Follina: The Critical 0-Day Vulnerability Affects Windows Systems
A 0-day vulnerability has been identified that allows threat actors to perform code execution activities on targeted Windows systems through Microsoft Office documents. It has been observed that threat actors exploiting the vulnerability called Follina obtain an HTML document from the command and control (C&C) server with the “remote template” feature of the malicious Microsoft Word document and use the ‘ms-msdt’ MSProtocol URI scheme to execute the malicious code on the target system.
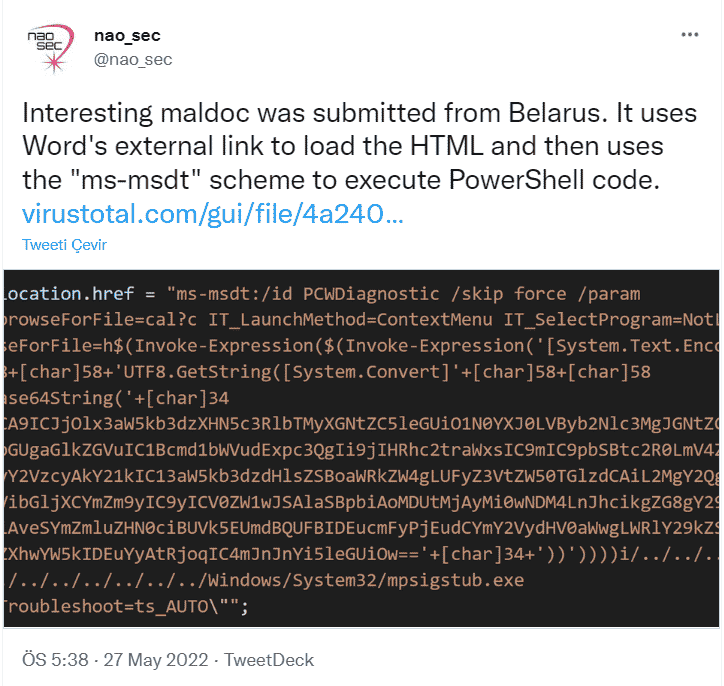
MSDT is a tool that collects errors that Windows users receive on the system for analysis. Threat actors can execute malicious code on the system with the MSDT tool, even if the targets do not enable macros of Microsoft Word documents. Also, converting the document to RTF format runs the code in the browser without the need to open the document.
The malicious Microsoft Word document, which cannot be detected in the Microsoft Defender Anti-Malware solution, affects Office 2016 and 2021 applications. In this context, it is recommended not to open Office documents obtained from unknown parties via e-mail attachments and other vectors, benefit from comprehensive Anti-Malware solutions, and use Office applications in the most up-to-date versions.
GoodWill: A New Ransomware Group Raising Attention to Social Responsibility
CloudSEK security researchers have identified a ransomware group that solicits donations from targets to individuals and patients who need help in exchange for a decryption tool. Ransomware called GoodWill was detected in March 2022. As the threat group’s name suggests, operators are allegedly more interested in promoting targets for social justice than traditional financial motivations. Some of the features identified by GoodWill in the analyzes are as follows;
- GoodWill ransomware was developed with .NET and packaged with UPX wrappers.
- It can stay in sleep mode for 722.45 seconds to avoid being detected during dynamic analysis.
- It uses the AES_Encrypt function to encrypt the captured files with the AES algorithm.
- It has a function called “GetCurrentCityAsync” that tries to detect the geolocation of the infected system.
When GoodWill infects systems, it encrypts documents, photos, videos, databases, and other important files with the “.gdwill” extension, making all these elements inaccessible without the decryption key. In the ransom note that the group left on the systems, it is stated that the targets must perform some social activities to obtain the decryption key.
 In the detailed analysis of GoodWill carried out by CloudSEK threat intelligence researchers, it has been observed that the ransomware in question has approximately 1246 threads, and 91 of them overlap with the open-source HiddenTear ransomware software developed by an operator of Turkish origin. In addition, the use of Hindi scripts by threat actors in the existing lines leads to the opinion that the group is based in India.
In the detailed analysis of GoodWill carried out by CloudSEK threat intelligence researchers, it has been observed that the ransomware in question has approximately 1246 threads, and 91 of them overlap with the open-source HiddenTear ransomware software developed by an operator of Turkish origin. In addition, the use of Hindi scripts by threat actors in the existing lines leads to the opinion that the group is based in India.
Although the threat actors behind the GoodWill ransomware software claim to operate under the name of social responsibility campaigns, they violate the intellectual property and privacy concepts of institutions/organizations. At the same time, these activities cause the targeted organizations to be unable to provide services, damage their reputation, material, and moral losses, and violate the security of personal information.
To not be the target of similar attacks in this context, it is recommended that email, attachments, and links from unknown parties are not respected, and input information used in accounts is created using unique and powerful policies. Also, it is important to use comprehensive security solutions and enable 2FA/MFA features on all possible platforms.
Misconfigured Elasticsearch Servers Targeted by Threat Actors
Secureworks security researchers have identified a new attack campaign targeting misconfigured Elasticsearch databases. Threat actors demand ransom payments from targets by altering the database content on vulnerable Elasticsearh servers with their ransom notes.

However, at this stage, promises made by threat actors should not be respected because it is impractical for threat actors to store large amounts of content. Most likely, the contents of the hacked databases are deleted, but ransom notes are left promising to restore the contents to the system. Therefore, database administrators need to take regular backups.
These and similar security breaches can lead to loss of reputation, data leakage, and possible service interruptions that may cost much more than the ransom amount of the affected institutions/organizations and organizations. In this context, it is recommended to use the current versions of the systems and programs, take regular backups of critical systems/files, perform attack surface analysis tests at regular intervals, and use comprehensive security solutions.






