Introduction
The internet as we know it is just the tip of the iceberg. Beyond the surface lies the vast Deep Web, a space filled with unindexed content, and the elusive Dark Web, a subset where anonymity reigns supreme. To access these hidden corners, specialized browsers and search engines come into play. While these tools have legitimate applications, they are also gateways to significant risks. This article explores the top deep web browsers and search engines, shedding light on their uses, potential dangers, and the importance of staying secure while navigating these uncharted territories.
Staying Anonymous
Staying anonymous is needed not only by whistleblowers but also by credit card scammers, drug dealers, etc. While you’ve probably heard of all the criminal activities that take place, one of the most significant benefits of using a Deep Web Browser is being able to browse the internet anonymously.
Such anonymous networks are the focus of attention not only of ordinary people fleeing censorship but also of criminal cartels. Many different applications are used to hide the users’ identities and ensure the security of the data they transmit on the internet. While some of these applications only work as a proxy server, there are also versions that can be installed as stand-alone software or an operating system. Some applications have their own network infrastructure, while others use the network infrastructure of other applications.
Top Deep Web Browsers
Tor Browser
The dark web is a part of the internet that we can reach only with a specific tool. It hosts onion links that you can not find with regular browsers like Chrome, Firefox, Edge, or Safari. For this, the Tor browser works best as it allows you to visit dark websites while maintaining anonymity by routing your traffic through several nodes.
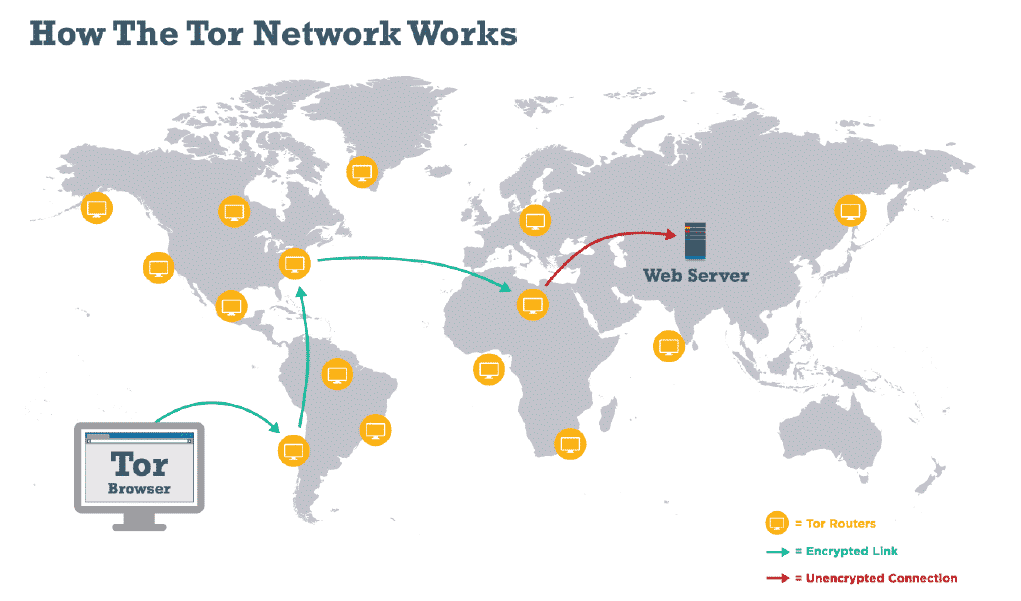
Tor (The Onion Router) is the name of a network and software project that provides anonymous communication to its users. The project enables users to access the internet in an encrypted manner by hiding their real identities by using the Tor web browser over the network of more than 6000 volunteer Tor servers located worldwide and reduces the risk of being tracked. Tor Browser relayed the traffic and encrypted it three times as it passed over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays.
I2P
Another deep web browser, I2P, is quite different from Tor as it offers anonymity and works with multiple layers of data streaming, thus protecting your privacy.
Invisible Internet Project (I2P) is a fully end-to-end encrypted private network layer enhanced by privacy and security by design that provides protection for your activity, location, and identity. I2P comes with a router that connects you to the network and applications to share, communicate with other I2P devices, and build stuff.
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information and has a suite of free software for publishing and communicating on the web without fear of censorship. Freenet’s goal is to provide freedom of speech on the Internet with strong anonymity protection.
In addition, thanks to the security mode it calls “darknet,” it can only connect to registered “trusted” nodes. This is why it differs from other popular anonymous networks.
FreeNet keeps encrypted files by allocating a certain part of your disk to support/feed its own network. And it does not accept responsibility for the legal side of the files kept. It states in its official documentation that users cannot easily discover what these encrypted files are.
Top Deep Web Search Engines
Ahmia
Ahmia presents itself as a hidden service search engine, and that’s what it does. It aims to provide users of the Tor Anonymity Network with a powerful and robust search engine that helps discover different useful websites on the dark web. Moreover, Ahmia can also be used to view statistics, insights, and news about the Tor network.
Recon
Recon is a new market/vendor data aggregator service and a cross-marketplace search engine. It allows you to see and look up data on multiple established darknet markets from one single modern and functional interface.
EXCAVATOR
EXCAVATOR is a dark web .onion Search Engine based on simplicity and anonymity that does not track you or use Java Script. This Search Engine was made in 2019 by an anonymous group of activists. They also have a project named Excavator Token, which you can buy and help development and maintenance costs of the Excavator.
Torch
Torch is one of the oldest and most well-known darknet search engines. As stated by the Torch team, Torch scrapes new onion sites every day, and our goal is to index every Tor website that’s publicly accessible. Currently, we have indexed over 100,000 onions and over 4 million web pages. The search results on Torch are not censored. Torch team believes trying to censor the dark web is counterproductive and a waste of resources.
The Deep Searches
The Deep Searches, the largest darknet, and deep web search engine, provides search services for hidden content.
GDark
GDARK is an association created to offer an advanced Darknet search engine.
Phobos
Phobos is a very minimalistic and simple search engine for Tor .onion hidden websites. It’s working very much the same. Like Google, you type the keyword you are searching for, click on search, and that’s it. Not much is known about who created Phobos or why, as there is no “About Us” or “Contact Us” page. However, Phobos is very easy to search and a high-speed Search Engine for Tor.

Tools like Tor Browser and I2P allow users to explore the hidden layers of the internet, providing anonymity and access to unindexed content. These browsers are often used for legitimate purposes, such as bypassing censorship or protecting privacy. However, they also come with significant risks. Cybercriminals leverage these platforms to host illegal marketplaces, distribute stolen data, and coordinate phishing campaigns.
Brandefense’s Dark Web Monitoring solution is designed to proactively detect and neutralize such threats. By scanning hidden forums, encrypted communication channels, and underground marketplaces, it identifies stolen credentials, counterfeit products, and other malicious activities targeting your business. This early detection allows companies to act swiftly, protecting their brand and minimizing damage.
Security Guide: Risks and Protection Strategies
Exploring the Deep Web and Dark Web offers unique opportunities but also exposes individuals and businesses to significant risks. Understanding these dangers and adopting effective security measures is essential for safe navigation. Below is an overview of the threats associated with these spaces and practical guidance on staying protected.
Risks: Threats on the Dark Web
- Malware Attacks: Dark Web platforms often harbor malicious software that can steal personal information, take over devices, or deploy ransomware.
- Phishing Attacks: Cybercriminals use phishing tactics to trick individuals into sharing sensitive information like passwords or financial details.
- Data Leaks and Sales: Stolen user data, including emails, passwords, and credit card numbers, frequently surface on Dark Web marketplaces.
- Legal Implications: Accessing illegal content or engaging in unlawful activities on the Dark Web can lead to severe legal consequences.
- Brand Exploitation: Company names, logos, and other intellectual property can be misused on the Dark Web for fraudulent activities.
How to Stay Protected
Navigating the hidden layers of the internet requires more than just caution—it demands actionable insights into emerging threats. Brandefense’s Threat Intelligence solution delivers a comprehensive analysis of malicious activities on the Dark Web, providing businesses with real-time data on potential risks.
By leveraging advanced analytics and a global monitoring network, Brandefense uncovers threats like intellectual property misuse, data breaches, and counterfeit goods. Armed with these insights, businesses can take informed action to neutralize risks and protect their digital assets.
Conclusion
Deep web browsers and search engines offer a glimpse into the hidden layers of the internet, empowering users with anonymity and access to unindexed content. However, this power comes with significant risks, as malicious actors exploit these tools for illegal activities. Understanding how these technologies work and their associated dangers is crucial for anyone venturing into this space.
In this article, we explored the tools that unlock the hidden corners of the internet, from specialized deep web browsers like Tor and I2P to search engines designed for unindexed content. We discussed their legitimate applications, the inherent risks they pose, and the importance of maintaining security when navigating these spaces. For those looking to deepen their understanding, topics like the risks of data breaches, how dark web marketplaces operate, and strategies for digital brand protection can provide further insights into this complex domain.
Navigating the deep web doesn’t have to be daunting. With solutions like Brandefense’s Dark Web Monitoring and Threat Intelligence, businesses can detect threats early, respond swiftly, and safeguard their digital assets. Whether you’re a business looking to protect your assets or an individual prioritizing online privacy, Brandefense ensures you’re always secure in the digital shadows.