Introduction
Ransomware Attacks and Vulnerabilities
Ransomware is used by threat actors to encrypt targeted victim systems. Threat actors obtain the data on the targeted system and demand ransom payments from victims in exchange for not disclosing the data to the public. Once the victims pay the ransom to the threat actors, the data sharing is stopped, and the targeted system is decrypted. It is known that there is an increase in ransomware campaigns against institutions and organizations day by day. Threat actors obtain critical data belonging to institutions and organizations in ransomware campaigns and demand large amounts of ransom money.
Threat groups use initial access vectors to launch ransomware distribution campaigns on the systems of targeted institutions and organizations. Initial access vectors include exploiting security vulnerabilities, leveraging obtained credentials, and brute force enforcement services such as RDP or SSH. Threat actors exploit security vulnerabilities identified in applications used on targeted systems to execute ransomware on the targeted system.
What is a CWE?
CWE (Common Weakness Enumeration) lists common software security weaknesses. Maintained by The MITRE Corporation and based on contributions from the general software community, CWE is an evolving resource that identifies and categorizes software vulnerabilities through a common language. The resource explains to users how to evaluate security measurement tools, how to identify vulnerabilities, and how to prevent and mitigate vulnerabilities. CWE strives to stop vulnerabilities and bugs by educating software developers to develop better products that are not vulnerable to exploitation. Software developers can use the CWE as a resource when writing code to prevent vulnerabilities during the development process.
CWEs are usually well documented and have detailed descriptions. Usually, the documentation includes common vulnerabilities, similar CVEs, and relationships with similar vulnerabilities in relation to CWEs. Security professionals can use CWE records to generate proactive alerts and remediation from related attack patterns. Each CWE has a section that lists different attack patterns with an associated vulnerability. Using this information, organizations can develop custom detection methods around CWEs, taking into account their risk tolerance level.
What is CVE?
CVE (Common Vulnerabilities and Exposures) is a database that details and categorizes security vulnerabilities in publicly disclosed applications. Each vulnerability in the database has a CVE identifier number. Through these CVE numbers, users can easily access detailed information about the vulnerability. Institutions and organizations often use CVE and related CVSS scores for planning and prioritization in vulnerability management programs.
Difference Between CWE and CVE
The main difference between CWE and CVE is that CWE classifies vulnerabilities while CVE only classifies known vulnerabilities related to specific systems and products. For example, a CVE might detail a specific vulnerability in an operating system that allows threat actors to execute code remotely. However, CWE outlines a vulnerability independent of any particular product or system.
A CWE uses a common language to enable software security vulnerabilities to be fixed or mitigated. Because software developers have access to data about security vulnerabilities early in their product lifecycle, they can develop products without encountering security vulnerabilities. This allows software developers to keep pace with rapid development lifecycles and deliver better, attack surface minimized products to customers faster.
Most Abused CWEs in 2022
Some of the CWE categories and vulnerabilities frequently exploited by threat actors in 2022 are listed in the table below.
| Rank | ID | Name |
| 1 | CWE-787 | Out-of-bounds Write |
| 2 | CWE-79 | Cross-site Scripting |
| 3 | CWE-89 | SQL Injection |
| 4 | CWE-20 | Improper Input Validation |
| 5 | CWE-125 | Out-of-bounds Read |
| 6 | CWE-78 | OS Command Injection |
| 7 | CWE-22 | Directory tree/path Traversal Errors |
| 8 | CWE-352 | Cross-Site Request Forgery |
| 9 | CWE-434 | Unrestricted Upload of File with Dangerous Type |
| 10 | CWE-287 | Improper Authentication |
Out-of-bounds Write
Software writes data after the end or before the beginning of the intended buffer. This usually occurs when the pointer or index is incremented or decremented to a location beyond the buffer boundaries or when pointer arithmetic results in a location outside the current memory location. This can result in the corruption of sensitive information, crashes, or code execution.
Cross-site Scripting
Cross-site scripting vulnerabilities, also known as XSS, allow threat actors to inject malicious code into websites. These attacks usually take two types: Stored XSS, where an attacker injects malicious code into a site, which is then displayed to visitors, for example, through a comment or like function, and Reflected XSS, where an attacker injects malicious code into their own browser, which is then automatically sent back to your website when they visit it.
SQL Injection
The software generates all or part of an SQL command using externally affected input from an upstream component but does not sanitize or miss-sanitize special elements that may alter the intended SQL command when sent to the downstream component. If SQL syntax in user-controllable inputs is not sufficiently removed or quoted, the SQL query generated can cause these inputs to be interpreted as SQL instead of ordinary user data. This can be used to modify the query logic to bypass security checks or possibly add additional statements that modify the backend database, including the execution of system commands.
Improper Input Validation
The product does not validate or incorrectly validate input that could affect the control flow or data flow of a program. When software fails to validate input properly, an attacker can generate input in a form that is not expected by the rest of the application. This can cause parts of the system to receive unwanted input, which can result in altered control flow, arbitrary control of a resource, or arbitrary code execution.
Out-of-bounds Read
The software reads data after the end or before the beginning of the intended buffer. This usually occurs when the pointer or index is incremented or decremented to a location beyond the buffer boundaries or when pointer arithmetic results in a location outside the current memory location. This can result in the corruption of sensitive information, crash, or code execution.
OS Command Injection
The software generates all or part of an operating system command using externally influenced input from an upstream component but does not sanitize or incorrectly sanitizes special elements that could modify the intended operating system command when sent to the downstream component, which could allow attackers to execute unexpected, dangerous commands directly on the operating system. This weakness can lead to a vulnerability in environments where the threat actor does not have direct access to the operating system, such as web applications. Alternatively, if the vulnerability occurs in a privileged program, it could allow the threat actor to specify commands that would not normally be accessible or to invoke alternative commands with privileges the attacker does not have.
Directory Tree/Path Traversal Errors
The software uses external input to create a pathname that is intended to identify a file or directory located under a restricted parent directory, but the software does not properly sanitize special elements that can resolve to a location outside the restricted directory. By using special elements such as “…” and “/” separators, attackers can go outside the restricted location to access files or directories located elsewhere on the system. One of the most common special elements is the “../” sequence, which in most modern operating systems is interpreted as the parent directory of the current location. This is called relative path traversal. Path traversal also includes the use of absolute pathnames such as “/usr/local/bin”, which can be useful for accessing unexpected files.
Cross-Site Request Forgery
When a web server is designed to receive a request from a client without any mechanism to verify that the request was sent intentionally, it is possible for an attacker to trick a client into making an unintentional request to the web server, which is then accepted as a genuine request. This can be done via a URL, image upload, XMLHttpRequest, etc., and can result in data exposure or execution of unwanted code.
Unrestricted Upload of File with Dangerous Type
The software allows the attacker to upload or transfer dangerous types of files that can be automatically processed in the product’s environment.
Improper Authentication
Improper authentication occurs when an application improperly authenticates a user. Vulnerability, which occurs in the Weakness, Architecture, Design, and Implementation phases, allows threat actors to gain certain privileges within the application, access sensitive data, and execute arbitrary code.
Most Abused CVEs in 2022
In their attack campaigns, threat actors exploit CWE vulnerability categories detected in targeted user systems to gain access to targeted user systems. Vulnerabilities detected in targeted user products specify the specific vulnerabilities of that product. Some of the security vulnerabilities frequently exploited by threat actors in 2022 are listed in the table below.
| RANK | CVE | Vulnerability Name | Vendor and Product | Type |
| 1 | CVE-2021-44228 | Log4Shell | Apache Log4j | RCE (Remote Code Execution) |
| 2 | CVE-2021-40539 | Zoho ManageEngine ADSelfService Plus | RCE | |
| 3 | CVE-2021-26855,CVE-2021-26857,CVE-2021-26858, | ProxyLogon | Microsoft Exchange Server | RCE |
| 4 | CVE-2021-31207,CVE-2021-34473,CVE-2021-34523 | ProxyShell | Microsoft Exchange Server | RCE |
| 5 | CVE-2021-26084 | Atlassian Confluence Server and Data Center | Arbitrary code execution | |
| 6 | CVE-2021-21972 | VMware vSphere Client | RCE | |
| 7 | CVE-2020-1472 | ZeroLogon | Microsoft Netlogon Remote Protocol (MS-NRPC) | Elevation of privilege |
| 8 | CVE-2020-0688 | Microsoft Exchange Server | RCE | |
| 9 | CVE-2019-11510 | Pulse Secure Pulse Connect Secure | Arbitrary file reading | |
| 10 | CVE-2018-13379 | Fortinet FortiOS and FortiProxy | Path traversal |
Log4Shell (CVE-2021-44228)
Found in Log4j in the Apache Java logging library and first detected in late 2021. The vulnerability, which allows remote code execution by threat actors, is very common due to the prevalence of the Log4j library in web applications.
Zoho ManageEngine ADSelfService Plus (CVE-2021-40539)
Zoho ManageEngine ADSelfService Plus version 6113 and earlier have been identified as a vulnerability causing a REST API authentication bypass and remote code execution. The bug, patched in September 2021, allows threat actors to use specially crafted Rest API URLs to bypass authentication due to a failure to normalize the URL before the authentication attempt. By bypassing the authentication filter, threat actors can exploit endpoints and perform attacks such as arbitrary command execution.
ProxyShell (CVE-2021-31207, CVE-2021-34473, CVE-2021-34523)
ProxyShell consists of three separate flaws in the Microsoft Exchange email server that allows security features to be bypassed, RCE, and privilege escalation. When combined in vulnerable environments, ProxyShell allows an attacker to establish persistence and execute malicious PowerShell commands. A successful exploit allows threat actors to take full control of vulnerable Microsoft Exchange email servers.
ProxyLogon (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-26858, CVE-2021-27065)
The ProxyLogon vulnerability can be exploited against unpatched mail servers running Microsoft Exchange Server 2013, 2016, or 2019 that are set to receive untrusted connections from the external environment. The vulnerability allows threat actors to execute commands on unpatched and internal Exchange Servers by sending commands through port 443. ProxyLogon is a pre-authenticated vulnerability, so a threat actor does not need to log in or complete any authentication process to execute code remotely.
Atlassian Confluence Server & Data Center (CVE-2021-26084)
CVE-2021-26084 is a critical security vulnerability that could allow an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance. Confluence is a Wiki-style service widely used in enterprise environments. The vulnerability, disclosed in August 2021, has been and continues to be actively exploited in the wild as it can be exploited by unauthenticated users regardless of configuration.
VMware vSphere Client (CVE-2021-21972)
VMware enables remote code execution in a vCenter Server plugin of the vSphere Client (HTML5), allowing threat actors to access port 443.
ZeroLogon (CVE-2020-1472)
ZeroLogon is a privilege escalation bug caused by a cryptographic error in Microsoft’s Active Directory Netlogon Remote Protocol (MS-NRPC). An unauthenticated attacker can exploit this flaw to log on to servers using NT LAN Manager (NTLM).
Microsoft Exchange Server (CVE-2020-0688)
This is another remote code execution vulnerability in Microsoft Exchange Server that occurs when the server fails to properly generate unique keys during installation. Knowing the authentication key allows an authenticated user with a mailbox to forward arbitrary objects to be serialized by the web application running as a SYSTEM.
Pulse Secure – Pulse Connect Secure (CVE-2019-11510)
Pulse Secure is a vulnerability affecting VPN devices that allows threat actors to gain access to victim networks. An unauthenticated, remote attacker could send a specially crafted URI to perform an arbitrary file read vulnerability.
Fortinet FortiOS and FortiProxy (CVE-2018-13379)
This is a path traversal vulnerability in the FortiProxy SSL VPN web portal. Exploiting this vulnerability could allow an unauthenticated, remote attacker to download FortiProxy system files via specially crafted HTTP resource requests.
Samples of Security Vulnerabilities Exploited by Threat Groups
The number of security vulnerabilities detected in applications is increasing day by day. Ransomware threat groups exploit security vulnerabilities to gain access to targeted systems. Since there are differences in the user profiles and system types targeted by ransomware threat groups, there may also be differences in the types of vulnerabilities exploited to gain initial access. Examples of ransomware campaigns organized by some ransomware threat groups by exploiting security vulnerabilities are listed below.
Conti
Threat actors associated with the Conti threat group have been found to use the VMware remote code execution vulnerability (CVE-2021-21985) in combination with the popular Log4J vulnerability (CVE-2021-44228) to gain access to VMware servers. While initial access to the organization itself is achieved using RDP, VPN, or phishing, gaining access to vCenter allows the threat actor to have a more significant impact, as many organizations virtualize important aspects of their operational infrastructure. The attack campaign carried out by threat actors is generally known to be targeted at Europe and the US.
Vuln ID: CVE-2021-44228
CVSS Severity: V3.1: 10.0 CRITICAL
CWE: CWE-917 – Expression Language Injection
Published: 10/12/2021
Affected Product: Apache Log4j2
Vuln ID: CVE-2021-21985
CVSS Severity: V3.1: 9.8 CRITICAL
CWE: CWE-20 – Improper Input Validation
Published: 26/05/2021
Affected Product: VMware vCenter
Cring
Exploiting the identified CVE-2018-13379 vulnerability in Fortinet FortiGate security appliances, threat actors distributed Cring ransomware after gaining initial access to targeted systems. In the attack campaign, threat actors targeted industrial organizations across Europe, waiting for the software version used in the FortiGate VPN server to be 6.0.2 to exploit the vulnerability tracked as CVE-2018-13379.
Vuln ID: CVE-2018-13379
CVSS Severity: V3.1: 9.8 CRITICAL
CWE: CWE-22 – Path Traversal
Published: 06/04/2019
Affected Product: Fortinet FortiOS
DearCry
According to cybersecurity researchers, DearCry ransomware was deployed on compromised Microsoft Exchange servers in 2021 after exploiting four vulnerabilities identified as ProxyLogon. CVE-2021-26855, one of the vulnerabilities identified in Microsoft Exchange, allows an unauthenticated threat actor to authenticate to the Exchange Server via HTTP requests.
After authenticating to the Exchange server, the threat actor can gain access to the Active Directory (AD) environment. The threat actor can use a tool like BloodHound to list the AD environment and then view the path to elevated privileges. The other 3 vulnerabilities identified in Exchange (CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065) allow threat actors to execute code remotely. The number of campaigns organized by sectors in the related ransomware campaign can be seen in the image below.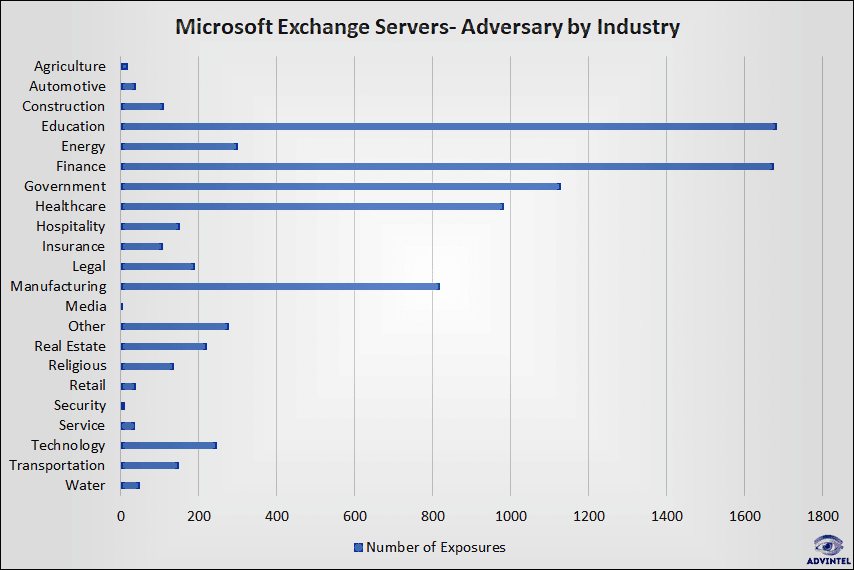
CVSS Severity: CVSS:3.1: 9.8 CRITICAL
CWE: CWE-918 – Server-Side Request Forgery (SSRF)
Published: 02/03/2021
Affected Product: Microsoft Exchange Server
Vuln ID: CVE-2021-26857
CVSS Severity: CVSS:3.1: 7.8 CRITICAL
CWE: CWE-502 – Deserialization of Untrusted Data
Published: 02/03/2021
Affected Product: Microsoft Exchange Server
Vuln ID: CVE-2021-26858
CVSS Severity: CVSS:3.1: 7.8 CRITICAL
CWE: –
Published: 02/03/2021
Affected Product: Microsoft Exchange
Vuln ID: CVE-2021-27065
CVSS Severity: CVSS:3.1: 7.8 CRITICAL
CWE: CWE-22 – Path Traversal
Published: 02/03/2021
Affected Product: Microsoft Exchange
Magniber
Threat actors are exploiting the critical PrintNightmare (CVE-2021-34527) vulnerability in the Windows Print Spooler, which allows code execution on the targeted system, to distribute the Magniber ransomware on Windows servers. Threat actors are known to target vulnerable systems in South Korea with the ransomware campaign.
Vuln ID: CVE-2021-34527
CVSS Severity: CVSS:3.1: 8.8 HIGH
CWE: CWE-269 – Improper Privilege Management
Published: 02/07/2021
Affected Product: Microsoft Windows
eCh0raix
Threat actors distributing eCh0raix ransomware have been identified to gain access to targeted QNAP systems with hard-coded credentials through backdoor software by exploiting the vulnerability tracked as CVE-2021-28799. Threat actors gaining access to targeted QNAP systems enable the distribution of eCh0raix ransomware.
Vuln ID: CVE-2021-28799
CVSS Severity: CVSS:3.1: 9.8 HIGH
CWE: CWE-285 – Improper Authorization
Published: 12/05/2021
Affected Product: QNAP NAS
HelloKitty
It is known that threat actors accessed systems by exploiting the CVE-2019-7481 critical vulnerability in SonicWall Secure Mobile Access (SMA) 100 series and Secure Remote Access (SRA) products, which allows an unauthenticated user to gain read-only access to unauthorized resources, and the distribution of HelloKitty ransomware.
Vuln ID: CVE-2019-7481
CVSS Severity: CVSS:3.1: 7.5 HIGH
CWE: CWE-89 – SQL Injection
Published: 17/12/2019
Affected Product: SonicWall SMA100
Vulnerabilities Exploited by Ransomware Threat Groups
Clop
| CVE | Vendor and Product | Type |
| CVE-2021-27101 | Accellion FTA | SQL Injection |
| CVE-2021-27102 | Accellion FTA | OS Command Execution |
| CVE-2021-27103 | Accellion FTA | SSRF |
| CVE-2021-27104 | Accellion FTA | OS Command Execution |
| CVE-2021-35211 | Solarwinds Serv-U | RCE |
Hive
| CVE | Vendor and Product | Type |
| CVE-2021-31207 | Microsoft Exchange | RCE |
| CVE-2021-34473 | Microsoft Exchange | RCE |
| CVE-2021-34523 | Microsoft Exchange | RCE |
Conti
| CVE | Vendor and Product | Type |
| CVE-2017-0143 | Microsoft Windows | RCE |
| CVE-2017-0144 | Microsoft Windows | RCE |
| CVE-2017-0145 | Microsoft Windows | RCE |
| CVE-2017-0146 | Microsoft Windows | RCE |
| CVE-2017-0147 | Microsoft Windows | RCE |
| CVE-2018-13379 | Fortinet FortiGate VPN | Path Travelsal |
| CVE-2018-13374 | Fortinet FortiOS | Improper Access Control |
| CVE-2020-1472 | Microsoft Windows Netlogon | Elevation of privilege |
| CVE-2021-31207 | Microsoft Exchange | RCE |
| CVE-2021-34473 | Microsoft Exchange | RCE |
| CVE-2021-34473 | Microsoft Exchange | RCE |
| CVE-2021-44228 | Apache Log4j2 | Expression Language Injection |
| CVE-2021-21985 | VMware vCenter | Improper Input Validation |
LockBit
| CVE | Vendor and Product | Type |
| CVE-2018-13379 | Fortinet FortiGate SSL VPN | Path Traversal |
| CVE-2021-20028 | SonicWall SSLVPN | SQL Injection |
| CVE-2021-31207 | Microsoft Exchange | RCE |
| CVE-2021-34523 | Microsoft Exchange | RCE |
| CVE-2021-34473 | Microsoft Exchange | RCE |
| CVE-2022-22986 | F5 BIG-IP | Path Travelsal |
| CVE-2021-22986 | F5-BIG-IP | SSRF |
AvosLocker
| CVE | Vendor and Product | Type |
| CVE-2021-40539 | Zoho ManageEngine ServiceDesk Plus | Authentication Bypass |
| CVE-2022-26134 | Atlassian Confluence Server and Data Center | RCE |
| CVE-2021-45046 | Apache Log4j | RCE |
| CVE-2021-44832 | Apache Log4j | RCE |
| CVE-2021-45105 | Apache Log4j | RCE |
| CVE-2021-44228 | Apache Log4j | RCE |
| CVE-2021-31207 | Microsoft Exchange | RCE |
| CVE-2021-34473 | Microsoft Exchange | RCE |
| CVE-2021-34523 | Microsoft Exchange | RCE |
| CVE-2021-44228 | Microsoft Exchange | RCE |
| CVE-2021-31206 | Microsoft Exchange | RCE |
Prevention and Mitigation Recommendations
- Keep systems and applications up to date by scanning for security vulnerabilities.
- Do not access links in unsafe spam messages or unknown websites.
- Do not provide personal information to untrusted sources.
- Do not rely on e-mails, attachments, files, and links from suspicious or unknown parties.
- Never use USB sticks obtained from unknown sources.
- Use VPN services on public Wi-Fi networks.
- Sensitive data in the system should be backed up at regular intervals.
- Institutions and organizations should provide awareness training to their employees against cyber security threats.
- Up-to-date security solutions should be used in systems and e-mail mail servers.
- Threat intelligence services should be obtained in order to take precautions before any cyber attack occurs.
Conclusion
Threat actors are targeting more and more institutions and organizations through ransomware using advanced techniques. Threat actors exploit current security vulnerabilities to access targeted systems. In order to prevent internet users from being affected by ransomware campaigns, it is recommended to perform vulnerability management and attack surface management against the initial access methods.






