A 0-day vulnerability has been identified that allows threat actors to perform code execution activities on targeted Windows systems through Microsoft Office documents. It has been observed that threat actors exploiting the vulnerability called Follina obtain an HTML document from the command and control (C&C) server with the “remote template” feature of the malicious Microsoft Word document and use the ‘ms-msdt’ MSProtocol URI scheme to execute the malicious code on the target system. MSDT is a tool that collects errors that Windows users receive on the system for analysis. Threat actors can execute malicious code on the system with the MSDT tool, even if the targets do not enable macros of Microsoft Word documents. Also, converting the document to RTF format runs the code in the browser without the need to open the document.
MSDT is a tool that collects errors that Windows users receive on the system for analysis. Threat actors can execute malicious code on the system with the MSDT tool, even if the targets do not enable macros of Microsoft Word documents. Also, converting the document to RTF format runs the code in the browser without the need to open the document.
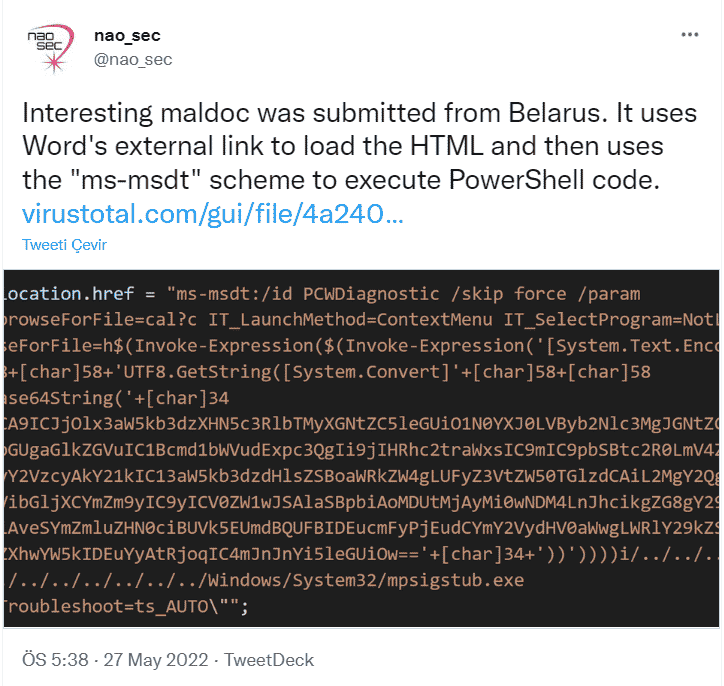 MSDT is a tool that collects errors that Windows users receive on the system for analysis. Threat actors can execute malicious code on the system with the MSDT tool, even if the targets do not enable macros of Microsoft Word documents. Also, converting the document to RTF format runs the code in the browser without the need to open the document.
MSDT is a tool that collects errors that Windows users receive on the system for analysis. Threat actors can execute malicious code on the system with the MSDT tool, even if the targets do not enable macros of Microsoft Word documents. Also, converting the document to RTF format runs the code in the browser without the need to open the document. The malicious Microsoft Word document, which cannot be detected in the Microsoft Defender Anti-Malware solution, affects Office 2016 and 2021 applications. In this context, it is recommended not to open Office documents obtained from unknown parties via e-mail attachments and other vectors, benefit from comprehensive Anti-Malware solutions, and use Office applications in the most up-to-date versions.






