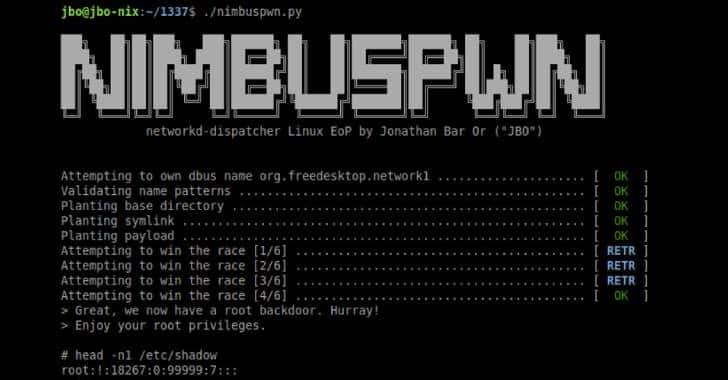
Microsoft security researchers have detected two critical vulnerabilities that could allow threat actors to carry out a series of malicious activities with root privileges on Linux systems. The vulnerabilities collectively called “Nimbuspwn” can be used to gain root privileges on Linux systems and allow threat actors to deploy various malicious software such as backdoor and ransomware to the vulnerable system.
Nimbuspwn security vulnerabilities, tracked as CVE-2022-29799 and CVE-2022-29800, exist in networkd-dispatcher, a component that sends link state changes on Linux machines. The vulnerability tracked as code CVE-2022-29799 exists due to a Directory Traversal error in the _run_hooks_for_state function in the source code of networkd-dispatcher. Another security vulnerability with code CVE-2022-29800 is related to a time-of-check to time-of-use (TOCTOU) error in the _run_hooks_for_state function.