Introduction
The apt group, known as APT28 or FANCY BEAR, is a threat group attributed to the Main Intelligence of the Russian Joint Chiefs of Staff, according to the July 2018 US Justice indictment. It is known that it has been operating since 2004. It targets various sectors and institutions from all over the world.
Group’s Mission and Vision
Among the main objectives of the group, its targets are to gather security and policy-oriented intelligence, and this information is considered by Russia to provide an opportunity for highly influential people to influence public opinion and make predictions about future policies.
In addition, because Russia sees security organizations such as NATO and OSCE across Europe as a constant threat to itself, attacks are carried out in which such organizations and individuals affiliated with these institutions are among the targets. The group actively engages in information theft and espionage.
Group’s Country of Origin and Known Aliases
FANCY BEAR is known by various security vendors by the following definitions.
- Sofacy (Kaspersky)
- APT 28 (Mandiant)
- Fancy Bear (CrowdStrike)
- Sednit (ESET)
- Group 74 (Talos)
- Pawn Storm (Trend Micro)
- Strontium (Microsoft)
- Swallowtail (Symantec)
- SIG40 (NSA)
- Iron Twilight (SecureWorks)
- ITG05 (IBM)
- Grizzly Steppe (US Government)
Targeted Countries and Industries
Russia sees European security organizations such as NATO and OSCE as a threat to them. For this reason, it targets both the member states of such organizations and the individuals affiliated with these organizations.
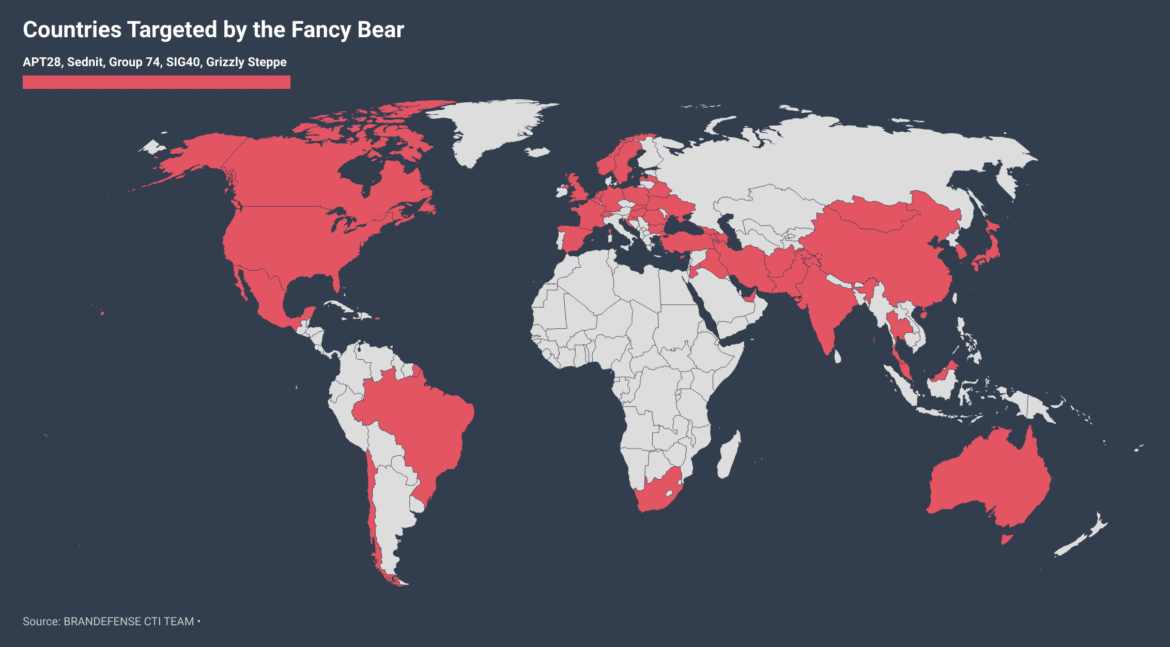
APT28 is known to target many industries. These sectors are shared below;
- Finance
- Aviation
- Chemical
- Education
- Defense
- State
- Embassies
- Health
- Fuel
- Information technologies
- Media
- Other (automotive and construction…)
Activities by Year
2013 MiniDuke Mystery
APT28 was found to be hacked in 2013 using the Adobe Reader 0-day exploit, code CVE-2013-0640, with PDF files specially created to distribute a previously unknown piece of advanced malware called ItaDuke. The PDF files used in the attacks have well-prepared content-themed human rights seminar information, Ukrainian foreign policy, and NATO membership plans.

2014 Cyber Attacks on the German Parliament
The APT28 group is held responsible for carrying out targeted phishing attacks over email against German parliamentarians. It is also known that the attackers make extensive use of Trojan software to increase their access to the Parlacom network.
2015 EFF Spoof, White House and NATO Attacks
APT28 targeted NATO members, US Defense, and White House officials with Java 0-day exploit and targeted attacks. This attack, which is considered part of a wider campaign called Pawn Storm, is aimed to deceive the target users by imitating the domain name of the Electronic Frontier Foundation (EFF).
2016 Pawn Storm Attack Campaign Adds Turkey To Its Target List
The long-running Pawn Storm attack campaign, targeting the armed forces, diplomats, software developers, journalists, and dissidents, has added several government offices, including the Turkish parliament and the Prime Ministry, to its target list.
The common feature of the assets in the target list is that they have the potential to threaten Russia. However, the possible reasons for Turkey to be included in the target list are shared below.
- Disputes after the Turkish Air Force shot down a Russian jet over Syria in 2015
- Internal conflicts with Kurdish groups
- Refugee groups trying to enter Europe through Turkey
2017 Dealer’s Choice Phishing Campaign
It was determined that APT28 carried out phishing attacks targeting NATO member states, including Turkey and Azerbaijan, as well as Ukraine, in early 2017.
2018 Cyber Attacks Targeting the US and Romanian Foreign Ministries
In 2018, APT28 targeted two unaffiliated US and Romanian government organizations outside its mandate. The first attack vector for the campaign carried out is the phishing e-mail with the subject “Upcoming Defense event February 2018”.
The text intended to deceive Targeted Users included instructions on the email attachment a calendar of events for the targeted organizations and actions to take in case of an error in viewing the document.
2019 Pawn Storm Target’s Defense Companies in the Middle East
The Pawn Storm group has continued to send spam emails to carry out phishing attacks since 2019. It has been observed that the majority of the compromised e-mails used in the attacks are from defense companies in the Middle East.
By monitoring Microsoft Exchange Autodiscover and e-mail servers around the world, the attackers discovered vulnerable systems by using user account information already leaked to the internet in Brute Force attacks.
2020 APT28 Distributes Zebrocy Malware in NATO-Themed Attack Campaign
The malware used by the APT28 group in this attack is the Zebrocy Delphi version, which has a very low detection rate. The detected C2 infrastructure associated with the malware is hosted in France. The theme of NATO’s Upcoming Training was used as bait in the campaign to distribute the malware.
2021 APT28 Exploited MSHTML Vulnerability in Espionage Against Government and Defense Targets
APT28 is aimed at employees in the defense industry and high-level power users overseeing security policies in West Asia.
The group used the OneDrive service as the command and control server. Thanks to this type of communication approach, it has been possible to perform spying activities on target systems since no suspicious network traffic is logged.
Cyber Attack Lifecycles and TTPs (MITRE ATT&CK)
It defines the techniques, tactics (TTPs), and procedures identified as being used in attacks carried out by the APT28 threat group.
| Tactical ID | Tactics | Technical ID | Technical |
| TA0043 | Reconnaissance | T1595 T1589 | Active Scanning Gather Victim Identity Information Phishing for Information |
| TA0042 | Resource Development | T1583 T1588 | Acquire Infrastructure Obtain Capabilities |
| TA0001 | Initial Access | T1190 T1133 | Exploit Public-Facing Application External Remote Services Phishing Replication Through Removable Media Trusted Relationship Valid Accounts |
| TA0002 | Execution | T1059 T1203 | Command and Scripting Interpreter Exploitation for Client Execution Inter-process Communication User Execution |
| TA0003 | Persistence | T1098 T1547 | Account Manupilation Boot or Logon Autostart Execution Boot or Logon Initialization Scripts Event-Triggered Execution External Remote Services Office Application Startup Pre-OS Boot Server Software Component Valid Accounts |
| TA0003 | Privilege Escalation | T1134 T1546 | Access Token Manipulation Event-Triggered Execution Exploitation for Privilege Escalation Valid Accounts |
| TA0005 | Defense Evasion | T1134 T1140 | Access Token Manipulation Deobfuscate/Decode Files or Information Exploitation for Defense Evasion Hide Artifacts Indicator Removal on Host Masquerading Obfuscated Files or Information Pre-OS Boot Rootkit Signed Binary Proxy Execution Template Injection Use Alternate Authentication Material Valid Accounts |
| TA0006 | Credential Access | T1110 T1056 | Brute Force Input Capture Network Sniffing OS Credential Dumping Steal Application Access Token |
| TA0007 | Discovery | T1083 T1040 | File and Directory Discovery Network Sniffing Peripheral Device Discovery Process Discovery |
| TA0008 | Lateral Movement | T1210 T1021 | Exploitation of Remote Services Remote Services Replication through Removable Media Use Alternate Authentication Material |
| TA0009 | Collection | T1560 T1119 | Archive Collected Data Automated Collection Data from Information Repositories Data from Local System Data from Network Shared Drive Data from Removable Media Data Staged Email Collection Input Capture Screen Capture |
| TA0011 | Command and Control | T1071 T1092 | Application Layer Protocol Communication Through Removable Media Data Obfuscation Encrypted Channel Ingress Tool Transfer Proxy Web Service |
| TA0010 | Exfiltration | T1030 T1048 | Data Transfer Size Limits Exfiltration Over Alternative Protocol Exfiltration Over Web Service |
| TA0040 | Impact | T1498 | Network Denial of Service |
Group’s Malware / Utility
Malware and utilities used by FANCY BEAR are shared below;
- ADVSTORESHELL
- Cannon
- CHOPSTICK
- CORESHELL
- DealersChoice
- Downdelph
- Drovorub
- HIDEDRV
- JHUHUGIT
- Koadic
- Komplex
- LoJax
- OLDBAIT
- USBStealer
- X-Agent for Android
- XAgentOSX
- XTunnel
- Zebrocy
- Fysbis
- Forfiles
- Certutil
- Mimikatz
- Net
- Responder
- Tor
- Wevtutil
- Winexe
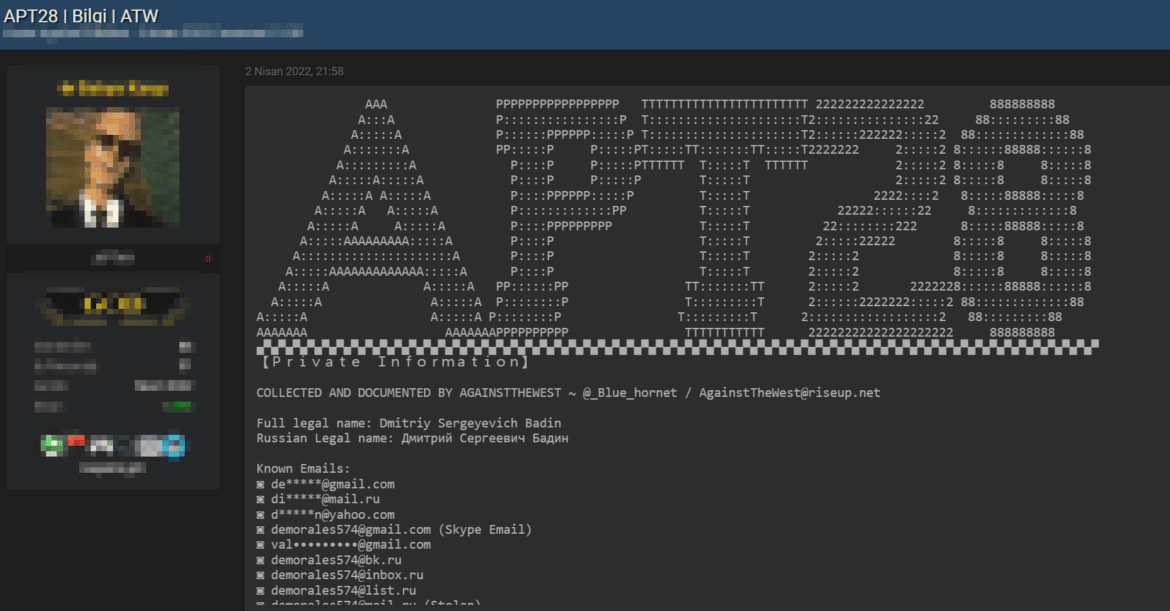
Leaking Information of Group Members
In a post from the darknet, it was claimed that some of the group members’ information was leaked.
YARA
Wound rules are used to classify malware and identify malicious code. We can obtain information about which malware family a detected malware belongs to or which hacker group is used by the Yara rules.
You can find the wound rules written for APT 28 below;
https://github.com/Neo23x0/signature-base/blob/master/yara/apt_apt28.yar
https://github.com/Yara-Rules/rules/blob/master/malware/APT_Grizzlybear_uscert.yar
Recommendations/Mitigations
Examining the cases encountered, the group mostly sought to gain initial access. Phishing attacks and security in existing systems are found to take advantage of its vulnerabilities. In this context, by APT28 Attack vectors used to protect against possible attacks precautions should be taken.
To protect assets in the digital world, security vulnerabilities, and important device recommendations to minimize the risk of exploitation arising from its configuration are shared below.
- Make sure that users in the system have the least privileges/authorities they need.
- Shared IoCs should be added to security solutions.
- Multi-factor authentication (MFA) must be used, including privileged accounts and all users.
- IDS/IPS systems that use network signatures should be used to identify network traffic generated by malware
- Antivirus/Antimalware software should be used to automatically quarantine suspicious files.
- As far as possible, the use of removable media devices such as USBs should not be allowed or restricted within the organization.
- Web Proxy to block the use of web-based external services should be used.
- Web Application Firewall (WAF) should be used to prevent exploit traffic from reaching the target application.
- The patches published for the external software used should be followed and updated regularly.
Download the IoCs from Brandefense Github Repository.






