In today’s interconnected world, supply chains are more complex and expansive than ever. From raw materials to finished products, countless businesses, suppliers, and vendors form a delicate web that ensures the smooth operation of industries across the globe. However, with this complexity comes increased vulnerability. As the supply chain grows, so do the potential entry points for cybercriminals looking to exploit weak links.
The truth is, securing your organization isn’t enough anymore. Modern cyberattacks target supply chains, infiltrating through trusted third parties and vendors, often with devastating results. A National Institute of Standards and Technology (NIST) study found that nearly 80% of cyber breaches in the past few years involved some form of third-party compromise.
In this blog, we’ll explore the complexities of supply chain cyber risks, explore real-world attacks that have disrupted entire industries, and outline actionable strategies to protect your business from becoming the next victim. By leveraging the insights from Brandefense’s digital risk protection platform, you’ll learn how to secure your supply chain and minimize the impact of cyber threats on your operations.
Understanding the Supply Chain Cyber Risk
Supply chains are inherently vulnerable because they involve multiple stakeholders and touchpoints. As a business, you may have invested heavily in cybersecurity measures, but every external partner—whether a logistics provider, manufacturer, or technology vendor—introduces potential weak points. Attackers often target the least secure link in the supply chain to have access to the entire network.
Supply chain cyber risks take many forms, from malware injections and ransomware to compromised credentials and data leaks. Here are some of the most common cyber threats supply chains face:
Vendor Compromise
One of the most common attack vectors is through vendors or third-party service providers. Hackers can exploit weak security measures within a vendor’s network, using it as a backdoor to infiltrate the larger organization. Once inside, they can move laterally through the supply chain, stealing data or deploying malware.
Phishing and Social Engineering
Cybercriminals are adept at tricking individuals into revealing sensitive information. Phishing attacks, fraudulent emails, or messages designed to steal data are particularly effective in supply chains. A single phishing email sent to a supplier or partner could compromise your entire network.
Malware and Ransomware
Supply chains often rely on interconnected IT systems and software solutions to coordinate operations. If one of these systems becomes infected with malware or ransomware, the disruption can ripple across the entire supply chain, halting production, delaying shipments, and causing financial losses.
Data Breaches
Many companies within a supply chain handle sensitive information, including trade secrets, product designs, and customer data. A data breach in one part of the supply chain can expose this valuable information to cybercriminals, putting the entire business at risk.
Insider Threats
Insider threats, intentional or accidental, can wreak havoc on a supply chain. A disgruntled employee, or one who unknowingly clicks on a malicious link, can introduce malware or grant unauthorized access to critical systems.
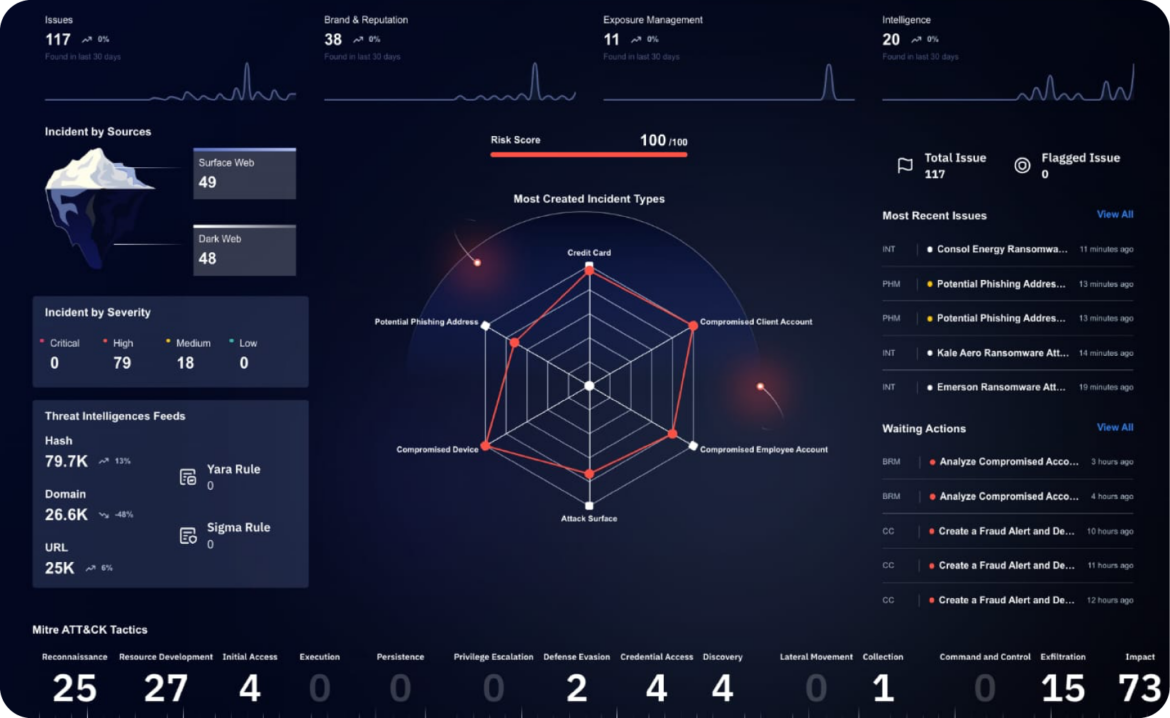
Real-World Examples
Several high-profile cyberattacks have underscored the importance of supply chain security. Let’s explore a few examples that reveal how attackers exploit supply chain vulnerabilities and the far-reaching impact of these breaches.
SolarWinds Attack
The 2020 SolarWinds attack is one of history’s most notorious supply chain attacks. Cybercriminals inserted malicious code into a routine software update from SolarWinds, a company providing IT management software to thousands of organizations. When the update was installed, it created a backdoor that allowed attackers to spy on networks, steal data, and compromise government agencies, including the U.S. Treasury and Department of Homeland Security.
This attack illustrated how cybercriminals could use trusted software vendors to gain access to highly secure environments, making it one of the most significant breaches in modern history.
Target Breach
In 2013, retail giant Target experienced a massive data breach that compromised the credit and debit card information of over 40 million customers. The attackers gained access through an HVAC contractor that worked with Target. Once inside, they moved laterally across Target’s network, installing malware on point-of-sale systems and harvesting customer data.
This breach highlighted the dangers of insufficient vendor management and how a small third-party vendor can become the weakest link in a vast supply chain.
NotPetya Attack
The NotPetya ransomware attack in 2017 spread rapidly across the globe, affecting numerous businesses and government institutions. It targeted the accounting software used by many companies in Ukraine, but its effects rippled out to global companies with operations in the country. Multinational corporations such as Maersk, Merck, and FedEx were hit hard, leading to billions of dollars in damages and supply chain disruptions that lasted for weeks.
The NotPetya attack demonstrated how a cyber incident in one region can devastate global supply chains, especially if it involves commonly used software or infrastructure.
How to Secure Your Supply Chain
While supply chain attacks are rising, businesses can proactively mitigate these risks. Here are some best practices for securing your supply chain against cyber threats:
Conduct Comprehensive Risk Assessments
The first step to securing your supply chain is understanding where the vulnerabilities lie. Conduct a comprehensive risk assessment of your entire supply chain, from vendors to logistics providers to software partners. Identify the weakest links, whether they involve outdated systems, poor security protocols, or human error.
Once you understand your supply chain’s risk profile, you can take steps to address its weaknesses. This may involve upgrading technology, enforcing stricter security standards, or working closely with partners to improve their cybersecurity practices.
Implement Vendor Risk Management (VRM) Programs
A strong Vendor Risk Management (VRM) program is essential for identifying, assessing, and managing the risks associated with third-party vendors. Your VRM program should include:
- Due Diligence: Conduct thorough due diligence before entering into a partnership to ensure that vendors have robust cybersecurity measures.
- Security Audits: Regularly audit vendors to ensure compliance with your organization’s cybersecurity policies and industry standards.
- Continuous Monitoring: Monitoring tools track vendor activities and identify potential security issues in real-time.
Strengthen Communication with Suppliers
Open and transparent communication is key to supply chain security. Regularly engage with your suppliers to discuss potential cyber risks and collaborate on cybersecurity strategies. Please encourage them to implement stronger security measures and share relevant threat intelligence.
Establish clear guidelines for handling and transmitting sensitive data between your organization and your suppliers. Ensure that all parties involved understand the importance of protecting critical systems and information.
Segment Your Network
Network segmentation is a powerful tool for limiting the spread of cyberattacks within your supply chain. By dividing your network into smaller, isolated segments, you can prevent an attacker who gains access to one part of the system from moving laterally and compromising the entire network.
For example, if a vendor’s network is compromised, segmentation can contain the damage and prevent it from spreading to other critical systems.
Employ Advanced Threat Detection
Modern cyberattacks are increasingly sophisticated, making employing advanced threat detection systems essential. These systems use artificial intelligence (AI) and machine learning (ML) to identify anomalies, detect potential threats, and stop cybercriminals before they can cause damage.
Brandefense offers a comprehensive threat detection platform that monitors your digital ecosystem for signs of botnets, ransomware, phishing attacks, and other threats. Our AI-driven system can detect supply chain risks in real-time, allowing you to respond proactively and mitigate risks before they escalate.
Implement a Zero Trust Security Model
The zero-trust security model operates on the principle that no one should be trusted by default, whether inside or outside the organization. This approach assumes that every user, device, and application poses a potential threat and requires continuous authentication and validation to access sensitive resources.
By implementing Zero Trust, you can minimize the risk of cyberattacks infiltrating your supply chain through unauthorized access. Even if attackers gain access to one part of the supply chain, Zero Trust measures will prevent them from reaching critical assets.
How Brandefense Protects Your Supply Chain
Brandefense provides powerful tools to protect your supply chain from cyber threats. Our platform offers 360-degree visibility into your supply chain, allowing you to identify vulnerabilities and take proactive measures to secure your operations.
- Risk Assessment: We help businesses evaluate the cyber risks associated with their suppliers, partners, and vendors.
- Continuous Monitoring: Our platform continuously monitors the digital footprints of all your supply chain partners, identifying potential threats before they escalate.
- Threat Intelligence: We use real-time threat intelligence to provide insights to help businesses respond quickly to attacks.
- Advanced API Integration: Our system integrates with your existing cybersecurity tools, enhancing your ability to detect and respond to supply chain threats.
By partnering with Brandefense, you can strengthen your supply chain security, minimize risks, and protect your business.






