The incident response aims to detect, contain, and resolve security incidents as quickly and efficiently as possible while minimizing damage and restoring normal business operations.
This blog will cover the basics of incident response and discuss how to build an effective incident response plan for your organization.
What Is Incident Response?
Incident response is a systematic approach to addressing security incidents in an organization. It involves a coordinated effort between various teams to quickly and efficiently identify and respond to security incidents, including security, IT, legal, and business units.
IR process typically involves six stages: preparation, identification, containment, eradication, recovery, and lessons learned. Each step is critical to the overall success of incident response, and failure to effectively execute any of these stages can significantly damage an organization.
How Incident Response Works?
The incident response process starts with preparation. This involves developing an incident response plan (IRP) that outlines the roles and responsibilities of each team member, defines the types of security incidents that could occur, and establishes the procedures for detecting, containing, and resolving these incidents.
Once the IRP is in place, the identification stage begins. This stage involves identifying potential security incidents through a combination of proactive monitoring and reactive reporting. Proactive monitoring involves using security technologies, such as intrusion detection systems (IDS) and security information and event management (SIEM) tools, to detect potential security incidents before they escalate. Reactive reporting involves employees reporting suspicious activity or security incidents they have observed.
After a potential security incident has been identified, the containment stage begins. This stage involves taking immediate action to contain the incident and prevent it from spreading. This may include isolating affected systems or networks, shutting down systems, or disconnecting from the internet.
Once the incident has been contained, the eradication stage begins. This involves identifying the root cause of the incident and taking steps to eliminate it. This may involve restoring data from backups, patching vulnerabilities, or removing malware.
The recovery stage involves restoring normal business operations as quickly as possible. This may involve restoring data from backups, reconfiguring systems, or rebuilding infrastructure.
Finally, the lessons learned stage involves reviewing the incident response process to identify areas for improvement. This may include updating the IRP, providing additional training for employees, or implementing new security technologies.
Incident Response Technologies
Incident Response Technologies (IRT) are a set of security solutions designed to help organizations respond to and manage unexpected events or emergencies. These events can range from cyber-attacks and data breaches to natural disasters and workplace accidents.
IRT solutions provide a streamlined, organized approach to incident response, helping teams to quickly identify and assess the situation, mobilize resources and personnel, and communicate effectively with stakeholders. In this section, we will discuss in detail what Incident Response Technologies are and what security solutions it includes.
What Are Incident Response Technologies?
Incident Response Technologies, also known as Incident Management Software, are software solutions designed to help organizations respond to unexpected incidents in a structured and efficient way. These technologies provide automated alerts and notifications, real-time incident tracking, integrated communication tools, and customizable response workflows to help teams respond quickly and effectively.
Incident Response Technologies are used by organizations to improve their incident response capabilities, reduce the impact of unexpected events on their operations, reputation, and bottom line, and improve their overall security posture.
There are several security solutions included in IRT, each serving a specific purpose in the incident response process.
Alerting and Notification Systems
Alerting and notification systems are one of key components of Incident Response Technologies. These systems provide real-time notifications to security teams when an incident occurs, allowing them to respond quickly and take action.
Alerting and notification systems can be customized to fit the specific needs of an organization, allowing teams to receive notifications via email, text messages, or other preferred communication channels. To illustrate for Alerting and Notification Systems; Everbridge Mass Notification, OnPage, and OnSolve Emergency/Mass Notification Services.
Incident Tracking and Management
Incident tracking and management systems are used to manage the incident response process from start to finish. These systems provide a centralized platform for tracking incidents, assigning tasks, and monitoring progress. They also provide a comprehensive view of the incident, allowing teams to identify the root cause of the incident and take appropriate action to prevent it from happening again.
Communication and Collaboration Tools
Effective communication is critical during an incident response. Communication and collaboration tools are included in Incident Response Technologies to help teams communicate and collaborate effectively. These tools allow teams to communicate in real-time, share information, and collaborate on tasks. They also provide a centralized platform for storing information, making it easily accessible to all members of the incident response team.
Threat Intelligence
Threat intelligence is the process of gathering, analyzing, and sharing information about potential threats to an organization. Incident Response Technologies include threat intelligence capabilities to help organizations proactively identify potential threats and take action to prevent them. Threat intelligence can also be used to identify patterns in attacks, allowing organizations to improve their incident response capabilities over time.
Forensic Analysis
Forensic analysis is the process of analyzing digital evidence to identify the root cause of an incident. Incident Response Technologies include forensic analysis capabilities to help organizations identify the source of an incident and take appropriate action. Forensic analysis can also identify vulnerabilities in an organization’s security posture, allowing them to take action to prevent future incidents.
Automation and Orchestration
Automation and orchestration capabilities are included in Incident Response Technologies to help organizations respond to incidents quickly and efficiently. These capabilities automate routine tasks, allowing incident response teams to focus on higher-level tasks. They also orchestrate the incident response process, ensuring that all jobs are completed in the correct order and in a timely manner.
Commonly used solutions in the Incident Response process are:
- Intrusion Detection Systems (IDS)
- Security Information and Event Management (SIEM) tools
- Endpoint Detection and Response (EDR) tools
- Network traffic analysis tools
- Incident response automation and orchestration tools
These solutions can help organizations detect security incidents more quickly, contain them more effectively, and respond more efficiently.
What Are Security Incidents?
Security incidents are any event that poses a threat to the confidentiality, integrity, or availability of an organization’s data or systems. Some common security incidents include:
- Malware infections
- Network intrusions
- Denial of Service (DoS) attacks
- Phishing attacks
- Insider threats
- Physical security breaches
Each of these incidents can significantly impact an organization’s operations and reputation.
Types of Security Incidents
There are many different types of security incidents that organizations may face. Some common types of security incidents include:
- Data breaches
- Ransomware attacks
- Advanced Persistent Threat (APT) attacks
- Distributed Denial of Service (DDoS) attacks
- Social engineering attacks
- Insider attacks
Each type of incident requires a unique response, and it’s important for organizations to be prepared for a variety of different scenarios.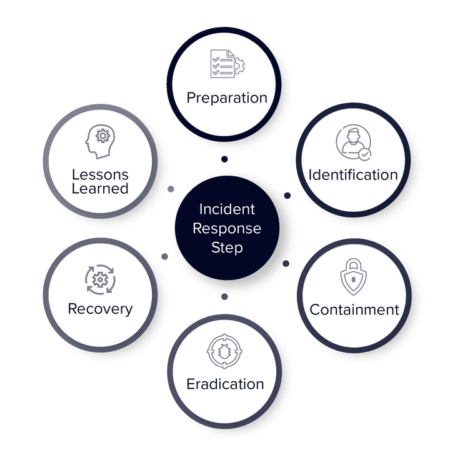
Effective Incident Response Steps
The effective incident response involves a series of coordinated steps designed to quickly and efficiently detect, contain, and resolve security incidents. These steps include:
- Preparation
Developing an incident response plan (IRP) that outlines the roles and responsibilities of each team member, defines the types of security incidents that could occur, and establishes the procedures for detecting, containing, and resolving these incidents.
- Identification
We are identifying potential security incidents through proactive monitoring and reactive reporting.
- Containment
Taking immediate action to contain the incident and prevent it from spreading.
- Eradication
It is identifying the incident’s root cause and taking steps to eliminate it.
- Recovery
Restoring normal business operations as quickly as possible.
- Lessons Learned
The “lessons learned” phase of IR involves a thorough review of the process to identify opportunities for improvement. This could include updating the incident response plan (IRP), providing further training for personnel, or implementing new security technologies. By analyzing the response to the incident, organizations can strengthen their defenses and enhance their ability to handle future security incidents.
By following these steps, organizations can minimize the impact of security incidents and restore normal operations more quickly.
Brandefense & Incident Response
Brandefense is a digital risk protection solution (DPRS) that helps organizations proactively safeguard their online presence. It constantly scans the online world, including the surface, deep, and dark web, to detect unknown events and prioritize real-time risks.
With Brandefense, organizations gain access to actionable intelligence that can be used to improve their security posture immediately. The solution provides an automated risk-scoring system highlighting critical issues and presenting relevant information to security and incident response teams. This allows them to quickly and efficiently identify potential threats and take proactive steps to mitigate them. By scanning the dark and deep web, Brandefense can detect potential threats that may not be visible through traditional security measures.






