What is Phishing?
Cyber attacks and threats are constantly evolving, so all potential threats must be addressed and patched quickly. For example, phishing is one of the most common social engineering attacks. In a phishing attack, the attacker tries to send fraudulent messages to the users present in the company to try to trick the person into revealing confidential information about the organization or to gain access within the organization.
In a phishing attack, the attacker masks itself into an entity that the user can trust and enter his credentials so that the attacker can steal the user data. The process of a phishing attack occurs by sending the recipient of an organization a malicious link. When the link is accessed or opened, it may start a download of malware, or the link would present itself as a trusted entity, i.e., a login form of a website which would trick the user into entering his credentials, which the attacker would steal to gain remote access of the system.
A successful phishing attack can have catastrophic results, and it may result in gaining unauthorized access to the system and making purchases or funds transfers of the account. Furthermore, it can be used for performing an identity theft of an employee within an organization, escalating the privileges, and executing a malicious payload that could potentially destroy the system.
Phishing Monitoring
Phishing protection and monitoring are a part of the organizational cybersecurity support program that would enable the company to prevent cyber attackers from potentially gaining access to a system and stealing sensitive information. Phishing monitoring is a service that is solely dedicated to providing protection against malicious and flagged links and emails and helping the organization by catching and filtering the link.
The most common way of a phishing link to gain unnoticed access to the system is through the email service, as several emails are generated every day; the overwhelming quantity of the emails can easily bypass a user. Due to this reason, companies rely on external phishing monitoring services for filtering such links and protection against accidental clicking and opening of these URLs.
Importance of Phishing Monitoring
A phishing monitoring program must be deployed within an organization as it would help in limiting the number of malicious requests and links by filtering the already flagged emails and URLs and reducing the possibility of a successful phishing attack.
In many cases, whenever a phishing URL is clicked and opened, it goes unnoticed, and the user might trigger an event that would lead to a chain of events triggering a malicious download. In this case, if a monitoring service is effective, it would generate an alert for the download, which can later be resolved by the user.
Hosting webpages of legitimate sites on fake URLs and then spreading the fake URL through email is one of the most common types of phishing attacks. A phishing monitoring service would detect the domain name of these phishing links and resolve the IP address to reveal the subdomain network, and after comparing the popularity of the subdomain, these monitoring tools would classify the email as spam.
The number of phishing emails that are currently generated is very high. The analysis of these email messages cannot be done using human intellect. Phishing monitoring service allows automated protection against such threats. In many cases, a report mail is set up which would flag similar emails, and if multiple malicious reports of a similar mail are generated, the email would be permanently marked as flagged.
It is important to conduct a manual phishing monitoring analysis as well. It would allow the analyst to classify the dangers of the incident and separate the emails that have been flagged to analyze the potential threats. Once the email has been identified to have an association with a phishing link, the domain, and the malicious URL would be blocked, and the mail would be classified as spam.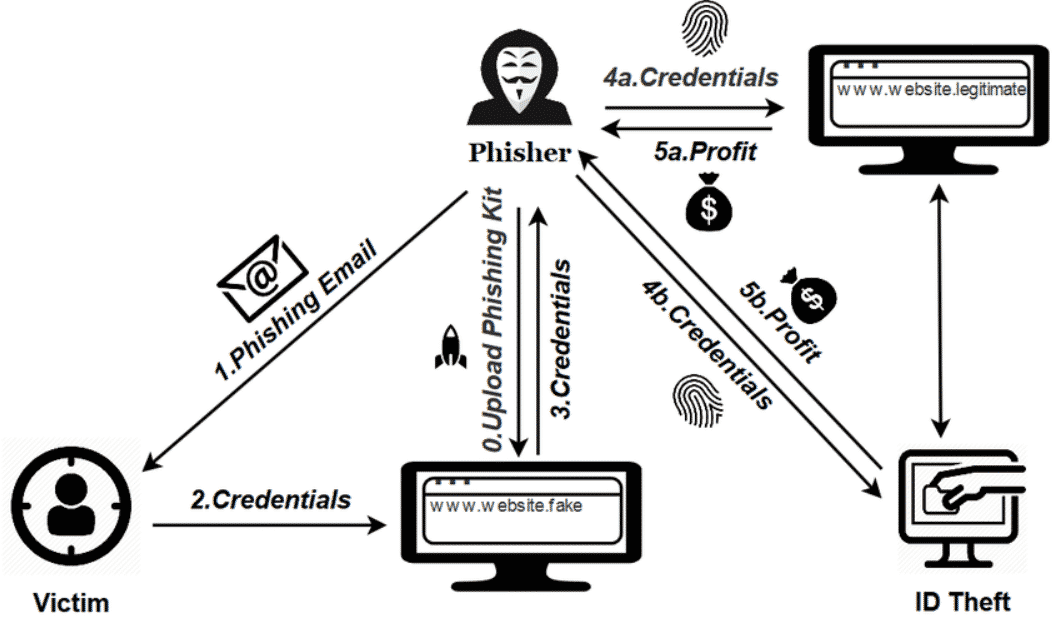
How Does BRANDEFENSE Protect Your Company From Phishing Attacks?
BRANDEFENSE Fraud Protection is a service that helps businesses to protect themselves from phishing attacks, cyber espionage, and more. We provide a range of tools and services to help businesses to stay safe, including:
- A cyber security assessment: This helps businesses to identify any weak spots in their cyber security.
- A fraud detection service: This helps businesses to detect and prevent digital fraud.
- A data breach response service: This helps businesses to deal with the fallout from a data breach.
For BRANDEFENSE Fraud Protection offers and more, contact us for a free demo.






