This research aims to share the Top 3 Different Stealer Malware behaviors and their properties. Malicious software attacks and their impacts continue to grow rapidly in early 2022.
Cyber threat actors and Stealer Malware developers mostly use MaaS (Malware as a Service) solution. MaaS is the lease of software and hardware for carrying out cyber attacks. Owners of MaaS servers provide paid access to a botnet that distributes malware. Typically, clients of such services are offered a personal account through which to control the attack, as well as technical support. Hackers usually buy this service on the Dark Web.
Raccoon, RedLine, and Vidar Stealers explained in this report are as follows;
- Definition, Attack, and MaaS Statistics
- Malicious Properties
- Spreading and Evading Techniques
This research can help private, and public sector organizations deal with the effects of stealer malware. It provides actions to help organizations prevent malware infection and also steps to take if systems are already infected.
Raccoon Stealer
Definition of Raccoon Stealer
Raccoon Stealer is a type of malicious software used as a MaaS (Malware as a Service), and it’s been actively developing since 2019. Malware developers have supported Raccoon to help their customers’ needs and technical requirements. This model provides Raccoon’s gloating users with an account in which they control cyber attacks (C2 Panels). So even people without technical skills can launch cyberattacks quite easily.
Statistics
Raccoon Stealer can be obtained for a subscription and costs $200 per month. There are 3,383 different Raccoon samples found on the Internet. So, it has already managed to infect 100,000 devices and become one of the most mentioned viruses in cyber security.
DarkMarket platforms that sell Stealer Logs offer 982,299 different computer systems from all over the world. The Raccoon Stealer malware has infected those systems, and all users have suffered critical information leakage like credit card numbers, social media accounts, corporate emails, etc.

Raccoon Stealer Properties
Malicious software is written in C++ by Russian-speaking developers, and it spreads on Russian-speaking hacking forums or messaging services. Raccoon Stealer usually abuses advertising networks, adding sneaky redirects to a malicious page. These malicious pages are linked with exploit kits which help to download the Raccoon malware.
Threat actors are also leveraging malicious files attached to phishing emails embedded with macros. Attached files download and execute the Raccoon Stealer on the targeted systems. Once the Raccoon Stealer is injected, it targets all the applications that contain credentials. Then, it dumps the credentials in a zip file and sends the zip file back to the C2 server of the attacker.
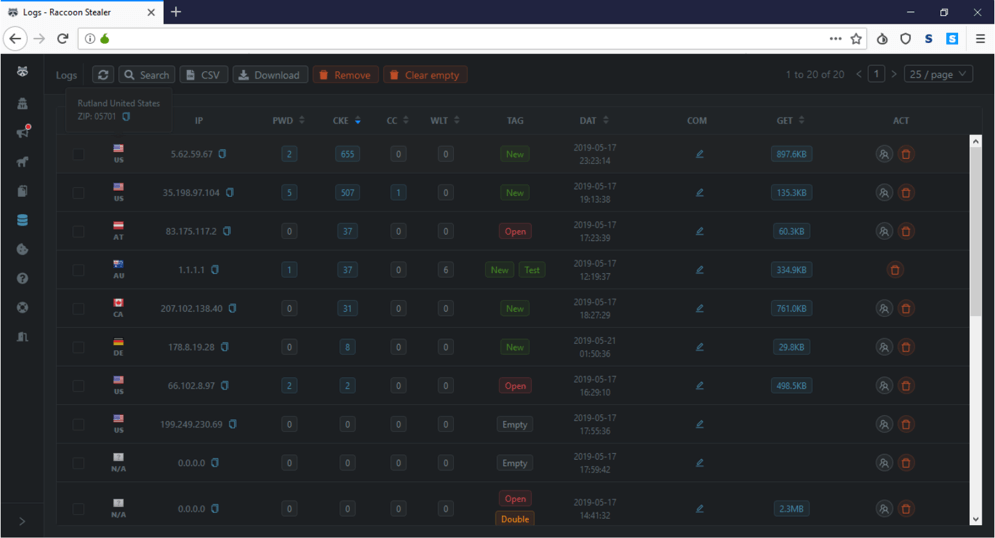
Ongoing Raccoon Stealer campaigns on underground dark web forums are in progress, and threat actors are advertising, selling stolen data with the help of malware.
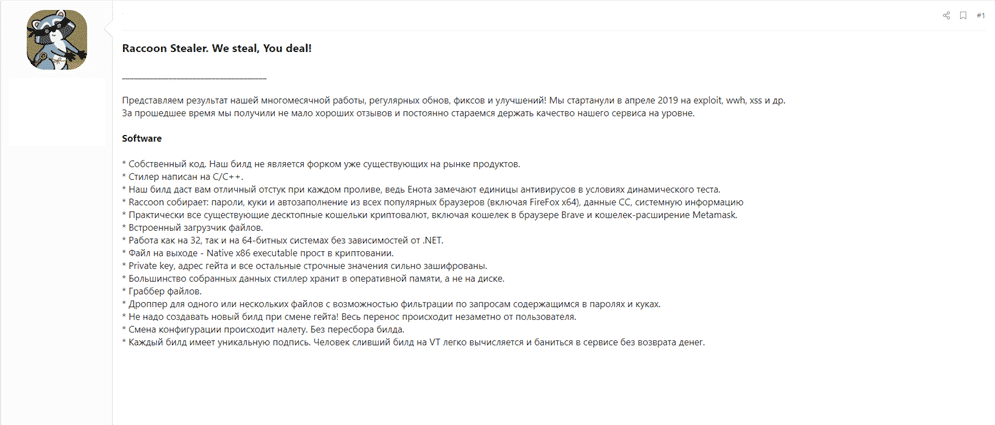
- The Raccoon Stealer is capable of:
Identifying applications, including web browsers that use credentials. It dumps user-sensitive data from these applications. - Steals sensitive data from about 60 different applications, including financial credentials like; browsers, cryptocurrency wallets, emails, VPN services, and FTP clients.
- Copy the file to its working folder (%Temp%).
- Sending stolen data back to the attacker’s C2 server.
- Stealing login credentials leads to other forms of targeted attacks.
- Storing stolen data in RAM, not harddrive.
- Perform the specific routines for the application in order to extract and decrypt the related data.
- Working on both 32-bit and 64-bit operating systems.
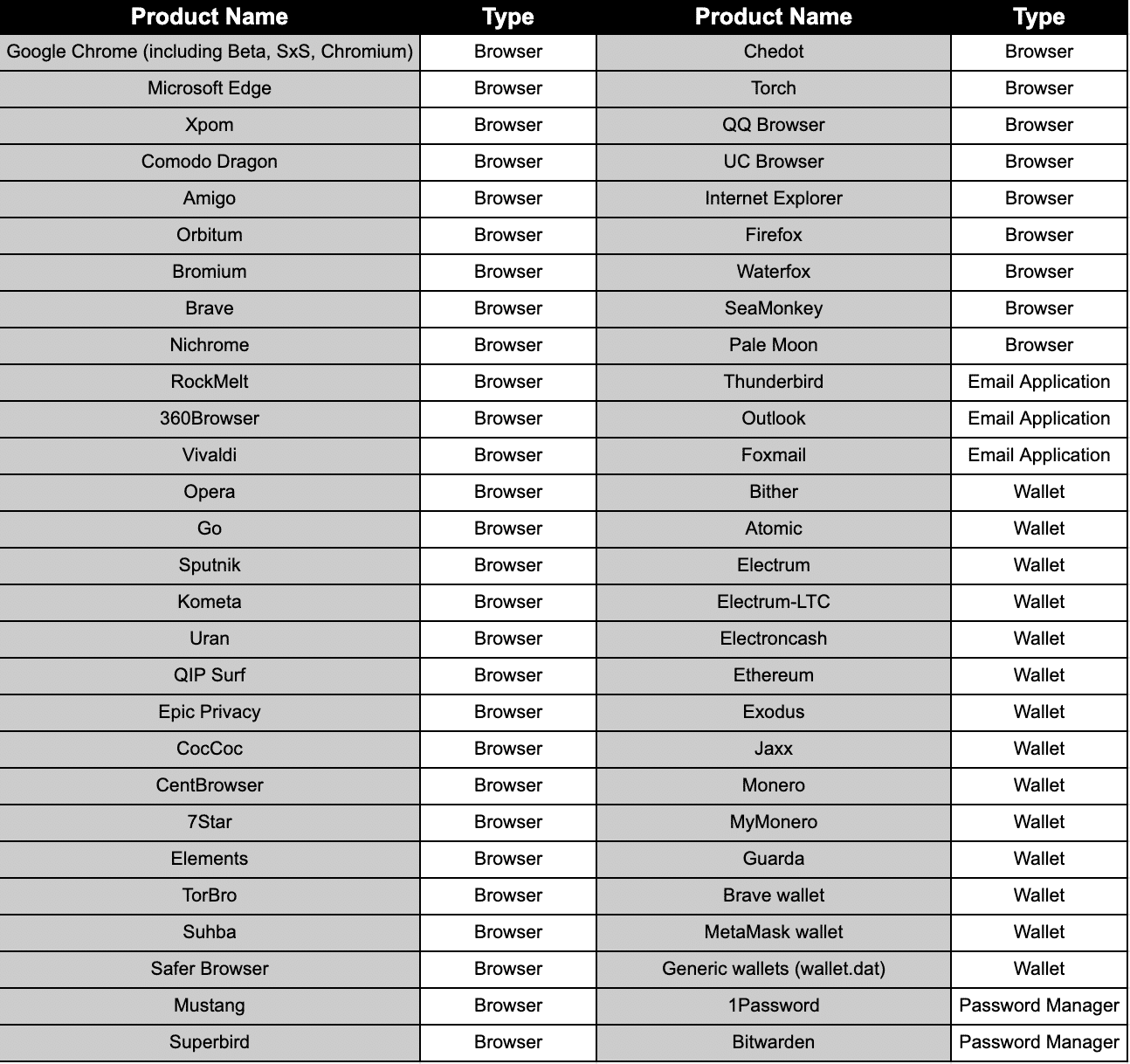
Raccoon Stealer’s information stealing target application list is as follows;
Raccoon Stealer’s Spreading and Evading Techniques
Raccoon Stealer is distributed using multiple channels like browsers. But the most popular destruction method is the use of exploit kits. The malware utilizes mainly the Fallout exploit kit. The Fallout exploit kit used spread malicious advertising methods for attack vectors. This delivery method makes it possible for the infection to occur even without active user interaction. Victims get infected while simply surfing the web.
Malicious files attached to phishing emails embedded with macros are also used as an attack vector to spread Raccoon Stealer. Those macros usually exploit the CVE-2017-11882 vulnerability, which affects Microsoft Office Remote Code Execution – a memory corruption vulnerability in Microsoft Office’s Equation Editor – to drop an embedded executable file, the final Raccoon payload.
After the execution, Racoon Stealer checks for the default user locale set on the infected device, and it does not work if it’s one of the following countries:
- Russia
- Ukraine
- Belarus
- Kazakhstan
- Armenia
- Tajikistan
- Uzbekistan
The stealer operates through a Tor-based command-and-control (C2) server to handle data exfiltration and victim management. Each Raccoon executable is tied with a signature specific to each client. And the new variant has the capability to store and update its C2 addresses that are stored on Telegram’s infrastructure.
During the C2 communication, Raccoon uses more creative ways to spread malware. Buer Loader and GCleaner software were used to spread Raccoon Stealer. Threat actors are also using fake game cheats, patches for cracked software, hacks, and mods for Fortnite, Valorant, NBA2K22, and other gaming software.
This kind of information stealer can cause a lot of damage to individuals and organizations. Proactively protecting vulnerable endpoints is critical to improving an organization’s overall security posture.
Redline Stealer
Definition of Redline
The Redline entering the malicious software group has first showed itself with the Covid-19 in 2020 with Spear Phishing attacks. In the beginning, Redline began to serve in the form of MaaS (Malware as a Service) in Russian Underground forums.
The Redline emerged with many different pricing was spread quickly with relatively fair prices.
It is designed to collect information from the Microsoft Windows platform and steal valuable assets from an infected system.
RedLine has present in the form of options such as weekly (100$), monthly (150$), and lifetime (800$), which are presented to the sale via Telegram. Malware can be purchased and paid for in Bitcoin, Ethereum, XMR, LTC, and USDT on the Telegram channel.
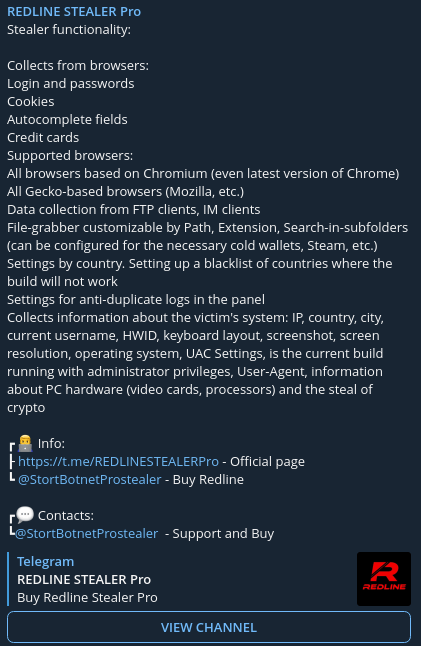
Statistics
According to our research, we only found that the data of 15,200,68 different systems were affected by Redline stealer malware on the single DarkMarket. This table shows how prevalent and dangerous the Redline malware is.
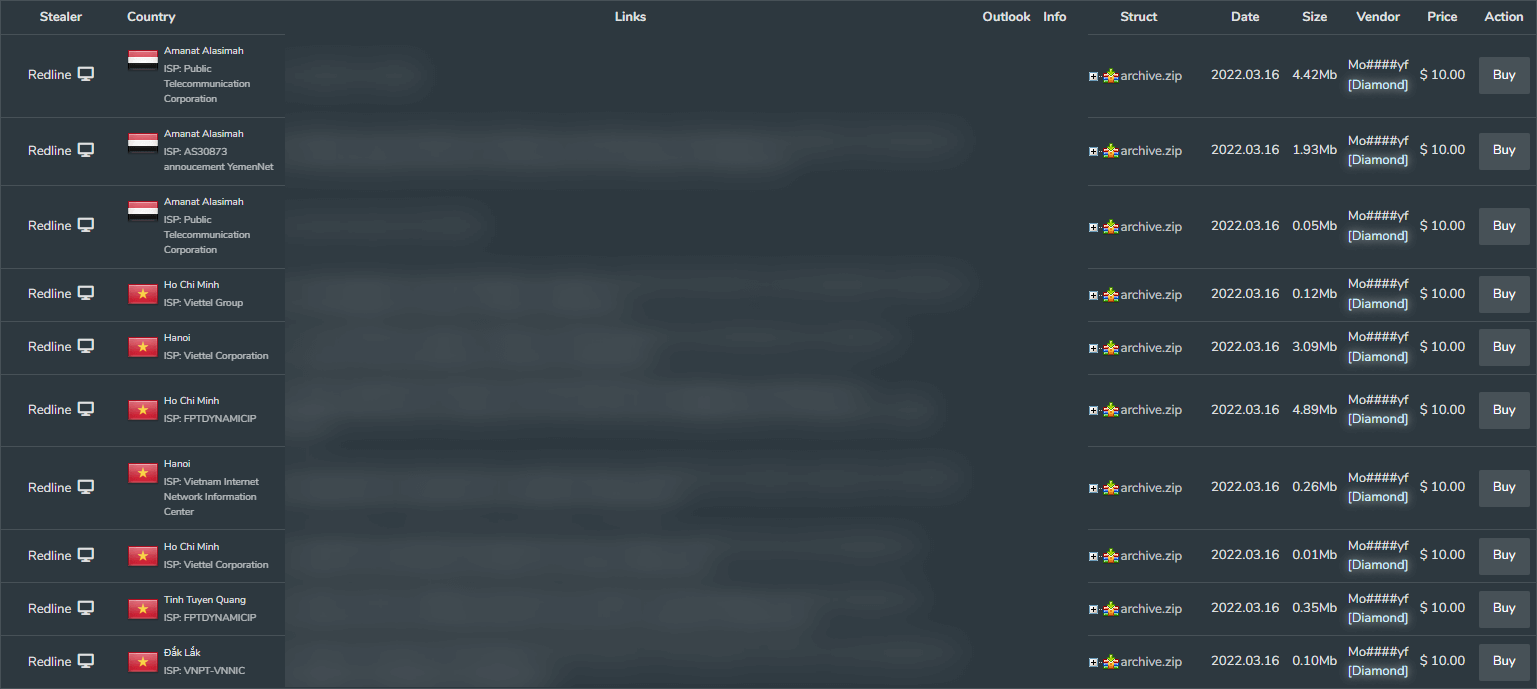
According to the report taken over Any.run, the most analyzed malware of the last year is not a coincidence. In this case, it has the effect of being leaked in the Redline Pro version.
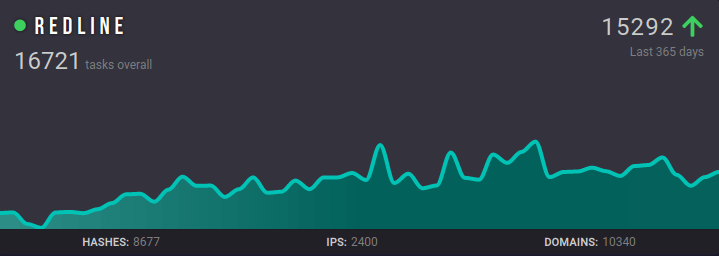
Redline Stealer Properties
Redline is written in C#, actively updated by the developer team, and new features are introduced on the official Telegram channel. Unlike malicious software with other MaaS models, the C&C panel is a GUI program installed on a custom Windows server. C&C Panel basically features we have seen in most stealer malware.
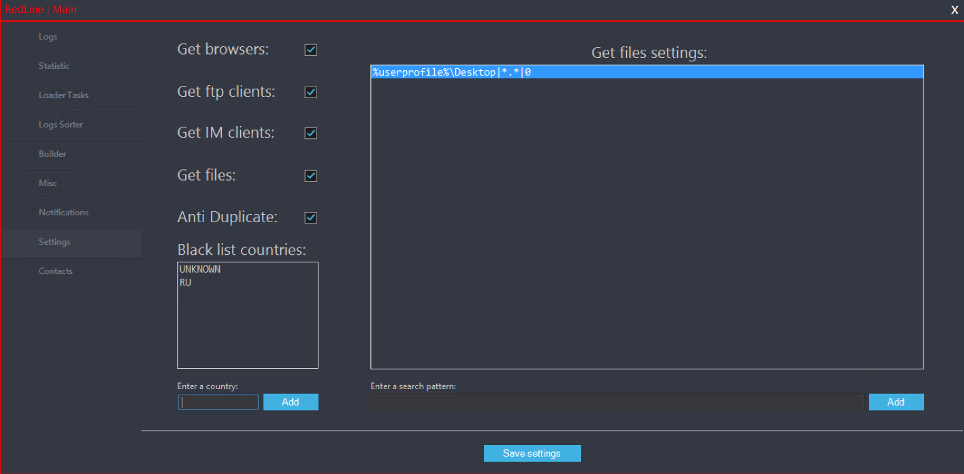
Redline takes advantage of Telegram API to inform criminals about new infections easily. After receiving a notification through a Telegram channel, the threat actor can interact with the Redline agent installed on the victim’s device using the C2 panel installed on a Windows machine.
Although this malware is equipped with many modern features, Redline does not use cryptography to create a secure channel when communicating with the C2 server. As a result, all packets and data are easily identifiable.
Redline Stealer is capable of:
- Identifying applications, including web browsers that use credentials. It dumps user-sensitive data from these applications.
- Steals sensitive data from about 40 different applications, including financial credentials like; browsers, cryptocurrency wallets, emails, VPN services, and FTP and IM clients.
- Steal login credentials lead to other forms of targeted attacks.
- Sending stolen data back to the attacker’s C2 server.
- Downloading a file to the victim by directly linking to a specified path in the system and then running capabilities.
- To be able to grab specially searched files with written rules.
Redline Stealer’s information stealing target application list is as follows;
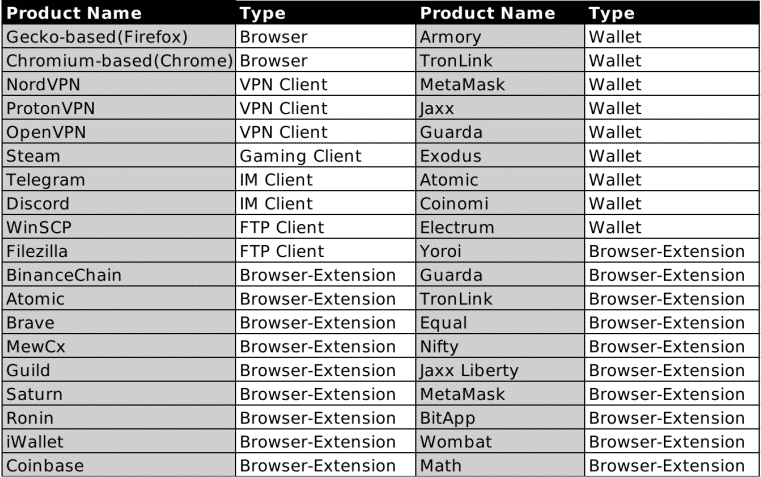
Redline Stealer’s Spreading
When distributing malware, threat actors often use repeated methods. The majority of these methods involve social engineering attacks. The Redline malware under investigation is typically spread in 3 headings.
- Spear-phishing emails
- Cracked software
- Malicious advertising campaigns
As another malware distribution method, it distributes itself as cheat software files of popular games like Valorant, CS:GO, etc.
Redline has been used in numerous small campaigns by threat actors who purchase malware. Therefore, the Redline malware family has hit many known infection vectors, malware campaigns, and targets.
In general, we should pay attention to the following file formats.
- RAR and ZIP files
- Office programs
- Executable files
In addition to these techniques, Redline stealer can also infect these zombie computers purchased from large botnet traffic providers.
Vidar Stealer
Definition of Vidar Stealer
Vidar is a dangerous malware that steals information and cryptocurrencies on infected systems. It is named after the ancient Norse god of vengeance. Vidar, this enhanced variant of the Arkei Stealer malware, has been actively used in attacks since 2018.
The malware is configured to stop execution if it detects that it is running on a machine located in a former USSR country or whose language is configured in Russian. The assumption is that threat actors of Russian origin distribute this malware.
Statistic
Vidar, which can be purchased as a MaaS (Malware as a Service) model, is priced at $700 for the PRO version on its “official” website. However, simplified malware versions also appear to be sold on underground forums for $250.
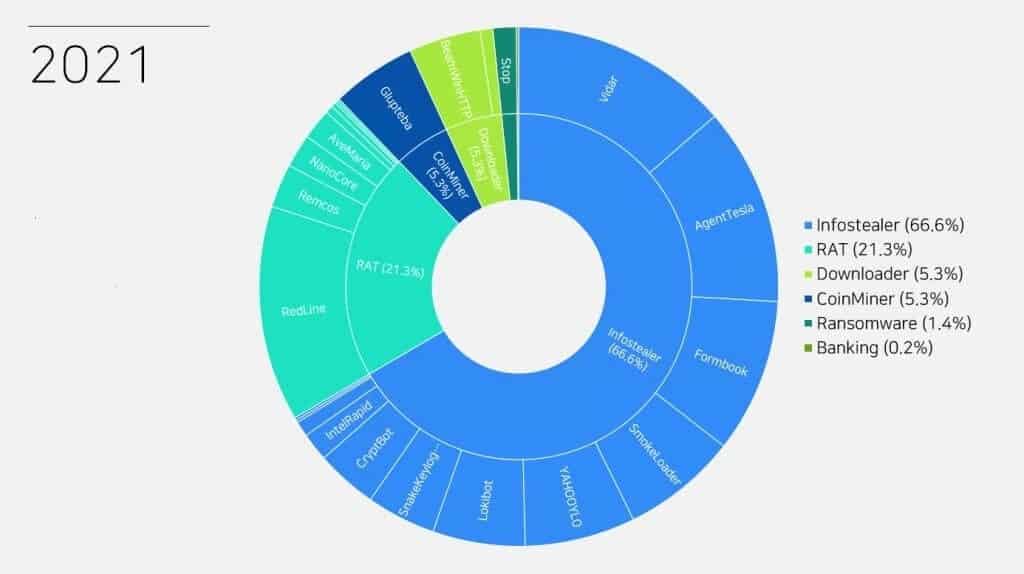
Looking at the statistics of Stealer Malware distributed in 2021, it is seen that Vidar Stealer has a large share.
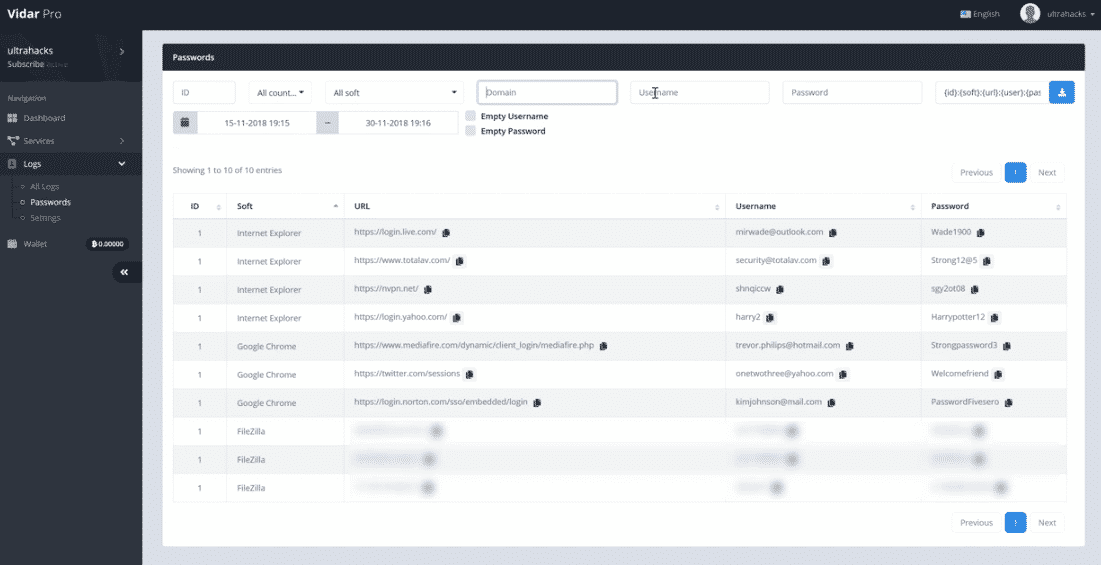
Vidar Stealer Properties
Vidar Stealer is written in the C++ programming language. A purchased Vidar Stealer account gives threat actors access to a control panel where they can set the malware to target specific information on the targets’ computer. The control panel displays the current renderer version, user settings, malware status, and logs. In addition, domain names are changed every four days so that the C&C servers to which the seized data are transferred are not detected.
Vidar Stealer is spread by ‘Malwertising’ methods, usually where a user clicks on an infected advertisement found on websites they visit. Other forms of spread include spam messages, phishing pages, cracked software.
Vidar also can seize digital currencies from offline wallets. Holders of Litecoin, Bitcoin, Ethereum, Zcash, and DashCore are potentially in danger as they are the cryptocurrencies that Vidar supports. After collecting the targeted information, the malware archives it and sends the data to the C&C server. Then Vidar erases the traces of his work and deletes himself from the system.
The Vidar Stealer is capable of:
- The malware has the ability to leak various data from an infected system, including system information, browser data, and credentials.
- Data collected from affected systems include Machine ID and GUID, operating system, computer name, current user name, screen resolution, keyboard language, hardware information, network information, and a list of installed software.
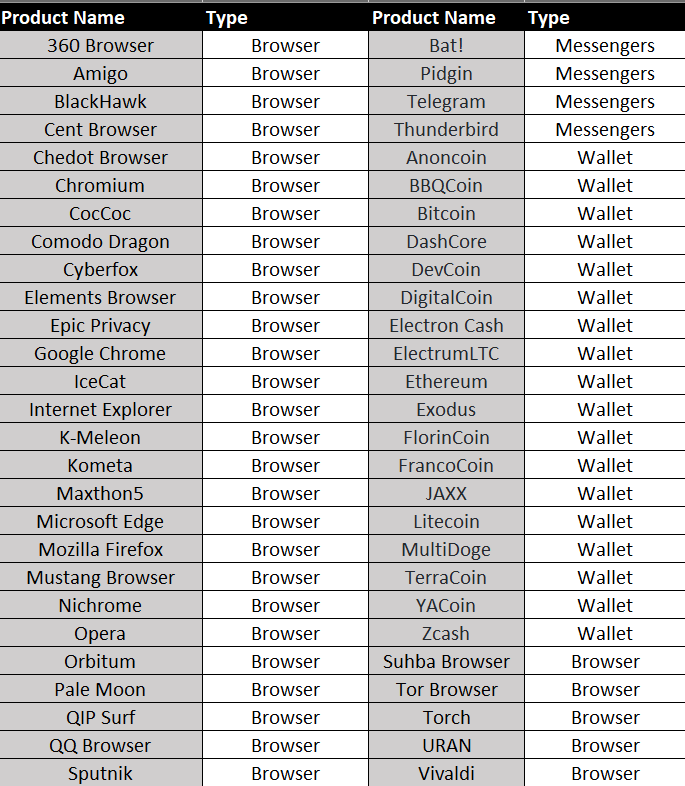
Vidar Stealer’s information stealing target application list is as follows;
Vidar’s Spreading
Vidar Stealer is distributed via spam emails, advertisements, and phishing pages. Also, cases where Vidar was distributed using cracked software, were existed. For example, the recently detected Vidar Stealer is mainly disguised as Windows activation software. Because licensed Windows products are paid, many users download illegal activation software to use for free.
Another recent cyber attack has been detected that Vidar was using a social media platform called Mastodon to generate C&C server addresses.
Finally, in another scenario, it was observed that Vidar abused the game matching program “Faceit” to generate a C&C server URL.

In addition, the Vidar info stealer targets various countries except for some former USSR countries, including Russia. Some of these are those;
- NATO Countries
- Poland
- Estonia
- Latvia
- Lithuania
Mitigation & Conclusion
Since there’s no way to completely protect all computer systems against malware attacks, people should adopt a ‘defense-in-depth’ approach. This means using layers of defense with several mitigations at each layer. This approach will create more opportunities to detect malware attacks and then stop them before it causes real harm to computer systems.
Assuming that some malware will infiltrate, some steps must be taken to limit the impact this would cause and speed up the response;
- Install the latest security patches and updates for operating systems.
- Avoid Using Torrent Sites.
- Avoid clicking on ads hosted on web pages.
- Avoid saving user credentials on web browsers.
- Activate 2FA/MFA solutions on all personal/business user accounts.
- Use the latest AV, prevention, and detection software.
- Continuous monitoring of unusual endpoint behaviors.
- Segment the network to hinder proliferation across the environment.
- Raise awareness against phishing campaigns.
- Ensure that email security controls are applied, such as DKIM, DMARC, and SPF.
- Invest in user training and build a culture of cyber security.
Also, there are some actions you can take to detect malicious documents;
- Never configure Microsoft Office to enable macros by default. Many malware families use macros as an infection vector.
- Do not enable macros in Microsoft Office attachments, especially if the file’s only apparent contents are directions to enable macros.
- Always be suspicious of unexpected emails, especially regarding financial or delivery correspondence, documents, or links.
- Exercise caution if it is necessary to open emails with generic subject lines.
- Verify significant or potentially legitimate attachments with the sender via alternative means (e.g., by phone or in-person) before opening them.
Authors:
Ali Yılmaz
Berk Baykan
Burçem Güloğlu






