This blog post comes from the KageNoHitobito Ransomware Technical Analysis report. If you want to read more details, download it as a PDFclick here
Executive Summary
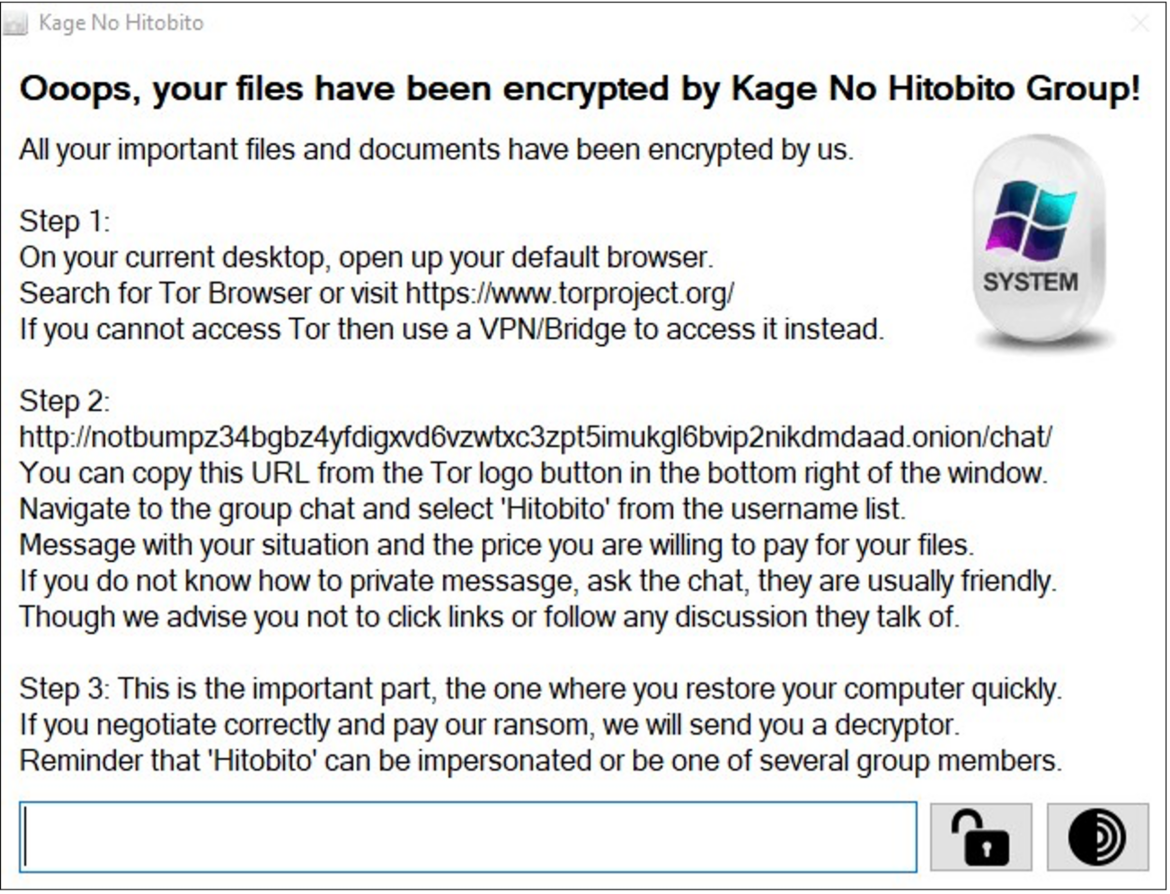
In late March 2024, samples of the KageNoHitobito ransomware became publicly available. This ransomware operates by encrypting files on infected machines and then demanding a ransom in exchange for the decryption keys, as indicated in ransom notes left on the victims’ systems. The KageNoHitobito group utilizes the TOR network to facilitate communication with its victims but does not maintain a data leak site, indicating that they do not claim to have exfiltrated any sensitive information from the victims.
Additionally, the KageNoHitobito ransomware employs sophisticated techniques to evade detection, including debugger evasion tactics to avoid analysis by security researchers. For persistence, it modifies the system registry to ensure it remains active even after the system is rebooted. Notably, the ransomware is designed to target and encrypt files solely on the local drives of compromised computers, avoiding any networked drives. The files encrypted by this ransomware are identifiable by a distinctive “.hitobito” extension.
Scope
| Filename | Locker.exe |
| Filetype | Win32 EXE |
| Written Language | .NET |
| MD5 | 45ec0c61105121da6fed131ba19a463b |
| SHA1 | 900944b4eb076ee4bf9886bec81dce499b48d69b |
| SHA256 | 8939bfe20bc6476806d22c8edfcaba5c36f936b893b3de1c847558502654c82f |
| First Seen / Detection Date | 2024-03-21 |
| Initial Infection Vector | N/A |
MITRE ATTA&CK Threat Matrix
- TA002 Execution
- T1059 Command and Scripting Interpreter
- T1106 Native API
- TA003 Persistence
- T1547 Boot or Logon Autostart Execution
- T1547.001 Registry Run Keys / Startup Folder
- T1547 Boot or Logon Autostart Execution
- TA005 Defense Evasion
- T1027 Obfuscated Files or Information
- T1036 Masquerading
- T1070 Indicator Removal
- T1622 Debugger Evasion
- T1070.006 Time Stomp
- T1112 Modify Registry
- T1140 Deobfuscate/Decode Files or Information
- TA005 Discovery
- T1057 Process Discovery
- T1082 System Information Discovery
- T1083 File and Directory Discovery
- TA0034 Impact
- T1486 Data Encrypted for Impact
Mitigation Strategies
Regularly check for the presence of suspicious keys in the Windows registry, specifically under the path Software\Microsoft\Windows\CurrentVersion\Run. Be alert for a key named AlertaRansomware, which indicates the presence of the KageNoHitobito ransomware.
Maintain regular and up-to-date backups of all critical data. Ensure these backups are stored offline and are not accessible from the network.
Conclusion
This report provides a detailed technical analysis of the KageNoHitobito ransomware. The malware contains a number of sophisticated capabilities. KageNoHitobito is notable for its ability to employ advanced detection evasion techniques, including debugger evasion, to avoid analysis by security researchers. It also achieves persistence on infected systems through registry modifications, specifically by creating a key.
Our analysis has comprehensively examined the code structure and behavioral characteristics of the KageNoHitobito ransomware, providing key insights into its propagation methods. This information can help organizations formulate more effective protection strategies. Of particular note are the malware’s stealth techniques, which highlight the need for improvements to alert systems to increase their sensitivity.
You can find the IoCs and YARA Rules on our GitHub Repo.
This blog post comes from the KageNoHitobito Ransomware Technical Analysis report. If you want to read more details, download it as a PDFclick here






