the Ocean Lotus group targets politicians and journalists opposed to the Vietnamese government.
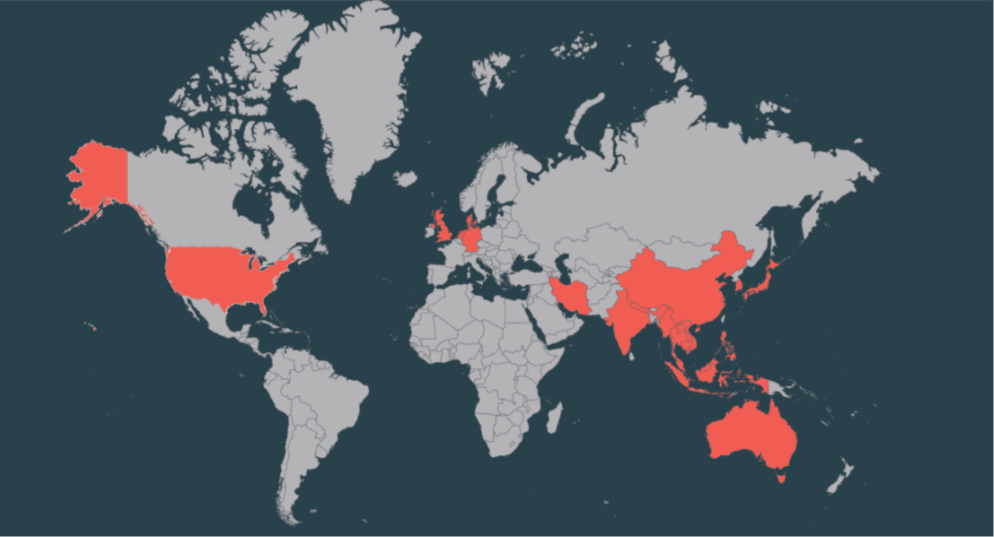
Targeted Countries & Industries
The cyberespionage group Ocean Lotus, active since 2014, targets organizations in various industries in Vietnam and other Southeast Asian countries.
- Indonesia,
- Iran,
- Japan,
- Laos,
- Malaysia,
- Myanmar,
- Nepal,
- Netherlands,
- Philippines,
- Singapore,
- South Korea,
- Thailand,
- UK,
- USA,
- Vietnam,
- ASEAN,
- Australia,
- Bangladesh,
- Brunei,
- Cambodia,
- China,
- Denmark,
- Germany,
- India.
- Ocean Lotus targeted dissidents and journalists operating against Vietnam.
- Ocean Lotus attempted to steal trade secrets by breaching the network security of automotive manufacturers BMW and Hyundai.
- Ocean Lotus targeted the Chinese Ministry of Emergency Management and the Wuhan Municipal Government to obtain information on the COVID-19 pandemic.
- Ocean Lotus compromised the mod.gov[.]kh domain of the Cambodia Ministry of Defense in its Watering Hole campaign.
- Ocean Lotus used mobile malware to attack mobile devices and steal confidential personal information such as SMS, call logs, connections, geolocation, and browser logs.
Various security vendors have reported that the Ocean Lotus group also has targeted finance, hospitality, and product sales sectors.
Operations Performed by APT32
In 2016, Ocean Lotus was observed targeting a number of Vietnamese organizations with a watering hole attack. The group used a website that masqueraded as a site for Vietnamese students studying abroad. When visitors to the site attempted to register for an account, they were redirected to a malicious website that served malware. This malware allowed Ocean Lotus to gain control of the victim’s computer.
In 2017, Ocean Lotus carried out a campaign against Vietnam’s National Assembly. The group sent spear phishing emails containing a link to a fake website that mimicked the National Assembly’s intranet login page. Victims who attempted to log in had their credentials stolen by Ocean Lotus.
In 2018, Ocean Lotus launched a successful campaign against Vietnam’s Ministry of Foreign Affairs. The group sent spear phishing emails containing a link to a fake website that mimicked the Ministry of Foreign Affairs intranet login page. Victims who attempted to log in had their credentials stolen by Ocean Lotus.
In 2019, Ocean Lotus was observed targeting a number of Vietnamese organizations with watering hole attacks. The group used websites that masqueraded as sites for Vietnamese students studying abroad. When visitors to the sites attempted to register for an account, they were redirected to malicious websites that served malware. This malware allowed Ocean Lotus to gain control of the victim’s computer.
Ocean Lotus’ operations have continued into 2020. In February 2020, the group was observed targeting Vietnamese organizations with a phishing campaign. The group sent emails containing a link to a fake website that mimicked the login page for Google’s Gmail service. Victims who attempted to log in had their credentials stolen by Ocean Lotus.
Ocean Lotus has been active for over eight years and shows no signs of slowing down. The group is skilled in carrying out sophisticated attacks and is considered a serious threat to organizations in Vietnam and other Southeast Asian countries.
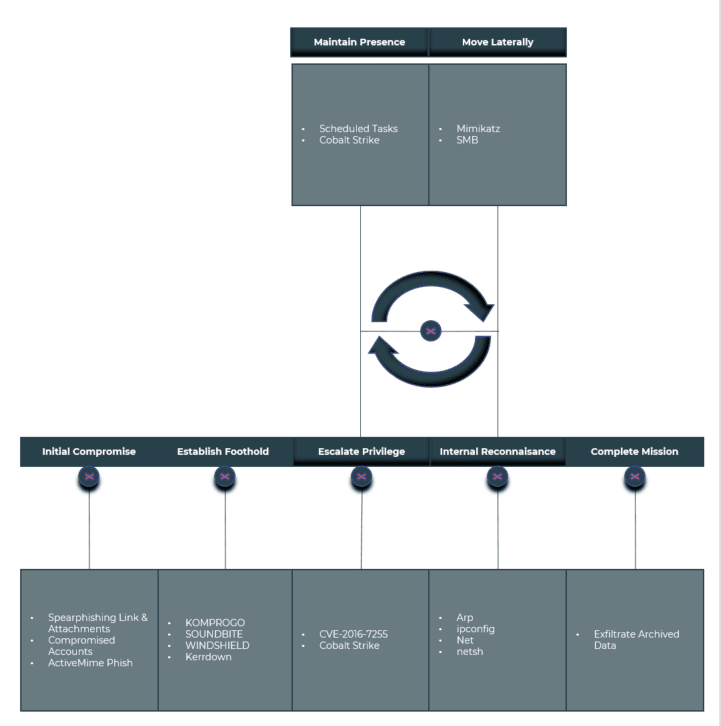
TTPs & Attack Lifecycle
The techniques, tactics, and procedures used by the Ocean Lotus group to violate the security of the target system in their attacks help define the threat group’s characteristics and determine the countermeasures that can be taken. In addition, the information below will be helpful for an overview of how a typical attack lifecycle is performed with the software used by Ocean Lotus and for what purposes the tools are used.
| Tactic | Tactic ID | Technique | Technique ID |
| Initial Access | TA0001 | Drive-by CompromisePhishing •Spearphishing Attachment •Spearphishing Link Valid Accounts •Local Accounts | T1189T1566 T1566.001 T1566.002 T1078 T1078.003 |
| Execution | TA0002 | Command and Scripting Interpreter•JavaScript •PowerShell •Visual Basic •Windows Command Shell Exploitation for Client Execution Scheduled Task/Job •Scheduled Task Software Deployment Tools System Services •Service Execution •Malicious File •Malicious Link Windows Management Instrumentation | T1059T1059.007 T1059.001 T1059.005 T1059.003 T1203 T1053 T1053.005 T1072 T1569 T1569.002 T1204.002 T1204.001 T1047 |
| Persistence | TA0003 | Boot or Logon Autostart Execution•Registry Run Keys / Startup Folder Create or Modify System Process •Windows Service Hijack Execution Flow •DLL Side-Loading Office Application Startup Server Software Component •Web Shell | T1547T1547.001 T1543 T1543.003 T1574 T1574.002 T1137 T1505 T1505.003 |
| Privilege Escalation | TA0004 | Exploitation for Privilege EscalationProcess Injection | T1068T1055 |
| Defense Evasion | TA0005 | Hide Artifacts•Hidden Files and Directories •Hidden Window •NTFS File Attributes Indicator Removal on Host •Clear Windows Event Logs •File Deletion •Timestomp Masquerading •Masquerade Task or Service •Match Legitimate Name or Location •Rename System Utilities Modify Registry Obfuscated Files or Information •Binary Padding System Binary Proxy Execution •Mshta •Regsvr32 •Rundll32 System Script Proxy Execution •PubPrn Use Alternate Authentication Material •Pass the Hash •Pass the Ticket | T1564T1564.001 T1564.003 T1564.004 T1070 T1070.001 T1070.004 T1070.006 T1036 T1036.004 T1036.005 T1036.003 T1112 T1027 T1027.001 T1218 T1218.005 T1218.010 T1218.011 T1216 T1216.001 T1550 T1550.002 T1550.003 |
| Credential Access | TA0006 | Input Capture•Keylogging OS Credential Dumping •LSASS Memory Unsecured Credentials •Credentials in Registry | T1056T1056.001 T1003 T1003.001 T1552 T1552.002 |
| Discovery | TA0007 | Account Discovery•Local Account File and Directory Discovery Network Service Discovery Network Share Discovery Query Registry Remote System Discovery System Information Discovery System Network Configuration Discovery System Network Connections Discovery System Owner/User Discovery | T1087T1087.001 T1083 T1046 T1135 T1012 T1018 T1082 T1016 T1049 T1033 |
| Tactic | Tactic ID | Technique | Technique ID |
| Lateral Movement | TA0008 | Lateral Tool TransferRemote Services •SMB/Windows Admin Shares Software Deployment Tools | T1570T1021 T1021.002 T1072 |
| Collection | TA0009 | Archive Collected Data | T1560 |
| Command and Control | TA0011 | Application Layer Protocol•Mail Protocols •Web Protocols Ingress Tool Transfer Non-Standard Port Web Service | T1071T1071.003 T1071.001 T1105 T1571 T1102 |
| Exfiltration | TA0010 | Exfiltration Over Alternative Protocol•Exfiltration Over Unencrypted Non-C2 Protocol Exfiltration Over C2 Channel | T1048T1048.003 T1041 |
Recommendations & Mitigations
We have listed the steps to be taken in order to be protected from the threat and/or to minimize the possible damage according to the identified techniques, tactics, and procedures of the Ocean Lotus APT group.
- Use strong passwords and multi-factor authentication: This will help to protect your accounts from being compromised by password guessing or brute force attacks. Multi-factor authentication adds an extra layer of security by requiring another form of verification, such as a code sent to your mobile phone, in addition to your password.
- Keep your software up to date: Outdated software can contain security vulnerabilities that can be exploited by attackers. By ensuring that your software is up to date, you can help to close these potential entry points.
- Install a reputable security suite: A good security suite can provide protection against a wide range of threats, including viruses, malware, and phishing attacks.
- Be cautious when opening email attachments: Email attachments may contain malicious code that can infect your computer. Before opening an attachment, make sure that you trust the sender and that you have scanned the attachment for viruses using reliable antivirus software.
- Don’t click on links in emails from unknown senders: Emails from unknown or untrustworthy sources may contain malicious code/attachments.
Conclusion
Ocean Lotus is well-resourced and executes its attacks with precision and care. The group uses a variety of custom tools, which suggests a high level of technical capability. Additionally, the group appears to have significant financial resources, as evidenced by its use of 0-day exploits and ability to mount long-term operations.






