In today’s fast-paced digital landscape, the very survival of your business can hinge on one key factor: cybersecurity. With cyberattacks becoming increasingly sophisticated, traditional defense mechanisms are no longer sufficient. This is where Cyber Threat Intelligence (CTI) steps in. By providing actionable insights into malicious actors’ tactics, techniques, and procedures, CTI can differentiate between a minor security incident and a catastrophic breach. But what exactly is Cyber Threat Intelligence, and how can it save your business from falling prey to cybercriminals?
This blog explores how CTI works, its importance for modern businesses, and how leveraging platforms like Brandefense can protect your business from the evolving cyber threat landscape.
Understanding Cyber Threat Intelligence: What Is It?
At its core, Cyber Threat Intelligence is the collection, analysis, and use of information regarding current and emerging threats targeting an organization’s digital ecosystem. Unlike traditional reactive cybersecurity approaches, CTI is proactive, and it helps organizations anticipate potential cyber threats before they materialize. This allows businesses to bolster their defenses, reduce vulnerabilities, and prepare effective incident response plans.
CTI is often categorized into three main types:
Tactical Threat Intelligence
This type of intelligence focuses on specific threat actors’ tools, techniques, and procedures (TTPs). Organizations can strengthen their security measures against known threats by analyzing attackers’ patterns and behaviors.
- Purpose: Focuses on the attackers’ tactics, techniques, and procedures (TTPs) to give a detailed view of how attacks are likely to occur.
- Content: Explains specific attack methods, tools used by hackers, and behavioral patterns.
- Usage: Helps security teams implement specific countermeasures, such as configuring firewalls, deploying endpoint protection, or conducting incident response exercises.
- Sources: Incident reports, malware analysis, and cyber threat frameworks (like MITRE ATT&CK).
Tactical Threat Intelligence solves the issue of security teams not fully understanding how cyber attackers operate. This often results in ineffective defenses against specific attack techniques. Brandefense provides detailed insights into the tactics, techniques, and procedures (TTPs) of attackers, helping security teams develop targeted defenses against common attack methods such as phishing, malware, or ransomware.
Operational Threat Intelligence
Operational threat intelligence delivers insights into specific cyberattacks or campaigns targeting an organization. It provides real-time data on who is targeting your business, their methods, and how to defend against them.
- Purpose: Provides insights into cyber threats that are currently in play or imminent. It delivers actionable information about planned or ongoing attacks.
- Content: Includes details on attack campaigns, botnet activity, phishing attacks, and malware distribution.
- Usage: Helps organizations anticipate and mitigate active threats in real-time by adjusting security measures and defenses accordingly.
- Sources: Data from dark web monitoring, open-source intelligence (OSINT), and active threat feeds
Operational Threat Intelligence tackles the problem of delayed responses to real-time threats. Without real-time monitoring, organizations are vulnerable to active cyberattacks. Brandefense provides real-time threat detection and alerts, enabling security teams to respond instantly to ongoing threats, such as phishing campaigns or botnet activity, minimizing potential damage
Strategic Threat Intelligence
This high-level intelligence focuses on long-term trends in cybersecurity. It helps decision-makers understand the broader cyber threat landscape and align their security strategies accordingly. This type of intelligence is especially useful for C-suite executives and security leadership teams when making budgetary and policy decisions.
- Purpose: Provides high-level insights into the overall threat landscape, trends, and long-term risks. This type of intelligence is intended for senior leadership and decision-makers.
- Content: Includes geopolitical trends, motivations of attackers, the potential impact of cyber threats on business operations, and future predictions.
- Usage: Helps organizations align their cybersecurity strategies with business objectives and informs long-term planning.
- Sources: Government reports, security research, and industry white papers
Strategic Threat Intelligence addresses the problem of organizations lacking long-term awareness of emerging threats and cyber risks. Without this understanding, companies often fail to adapt their security strategies. Brandefense solves this by providing high-level insights into global threat trends, enabling businesses to align their cybersecurity strategies with potential future risks, ensuring long-term protection and resilience.
Why Cyber Threat Intelligence Is Critical for Your Business
Cyber Threat Intelligence is not just another buzzword; it’s an essential tool in modern cybersecurity. Here’s why:
Proactive Defense
Traditional cybersecurity tools often operate in a reactive mode, responding to threats after they occur. CTI flips this model on its head by enabling businesses to anticipate attacks before they happen. With advanced threat intelligence, you can stay one step ahead of cybercriminals by identifying vulnerabilities in your systems before they are exploited.
Minimize Financial and Reputational Damage
The financial and reputational costs of a cyberattack can be devastating. This kind of financial hit could be impossible for smaller businesses to recover from. By using CTI to prevent breaches or mitigate their impact, you can avoid the costly consequences of a successful attack.
Enhance Incident Response
How quickly and effectively you respond can make all the difference when a breach occurs. With CTI, your incident response team will have real-time, actionable intelligence to identify the threat, understand its impact, and respond accordingly. This can drastically reduce the time it takes to contain and eliminate the threat.
Informed Decision-Making
Cybersecurity budgets are finite, and allocating resources where they are needed most is crucial. CTI provides data-driven insights that help decision-makers understand which assets are most at risk, allowing for smarter investments in security measures.

Real-World Examples
Let’s examine some real-world examples of how Cyber Threat Intelligence played an important role in protecting businesses.
The SolarWinds Attack
The infamous SolarWinds attack in 2020 was a wake-up call for businesses worldwide. Hackers managed to infiltrate the IT management software company and insert malicious code into one of its routine software updates. This allowed the attackers to access the networks of numerous high-profile organizations, including government agencies and Fortune 500 companies.
While the initial attack went unnoticed, companies with robust CTI programs were able to detect suspicious activity early on. With actionable intelligence, these businesses mitigated the damage, isolated infected systems, and prevented the attackers from moving laterally within their networks.
The WannaCry Ransomware Attack
In 2017, the world witnessed one of the most widespread ransomware attacks in history:WannaCry. The ransomware infected over 200,000 computers across 150 countries, causing billions of dollars in damages. The attackers exploited a vulnerability in Microsoft Windows systems to spread the malware rapidly.
Organizations leveraging CTI received early warnings about the vulnerability and applied the necessary patches before the attack occurred. This proactive approach prevented ransomware from infiltrating their networks and saved them from significant financial and operational disruptions.
The NotPetya Cyber Attack
NotPetya, another global ransomware attack, occurred in 2017 and caused massive disruption across industries, from shipping to pharmaceuticals. The attack targeted companies using accounting software in Ukraine, but its impact spread worldwide.
Companies that had implemented CTI could detect anomalous network activity as the attack unfolded, allowing them to shut down infected systems and prevent further damage. By relying on real-time intelligence, these businesses were able to contain the attack quickly and minimize the fallout.
How Cyber Threat Intelligence Works: A Step-by-Step Breakdown
So, how exactly does CTI work? Let’s break down the process:
Data Collection
The first step in the CTI process is gathering data from various sources, including open-source intelligence (OSINT), proprietary threat databases, social media, and dark web forums. This data provides insights into emerging threats, malicious actors, and ongoing cyber campaigns.
Analysis
Once the data is collected, it’s analyzed to identify patterns, correlations, and anomalies. This is where the magic happens. Sophisticated algorithms and machine learning tools can sift through massive amounts of data to uncover valuable insights that would be impossible to detect manually.
Contextualization
Raw data alone is not enough to protect your business. CTI involves contextualizing the information to make it actionable. This means understanding the who, what, why, and how behind a cyber threat. For example, knowing that a specific type of malware is being used by a known threat actor targeting your industry allows you to prepare a targeted defense.
Dissemination
Once the intelligence has been analyzed and contextualized, it’s shared with relevant stakeholders, including security teams, C-suite executives, and third-party partners. This ensures that everyone involved in your organization’s cybersecurity efforts is equipped with the information they need to act.
Action
The final step is to take action. This could involve patching vulnerabilities, updating security policies, deploying new defensive measures, or launching an incident response plan. The key is to act on the intelligence quickly before the threat can escalate.
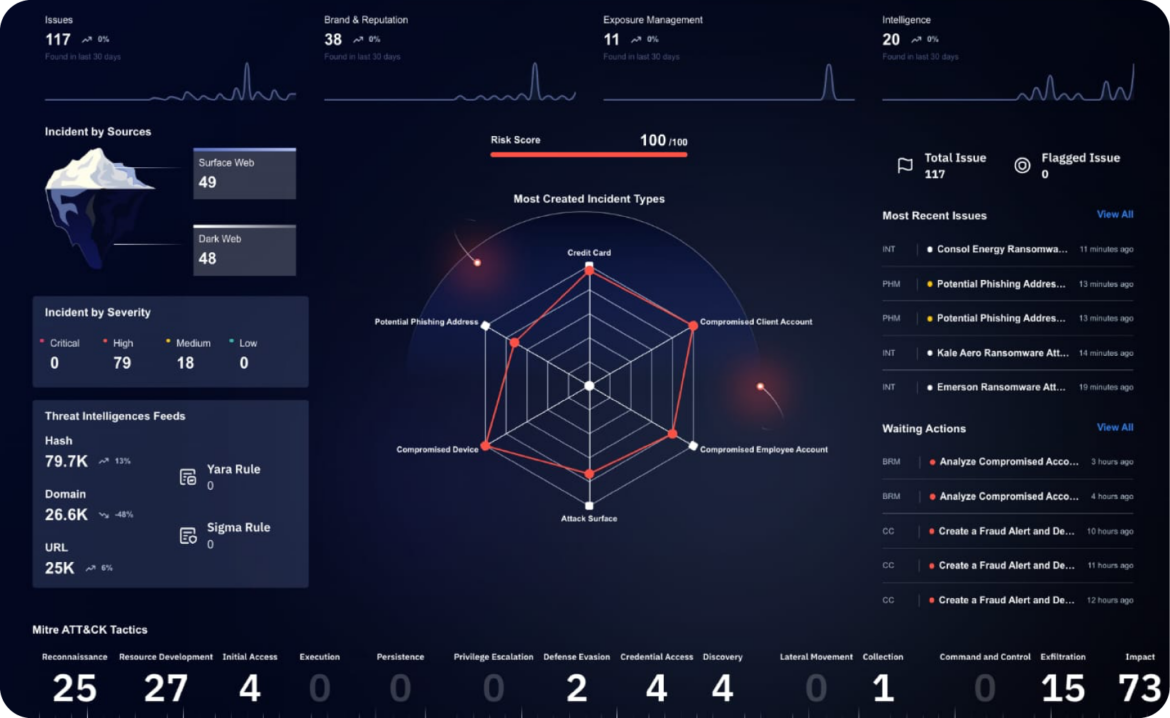
Key Benefits of Using Brandefense for CTI
Now that we’ve covered the basics of CTI let’s explore how Brandefense can help your business harness the power of threat intelligence to stay secure in an increasingly dangerous digital landscape.
360° Visibility
Brandefense offers comprehensive visibility into your organization’s attack surface, providing real-time intelligence on threats targeting your business. Our platform scans the surface, deep, and dark web to identify vulnerabilities and potential attack vectors before they can be exploited.
AI-Driven Threat Detection
Using advanced AI algorithms, Brandefense can detect emerging threats and provide real-time actionable insights. Our platform monitors new threats and updates its database to ensure you’re always ahead of cybercriminals.
Customized Threat Intelligence
Not all businesses face the same cyber threats. Brandefense tailors its CTI solutions to meet your organization’s specific needs. Whether you’re a small business or a multinational corporation, we’ll help you identify the most relevant threats and develop a customized defense strategy.
False Positive Elimination
One of the biggest challenges in cybersecurity is the overwhelming number of false positives generated by security systems. Brandefense eliminates false positives by providing highly accurate intelligence, allowing your security teams to focus on genuine threats.
Continuous Monitoring
Cyber threats are constantly evolving, and so should your defenses. Brandefense provides continuous monitoring to ensure that your business is protected 24/7. Our platform identifies new vulnerabilities, tracks changes in the threat landscape, and alerts you to potential risks in real-time.
Conclusion: The Future of Cyber Threat Intelligence
As cyber threats evolve, businesses can no longer afford to rely on outdated security measures. Cyber Threat Intelligence is the key to staying ahead of cybercriminals and protecting your business from costly breaches.
The future of cyber threat intelligence will be defined by advanced AI, machine learning, and automated response systems capable of identifying and neutralizing threats in real time. The rise of quantum computing will further challenge traditional encryption methods, making quantum-resistant security crucial. Cross-industry collaboration, threat-sharing platforms, and decentralized intelligence networks will be critical in anticipating new attack vectors. Organizations will need to embrace predictive analytics and behavioral threat modeling to stay one step ahead, while regulatory bodies will push for stricter data privacy and cybersecurity laws. The future will demand a shift from reactive to proactive threat defense strategies, transforming how we secure the digital world.





