Avast discovered that Worok used a C++-based Payload called CLRLoad to pave the way for a PowerShell script embedded in PNG images, using a cloaking technique known as steganography. The findings show that the threat actor applied DLL Injection after gaining initial access to execute the CLRLoad malware.
Used in the attack chain, Malware called DropboxControl uses a Dropbox account for command and control (C&C) and captures data by allowing the threat actor to download/upload/run files to specific folders. Private companies and government agencies operating in locations such as Cambodia, Vietnam, and Mexico are among the countries affected by DropboxControl.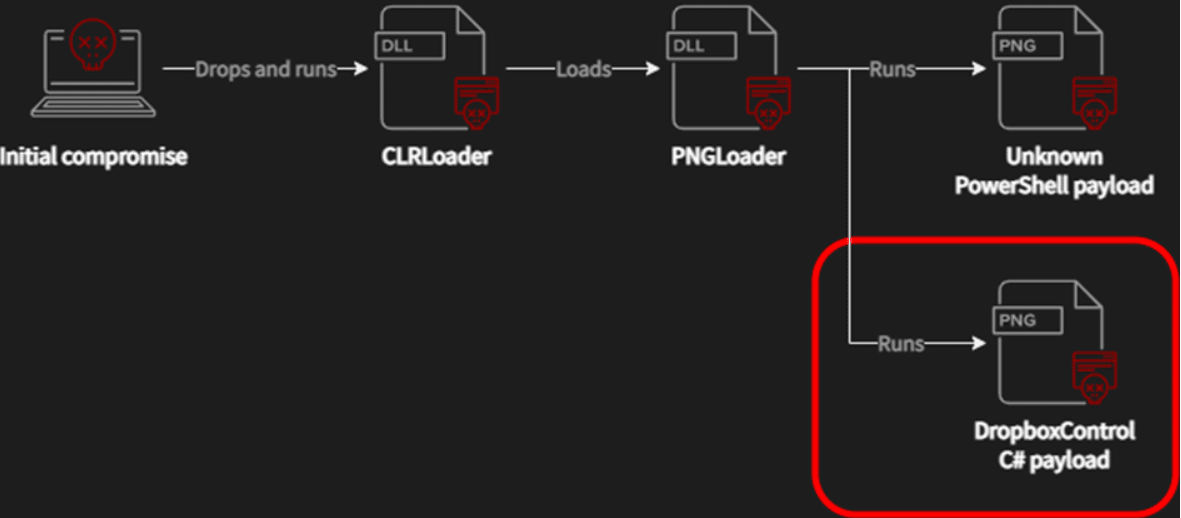
The tools used by Worok, which capture data through Dropbox accounts registered in active Google e-mails, are not very common; It is considered to be an APT project focused on high-profile organizations in the private and public sectors in Asia, Africa and North America.
As a precaution against targeted cyber attacks;
- E-Mails, attachments, and links from suspicious parties should not be respected,
- Files or programs should be downloaded from reliable sources,
- The most up-to-date versions of existing systems/programs should be used,
- It is recommended to block IoC findings related to the attack campaign by security solutions.






