Adobe Acrobat Sign allows registered users to send document signing requests to anyone. This will create an email that will be sent to the targeted recipients containing a link to the document (PDF, Word document, HTML) that will be hosted on Adobe’s servers. The sender can also add text to the email, which is an important detail that can be easily exploited by cybercriminals.
Attack Vector for Adobe Acrobat Sign
The observed malicious software campaign starts with threat actors sending a signature request email to recipients from the email address adobesign@adobesign.com, which is a valid email address.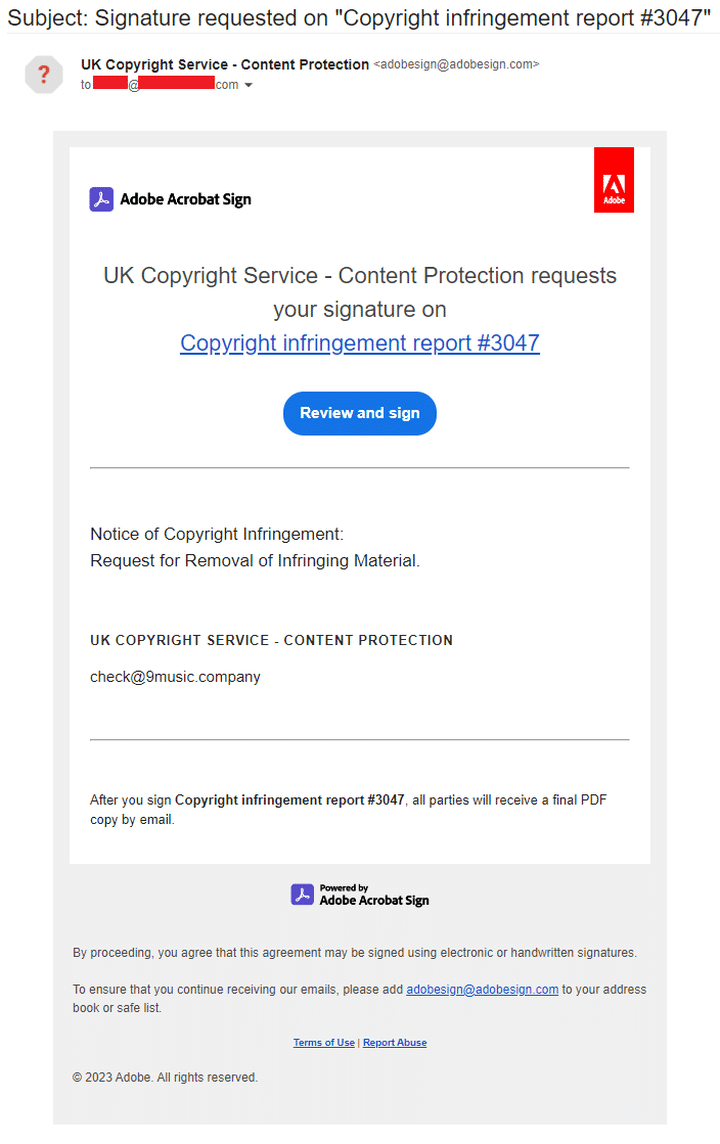
Threat actors add a link to the fake document that recipients are expected to sign, which allows them to review the content before signing. When recipients click on the link, they are redirected to another site where they are asked to enter a fixed encoded CAPTCHA. Once the CAPTCHA is entered, they are prompted to download a ZIP file containing a Redline Trojan variant designed to steal passwords, crypto wallets, and more.
The same malicious software campaign has been observed to be executed using different methods towards the same target.
Protection and Solution Recommendations
- Emails, attachments, and links from unknown sources should not be trusted or clicked.
- Comprehensive and reliable security solutions should be used, and the IoCs (indicators of compromise) identified in the relevant campaign should be blocked by these security solutions.
RedLine Continues to Be Used Frequently
On 9th August 2022, Avast security researchers identified multiple business accounts on social media that distribute the Redline Stealer malware, which is responsible for capturing users’ login credentials from infected systems.
The Redline entering the malicious software group first showed itself with Covid-19 in 2020 with Spear Phishing attacks. In the beginning, Redline began to serve in the form of MaaS (Malware as a Service) in Russian Underground forums.
The malware distribution campaign was identified through a sponsored post on Facebook promoting free Adobe Acrobat Reader software. The post in question was shared via the Facebook business account of Viu Internet, an internet service provider in Brazil.
The post contains a link redirecting destinations to the “Mediafire.com” platform instead of “Adobe.com.” By clicking the link in the post, the files on the storage and sharing platforms are requested to be downloaded to the systems. Readline Stealer injection requires visitors to download the file, extract the content from the archive, and run it.
Viu Internet warns users who visit their homepage that their Facebook account has been hacked. In addition to Viu Internet’s Facebook account, several hacked Facebook business accounts have been found to post the same malicious content.
In this context, it is recommended to consider the following security warnings to avoid being the target of malware campaigns that can be carried out with similar methods.
- Emails, attachments, and links from unknown parties should not be respected.
- Advertisements and links in social media content should not be opened.
- Downloads of files, programs, or applications should be done from trusted, legitimate sources.
- Comprehensive security solutions (Anti-Virus/Anti-Malware) should be used.






