This blog post comes from the Stone Gaze: In-Depth Analsysis of Medusa Ransomware report. If you want to read more details, download it as a PDFclick here
Executive Summary
This report presents a comprehensive technical analysis of Medusa Ransomware, which has increasingly targeted victims worldwide. Medusa Ransomware can encrypt files on infected systems and demand a ransom payment from the victim in exchange for decryption. Various techniques have been employed to evade detection and ensure successful distribution.
Medusa Ransomware spreads primarily through phishing emails with malicious attachments or links. It also exploits vulnerabilities in outdated software for initial system access. The ransomware employs AES-256 and RSA-2048 encryption algorithms, known as a hybrid architecture, to securely encrypt files. This dual encryption method ensures that the files are inaccessible without the decryption key, which is held by the attacker.
Medusa employs techniques such as code obfuscation and disabling antivirus software to bypass security measures. It also checks for virtual analysis environments to avoid being analyzed.
After successful encryption, Medusa Ransomware displays a ransom note to the victim, containing payment instructions and a deadline. The note typically includes a unique identifier for the victim and a contact email address or a link to a Tor-based payment site. Payments are usually demanded in cryptocurrency, making transactions difficult to trace.
The repercussions of Medusa Ransomware on targeted organizations are grave. They can lead to significant downtime, loss of critical data, and potential reputational damage. The recovery costs can be exorbitant, depending on the organization and the extent of data compromised. Even if the ransom is paid, there’s no guarantee of full data recovery.
Introduction
The Medusa ransomware group has been operating intensively since 2021. The Medusa ransomware group stands out from other ransomware actors by targeting educational institutions, among other types of organizations. The Medusa ransomware group has attacked a wide range of organizations globally, including educational institutions, healthcare providers, and government agencies.
The Medusa group uses the Ransomware-as-a-Service (RaaS) model and its members are thought to speak Russian.
Medusa ransomware appends the extension “.MEDUSA” to the encrypted file names and creates a ransom note in each folder called “!!!READ_ME_MEDUSA!!!.txt” containing information about what happened to the victim’s files.
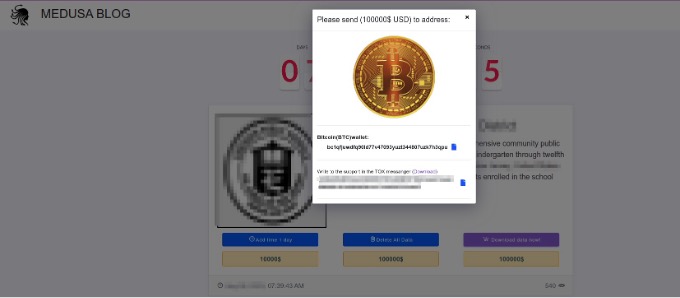
The data of victims attacked by Medusa ransomware is published in 3 places: a Telegram channel called “information support” and 2 websites (one with the extension “.onion”).
Figure 1, Figure 2 and Figure 3 show the sites and Telegram channel where the Medusa ransomware group shared its victims’ data.
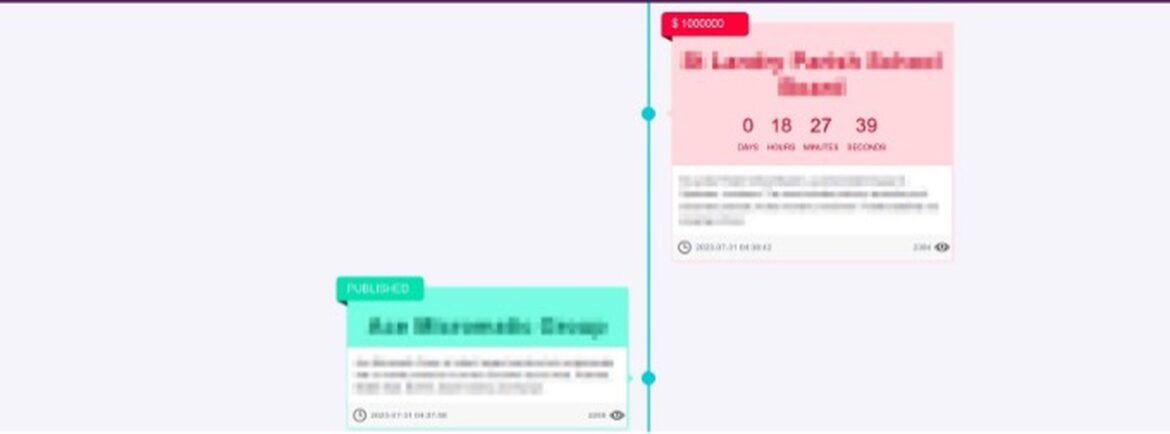
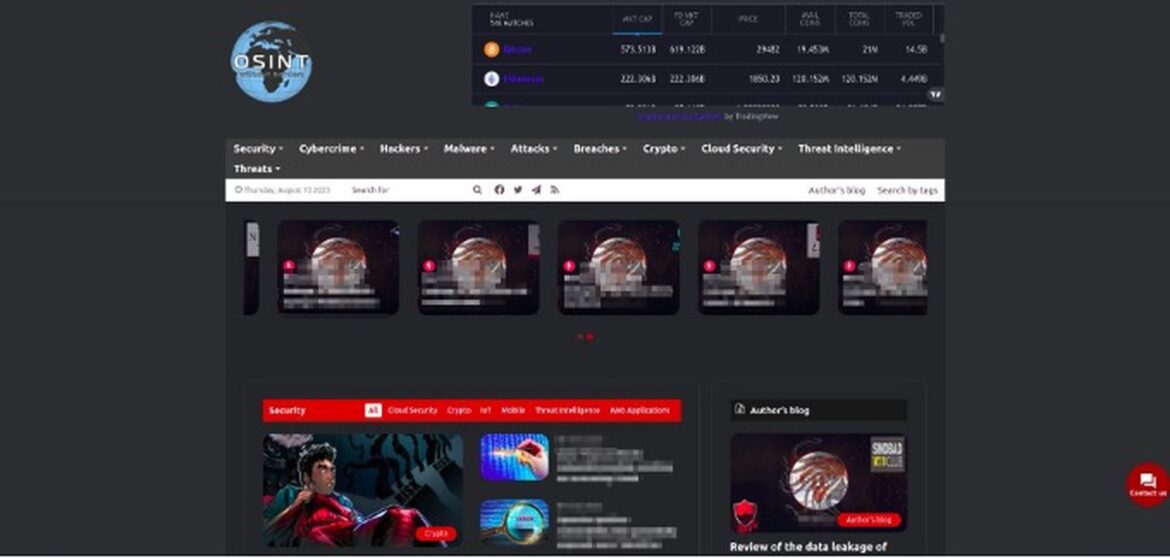
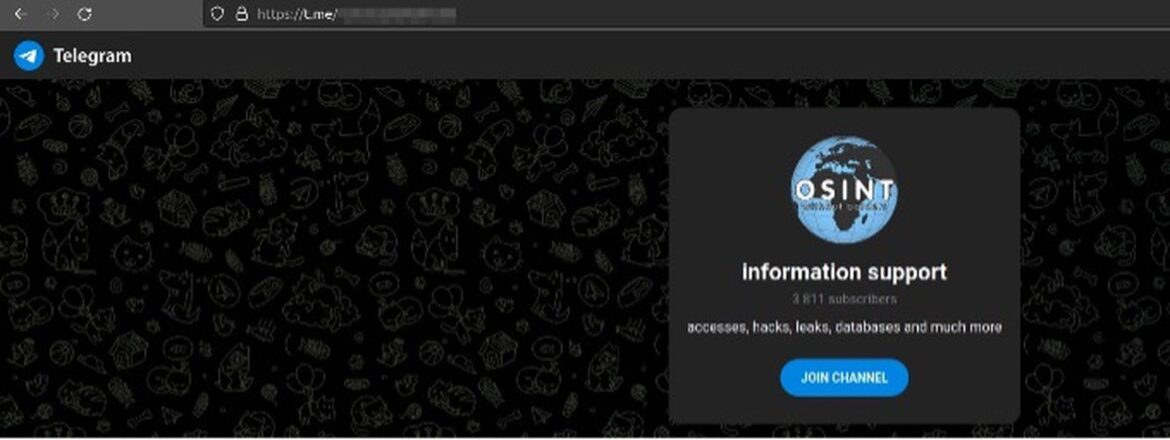
The Medusa group’s page with the onion extension includes the address of the Bitcoin wallet where the ransom will be paid and a Tox address to contact.
Tox is a peer-to-peer instant messaging and video calling protocol that offers end-to-end encryption.
Operational Model
The Medusa group sometimes attacks their targets through their own methods and sometimes through initial access brokers.
The Medusa ransomware group gains initial access to victims’ networks by actively exploiting CVE-2023-48788, an SQL injection vulnerability in FortiClient Enterprise Management Servers, and CVE-2023-4966, a critical vulnerability in Citrix ADC cloud servers that allows unauthenticated attackers to exfiltrate session tokens.
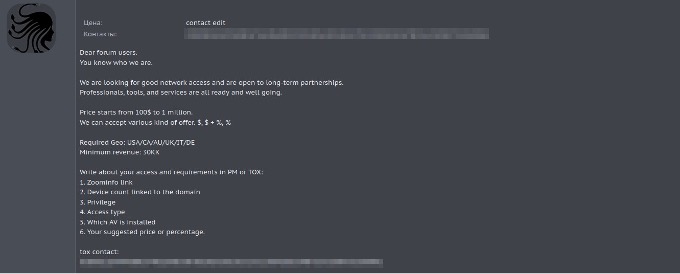
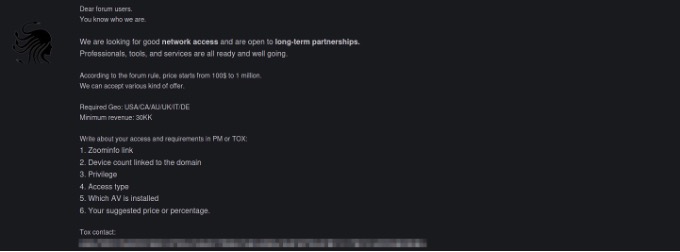
The Medusa group conducts business with initial access brokers on various dark web forums.
Some forum posts associated with accounts identified as belonging to the Medusa group are shown in Figures 6-8.
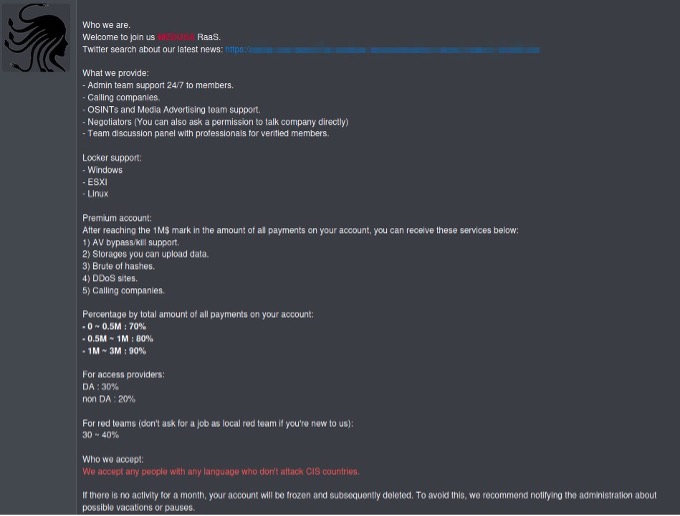
While working with initial access brokers, Medusa only purchases accesses in six countries. These countries are:
- United States
- Canada
- Australia
- United Kingdom
- Italy
- Germany
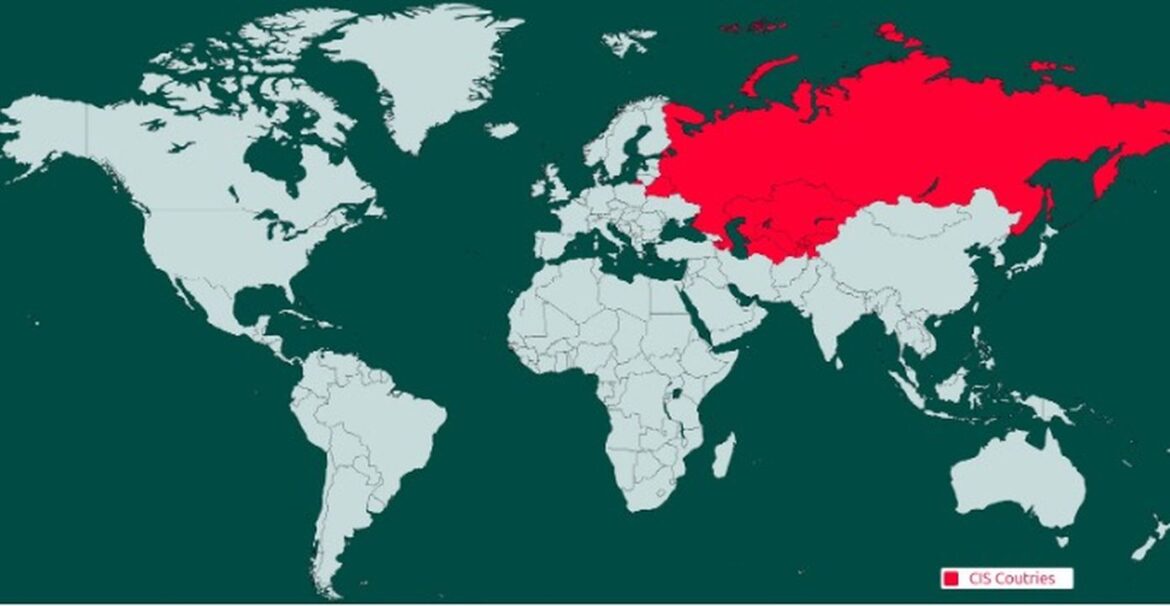
Medusa and its affiliates do not attack CIS countries. These countries are:
- Armenia
- Kazakhstan
- Russia
- Azerbaijan
- Kyrgyzstan
- Tajikistan
- Belarus
- Moldova
- Uzbekistan
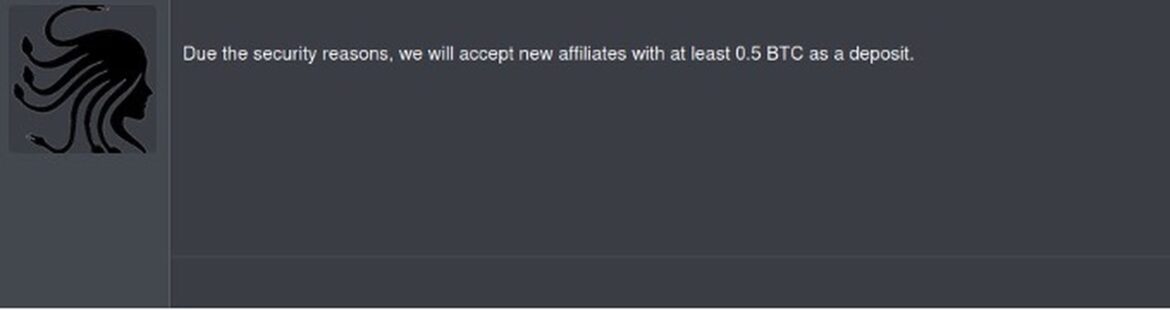
From the second quarter of 2024, for security reasons, Medusa requires candidates for affiliate agreements to maintain a deposit of at least 0.5 BTC in their forum accounts.
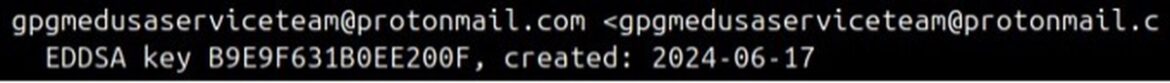
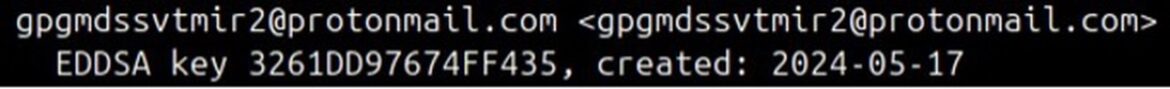
The Medusa group uses TOX and E-Mail for communication. Our research has found that Medusa periodically changes its TOX and E-Mail addresses. For example, when examining the creation dates of the E-Mail addresses
“mds.svt.mir2@protonmail[.]com” and “medusa.serviceteam@protonmail[.]com” used by Medusa, we found a one-month interval between them.
MITRE ATTA&CK Threat Matrix
- TA0002 Execution
- T1059 Command and Scripting Interpreter
- TA0005 Defense Evasion
- T1140 Deobfuscate/Decode Files or Information
- T1070 Indicator Removal
- T1497 Virtualization/Sandbox Evasion
- T1027 Obfuscated Files or Information
- TA0007 Discovery
- T1518 Software Discovery
- T1010 Application Window Discovery
- T1083 File and Directory Discovery
- T1057 Process Discovery
- T1082 System Information Discovery
- TA0040 Impact
- T1486 Data Encrypted for Impact
Mitigation Strategies
- Regular Data Backups: Regular backups of critical data prevent data loss in the event of a ransomware attack. Backups should be stored in isolated environments inaccessible to the ransomware. Regular testing of backups ensures a smooth data restoration process.
- Up-to-date Software and Systems: Keeping software and operating systems updated with the latest security patches prevents the exploitation of known vulnerabilities.
- Employee Training: Regular training sessions should be conducted to help employees recognize phishing attacks and avoid such emails.
- Email Filtering and Threat Detection: Use email filtering and threat detection systems to prevent malicious emails from reaching users’ inboxes.
- Least Privilege Principle: Access rights to user accounts and systems should be limited according to the principle of least privilege.
- Multi-Factor Authentication: Implementing multi-factor authentication to access sensitive systems and data helps prevent unauthorized access.
Conclusion
Medusa Ransomware stands out among modern cybersecurity threats due to its complex structure and advanced evasion techniques. This comprehensive technical analysis of the ransomware reveals its operational mechanisms and impacts on target systems in detail.
Medusa’s powerful encryption algorithms and methods for maintaining stealth demonstrate how effectively attackers can control targeted systems. Its advanced evasion techniques make the detection and analysis of ransomware more challenging. This situation highlights the need for continuous updates and improvements in security software and defense mechanisms.
Medusa’s ability to exfiltrate data before encryption creates additional pressure on victims by threatening data disclosure if the ransom is unpaid. Also, it underscores the importance of robust data protection and backup strategies.
This blog post comes from the Stone Gaze: In-Depth Analsysis of Medusa Ransomware report. If you want to read more details, download it as a PDFclick here






