Organizations face increasingly sophisticated cyber threats. Developing cyber resilience is essential to ensuring business continuity, safeguarding sensitive data, and mitigating potential damages caused by cyberattacks. This article explores key strategies to strengthen cyber resilience and effectively navigate complex threats.
What is Cyber Resilience, and Why is it Essential?
Cyber resilience is an organization’s ability to anticipate, recover from, and adapt to cyber threats while ensuring business operations continue with minimal disruption. It goes beyond traditional cybersecurity, which primarily focuses on preventing attacks, by emphasizing the importance of resilience in the face of inevitable breaches. Cyber threats like ransomware and data breaches are growing in sophistication, making it nearly impossible for businesses to guarantee complete protection. However, organizations that invest in robust business continuity planning and incident response strategies can minimize financial losses, prevent reputational damage, and ensure regulatory compliance even when attacks occur.
Cyber resilience is no longer optional but necessary in an increasingly digital world. The global shift toward cloud computing, IoT devices, and remote work environments has expanded the attack surface, increasing the likelihood of cyber incidents. Organizations risk prolonged downtimes, disrupted services, and significant financial repercussions without a comprehensive cyber resilience framework. Furthermore, compliance regulations such as GDPR, HIPAA, and NIST demand that businesses maintain high data security and recovery readiness standards. Companies that proactively build cyber resilience can protect their assets and gain a competitive advantage by fostering trust among customers and stakeholders.
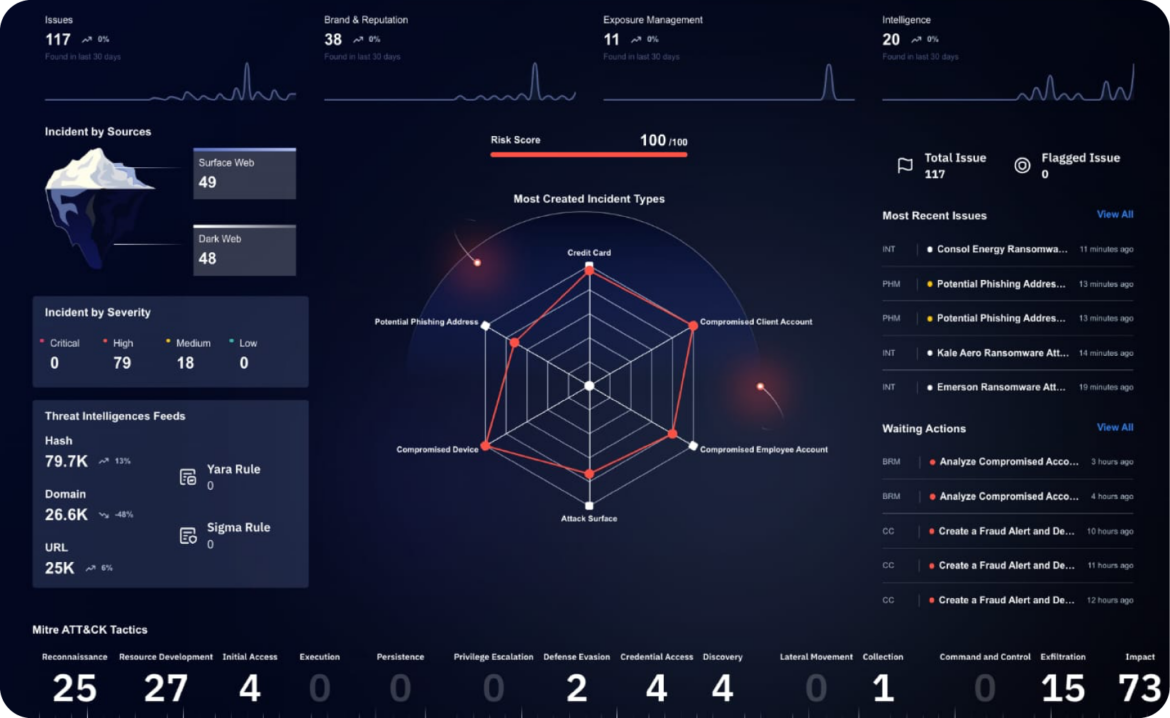
How to Develop a Robust Cyber Resilience Strategy
Establishing a cyber resilience strategy involves more than just deploying the latest security tools—it requires a proactive, multi-layered approach that integrates technology, processes, and people. One of the first steps in building resilience is conducting thorough risk assessments to identify vulnerabilities and prioritize security investments. Organizations should evaluate their security posture, assess potential attack vectors, and determine the most critical assets requiring protection. This helps create a tailored strategy that addresses the business’s unique risks.
Beyond risk assessments, companies must combine technical controls and organizational policies to strengthen cyber resilience. Implementing multi-factor authentication and strong access controls can significantly reduce unauthorized access. Regular training on phishing detection, password management, and safe browsing practices can prevent breaches caused by human error. AI-driven security tools can detect anomalies and automate threat mitigation, providing an added layer of protection. In addition, establishing a robust incident response plan ensures that teams can act swiftly and virtually during an attack, minimizing downtime and damage.
Organizations should continuously test and refine their cyber resilience strategies through simulated attacks, penetration testing, and ongoing security audits. By integrating security best practices across all business functions, companies can build a more resilient infrastructure capable of withstanding even the most sophisticated threats.
The Role of Incident Response and Business Continuity Planning
A comprehensive incident response plan is very important for mitigating the impact of cyber incidents. Organizations should establish a well-defined response framework that outlines how to detect, contain, investigate, and recover from cyber threats. This plan should include designated response teams with clear roles and responsibilities, ensuring key personnel can act swiftly during an attack. By implementing structured communication protocols, businesses can prevent misinformation and efficiently coordinate with stakeholders, regulators, and law enforcement.
Beyond incident response, a strong business continuity planning (BCP) framework is essential to ensure uninterrupted operations even during cyber crises. BCP involves identifying mission-critical functions, creating contingency plans, and implementing disaster recovery mechanisms. Organizations should maintain regularly updated backups, preferably in cloud environments, to facilitate rapid data restoration during ransomware attacks or system failures. Testing these plans through tabletop exercises and simulated breach scenarios helps ensure their effectiveness in real-world situations.
By combining robust incident response and business continuity planning, companies can create a security-first culture prioritizing resilience. The faster an organization can detect and neutralize a cyber threat, the less impact it will have on business operations, reputation, and financial stability.
Leveraging AI and Automation for Stronger Cyber Resilience
Artificial intelligence and automation play a crucial role in strengthening cyber resilience. AI-driven security tools enhance threat detection, automate incident responses, and analyze patterns to predict potential attacks. With real-time threat monitoring, organizations can identify vulnerabilities before they are exploited. AI-powered security solutions enable automated response mechanisms that neutralize threats instantly, reducing the risk of prolonged exposure. By leveraging machine learning and behavioral analytics, companies can proactively detect anomalies and prevent cyber threats from escalating into major security incidents.
Automation also reduces human error, which remains one of the leading causes of security breaches. Manual security operations can be prone to oversight and delays, whereas automated systems ensure continuous monitoring and rapid incident response. Additionally, AI-driven tools help streamline compliance efforts by maintaining detailed logs and reports for auditing purposes. Organizations incorporating AI and automation into their cybersecurity frameworks can enhance their security posture, reduce response times, and improve overall resilience against cyberattacks.
Case Studies: Organizations that Successfully Navigated Cyber Attacks
Several organizations have successfully navigated cyber threats through proactive cyber resilience measures. A leading financial institution was able to thwart a ransomware attack using AI-driven threat detection and rapid incident response. By continuously monitoring its network for suspicious activity, the organization identified and isolated the threat before it could spread, preventing a potential data breach and financial loss.
An e-commerce company also demonstrated cyber resilience by minimizing downtime after a large-scale DDoS attack. The company redirected traffic through a distributed denial-of-service mitigation solution by activating its business continuity plan, ensuring its online platform remained operational. Leveraging cloud-based security solutions further helped the organization distribute network loads and maintain service availability despite the attack.
A provider successfully mitigated a data breach in the healthcare sector by implementing strong access controls and real-time monitoring tools. The security team immediately revoked access when unauthorized access was detected, preventing sensitive patient data from being compromised. Through continuous security training and investment in advanced cybersecurity tools, the healthcare provider was able to respond effectively and strengthen its defense against future threats.
These examples highlight the importance of adopting comprehensive cyber resilience strategies to safeguard critical assets and maintain business operations. Organizations must remain vigilant, proactive, and adaptable to emerging cyber risks in today’s evolving threat landscape. By prioritizing cyber resilience, businesses can protect themselves from financial and reputational damage and gain a strategic advantage in an increasingly digital world.






