Hotel chain Marriott International has confirmed that it has suffered a new data breach that resulted in the hijacking of 20GB of internal data by threat actors. In this breach, threat actors compromised the BWI Airport Marriott Maryland (BWIA) network.
About a month ago, threat actors gaining unauthorized access to the BWI Airport Marriott network seized 20GB of data, allegedly containing credit cards, reservations, flight information, and internal confidential business documents belonging to Marriott customers. After the breach, threat actors informed many company employees about the breach. As a result, it is known that Marriott International officials refused the ransom payment demanded by the threat actors and launched a joint investigation with law enforcement officials for the unauthorized access, which was brought under control within about six hours. Images of some documents that are stated to have been seized by the threat actors in the breach are given below:
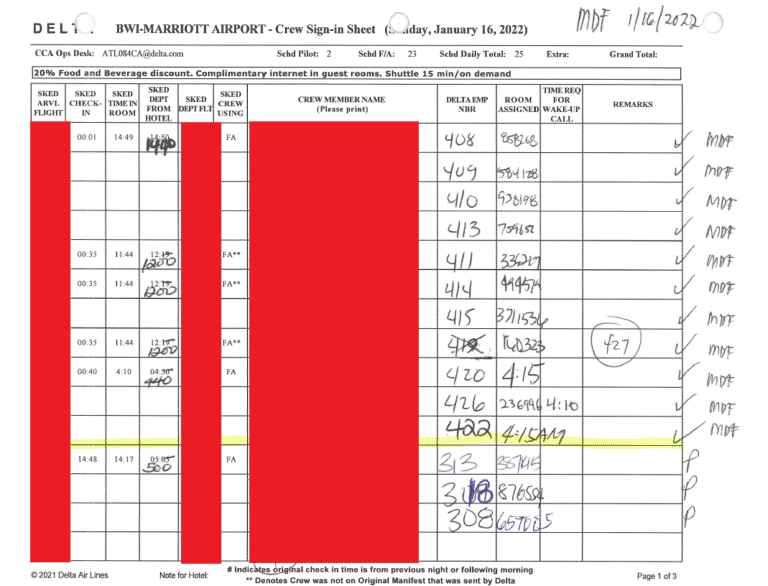
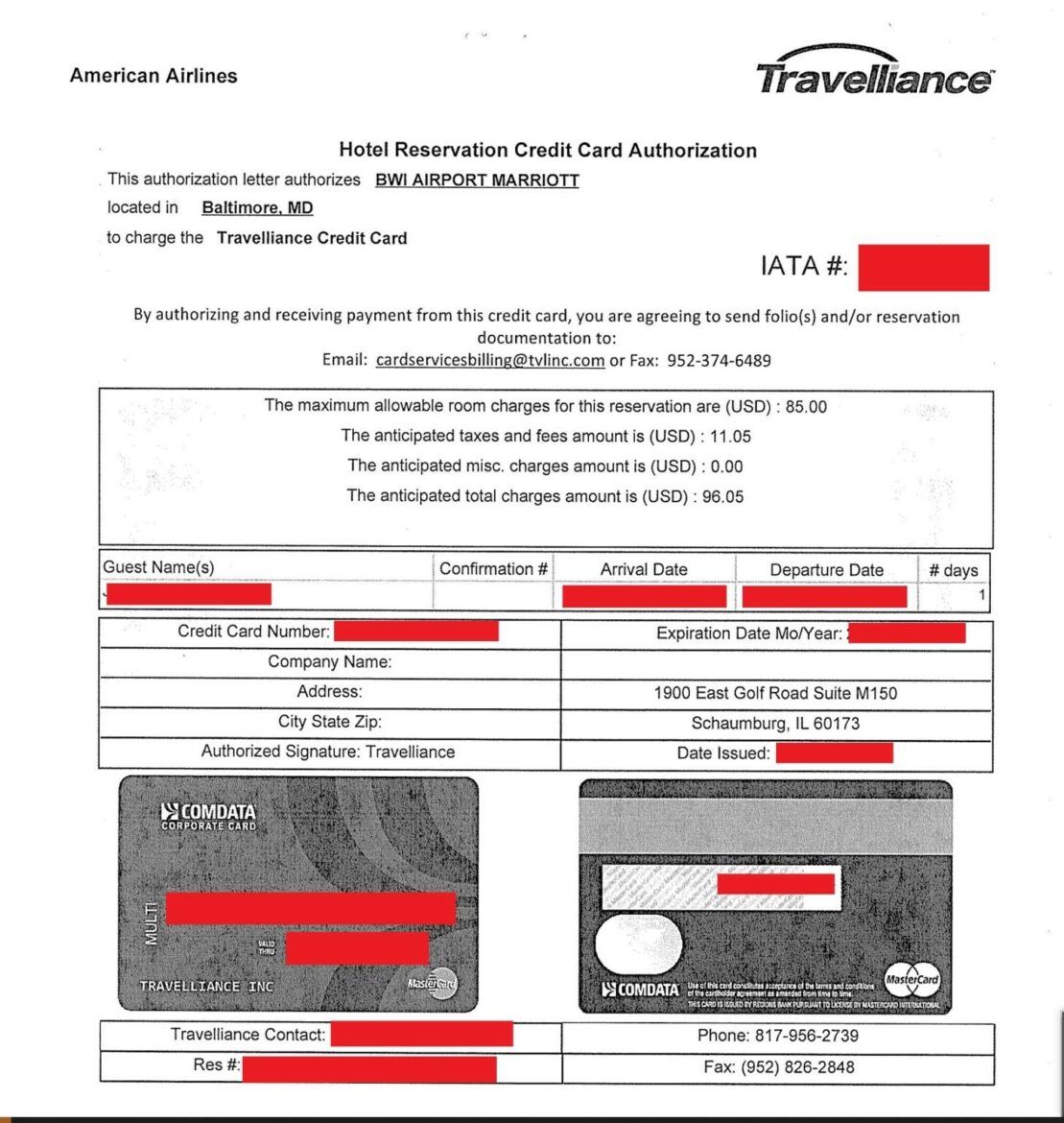
Although Marriott International, known to have been exposed to similar data breaches before, defines the seized data as non-sensitive internal business files, it has announced that approximately 400 people thought to be affected by the breach will be informed of the breach. Therefore, in order not to be the target of similar security breaches that may be carried out in this context, it is recommended to consider the following practices and precautions:
- The system/program or software being used should always be kept up to date,
- Updates and fixes that eliminate vulnerabilities should be applied immediately,
- Institution/organization personnel should be made aware of possible social engineering/phishing attacks,
- Critical system/data should be backed up regularly,
- Comprehensive security solutions should be used,
- Passwords used in accounts should be created using strong policies,
- MFA/2FA authentication features should be enabled on all possible platforms,
- Attack surface analysis tests should be performed regularly in the institution/organization network.
In order not to be the target of similar ransomware attacks that may be carried out in this context, it is recommended to take the following actions;
- Beware of unreliable e-mail content,
- Suspicious e-mail attachments and links should not be respected,
- Using reliable Anti-Malware solutions,
- Using licensed and up-to-date technologies,
- Used security solutions should block shared IOC findings regarding the malware campaign.






