The campaign started on January 18, 2022, targeting 80 restaurants using MenuDrive and 74 restaurants using the Harbortouch platform. InTouchPOS, on the other hand, was targeted by another MageCart campaign on November 12, 2021, which resulted in e-skimmer infections in 157 restaurants using the platform. It was observed that 50,000 bank card information seized in the campaign, which affected 311 restaurants in total, was put up for sale on Dark Web platforms.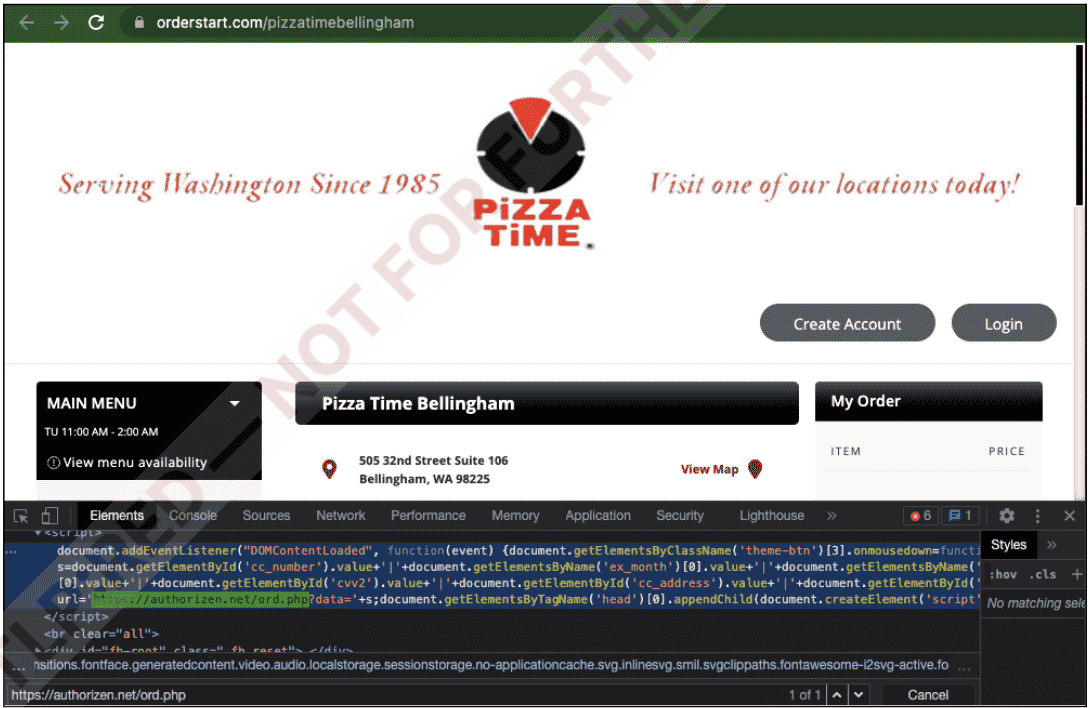
- Personal information should not be entered on unreliable/suspicious websites,
- Virtual cards created for e-commerce transactions should be used,
- Make sure that the visited page is not a fake domain with a similar name created by threat actors,
IOC findings such as IP addresses and domains known to be used by threat actors in these campaigns should be blocked from security solutions in use.






