Introduction
Ransomware, in which an attacker steals or freezes an organization’s computer systems or data and demands a ransom payment to restore access to them, is one of the fastest-growing and most common cybersecurity threats facing businesses today.
The U.S. Treasury Financial Crimes Enforcement Network, or FinCEN, reported that more than $590 million in ransomware payments were made in the first half of 2021 alone, with the top 10 hacking groups making nearly $5.2 billion worth of ransomware payments in Bitcoin. Last three years. As staggering as these numbers are, they probably underestimate the true scope of the threat, as many ransomware victims never report the crime to the authorities or publicly agree to pay the ransom and fail to account for ransoms paid via other cryptocurrencies.
While we’ve started seeing ransomware attacks in the headlines lately, the threat has been around for much longer. The attack method and techniques have evolved over time, but the incredible damage that ransomware attacks can do to organizations and individuals remains the same.
To understand how to better protect against ransomware attacks, we must first look at where we came from.
First Ransomware Attack
The earliest known ransomware attack was in 1989. An AIDS researcher named “Dr. Joseph L. Popp” made a total of 20000 floppy disks and sent them to random mailing addresses. The software in this floppy disk encrypted all the files of the computer and demanded a ransom of $189 to restore the files. In the image below, you can see the message left for the requested ransom.
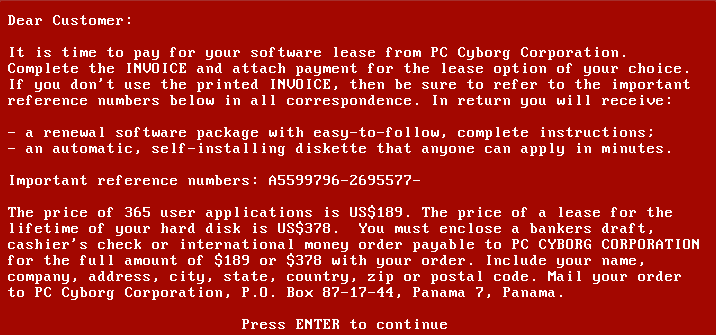
The Beginning of Today’s Ransomware
With more organizations coming online, cybercriminals have been able to spread ransomware to more victims. But they had a fatal flaw in their method. They used symmetric cryptography. In symmetric cryptography, the same key is used for encryption and decryption. And since this key is inside the malware, it can be easily extracted, and encrypted files can be decrypted. As a result, cybersecurity firms were able to develop universal decryption tools soon after infections were discovered.
As we often see in nature, ransomware strains have evolved as the environment has changed. The next step in the evolution of ransomware was asymmetric encryption, where we used two keys rather than a single key. In asymmetric encryption, one key pair is created. One is called a Public Key, and the other is called a Private Key. Data encrypted with a public key is opened with a private key and vice versa.
While the attacker holds a private key, a public key is stored in the cryptovirus. After infecting the computer, the virus generates a new symmetric key and uses it to encrypt all the files on its disk. The newly created key is locked in an encrypted archive and removed from the victim’s machine.
After the ransom is paid, the victim must send the encrypted archive to the attacker; The attacker uses the private key to open it, extracts the session key, and sends it back to the victim so they can decrypt their files. This way, each infected machine requires a unique key and even the attacker cannot decrypt files without the session key. A victim’s unlock key will not work for other victims, and the private key will never be shared with victims. This evolution is now the foundation of every crypto virus.
The Next Step in Evolution
With the introduction of asymmetric cryptography, ransomware became much more difficult for victims to remove, resulting in more victims deciding to pay the ransom. However, attackers still needed a more efficient delivery system to spread their virus. Up until this point, attackers have generally relied on distribution via spam emails or phishing attacks that manage to infect single users, not entire organizations. That changed with the emergence of the WannaCry worm in 2017.
WannaCry still infiltrated an organization through a phishing attack, but once inside, it managed to quickly spread across all networks using the SMB vulnerability. This vulnerability, called EternalBlue, allowed the ransomware to quickly spread over a network without any action from the user beyond the initial infection. It is estimated that around 200,000 computers in 150 countries are infected with WannaCry.
In addition to this topic, Ransomware groups may take sides in certain countries. For example, during the COVID-19 pandemic, we saw Chinese-backed threat actors trying to steal data from the COVID-19 vaccine. In another example, the Conti ransomware group had some internal conflicts during the Ukraine-Russia war. The Conti group stated that it was on Russia’s side in this war. But one or more of the team members supported the Ukrainian side. This caused an unprecedented internal conflict, and all the data related to the Conti group was leaked. It was an interesting example of taking sides between ransomware groups.
Ransomware as a Service
Over time, threat actors found a way to spread their malware to more people. They would allow others to use their own malware as a service. Thus, they would reach more victims, and their reputation in the media would rise.
Today, ransomware groups have chosen to give them to more experienced threat actors rather than sell exploit kits and let malicious people use them freely.
It is important to note that today RaaS is not a simple subscription model as it is often described. Instead, ransomware operators develop the malware and run the infrastructure.
After a successful attack, the ransomware operators and their affiliates split the ransom. Generally, the affiliates get the biggest share. This rate varies between 80% and 90%.
Previously, the attacks were opportunistic and used worm-like behavior (WannaCry), focusing on the most direct way to monetize. Under today’s profit-sharing model, threat actors have adopted tactics, techniques, and procedures from advanced persistent threat (APT) groups with a focus on maximizing damage and pressure, not speed.
This enables today’s ransomware groups to manage the multimillion-dollar ransomware we see in the headlines. They spend weeks or months carrying out an attack.
Simply encrypting random data is no longer enough. They encrypt the data and, at the same time, steal it and threaten to sell it.
What to Expect in the Future
Ransomware is expected to increase in the future. Because it is easier to program than other malware, and the payments are increasing. Additionally, ransomware is attractive to attackers as it does not need to be disguised like other types of malware. Malware is usually designed to evade detection, but ransomware is designed to be detected after files have been encrypted—usually in a pop-up message on the victim’s machine.
Additionally, more anti-ransomware companies will start to rise. Investments in cyber security will increase as threats increase.
You can take precautions yourself by following the steps below.
- Provide regular training in order to raise awareness of cyber security among your employees
- Identify, prioritize, and back up the asset that you need to protect at regular intervals and keep 3 different copies of the created backups in two different media types and one outside the institution.
- Be suspicious of e-mails of unknown origin and the file attachments they contain. If possible, do not open them.
- Use licensed and up-to-date operating systems.
- Use reliable anti-virus solutions.
As Brandefense, we regularly monitor ransomware activities. And in this regard, we regularly inform our customers about attacks on a sector-oriented basis. At the same time, we publish reports for each quarter evaluating the important ransomware activities, news, and impact on the industry during that period.






