Introduction
Cyber attacks experienced during the COVID-19 pandemic process have increased not only in vectors and numbers but also in terms of their impact. The pandemic process has expanded the surface of attacks and caused an increase in the number of cyber attacks targeting organizations through homes and offices. Also, cyber threat environments are changing with the fact that attackers are coming up with new technologies and processes constantly.
For example, in 2021, when we inspect the SolarWinds attack, which made an enormous impact, it seems that the malware has adopted a way of distributing embedded in a trusted product. After the SolarWinds attack, it has been determined that 1500 small and medium-sized companies were affected, especially the U.S. and Europe.
It has been observed that the main motivation of individual threat actors who carry out European-focused attacks is to earn financial gain. Cybercriminals have made the banking/financial sector the main target. With the crisis of the COVID-19 Pandemic, targeted ransomware attacks have increased swiftly. Many organizations that could not afford service interruptions had to pay the requested ransom. Although, some ransomware groups have demanded more ransomware, threatening organizations to publish stolen data using Double Extortion methods.
Threat actors that are supported by governments usually organize longer-term operations in the interests of the state they are affiliated with. Financial interests are in the background and trying to obtain strategic intelligence about the targeted country. It all comes to this that it is significant for security teams’ operations in today’s environment, where visibility and agility are crucial more than ever to be able to monitor cyber threat actors and their ongoing activities.
Darka
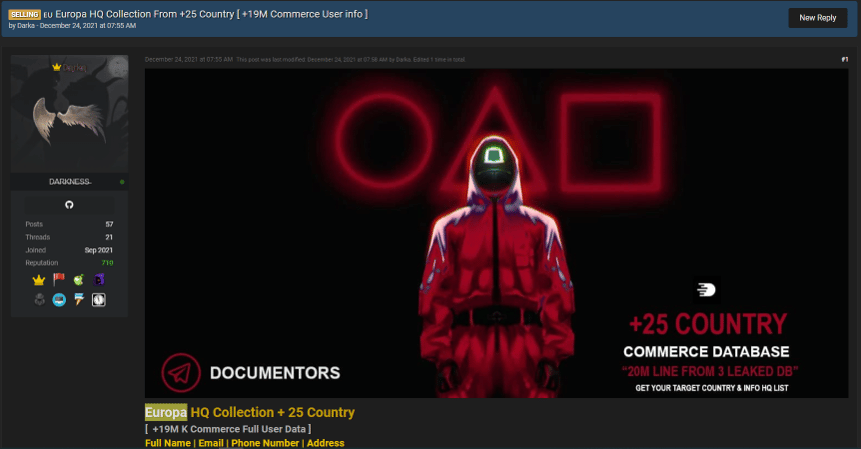
The threat actor, who uses the username DARKA on underground platforms, is actively selling databases belonging to 25 European countries. When the other shares of the threat actor were examined, the shares containing the sale of passports, identity cards, and personal data aimed at Europe were observed.
Spamhouse
The threat actor called Spamhouse often operates on Russian underground platforms. When the shares were examined, it was seen that the seized databases belonging to institutions in many European countries were sold. The threat actor regularly sells new hacked databases.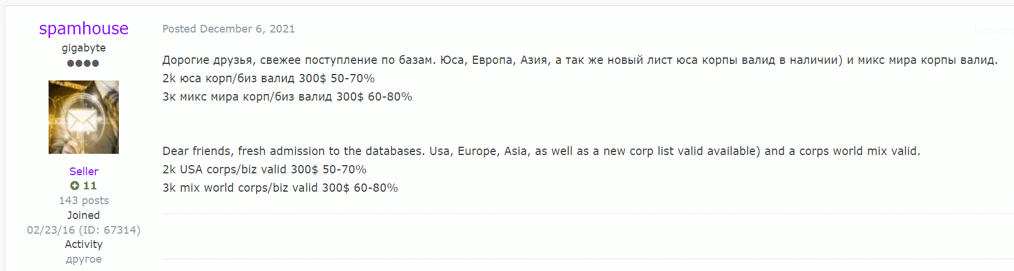
Juzab
The threat actor named Juzab continues his strategies on Russian underground platforms, exploiting certain vulnerabilities and selling access to institutions. The group usually sells the access information of the relevant institution to the highest bidder using the auction method.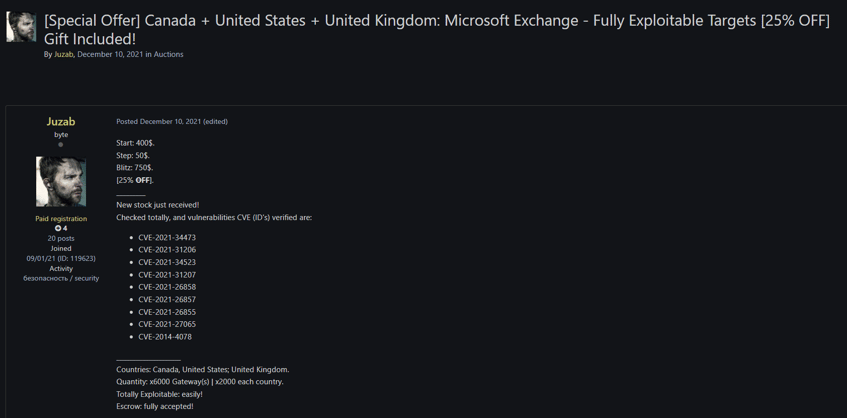
Matanbuchus
The threat actor, who uses the username Matanbuchus mostly continues his activities by renting the malicious software they have specially prepared to other attackers. When the threat actor’s other shares are examined, it is seen that he sells and rents malicious software that is not caught by antivirus systems.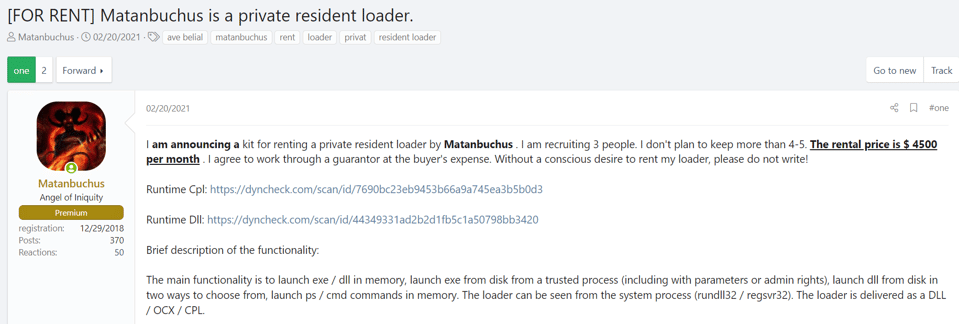
убитноневами
The threat actor named убитноневами, who is active on Russian underground forums, usually sells user information obtained from devices included in the botnet network. Besides, it also shares large log data publicly in order to achieve popularity. The shared log data belongs to the users who are included in the botnet network. This data includes much information such as desktop screen photos, credit card and password information saved in the browser, system information, a list of processes running in the system, autofill values, and cookie values saved in the browser. The relevant log data is obtained from many countries worldwide by infecting the user’s computers with malicious software called Stealer.
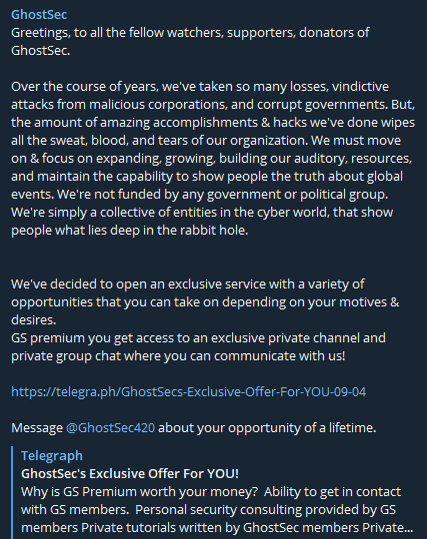
GhostSec
The threat actor named GhostSec, who is active on underground forums and Telegram channels, announce group’s hacking activities. The group started their activities on 2015 against ISIS but they have unknown origin.
GhostSec is a highly organized hacktivist group that has ties with members of the “Anonymous” hacktivist collective. Similar like Anonymous operations, the actions of GhostSec is shared on Twitter and Telegram to show DDoS attacks, OS intrusions, webpage defacement (indexed websites) and data leaks.
The threat group has a subscription-based premium channel on Telegram, in which they share exclusive content, such as leaks, tutorials, and others with their subscribers.
AgainstTheWest / BlueHornet
The threat actor named BlueHornet, who is active on underground forums and Telegram channels, announce group’s hacking activities. The group usually targets Russian companies.
Also the BlueHornet claimed about hacking TikTok’s databases. After couple of proof of concept tweets and serious data leakage Twitter has suspended the group’s social media account. Despite of shared proof of concepts by the BlueHornet, allegations were denied from TikTok.