- GoodWill ransomware was developed with .NET and packaged with UPX wrappers.
- It can stay in sleep mode for 722.45 seconds to avoid being detected during dynamic analysis.
- It uses the AES_Encrypt function to encrypt the captured files with the AES algorithm.
- It has a function called “GetCurrentCityAsync” that tries to detect the geolocation of the infected system.
When GoodWill infects systems, it encrypts documents, photos, videos, databases, and other important files with the “.gdwill” extension, making all these elements inaccessible without the decryption key. In the ransom note that the group left on the systems, it is stated that the targets must perform some social activities to obtain the decryption key.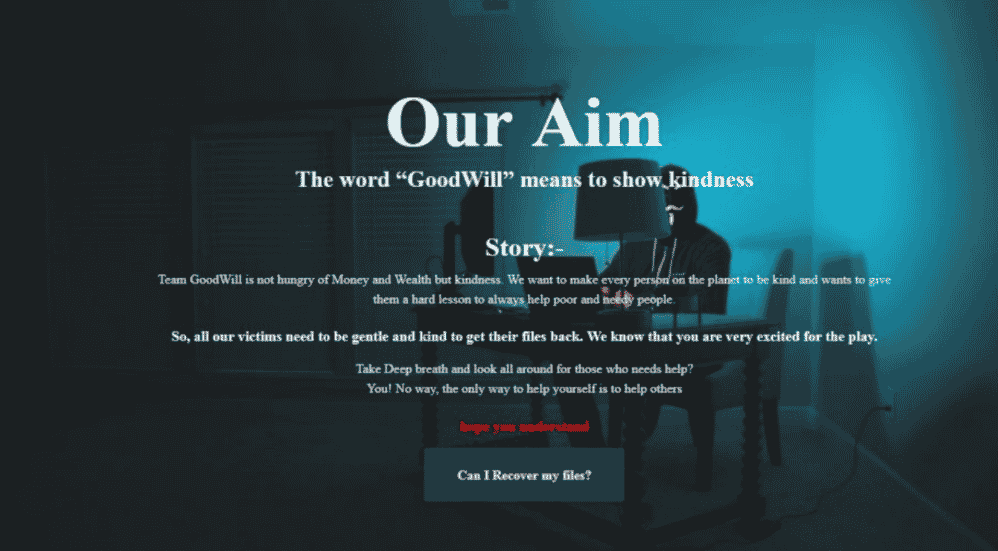 In the detailed analysis of GoodWill carried out by CloudSEK threat intelligence researchers, it has been observed that the ransomware in question has approximately 1246 threads, and 91 of them overlap with the open-source HiddenTear ransomware software developed by an operator of Turkish origin. In addition, the use of Hindi scripts by threat actors in the existing lines leads to the opinion that the group is based in India.
In the detailed analysis of GoodWill carried out by CloudSEK threat intelligence researchers, it has been observed that the ransomware in question has approximately 1246 threads, and 91 of them overlap with the open-source HiddenTear ransomware software developed by an operator of Turkish origin. In addition, the use of Hindi scripts by threat actors in the existing lines leads to the opinion that the group is based in India.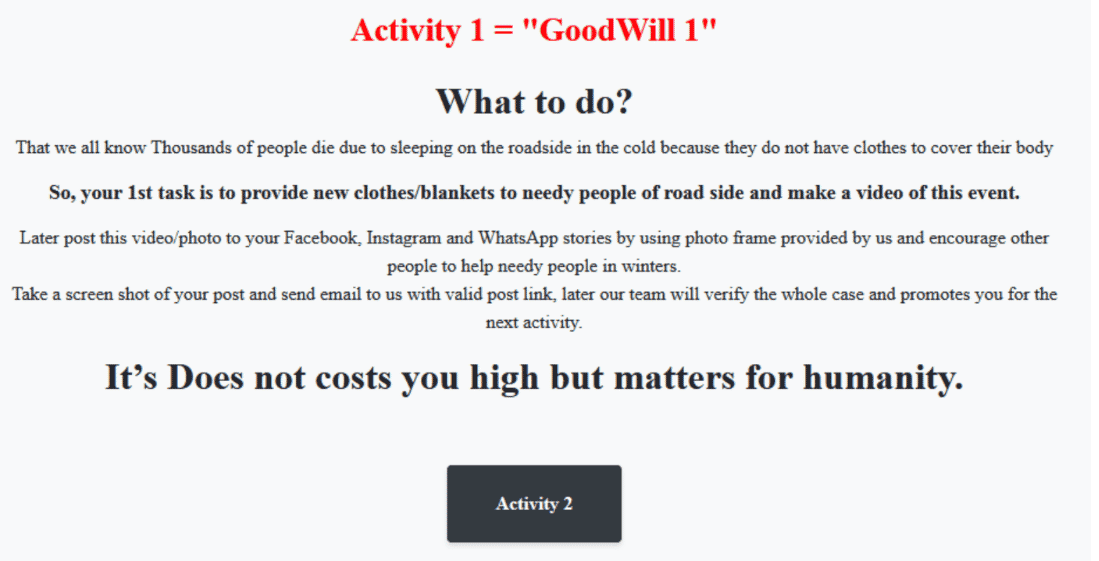 Although the threat actors behind the GoodWill ransomware software claim to operate under the name of social responsibility campaigns, they violate the intellectual property and privacy concepts of institutions/organizations. At the same time, these activities cause the targeted organizations to be unable to provide services, damage their reputation, material, and moral losses, and violate the security of personal information.
Although the threat actors behind the GoodWill ransomware software claim to operate under the name of social responsibility campaigns, they violate the intellectual property and privacy concepts of institutions/organizations. At the same time, these activities cause the targeted organizations to be unable to provide services, damage their reputation, material, and moral losses, and violate the security of personal information.
To not be the target of similar attacks in this context, it is recommended that email, attachments, and links from unknown parties are not respected, and input information used in accounts is created using unique and powerful policies. Also, it is important to use comprehensive security solutions and enable 2FA/MFA features on all possible platforms.






