Intro
Cyber Intelligence is knowledge, skills, and analyzed data to understand threat actors’ targets, behaviors, motives, and what they seek. The world of the Deep Web can be used to gain knowledge about cyber intelligence. Hacking and carding forums, leak databases, encrypted chat platforms, and illegal marketplaces provide threat actors a network, requiring deep web intelligence to understand potential threats.
Deep web or networks are connections that are made amongst trusted peers and some of them include Tor, Invisible Internet Project (I2P), or Freenet. Deep web intelligence, has a reputation in cyber threat intelligence as it monitors different sources to obtain security insights. This can be generated and prepared that could prevent cyber threats. Deep web intelligence plays an important role as many unindexed websites also have a lot of valuable information that helps to take the necessary measures. Deep web intelligence also uses deep web forum portals in order to make counter-hacking, collect confidential information, and cyber-attack surface analysis.
Most Common Threats From the Deep Web
Deep Web is a gateway to the underground crime market. Many threat actors use forums as like a rite of passage for more advanced threat actors. Searching threats from the deep web forums should not be limited to just hacker and dark web (TOR) forums. Even threat actors hang out on nonhacker forums, which can require skills like cracking, zero-day hacking, or launching ransomware attacks.
Here are some types of common threats from the deep web:
- Botnets: Such malware includes many bots that coordinate different types of attacks and hackers offer them on the dark web.
- Ransomware: Advanced threat actors develop malicious software to encrypt all the data after collecting them from their victims. Targeted and highly motivated cyber-attacks are shown and published on the Deep Web.
- Exposed databases: Hackers acquire credentials from malware and phishing campaigns. Consequently, they can abuse the compromised accounts to their advantage.
- Hacked accounts: Hacked accounts not only jeopardize the owner’s information but also pose a threat to other accounts on that domain. The hacker might use the account covertly as a foothold for launching further attacks.
- Vulnerability publishers: Almost every application/service has some security vulnerabilities. Hackers target, discuss and publish these vulnerabilities on the dark web.
- Targeted cyber attacks: Hackers offer or ask for tailored cyber attacks on different websites and deep web forums. Targeted cyber-attacks are usually like DDoS, SQL Injection, or RDP exploits.
Rise of Ransomware Attacks
Over the last few years, organized crime has watched, and learned, from how simply, and anonymously similar attacks can be utilized as a part of their overall illegal business plans. The harvesting of critical data gave control and power to threat actors and the Ransomware spawned and the global economy has changed forever.
Ransomware, in the simplest of terms, is the name given to a type of Malware from crypto virology that typically threatens to publish the victim’s data or block access to it unless a ransom is paid.
Ransomware and cyberattacks on a high level are a challenge to keep track of. It is evolving over the last few years. Now it means that threat actors exfiltrate data and then demonstrate them on the Deep Web.
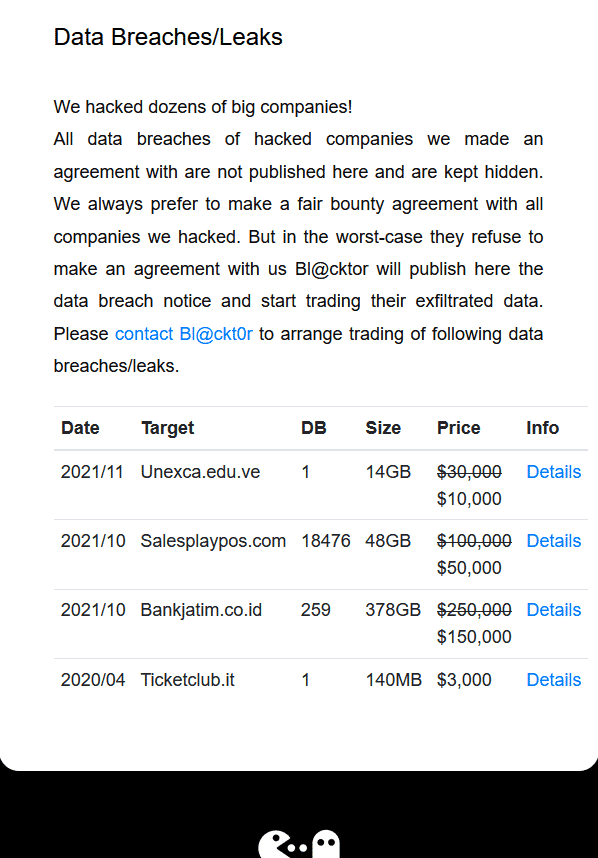
Here are examples of REvil Ransomware Group’s cyber-attacks and demonstration of critical data: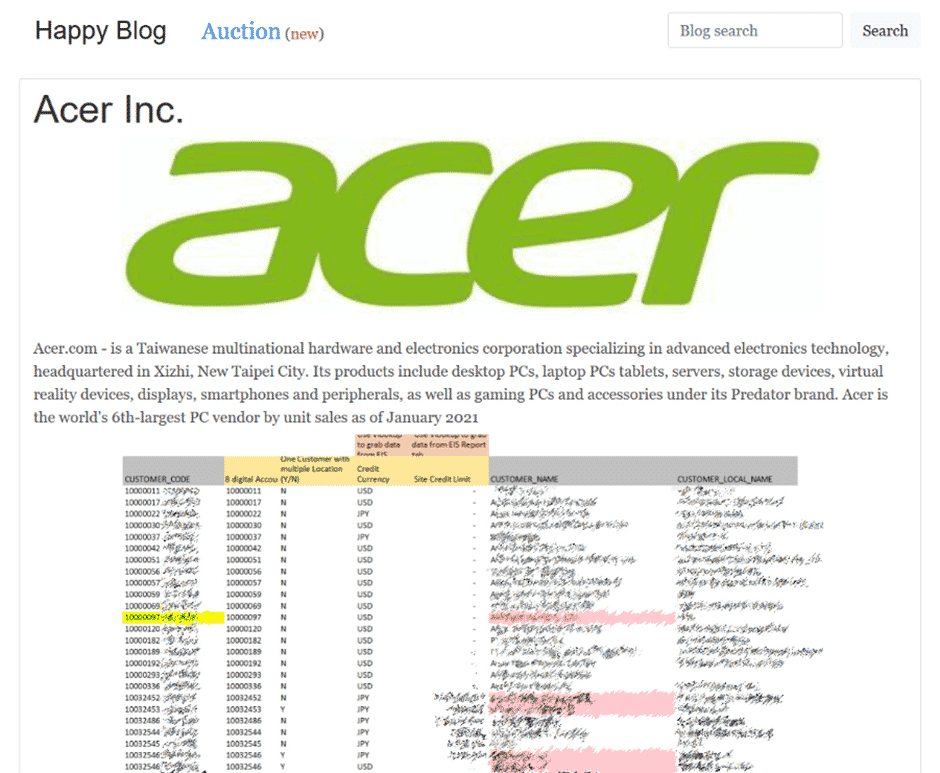
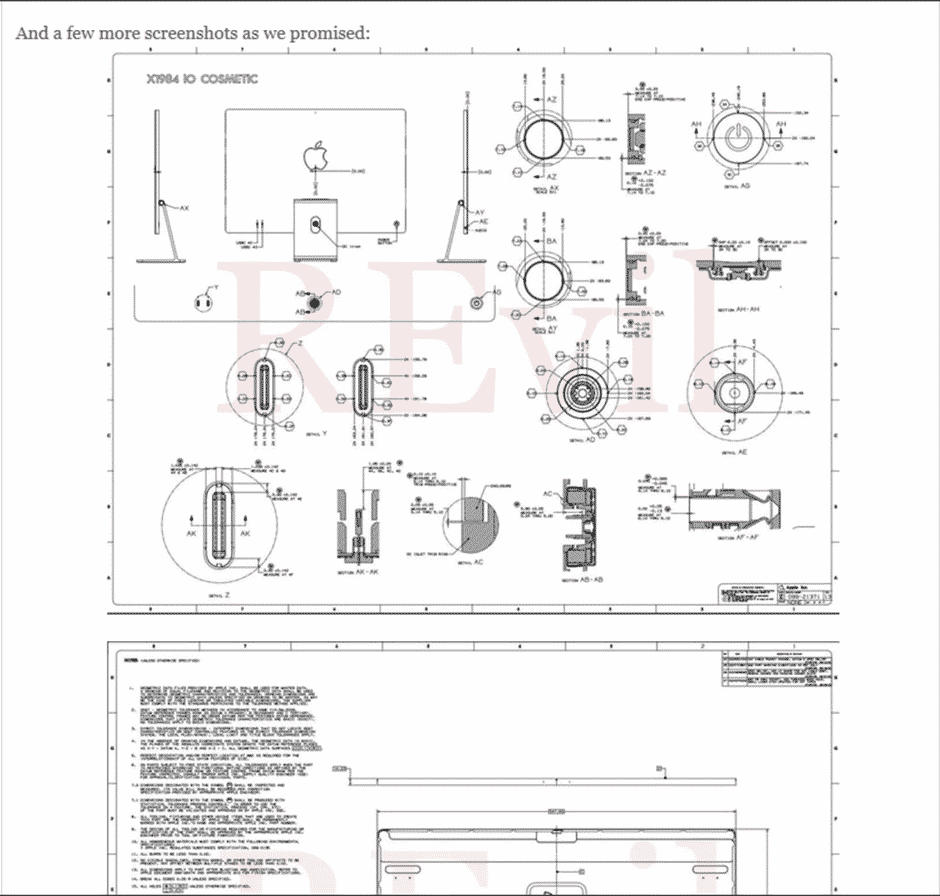
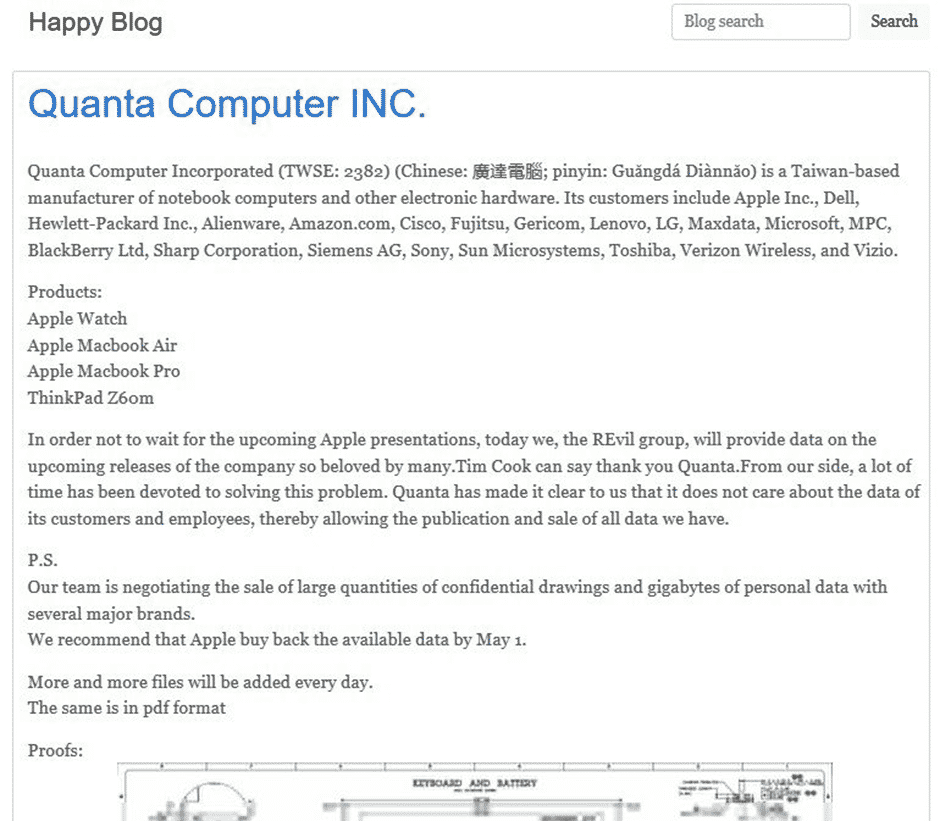 Gathering intelligence and investigating Ransomware attacks can provide in-depth analysis to get a high-level security mindset.
Gathering intelligence and investigating Ransomware attacks can provide in-depth analysis to get a high-level security mindset.
Deep Web Intelligence Trends
Deep web intelligence is mostly found in online services. Controlling searchable lists, guides and directories that contain indexed information on a specific topic is very important. Collecting deep web intelligence can be a more labor-intensive process than gathering OSINT on the surface web. Here are some Intelligence feeds for example;
- Paste Sites,
- Deep Web Forums,
- Credential Marketplaces,
- Identity Fraud,
- Chat-Based Services,
- Carding Marketplaces,
- Ransomware Group Sites,
- Deep Web Search Engines.
Among these feeds, almost 70% of stolen data is marketed on Chat-Based Services and Carding Marketplaces.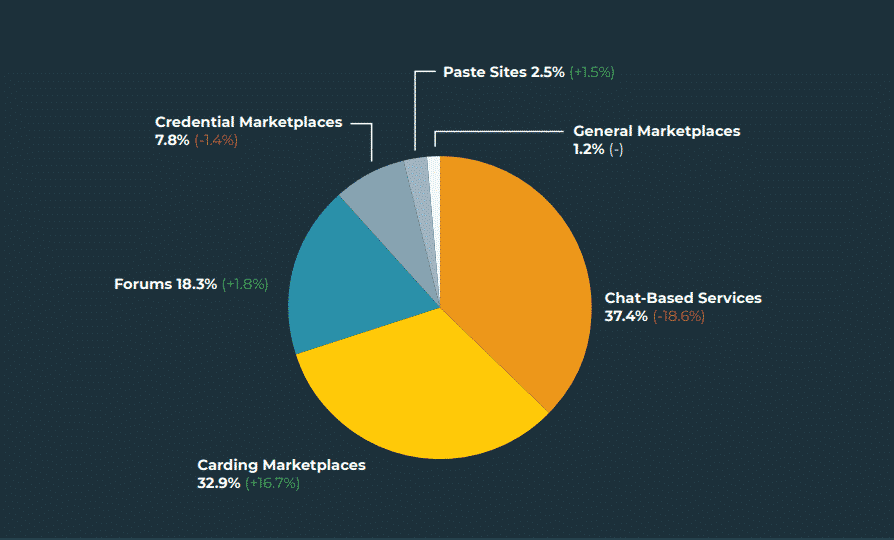
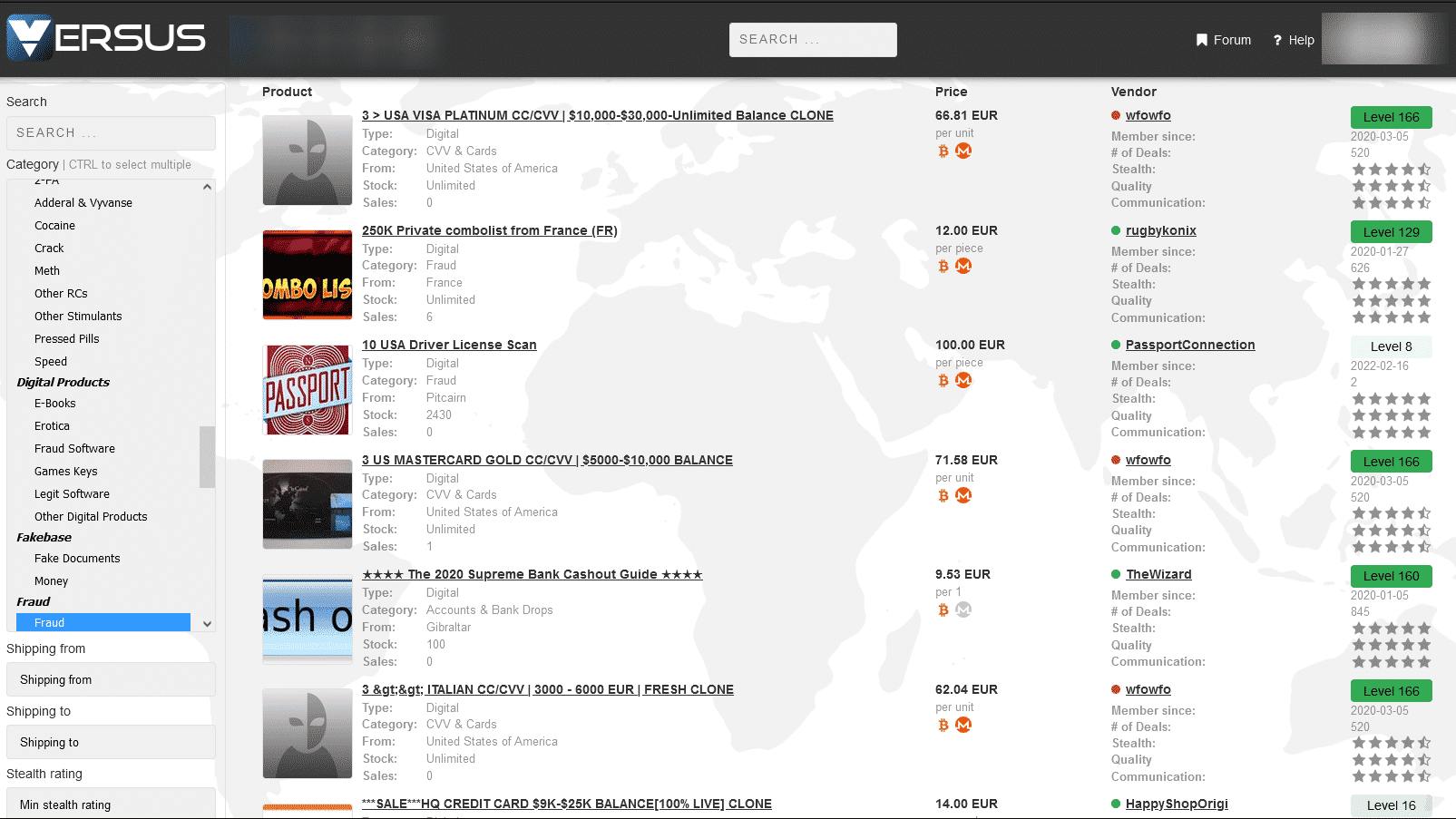
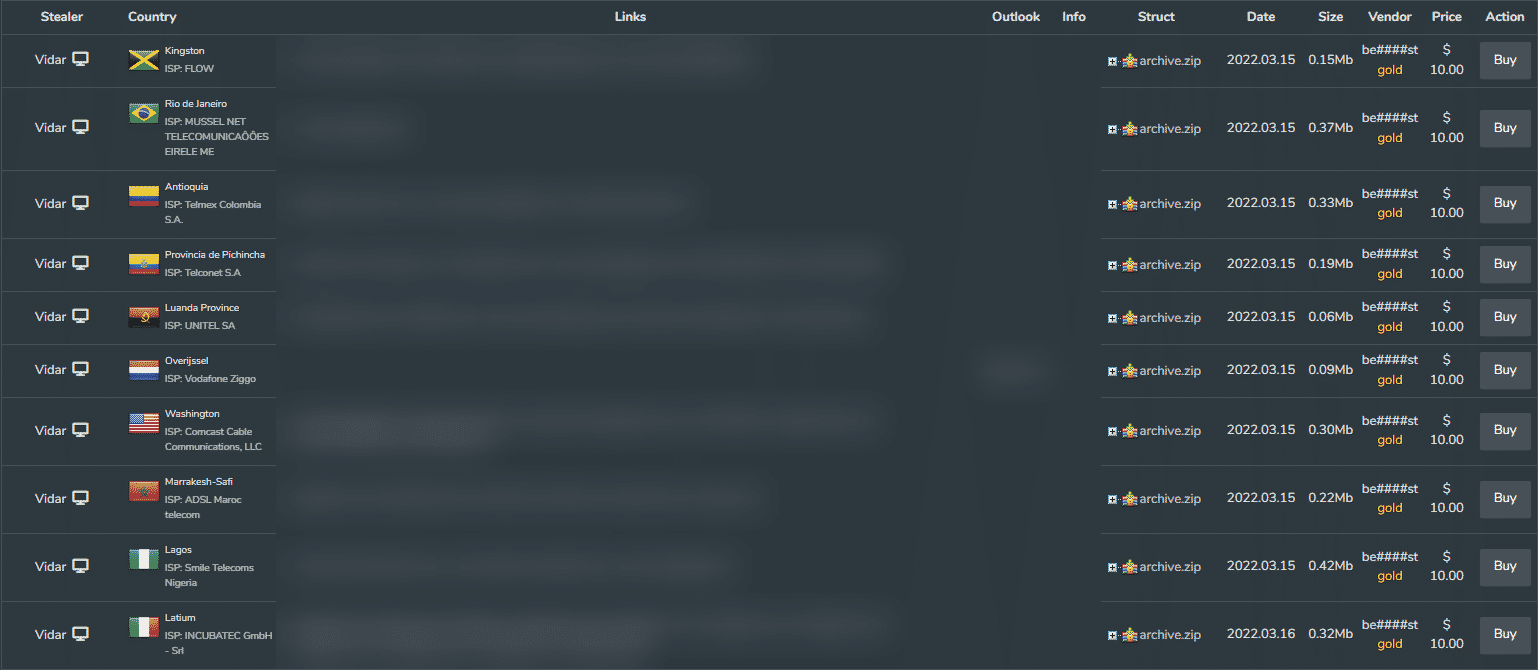
 Identity fraud, fake passports, and documents are sold through Deep Web. Fake IDs are in use of social engineering or targeted phishing attacks by threat actors.
Identity fraud, fake passports, and documents are sold through Deep Web. Fake IDs are in use of social engineering or targeted phishing attacks by threat actors.
Conclusion
Deep web can be useful for collecting valuable data that informs the types of cyber threats a company is facing as well as supporting a more nuanced understanding of its risk profile. However, data from this source can be hard to find and is often unreliable.
As-a-service offerings, data dumps, and general chatter about an organization can all be valuable that can inform a security posture. Validating each data point is crucial to avoid wasting resources. The resources required to find the data in the first place and then validate will be significant.
It’s essential that security teams focus their deep web efforts appropriately. While there is plenty of criminal activity on the web, focusing on the specific threats to your business will allow you to cut through the noise and understand your organization’s unique risk profile.
With the use of web monitoring systems gather intelligence and provide knowledge of the possible threats against your digital assets. Such tools can be used for the following types of intelligence:
- Security News from the Deep web Monitoring Systems: give clues that your site has become a trend on hacker forums.
- Discussions: gathering information from deep web discussions will let you know whether weaknesses on the web have been exploited. This can be used to secure websites to prevent attacks in the future.
- Underground identities: threat actors try to keep their identities anonymous, however, you can gather information on which deep web forum they are based and what they are interested in.
- Service providers, data sales, and leakage: threat actors need to advertise their services and the data they can provide to make money. Using a service such as Brandefense will help you to detect leaks and data sales.
Brandefense protects your online assets by monitoring deep&dark web continuously. This proactive approach gains you the time and money that you need.
Deep web intelligence can be used to proactively fight fraud activities and it has proven to reduce financial losses. Deep web intelligence contains different sets of data feeds in reach from the deep web; malware networks, botnets, ransomware groups, identity fraud, credential marketplace, and other technical infrastructure used by cyber threat actors to commit financial acquisition.






