OCTO malware has many functions, such as recording keystrokes (keylogging), hijacking credentials, bypassing security solutions, and ensuring persistence on the target system. Also, Octo Malware gains remote access capability through the update to ExobotCompact, allowing threat actors to perform on-device fraud (ODF) activities.
ODF is a very dangerous, risky, and unsuspecting type of fraud transaction that is started from the device the targets are using and can be used in other applications available in the system. However, performing such fraudulent activities on the target system requires users to enable Accessibility Services.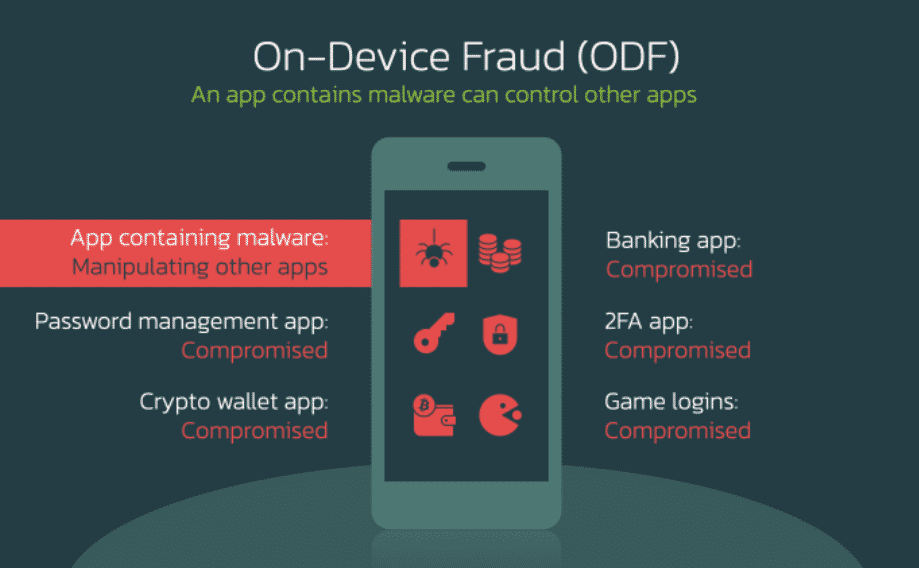 Applications used for the distribution of malware are as follows:
Applications used for the distribution of malware are as follows:
- Pocket Screencaster (Com.Moh.Screen)
- Fast Cleaner 2021 (Vizeeva.Fast.Cleaner)
- Play Store (Com.Restthe71)
- Postbank Security (Com.Carbuildz)
- Pocket Screencaster (Com.Cutthousandjs)
- BAWAG PSK Security (Com.Frontwonder2)
- Play Store App Install (Com.Theseeye5)
OCTO trojan distributed through the above applications can also be distributed via fake Google Chrome or Play Store updates. OCTO’s capabilities to capture screen contents in real-time and record keystrokes allow threat actors to capture entered credentials, a lock pattern or PIN code used to unlock the device, and user data stored in browsers.
Based on the different communication techniques established by OCTO with command and control (C&C) servers, multiple different threat actors are thought to be behind the attacks. It has been foreseen that attacks using malicious software with financial motivation such as OCTO, Cerberus, and Medusa will continue to increase.
To not be the target of similar campaigns, it is recommended to download applications/programs from reliable official sources, check the permissions requested by the applications, keep the applications downloaded to the devices to a minimum, and use Anti-Virus/Anti-Malware solutions.






