Dragos security researchers identified a malware distribution campaign to industrial control systems (ICS) through password recovery tools developed for programmable logic controllers (PLC). Password recovery tools that are advertised on various social media platforms promise to recover passwords of systems used in industrial control environments such as Automation Direct, Omron, Siemens, Fuji Electric, Mitsubishi, LG, Vigor, Pro-Face, Allen Bradley, Weintek, PLC, ABB, Panasonic, and HMI.
Also, thanks to the Sality trojan’s ability to communicate over a peer-to-peer (P2P) network, infected systems can become part of a botnet network controlled by threat actors. The Sality sample analyzed by Dragos researchers has been observed to be infected to carry out activities focused on cryptocurrency hijacking from vulnerable systems.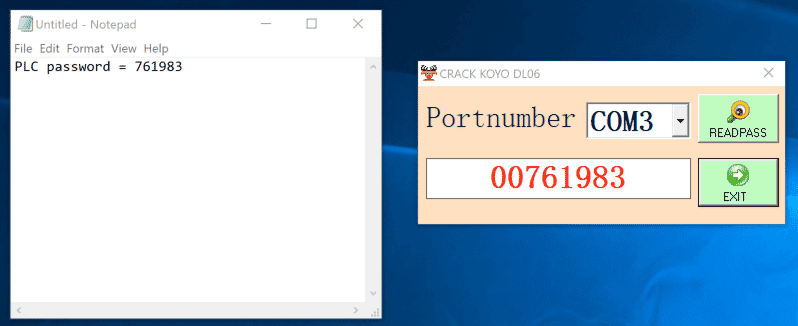
- It should be ensured that the systems, software, and hardware used are always used in the current versions where the vulnerabilities are fixed,
- Comprehensive and reliable Anti-Virus / Anti-Malware and Firewall solutions should be used,
- User privileges on systems should be limited,
- E-mails, attachments, and links from unknown parties should not be respected,
- Application, program/software downloads must be made through legitimate and reliable sources,
- Avoid downloading cracked software,
- Institution/organization personnel should be made aware of potential phishing/social engineering attacks,
- Passwords used in systems should be created using unique and strong policies,
- Detected IOC findings regarding the malware should be blocked from the security solutions in use.






