As we transition into 2025, the lessons and advancements of 2024 provide a strong foundation for navigating an increasingly complex cybersecurity landscape. Organizations have recognized the need for a strategic approach to security investments, ensuring that resources are allocated to technologies and practices that deliver the greatest impact. Businesses can strengthen their defenses while managing costs effectively by prioritizing AI-driven solutions, proactive risk management, and social optimization. Success in 2025 will depend on leveraging these key insights to build a resilient security posture that addresses current and emerging threats.
Cost-Effective Cybersecurity: Prioritizing Investments
As the digital threat landscape grows increasingly complex, organizations are under constant pressure to maximize the impact of their cybersecurity budgets. Adopting a cost-effective cybersecurity approach involves more than just cutting costs; it requires strategic planning and a deep understanding of risk profiles. Organizations must identify their most vulnerable assets and allocate resources toward securing them, ensuring that high-priority areas such as endpoint protection, automated threat remediation, and real-time monitoring receive the attention they deserve. Advanced tools and platforms designed to detect and neutralize threats early in their lifecycle are critical for achieving robust defenses without unnecessary expenses.
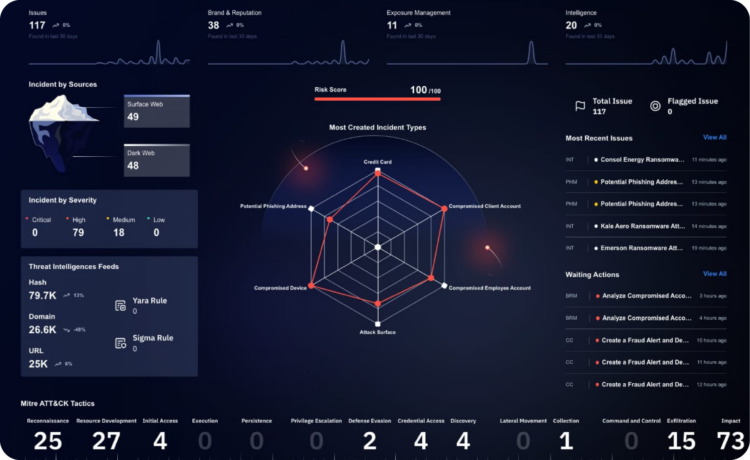
Comprehensive cyber threat intelligence feeds are one of the most impactful strategies for achieving cost-efficiency. These solutions provide actionable insights into emerging risks, enabling organizations to anticipate and neutralize threats before they escalate. Integrating such feeds with existing systems ensures seamless operations, reducing redundancies and allowing security teams to operate more efficiently. Moreover, optimizing Security Operations Centers (SOC) by leveraging AI-driven tools and automation further enhances resource allocation. These methods ensure that every dollar invested in cybersecurity contributes directly to building a resilient and adaptable defense framework capable of meeting current and future challenges.
AI-Driven Solutions for Streamlined Threat Detection
Integrating AI-driven solutions into cybersecurity operations marks a transformative shift in how organizations detect and respond to threats. By utilizing artificial intelligence, businesses can analyze vast volumes of data in real-time, uncovering subtle patterns and anomalies that traditional systems might overlook. These insights empower security teams to act quickly and decisively, often neutralizing risks before they materialize into significant incidents. AI technologies are particularly adept at identifying complex attack vectors and correlating data points across different systems, making them indispensable in the modern security landscape.
In addition to enhancing threat detection accuracy, AI-driven tools significantly reduce the burden on human analysts. These solutions can filter out low-priority alerts, allowing security teams to concentrate on addressing genuine risks. Integrating AI into proactive risk management strategies ensures vulnerabilities are identified and mitigated before attackers can exploit them. Furthermore, AI’s ability to learn from new information makes it essential to any forward-thinking cybersecurity strategy. Investing in these technologies streamlines threat detection and provides long-term value by enabling organizations to stay ahead of evolving cyber threats.
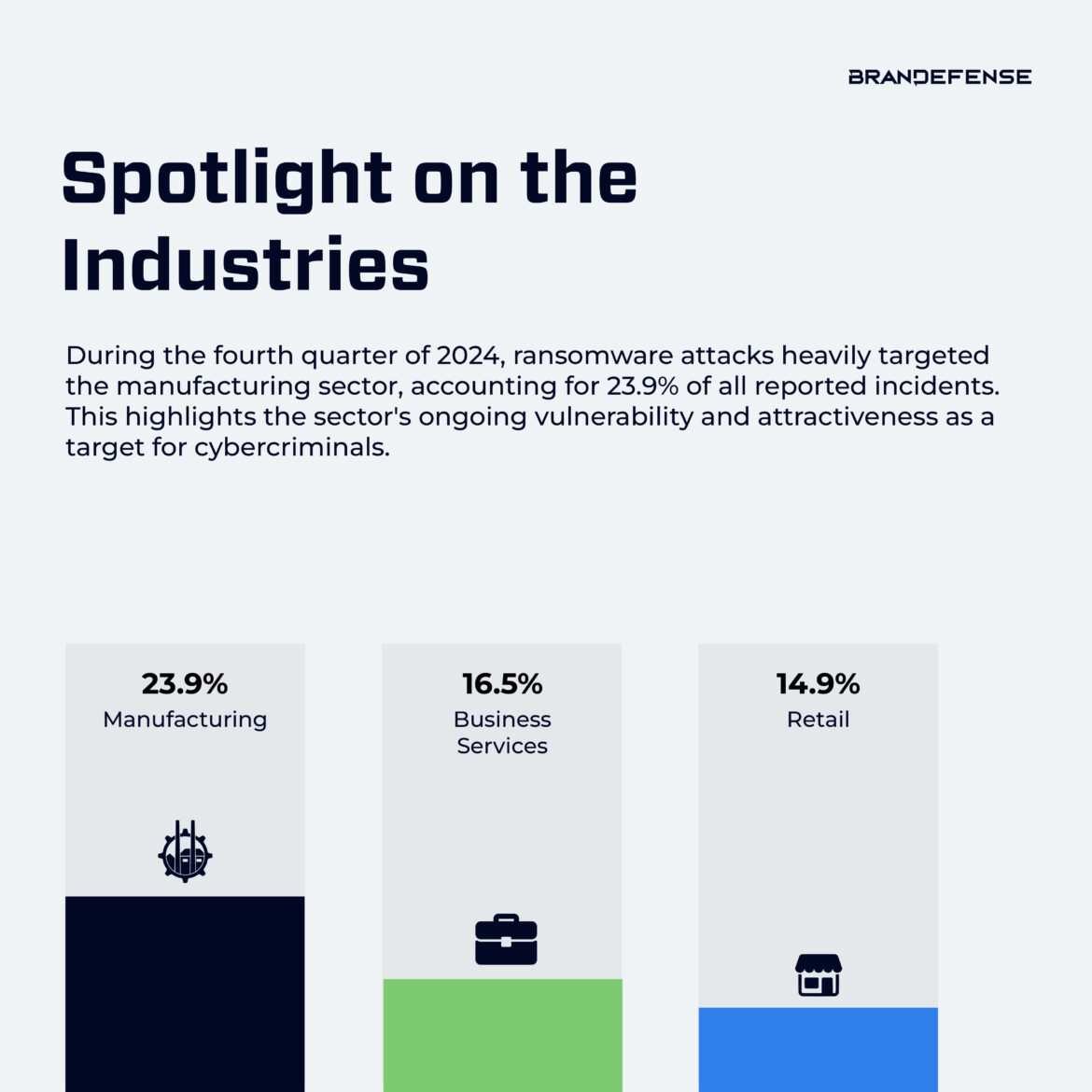
The Q4 2024 Ransomware Trends Report highlights a surge in global ransomware activity, with notable increases in attacks on critical industries and a shift in prominent threat actors.
In preparing this report, the primary focus has been on meticulously analyzing the attacks carried out by various cybercriminal groups, which have been under close surveillance by our analysts from October to December. Within this scope, an attempt has been made to meticulously derive the 3-month trends of the attacking groups, taking into account various factors such as the countries targeted, the industries affected, the ransom amounts demanded, and the annual revenue of the targeted companies.
To gain more details, Download the Report
Vendor Risk Management in a Complex Digital Ecosystem
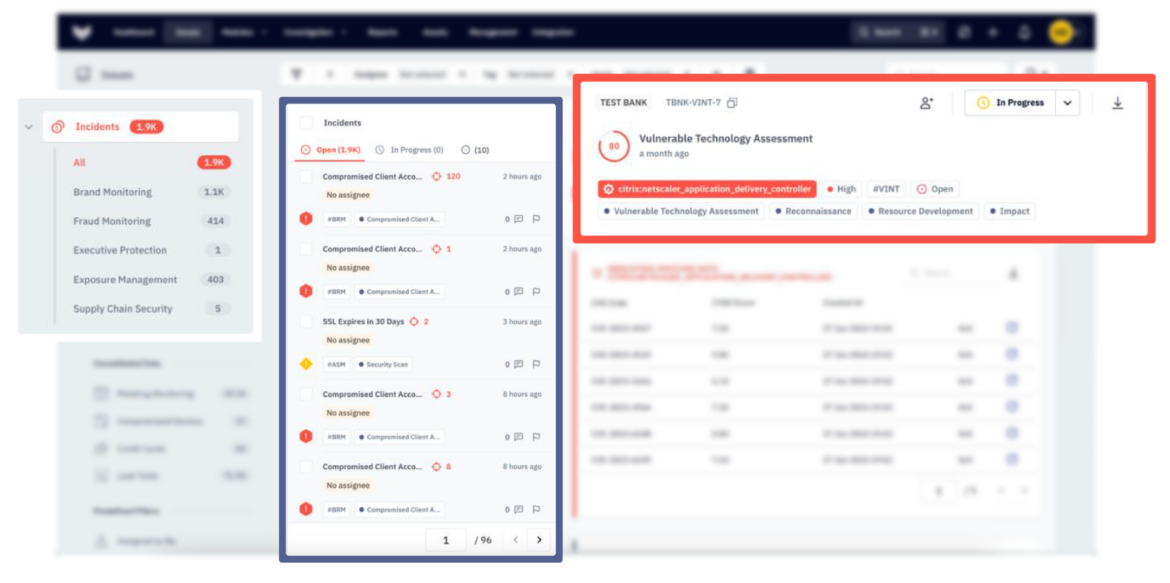
Companies rely heavily on third-party vendors and service providers, so vendor risk management has become critical to comprehensive cybersecurity strategies. These external partners often have access to sensitive systems and data. Managing these risks requires a robust framework that includes regular assessments of vendor security practices, continuous monitoring of their digital footprints, and enforcing strict access controls. This approach ensures that vulnerabilities within the supply chain do not compromise the integrity of an organization’s broader security posture.
These solutions enable businesses to enforce compliance with industry standards and regulations, reducing the likelihood of breaches originating from supply chain vulnerabilities. Additionally, integrating automated threat remediation capabilities into vendor management strategies allows organizations to respond quickly to incidents, minimizing their impact. Organizations can strengthen their defenses and build trust within their digital ecosystems by adopting a proactive and collaborative approach to vendor risk management.
Managing Third-Party Risks with Brandefense: A Strong Shield Against Cyber Threats
Cybersecurity is no longer just about protecting internal networks; it now requires safeguarding an entire supply chain that includes business partners, suppliers, and external service providers. However, this expanded network also introduces third-party cyber threats.
This is where Brandefense comes in, offering a proactive threat intelligence solution that helps organizations manage third-party risks effectively.
But how does Brandefense’s Third-Party Risk Management (TPRM) solution support businesses?
How Does Brandefense’s Third-Party Risk Management Solution Help Reduce Risks?
Brandefense is a comprehensive cybersecurity platform that enables organizations to identify and manage security risks originating from third parties. The TPRM solution continuously monitors all stakeholders within the supply chain, allowing you to detect potential security threats at an early stage.
1. Continuous Monitoring of Third-Party Risks
Traditional security approaches often rely on periodic assessments of third parties. However, cyber threats are dynamic and constantly evolving. Brandefense’s automated and continuous monitoring system allows organizations to evaluate the cybersecurity posture of their suppliers and business partners in real time.
2. Attack Surface Mapping and Vulnerability Detection
Third-party companies may unknowingly have security vulnerabilities. Through vulnerability scans, open port analysis, credential leak detection, and attack surface evaluation, Brandefense identifies potential security gaps in your vendors and prioritizes risks accordingly.
3. Dark Web and Deep Web Monitoring
Many data breaches and malicious activities occur in underground forums or within private attacker networks. Brandefense conducts continuous scans of the dark web and deep web to detect any leaked information related to your third parties, allowing you to act before an incident escalates.
4. Risk Prioritization with Security Scoring
Not all third-party relationships pose the same level of risk. Using advanced threat intelligence analytics, Brandefense assigns a security score to each third party. This helps security teams prioritize high-risk vendors and develop a more effective risk management strategy.
5. Automated Alerts and Reporting Mechanism
When Brandefense detects a risk, it sends automated alerts to ensure security teams take immediate action. Additionally, it generates detailed reports to assist SOC analysts, CISOs, CIOs, and CTI analysts in making proactive security decisions.
The cyber threat landscape is becoming increasingly complex, and the security posture of your business partners directly impacts your own security. The Brandefense Third-Party Risk Management (TPRM) solution provides automated, continuous, and proactive monitoring to strengthen your cybersecurity posture. With real-time threat intelligence, security scoring, and dark web monitoring, Brandefense is an essential tool for SOC teams, CISOs, CIOs, and all cybersecurity professionals.

Reducing False Positives to Save Time and Resources
One of the most persistent challenges in cybersecurity is the overwhelming number of false positives generated by traditional detection systems. While intended to safeguard assets, these alerts often overwhelm security teams, diverting attention from genuine threats and leading to inefficiencies. Addressing this issue requires implementing advanced false positive reduction strategies, which focus on improving the accuracy of threat detection systems. Machine learning algorithms and AI-driven analytics play a pivotal role in this process, as they can analyze and contextualize data to distinguish between legitimate threats and harmless anomalies.
Reducing false positives improves efficiency and allows organizations to allocate resources more effectively. Security teams can focus on high-priority incidents, promptly addressing critical vulnerabilities. Integrating automated threat remediation tools further enhances this process by enabling rapid responses to confirmed threats. These systems can isolate affected assets, neutralize risks, and restore operations with minimal disruption. By minimizing false positives, organizations can optimize their SOC operations, reduce the risk of alert fatigue, and maintain a stronger overall security posture in the face of evolving threats.
Proactive Risk Management for Enhanced Security Posture
In today’s rapidly evolving threat landscape, proactive risk management has become a cornerstone of cybersecurity. This approach involves anticipating potential threats, assessing vulnerabilities, and implementing measures to mitigate risks before they can cause harm. By shifting focus from reactive to proactive strategies, companies can decrease the likelihood of successful cyberattacks. Continuous monitoring of digital assets and regular vulnerability assessments form the foundation of this approach, enabling businesses to maintain a dynamic and responsive security posture.
A key component of proactive risk management is using cyber threat intelligence feeds. These feeds provide real-time insights into threat actors’ tactics, techniques, and procedures (TTPs), enabling security teams to anticipate and counteract attacks. By combining this intelligence with advanced analytics and risk modeling, organizations can prioritize remediation efforts, ensuring that resources are directed toward addressing the most pressing vulnerabilities. This holistic approach enhances security and fosters a culture of vigilance and preparedness, equipping organizations to navigate an increasingly complex digital landscape confidently.