The vulnerability, AttachMe, compromises the security of cloud isolation by allowing threat actors to access other users’ OCI storage volumes without permission, capture and modify sensitive data stored on the volume, and execute code on affected systems. Successfully exploiting the vulnerability requires threat actors to capture the Oracle Cloud Identifier provided to an Oracle Cloud Infrastructure user and insert it into their Oracle Cloud virtual machine. Oracle Cloud infrastructure does not have a security mechanism that checks who owns this identifier. Therefore, threat actors can easily add the identifier to their virtual machines and gain access to the storage units of the Cloud customer that owns the identifier.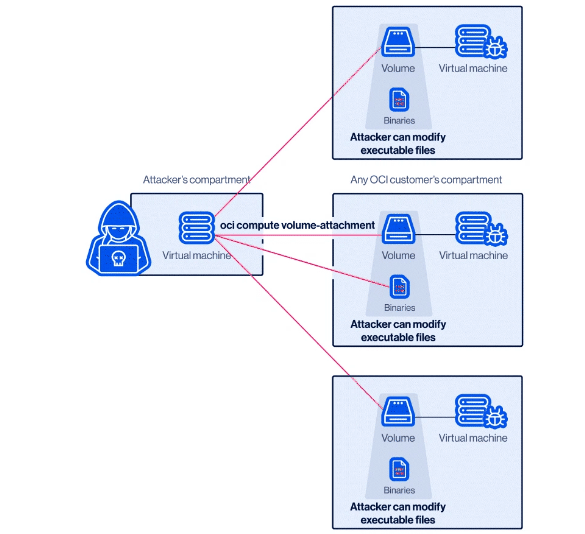
AttachMe: The Critical Vulnerability in Oracle Cloud Infrastructure
- Categories
- Latest News
-
 FishMonger APT Group: A Persistent China-Aligned Cyber Espionage Actor
FishMonger APT Group: A Persistent China-Aligned Cyber Espionage Actor -
 Dark Caracal APT Group (G0070): Mobile-Centric Espionage and Regional Surveillance
Dark Caracal APT Group (G0070): Mobile-Centric Espionage and Regional Surveillance -
 LIMINAL PANDA: China’s Emerging Espionage Threat in the Semiconductor and Technology Sectors
LIMINAL PANDA: China’s Emerging Espionage Threat in the Semiconductor and Technology Sectors -
 Reynolds Ransomware: BYOVD Evasion & NSecKrnl Abuse
Reynolds Ransomware: BYOVD Evasion & NSecKrnl Abuse -
 Winter Vivern (TAG-70 / UAC-0114 / TA473): A Persistent Eastern European Cyber-Espionage Threat Targeting NATO and EU Governments
Winter Vivern (TAG-70 / UAC-0114 / TA473): A Persistent Eastern European Cyber-Espionage Threat Targeting NATO and EU Governments
- Follow Us on Social Media!

