According to the statement made by blockchain security firm CertiK, the breach was committed by threat actors by injecting malicious JavaScript code into the Premint web application (premint.xyz). This malicious Javascript code enables visitors and collectors to approve the “setApprovalForAll” function in connecting their crypto wallets (MetaMask, Coinbase, WalletConnect) to the compromised website. The “setApprovalForAll” function requests the ability to access and modify user funds by showing the token’s contract address. If the user approves, threat actors can access the crypto assets of the targets.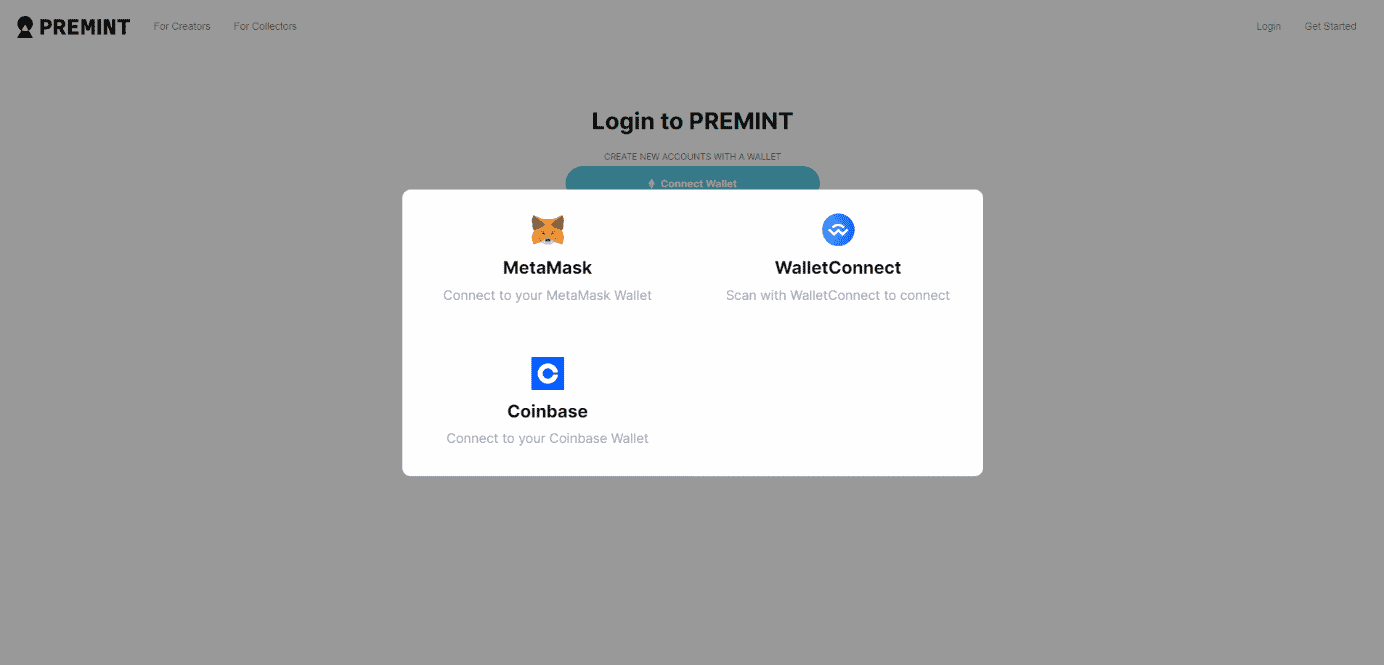
- The login information used in crypto wallets should be created using unique and strong policies.
- Direct NFT trading should not be performed with wallets containing crypto assets. In this process, assets should be distributed using different wallets.
- Cryptocurrency wallets should not be connected to platforms unsure of their reliability.
- Finally, care should be taken not to have any other browser add-ons in browsers with crypto wallets used as browser add-ons, such as Metamask.






