Introduction
Ransomware is malicious software designed to encrypt files on targeted devices and the systems on which those files are based, making them unusable. This software initiates a cryptoviral interception attack that secretly installs itself on the victim’s device (computer, smartphone, wearable devices, etc.) or holds the victim’s data hostage and demands a ransom. The attacker can threaten to publish, keep inaccessible, or delete the victim’s data until the ransom is paid.
Ransomware attacks are growing in size and frequency, threatening businesses around the world. These types of attacks can be scary, especially for small businesses that can’t afford to pay a ransom for their data. That’s why it’s important to stay informed about what ransomware is, how it works, and the types of ransomware there are.
According to data and ransomware statistics collected by security company Sophos[22], Cybercrime magazine, and CyberSecurity Ventures:
- Ransomware cost the world $20 billion in 2021. That number is expected to rise to $265 billion by 2031.
- In 2021, 37 percent of all businesses and organizations were hit by ransomware.
- Recovering from a ransomware attack cost businesses $1.85 million on average in 2021.
- Out of all ransomware victims, 32 percent pay the ransom, but they only get 65 percent of their data back.
- Only 57 percent of businesses are successful in recovering their data using a backup.
The year 2020 saw a rise in the ransom demanded by hackers, which increased by %60 since the start of the year to $178,000 on average. In 2021, the average ransom demand reached $220,298 — up 43 percent compared to 2020.![YES! Ransom Gangs Retarget Same Companies, Learn Why! 1 Figure 1: Average and Median Ransom Payments Between Q3 2018 and Q1 2021 [21]](https://brandefense.io/wp-content/uploads/2022/10/ransom-payments.png)
According to a study by security firm Sophos[22], 51 percent of all surveyed businesses were hit by ransomware in 2020, though the number of cases dropped to 37 percent in 2021. This number varies with the size of the company, with larger companies being more at risk.Ransomware costs businesses billions of dollars each year. By the end of 2019, cybercriminals using ransomware had made off with a reported $11.5 billion in ransom payments. That number already reached $20 billion in 2021. Things aren’t looking too bright in the future. If ransomware attacks keep growing in scale as they have so far, the total cost of ransomware damages around the world is expected to reach a jaw-dropping $265 billion in 2031.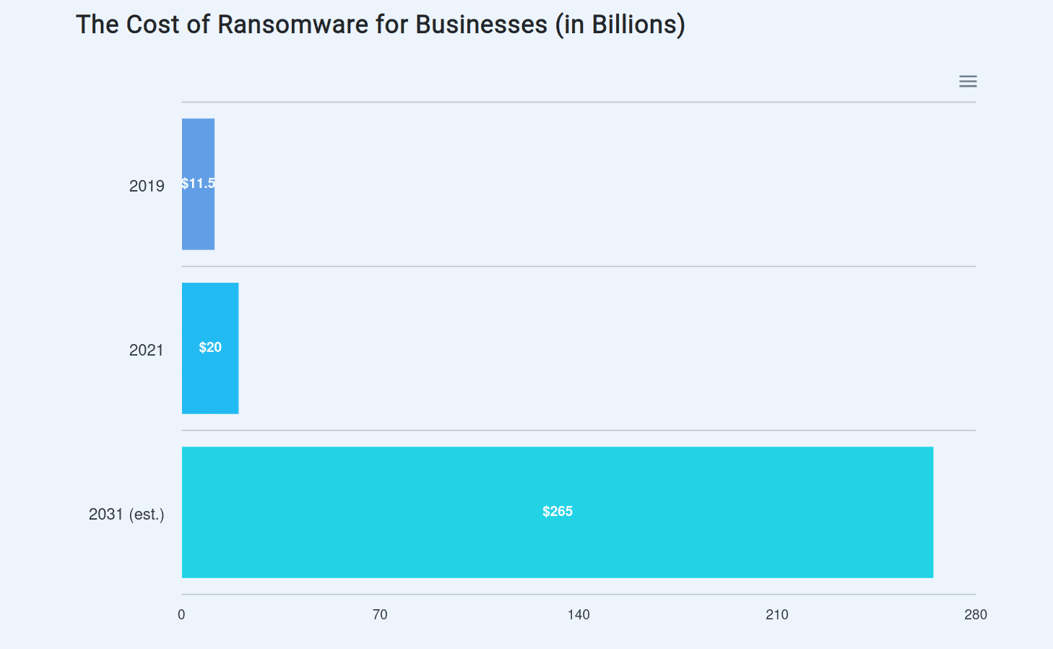
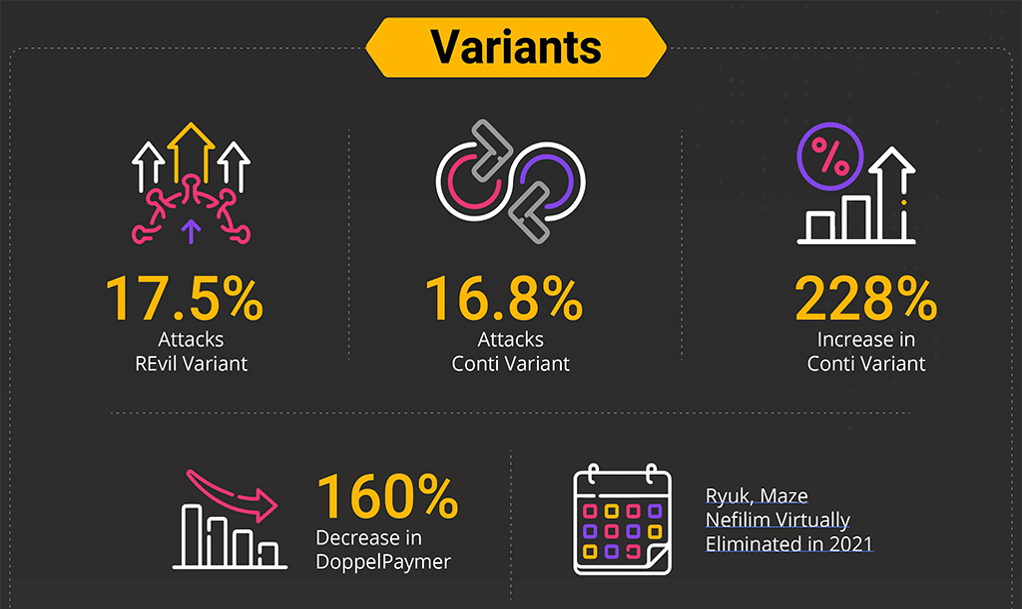
The second half of 2021 made a huge increase in the number of attacks from Conti, which finished the year with 16.8% of all variants and a 228% increase over 2020. On the positive side, some variants were virtually eliminated. Like 160% down on Ryuk, Maze Nefilim and DoppelPaymer.
BlackFog 2022 Ransomware Reports
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 4 Figure 4: Ransomware Attacks by Month [14]](https://brandefense.io/wp-content/uploads/2022/10/ransom-attacks-in-months.png)
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 4 Figure 4: Ransomware Attacks by Month [14]](https://brandefense.io/wp-content/uploads/2022/10/ransom-attacks-in-months.png)
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 6 Figure 5: Ransomware Attacks by Country and Ransomware by Variant [18]](https://brandefense.io/wp-content/uploads/2022/10/ransom-attacks-countries.png)
Double Extortion, Data Leak Threats on the Rise
Once a ransomware data breach occurs, a company’s data is at the mercy of hackers. Still, a company can easily get its data back using a backup (if backup software was installed before the attack). However, hackers have gotten wise to this, and they’ve adapted their methods by including a threat to not only encrypt stolen data but leak it to competitors or sell it on the black market.
In the past, ransomware was about attackers encrypting information found on a system and then demanding a ransom in exchange for a decryption key. With double extortion, attackers also exfiltrate the data to a separate location. There, it can be used for other purposes, including leaking the information to a public website if payment is not received. According to Coveware[21], in 2021, an entire 77 percent of ransomware attacks included a data leak threat, which is 10 percent higher than in the year 2020.
The ransomware tactic, called “double extortion,” first emerged in late 2019 by Maze operators – but has been rapidly adopted over the past few months by various cybercriminals behind the Clop, DoppelPaymer, and Sodinokibi ransomware families.
A November 2019 ransomware attack against Allied Universal, a large American security staffing company, set a precedent for “double extortion.” After the company was hit by a Maze ransomware attack and refused to cough up the 300 Bitcoin ($2.3 million) ransom, the attackers threatened to use sensitive information extracted from Allied Universal’s systems, as well as stolen email and domain name certificates, for a spam campaign impersonating Allied Universal.
To prove the validity of the threat, the threat actors leaked 700 MB worth of data (only 10 percent of what the crooks claimed to have stolen), including contracts, medical records, encryption certificates, and more – and published a new ransom demand that was 50 percent higher than the original.Researchers also revealed TA2101, the group behind the Maze ransomware, has created a dedicated web page that lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data.![YES! Ransom Gangs Retarget Same Companies, Learn Why! 7 Figure 6: Maze Web Page Listing Compromised Companies and Data Dumps [25]](https://brandefense.io/wp-content/uploads/2022/10/maze-webpage.png)
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 8 Figure 7: Revil Group’s “Happy Blog” Listing Compromised Companies and Data Dumps [26]](https://brandefense.io/wp-content/uploads/2022/10/disorder.png)
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 9 Figure 8: Revil warned that they would release data stolen from victims if payment is not made.[27]](https://brandefense.io/wp-content/uploads/2022/10/REvil-1.png)
Why Ransomware Victims Are Retargeted
At first glance, it may seem reasonable that after a cybercriminal successfully pulls off a ransomware attack, they will move on from their victim and target a new company. But, as it turns out, companies that have suffered a ransomware incident are more likely to be targeted again, often by the same attacker. Intuitively, it makes sense that a cybercriminal might try again, especially while the company, struggling to restore operations and shore up its defenses, remains vulnerable. And while companies may believe paying the ransom is the most prudent course of action, paying the ransom indicates to cybercriminals that you’re more likely to pay again.
Many malware programs and cybercriminals contain hidden tools that are often used to launch a second attack. Often, inexperienced IT personnel working to clean up compromised systems overlook these items and fall victim again.
Boston-based Cybereason found that 80% of organizations that previously paid ransom demands confirmed they were exposed to a second attack, according to a commissioned survey of 1,263 cybersecurity professionals in varying industries from the U.S., United Kingdom, Spain, Germany, France, United Arab Emirates, and Singapore.
At the same time, according to the data presented by the team of Atlas VPN, 50% of businesses worldwide have experienced recurring attacks from the same hackers, with companies in the United Kingdom suffering the most.The survey included responses from 1,778 IT and IT security professionals in North America, Latin America, the United Kingdom, and Europe. Out of all the countries featured in the survey, companies in the UK have had the most cybersecurity incidents due to an inability to prevent the recurrence of an attack from the same threat actor. This challenge affected 55% of the organizations in the UK.
The top five security threats affecting organizations are cloud vulnerabilities (65%), denial of service attacks (60%), phishing and social engineering attacks (52%), malicious insider threats (45%), as well as DNS-based attacks (44%).
- One reason is that even when a ransomware attack fails, if it remains undetected, attackers have a chance to attack again because incident response and network forensics are a challenge for many security teams. The process of wading through log files to pinpoint the root cause of an attack and identify impacted systems is incredibly costly and time-consuming, even for skilled analysts, which grants attackers the time they need to strike again.
- Another reason would be that attackers are trusting that weak perimeter defenses remain unfortified or that vulnerabilities remain unpatched even after they failed to exploit them.
- There are also scenarios where persistent threat actors attack organizations even if they fail many times. In such cases, what motivates the threat actors to continue targeting the organization might change. They might pursue it for the substantial financial reward they could receive if they succeed, for reputation and goodwill in society, or for more straightforward motives like vengeance. For example, a ransomware attack in late October 2019 resulted in the forced shutdown of thousands of servers and devices a ransomware attack forced shutdown of thousands of servers and devices in Las Cruces Public Schools, a school district headquartered in Las Cruces, New Mexico. This was the third time in the past six years that Las Cruces Public Schools has been attacked. It has been determined that the previous attack and the last attack were carried out by the Ryuk ransomware group. Security experts believed that this ransomware organization grew in attack targets and sizes as school districts received more cyber security insurance.
Methods Use to Perform Ransomware Attacks
There are a number of attack vectors ransomware can exploit to take over computers or servers.
- Phishing E-mails: The most common method for hackers to spread ransomware is through phishing emails. Hackers use carefully crafted phishing emails to trick a victim into opening an attachment or clicking on a link that contains a malicious file. This might seem like a significant effort, but it has become quite simple with software automation. The principle behind the strategy is that it only takes one person to click on the link to enable cyber attackers to infiltrate an entire organization. Bad actors don’t focus solely on the technical side of attacks but also on emotional factors. Since they need to take advantage of people’s trust, they use social engineering techniques to create emails that make sense from a corporate perspective and have the same tone of voice and format as legitimate messages. They lower victims’ skepticism and increase their chances of a successful phishing attempt. All it takes is for one person to naively open an attachment in the phishing email, the data is encrypted, and ransomware gains a foothold on the machine. Locky, Cerber, and Nemucod are three popular ransomware that use phishing to exploit victims.
- Remote Desktop Protocol (RDP) Targeted Attacks: Another increasingly popular mechanism in which attackers are infecting victims is through Remote Desktop Protocol (RDP). As the name implies, Remote Desktop Protocol was created to enable IT administrators to securely access a user’s machine remotely to configure it, troubleshoot problems, install updates, or simply use the machine. RDP typically runs over port 3389. While opening doors to a device for legitimate use has many benefits, it also presents an opportunity for a bad actor to exploit it for illegitimate use. In 2017, it was determined that over 10 million machines are advertising themselves to the public internet as having port 3389 open. RDP often goes hand in hand with brute-force attacks through which bad actors use trial-and-error to guess login information and access computers. Another tactic that works for unauthorized RDP access is purchasing credentials on the dark web. SamSam, LowLevel04, and CrySis are three popular ransomware that use RDP to exploit victims.
- Drive-by Downloads From a Compromised Website: Another entry path that attackers use to deliver ransomware is through what is known as drive-by downloads. These are malicious downloads that happen without a user’s knowledge when they visit a compromised website. Attackers often initiate drive-by downloads by taking advantage of known vulnerabilities in the software of legitimate websites.
They then use these vulnerabilities to either embed the malicious code on a website or to redirect the victim to another site that they control, which hosts software known as exploit kits. Exploit kits give hackers the ability to silently scan the visiting device for its specific weaknesses and, if found, execute code in the background without the user clicking anything. The unsuspecting user will then suddenly be faced with a ransom note, alerting them of the infection and demanding payment for returned files. While this may sound like something encountered only on small, under-the-radar sites, drive-by downloads are actually not limited to obscure websites. They have happened to some of the most popular sites in the world, including the New York Times, the BBC, and the NFL – all of these were targeted in a ransomware campaign through hijacked advertisements. CryptoWall, PrincessLocker, and CryptXXX are three popular ransomware exploiting victims through a drive-by.
- USB and Removable Media: Another method used by ransom actors to penetrate an environment and infect the machines is a USB drive. In 2016, Australian police issued a warning to citizens about USB drives containing malicious software appearing in mailboxes. The USB drives masqueraded as a promotional Netflix application, then once opened, deployed ransomware onto the unsuspecting user’s computer.
Ransomware has become the go-to attack of choice for cybercriminals to generate revenues. It’s simple to buy on the dark web through Ransomware-as-a-Service (RaaS), and attacks are relatively easy to launch through one of the mentioned methods. Therefore, it’s crucial for organizations to recognize how their systems can be targeted and proactively take steps through a layered security approach to keep themselves protected and safeguard their business service continuity.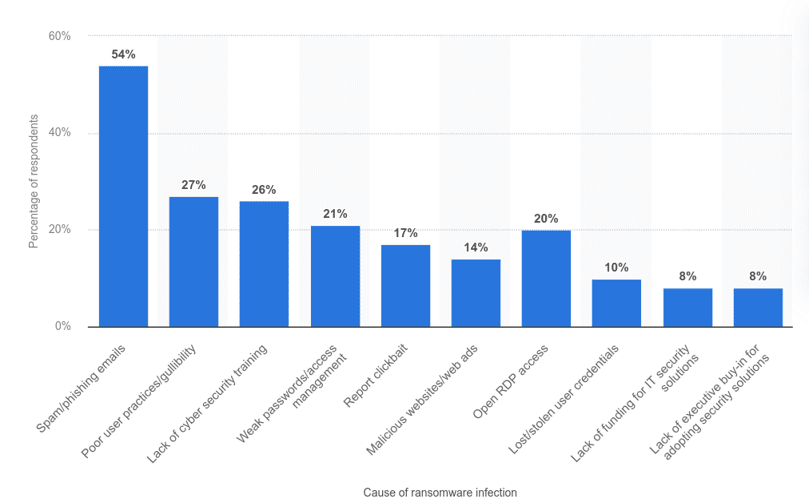
Measures to Protect Companies from Ransomware Attacks
To protect your organizations and assets from ransomware :
- Back up all data: Store the data in a separate device or offline in order to access it in the event of a ransomware attack. Backups are essential for lessening the impact of potential malware threats, so if something goes wrong, organizations should be able to quickly and easily revert to a recent backup. Backup won’t protect organizations from being the target of an attack. But if they’re ever attacked, the fallout won’t be nearly as devastating.
- Keep software updated: Ransomware attackers sometimes find an entry point within the software by exploiting any vulnerabilities. Fortunately, some developers actively search for new vulnerabilities and patch them. Adopt a patch management strategy and ensure that all team members are constantly aware of the latest updates. Effective and timely patching ensures any detected vulnerabilities get remediated on time before threat actors manage to exploit those vulnerabilities. Patching should include all applications you use (in-house and third party), a firmware on devices connected to your network, and operating systems on endpoint workstations.
- Use better threat detection: Most ransomware attacks can be detected and resolved before it’s too late. To maximize your chances of protection, have an automated threat detection system in place.
- Adopt multi-factor authentication: Multi-factor authentication forces users to verify their identities in multiple ways before they’re granted access to a system. If an employee’s password is ever leaked to a criminal, the attacker won’t be able to gain easy access to your systems.
- Use the principle of least privilege: Employees should never have more access to data than they truly need. Segmenting organizations and restricting access can provide a kind of quarantine effect, minimizing the impact of a potential attack and limiting the vectors of access.
- Scan and monitor emails and file activity: Emails are the default choice of cyber criminals running phishing schemes. Scan and monitor emails on an ongoing basis, and consider deploying an automated email security solution to block malicious emails from reaching users. Also, consider scanning and monitoring file activity.
- Improve employee training: Most ransomware attacks are the by-product of bad employee habits or pure ignorance. Employees can serve as the first line of defense to combat online threats and can actively help stop malware from infiltrating the organization’s system. A strong security program paired with employee education about the warning signs, safe practices, and responses aid tremendously in preventing these threats.
- Don’t pay the ransom: If your organization happens to be the victim of a ransomware attack, don’t pay the ransom. It might seem tempting to get out of this bad situation as quickly as possible. But even after paying the ransom, there’s no guarantee the attacker will be true to their word, and as described, sometimes the second wave of ransomware may come after paying the ransom actors.
- Use anti-ransomware solutions: To achieve its objective, ransomware must perform certain anomalous actions, such as opening and encrypting large numbers of files. Protecting against ransomware that “slips through the cracks” requires a specialized security solution. Anti-ransomware solutions monitor programs running on a computer for suspicious behavior commonly exhibited by ransomware. If these behaviors are detected, the program can stop any encryption before further damage is done.
- Network segmentation: The idea behind network segmentation is to divide a network into smaller sub-networks and limit the traffic between different zones. Network segmentation reduces the attack surface threat actors can work with while also preventing lateral movement between zones. Even if a malicious actor bypasses the perimeter, effective segmentation prevents them from moving into other network zones and ultimately protects your endpoints from being encrypted.
- Secure DNS: Dedicated DNS security helps to protect against ransomware by both blocking risky domains, potentially spreading malware, and identifying in-progress attacks. At the more advanced stages of a ransomware attack, hackers often use DNS tunneling to communicate between the victim environment and their control servers; effective security monitors DNS activity and stops this tunneling.
- Using modern framework. Modern security threats demand contemporary security measures. On this front, much support is available, particularly regarding recognizing dangers and strengthening your preventative and response capabilities. Security teams should think about the NIST Cybersecurity Framework and MITRE ATT&CK as two excellent possibilities. The NIST framework is intended to assist organizations in establishing a successful cybersecurity program and preventing cyberattacks. It consists of five functions: Identity, Protect, Detect, Respond, and Recover. Intending to assist in game planning, prevention, and response to realistic adversaries, MITRE ATT&CK is a widely used and accessible knowledge source of real-world tactics and threats. It contains ransomware-specific tactics under the “Impact” category. Security teams can use the information it gives them to anticipate potential attacks, evaluates their current capacity to spot and counteract such tactics and make plans for the best possible defense. Keeping thorough records of who, what, and when an incident occurred can simplify incident triage. The goal is to identify the systems that are essential to the operation of your company, to make sure they are adequately backed up, and to be able to test their recovery. As part of a sound layered security strategy, having reliable backups (or cloud storage) and knowing that they function as intended will help you recover from a ransomware attack more quickly.
![YES! Ransom Gangs Retarget Same Companies, Learn Why! 11 Figure 10: How To Defend Your Organization From Ransomware Attacks [11]](https://brandefense.io/wp-content/uploads/2022/10/defend.png)
Sources
1. https://www.cbsnews.com/news/ransomware-victims-suffer-repeat-attacks-new-report/
2. https://titaniam.io/state-of-data-exfiltration-and-extortion-2022/
3. https://www.spiceworks.com/it-security/threat-reports/news/state-of-data-exfiltration-extortion/
4. https://www.alvareztg.com/ransomware-victims/
5. https://www.cybereason.com/hubfs/Ransomeware_True_Cost_e-book_NewBrand.pdf
6. https://www.cloudwards.net/ransomware-statistics/
7. https://www.xorlab.com/en/blog/how-to-protect-businesses-against-ransomware-attacks
8. https://www.datto.com/resource-downloads/Datto-State-of-the-Channel-Ransomware-Report-v2-1.pdf
9. https://www.techrepublic.com/article/9-tips-to-protect-your-organization-against-ransomware/
10. https://www.weststarbank.com/our-info/4-ways-to-protect-your-business-from-ransomware-attacks
11. https://www.pcmag.com/news/how-to-protect-and-recover-your-business-from-ransomware
12. https://cybeready.com/protect-your-business-against-ransomware
13. https://www.innova.com.tr/en/blog/security-blog/how-to-protect-your-business-against-ransomware-attacks
14. https://www.blackfog.com/2021-ransomware-attack-report/
15. Why Companies Get Hit With Ransomware More Than Once (onsitecomputersinc.com)
16. https://www.safetydetectives.com/blog/ransomware-statistics/
17. https://edscoop.com/ryuk-ransomware-shuts-down-new-mexico-school-district-second-time/
18. https://www.blackfog.com/the-state-of-ransomware-in-2022/
20. https://blog.emsisoft.com/en/34822/the-state-of-ransomware-in-the-us-report-and-statistics-2019/
21. https://www.coveware.com/blog/ransomware-attack-vectors-shift-as-new-software-vulnerability-exploits-abound
22. https://assets.sophos.com/X24WTUEQ/at/k4qjqs73jk9256hffhqsmf/sophos-state-of-ransomware-2021-wp.pdf?cmp=120469
23. https://www.techtarget.com/searchsecurity/feature/Ransomware-trends-statistics-and-facts
24. https://threatpost.com/double-extortion-ransomware-attacks-spike/154818/
25. https://media.kasperskycontenthub.com/wp-content/uploads/sites/103/2020/04/ 15142309/ransomware-story-1.png
26. https://media.kasperskycontenthub.com/wp-content/uploads/sites/103/2020/04/ 15142414/ransomware-story-2.png
27. https://www.bleepingcomputer.com/news/security/sodinokibi-ransomware-publishes-stolen-data-for-the-first-time/
28. https://twitter.com/AltShiftPrtScn/status/1243166479903834112?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1243166479903834112&ref_url=https%3A%2F%2Fkasperskycontenthub.com%2Fthreatpost-global%2Fwp-admin%2Fpost.php%3Fpost%3D154768%26action%3Dedit






