Fraud is a pervasive threat that impacts businesses of all sizes and industries. As digital transactions and online activities continue to grow, so do the opportunities for fraudsters to exploit vulnerabilities. To safeguard their operations, assets, and reputations, businesses must implement comprehensive fraud protection solutions. This blog explores the key components of effective fraud protection and provides actionable steps for businesses to build robust defenses against fraudulent activities.
Importance of Fraud Protection
Fraud can take many forms, including identity theft, payment fraud, account takeover, and phishing. The consequences of falling victim to fraud can be severe, leading to financial losses, legal liabilities, and reputational damage. For businesses, the stakes are even higher, as fraud can erode customer trust, disrupt operations, and result in regulatory penalties.
Comprehensive fraud protection is essential for mitigating these risks and ensuring the long-term success of a business. By implementing a holistic approach that combines technology, processes, and employee training, businesses can detect, prevent, and respond to fraudulent activities effectively.
Key Components of Comprehensive Fraud Protection Solutions
Effective VIP security requires a multi-layered approach that integrates various security measures and technologies. Here are the key components of a robust VIP security strategy:
Identity Verification
Identity verification is the process of confirming that a person or entity is who they claim to be. This is a critical first step in preventing fraud, as it helps to ensure that only legitimate customers and partners can access services or complete transactions. Key identity verification methods include:
- Multi-Factor Authentication (MFA): Requiring users to provide multiple forms of identification, such as a password and a fingerprint, to verify their identity.
- Document Verification: Using software to scan and validate government-issued IDs, passports, or other official documents.
- Biometric Verification: Leveraging biometric data, such as facial recognition or fingerprint scanning, to confirm a user’s identity.
By implementing robust identity verification measures, businesses can reduce the risk of fraudsters using stolen or fake identities to gain unauthorized access.
Transaction Monitoring
Transaction monitoring involves continuously analyzing transactions for signs of suspicious or fraudulent activity. By monitoring transactions in real-time, businesses can detect and respond to potential fraud before it causes significant damage. Key features of transaction monitoring include:
- Rule-Based Monitoring: Setting up rules and thresholds that trigger alerts when certain conditions are met, such as unusually large transactions or transactions from high-risk locations.
- Behavioral Analysis: Using machine learning algorithms to analyze transaction patterns and detect anomalies that may indicate fraud.
- Risk Scoring: Assigning a risk score to each transaction based on factors such as the transaction amount, location, and user behavior. Transactions with high-risk scores can be flagged for further investigation.
Effective transaction monitoring enables businesses to detect fraud in real-time, allowing them to take immediate action to prevent losses.
Payment Security
Payment security is crucial for protecting against payment fraud, including credit card fraud, account takeover, and unauthorized transactions. Key payment security measures include:
- Encryption: Encrypting payment data both in transit and at rest to protect it from interception or unauthorized access.
- Tokenization: Replacing sensitive payment information, such as credit card numbers, with a unique token that can only be used by authorized parties.
- 3D Secure Authentication: Implementing 3D Secure (3DS) protocols to add an extra layer of authentication for online payments, requiring users to enter a one-time password or biometric verification.
- PCI DSS Compliance: Adhering to the Payment Card Industry Data Security Standard (PCI DSS) to ensure that payment processing systems meet stringent security requirements.
By implementing these payment security measures, businesses can protect their customers’ payment data and reduce the risk of payment fraud.
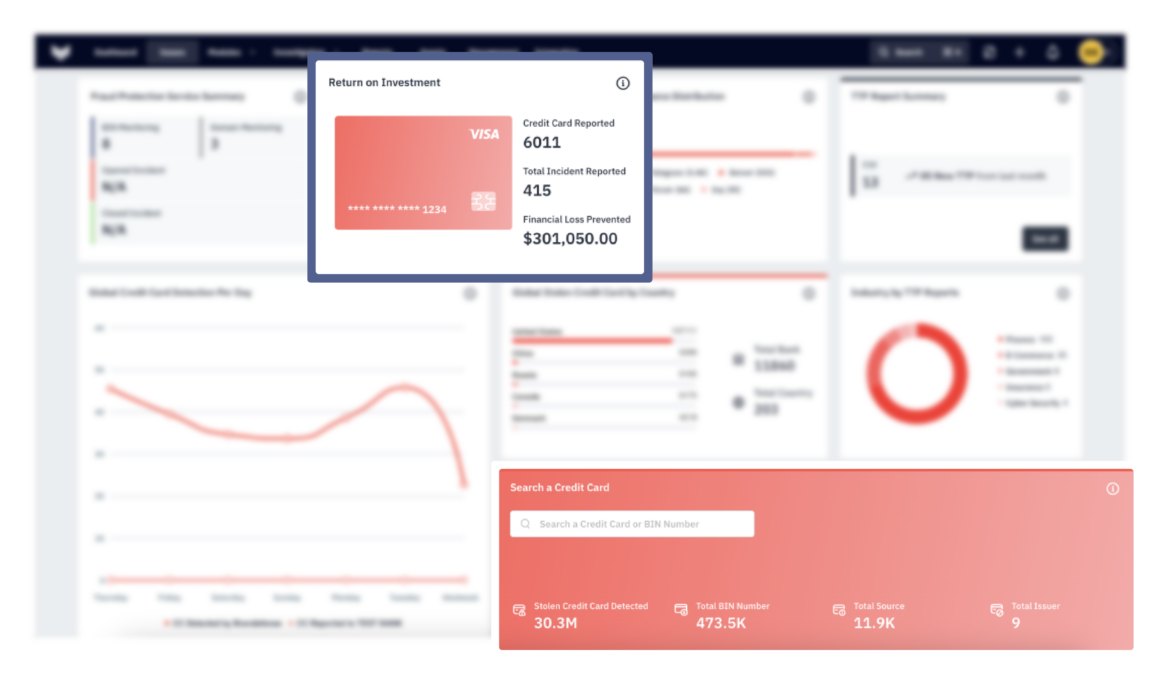
Fraud Detection and Prevention Tools
Advanced fraud detection and prevention tools are essential for identifying and stopping fraudulent activities before they can cause harm. These tools leverage machine learning, artificial intelligence, and big data analytics to detect patterns and anomalies that may indicate fraud. Key fraud detection tools include:
- AI-Powered Analytics: Using artificial intelligence to analyze vast amounts of data and identify suspicious patterns or behaviors that may indicate fraud.
- Real-Time Alerts: Generating alerts in real-time when potential fraud is detected, allowing security teams to respond quickly.
- Case Management Systems: Providing a centralized platform for investigating and managing fraud cases, tracking the progress of investigations, and documenting outcomes.
- Fraud Scoring Models: Assigning a fraud score to users, transactions, or accounts based on their risk profile, helping businesses prioritize investigations and responses.
These tools enable businesses to proactively detect and prevent fraud, reducing the likelihood of significant financial losses.
Employee Training and Awareness
Human error is a common factor in many fraud incidents. Employees may inadvertently click on phishing links, share sensitive information, or fall for social engineering attacks. To mitigate these risks, businesses must invest in employee training and awareness programs. Key training initiatives include:
- Phishing Simulations: Conducting regular phishing simulations to educate employees on how to recognize and avoid phishing attempts.
- Security Awareness Training: Providing ongoing training on the latest fraud tactics, common scams, and best practices for maintaining security.
- Incident Reporting Procedures: Establishing clear procedures for reporting suspicious activities or potential fraud incidents, ensuring that employees know how to act quickly and appropriately.
- Role-Specific Training: Tailoring training programs to the specific roles and responsibilities of employees, ensuring that those in high-risk positions receive specialized training.
By educating employees on the importance of security and fraud prevention, businesses can create a culture of vigilance and reduce the risk of insider threats.
Customer Education and Communication
Customer education is also a critical component of fraud protection. By informing customers about the risks of fraud and providing them with tips on how to protect themselves, businesses can reduce the likelihood of customers falling victim to scams. Key customer education initiatives include:
- Fraud Awareness Campaigns: Launching awareness campaigns to educate customers about common fraud tactics, such as phishing, vishing, and smishing.
- Secure Communication Channels: Encouraging customers to use secure communication channels, such as encrypted messaging apps, when interacting with the business.
- Account Monitoring: Advising customers to monitor their accounts regularly for suspicious activity and to report any unauthorized transactions immediately.
- Strong Password Practices: Educating customers on the importance of using strong, unique passwords and enabling MFA for their accounts.
By empowering customers with knowledge and tools to protect themselves, businesses can reduce the overall risk of fraud and build trust with their customer base.

Implementing a Comprehensive Fraud Protection Strategy
To implement a comprehensive fraud protection strategy, businesses should take the following steps:
Conduct a Fraud Risk Assessment
The first step in implementing a fraud protection strategy is to conduct a fraud risk assessment. This involves identifying potential fraud risks specific to the business, such as the types of fraud most likely to occur and the areas of the business most vulnerable to fraud. Based on the assessment, businesses can prioritize their fraud protection efforts and allocate resources accordingly.
Develop and Implement Fraud Policies
Businesses should develop clear fraud policies that outline the procedures for detecting, preventing, and responding to fraud. These policies should be communicated to all employees and stakeholders, and regular training should be provided to ensure compliance. Fraud policies should also include guidelines for reporting fraud incidents and the steps to be taken in the event of a fraud investigation.
Invest in Fraud Detection and Prevention Technologies
Investing in advanced fraud detection and prevention technologies is essential for staying ahead of evolving fraud tactics. Businesses should evaluate and select the right tools and technologies that align with their specific needs and risk profile. This may include AI-powered analytics, real-time monitoring systems, and fraud scoring models.
Monitor and Review Fraud Protection Measures
Fraud protection is an ongoing process that requires continuous monitoring and review. Businesses should regularly assess the effectiveness of their fraud protection measures and make adjustments as needed. This includes reviewing transaction monitoring data, updating fraud policies, and conducting regular audits to identify any gaps or weaknesses in the fraud protection strategy.
Foster a Culture of Fraud Awareness
Finally, businesses should foster a culture of fraud awareness across the organization. This includes encouraging employees to report suspicious activities, rewarding proactive fraud prevention efforts, and maintaining open communication about the importance of security. By creating a fraud-aware culture, businesses can enhance their overall security posture and reduce the risk of fraud.
Conclusion
In an era where fraud is a constant threat, businesses must implement comprehensive fraud protection solutions to safeguard their operations, assets, and reputations. By combining identity verification, transaction monitoring, payment security, fraud detection tools, employee training, and customer education, businesses can build robust defenses against fraudulent activities. Through proactive risk assessment, investment in advanced technologies, and fostering a culture of vigilance, businesses can reduce the risk of fraud and ensure their long-term success.






