Which APT groups & ransomware gangs were effective this month? The new malware, cyber-attacks, and more are in this monthly analysis.
Exploring Lazarus’ Latest Tactics: DeathNote Campaign Targets Linux and RustBucket Malware Hits macOS
Lazarus APT Group Expands DeathNote Campaign to Target Linux Users and New Sectors
North Korean APT group recently has expanded its tactics to target Linux machines with its long-term DeathNote campaign, also known as Operation DreamJob, Operation North Star or NukeSped. This campaign was first discovered on Windows machines in 2019, targeting job seekers from well-known aerospace and defence companies.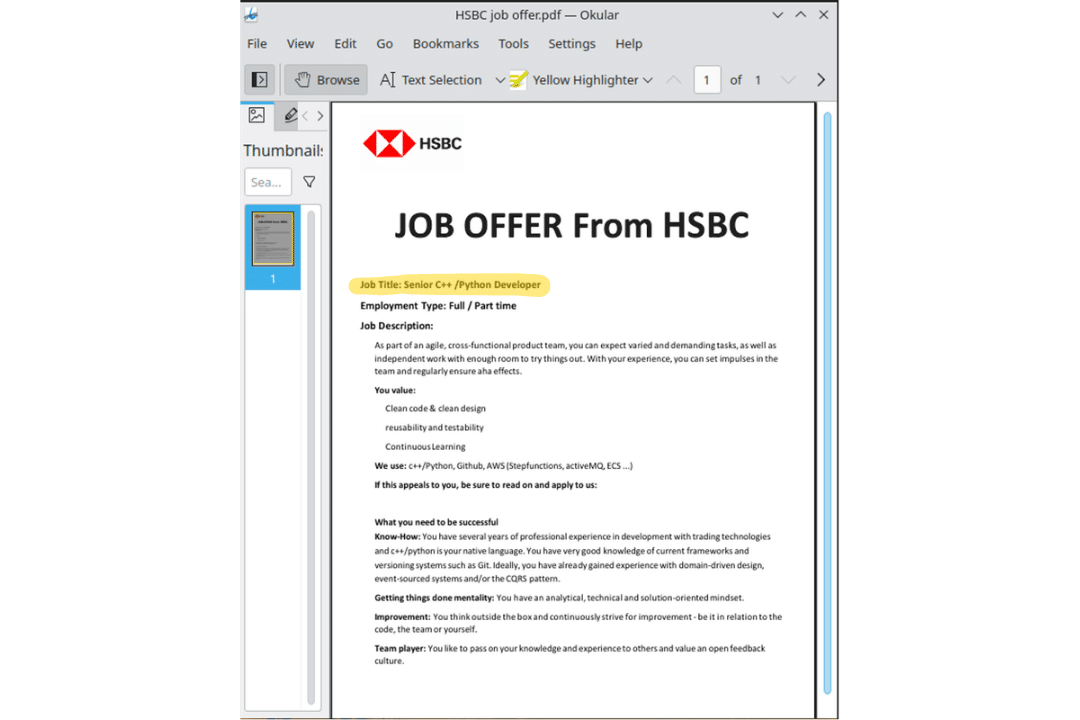
The Lazarus Group is a highly sophisticated Advanced Persistent Threat (APT) group believed to have been active since 2009. Its operations are primarily based on ideological reasons and are state-sponsored. The group has strong links to North Korea, and the US Federal Bureau of Investigation has identified it as a North Korean “state-sponsored hacking organization”.
The group’s primary goals include information theft, money extortion, espionage, and sabotage. Lazarus Group has various aliases such as APT 38, Andariel, Labyrinth, COVELLITE, HIDDEN COBRA, etc. They target defence, pharmaceutical, software businesses, cryptocurrency platforms, and electrical industries. Lazarus’s toolset and related malware have been spotted in 18 countries worldwide, including China, India, Iran, Russia, Saudi Arabia, South Korea, and the USA. The threat group has been responsible for numerous cyber-attacks, including the 2014 Sony breach, the 2016 Bangladesh Bank heist, the 2017 WannaCry ransomware attack, and the 2020 pharmaceutical company attacks.
However, with the recent social engineering campaign, the threat group changed its target and aims to deceive software developers and DeFi platform workers through bogus job offers. The scam involves enticing victims to download what appears to be a PDF file, which is a disguised SimplexTea Linux backdoor containing malicious files.
Researchers also have noted that this month’s DeathNote attacks marked Lazarus’s first use of Linux malware. Furthermore, they have expanded their targets beyond just the cryptocurrency industry. The group has been attacking various sectors, including the automotive, academic, and defence industries.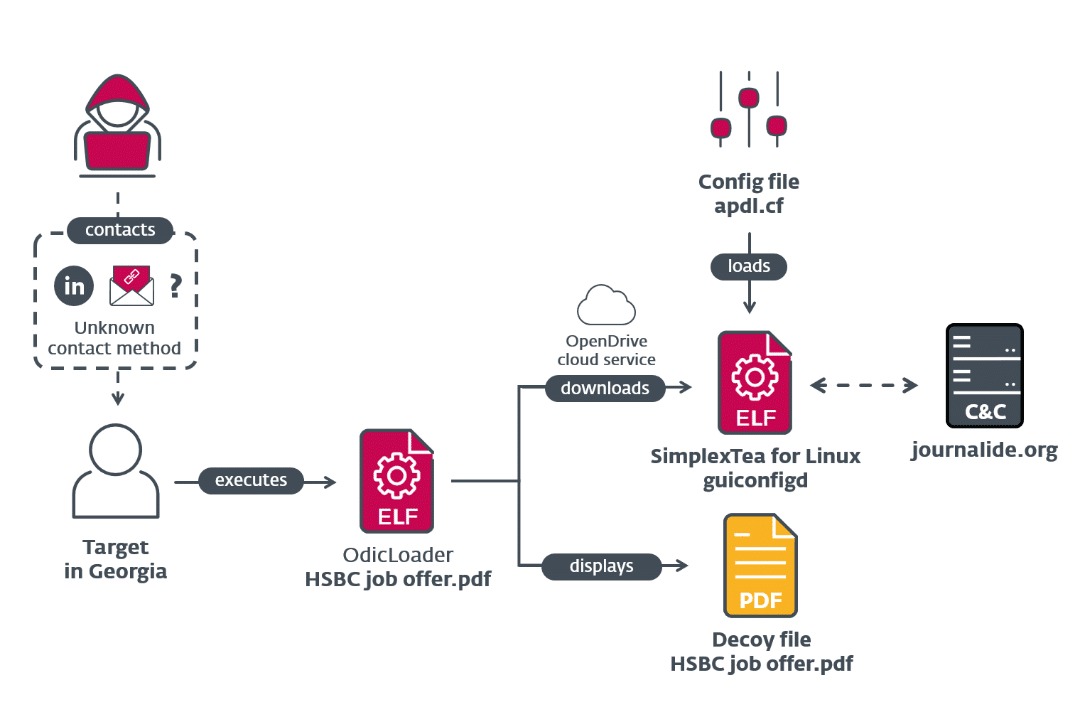
Lazarus’s Sub-Group BlueNoroff Targeting Telecommunication Sector
BlueNoroff, a state-sponsored North Korean Advanced Persistent Threat (APT) group, has gained notoriety for its sophisticated attacks on financial institutions since 2014. The threat group is associated with the Lazarus Group by researchers and focuses on financial gain, emphasizing banks and financial institutions. They employ spear-phishing, malware, and network infiltration to gain access to their targets.
Despite being a subgroup of Lazarus, BlueNoroff is financially motivated and primarily focuses on gaining monetary benefits from its offensive capabilities. In 2016, the group stole $81 million from the Bangladesh Bank and targeted other financial institutions in Mexico, Poland, and Vietnam.
Simultaneously with Lazarus’s Deathnote campaign in April, BlueNoroff was found responsible for another malware campaign recently targeting Apple’s macOS. The malware, called RustBucket, spread through an application disguised as an “Internal PDF Viewer,” an AppleScript file designed to download a second-stage payload from a remote server. The victim must intentionally bypass the Gatekeeper protections for the attack to succeed. When the victim opens a malicious PDF file, the second-stage payload initiates the next attack phase, which downloads and executes a third-stage trojan. And this Rust-written Trojan executes commands to gather information about the system.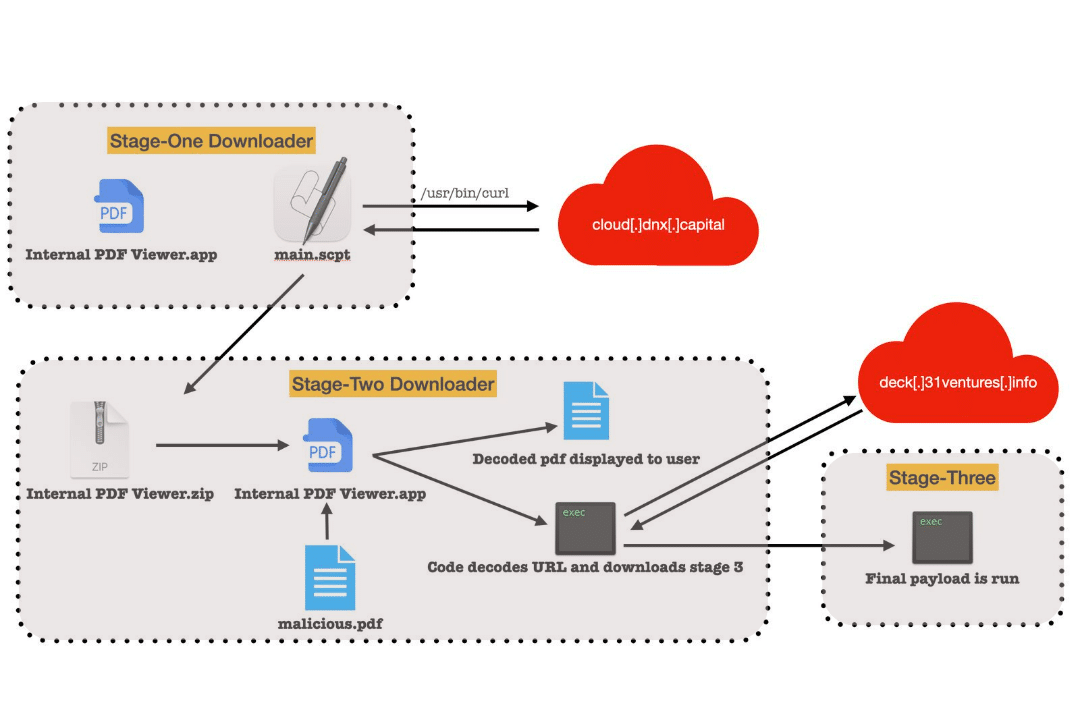
As a result of the malware investigation, it was found that Lazarus is modifying its toolsets to create cross-platform malware using programming languages such as Go and Rust. However, the method used by BlueNoroff to gain initial access to the system remains to be discovered.
Chinese APT Group Alloy Taurus Expands Its Arsenal with Linux Variant of PingPull Malware and Sword2033 Backdoor
A Chinese APT group called Alloy Taurus, also known as APT 41 or Gallium, uses a new version of the PingPull malware to target Linux systems.
Alloy Taurus is a group of cybercriminals with advanced skills engaged in various cyberattacks, such as stealing intellectual property, compromising supply chains, and carrying out ransomware attacks. They have targeted multiple industries, including healthcare, technology, telecommunications, and gaming. What makes them particularly concerning is their ability to carry out both financially motivated attacks and espionage activities, as this indicates that the group has the support and resources of a nation-state, making it challenging to identify and track the individuals responsible for the attacks. In addition, they employ advanced tactics, techniques, and procedures such as spear-phishing, water-holing, and custom malware to execute their attacks.
The threat group has been active since 2012 and has historically targeted telecommunication companies across Asia, Europe, and Africa. However, the group has recently broadened its focus to target financial institutions and government entities. Researchers observed the threat group recently targeting individuals in South Africa and Nepal as part of its new campaign and found a new malware. While initially identified as benign by most vendors, further analysis by the researchers revealed that the sample matched the communication structure, parameters, and commands of the known PingPull Windows malware first observed in September 2021.
The newfound malware uses encrypted data to communicate with its command-and-control (C2) server and can receive and run commands. After executing these commands, they are transmitted back to the server for additional processing. The Linux variant uses the same AES key as the original Windows PE (Preinstallation Environment) variant for encrypting its communication with the C2 server.
In addition to the variant of PingPull malware, the researchers also identified a backdoor named Sword2033, which communicates with the same C2 domain. This specific backdoor has three essential functions: it enables users to upload and download files to and from the system and execute commands. The commands used here are identical to those employed by the PingPull malware, and further investigation of the C2 infrastructure revealed links to Alloy Taurus operations.
According to the researchers, the detection of PingPull malware in a Linux variant and the recent use of the Sword2033 backdoor indicate that Alloy Taurus is constantly improving its operations to aid its espionage activities.






