Magniber Ransomware Targets Windows Users with Fake Software Updates
HP Wolf Security researchers have detected that the operators of Magniber Ransomware are running a new malware distribution campaign targeting Windows home users with advanced features.
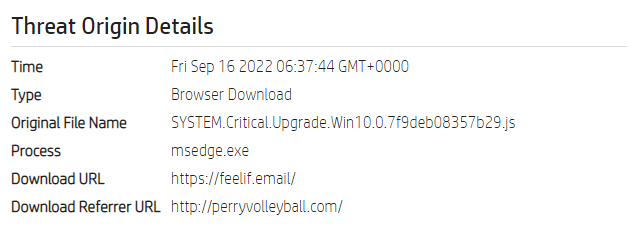
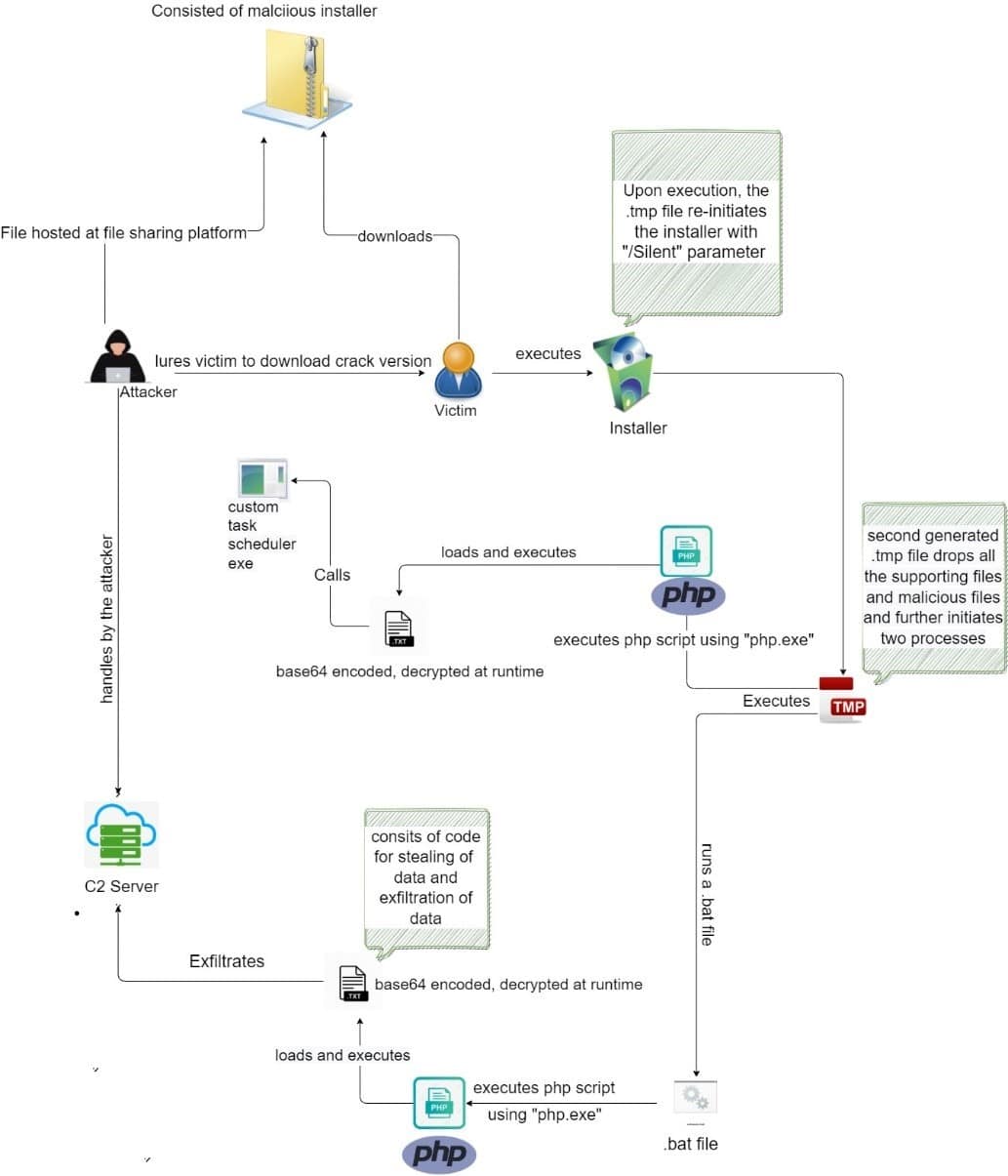

The threat actors behind the Magniber malware are known to demand a $2500 ransom payment from infected users. In this context, it is recommended to consider the following security steps in order not to be the target of this and similar ransomware campaigns.
- Administrator accounts used in line with the need should be created by considering the principle of least privilege,
- Software updates or programs should be obtained from reliable and official sources,
- The data stored in the systems should be backed up at regular intervals,
- Comprehensive Anti-Virus / Anti-Malware solutions should be used,
- IOC findings related to the campaign should be blocked from security solutions in use.
Multiple Vulnerabilities Detected in Juniper Networks Junos OS
Multiple critical security vulnerabilities have been identified in Junos OS, a network operating system used in security and network devices developed by Juniper Networks. The vulnerabilities allow threat actors to perform unauthorized file access, cross-site scripting (XSS), and directory traversal attacks.
Some of the detected security vulnerabilities are as follows;
- The security vulnerability, tracked as CVE-2022-22241, is due to incorrect login validation affecting the J-Web component of Juniper Networks Junos OS. As a result, an unauthenticated threat actor that successfully exploits the vulnerability can gain access to data through a specially crafted POST request without proper authorization.
- The vulnerability, tracked as CVE-2022-22246, is a PHP Local File Inclusion (LFI) vulnerability that affects the J-Web component of Juniper Networks Junos OS and could allow a low-privileged authenticated threat actor to execute a malicious PHP file on the vulnerable system.
- The vulnerability tracked as CVE-2022-22242 is a Cross-Site Scripting (XSS) vulnerability that affects the J-Web component of Juniper Networks Junos OS and could allow an unauthenticated threat actor to run malicious scripts in the user’s browser in the context of a J-Web session.
- The vulnerability tracked as CVE-2022-22244 is an XPath Injection vulnerability that affects the J-Web component of Juniper Networks Junos OS. An unauthenticated threat actor can exploit the vulnerability through a specially crafted POST request.
These vulnerabilities, which affect all versions of the Junos operating system, are critically rated as high and have been fixed with the updates released by Juniper Networks. In this context, in order not to be the target of attacks that can be carried out using vulnerabilities, it is recommended that vulnerable Junos OS users upgrade immediately to released updates, while as a workaround, disable J-Web or restrict access to trusted hosts only.
Timing Attacks Via Npm API Discloses Custom Package Names
An attack method that reveals the names of special packages has been identified by Aqua Security researchers. Organizations create internal projects and custom packages of certain software products to keep their code and functionality private to minimize the risk of their development teams and inventories being exposed to targeted attacks.
The detected attack method includes a timing attack using the npm API. The npm Register API allows users to download existing packages and check for the existence of packages. When using the npm registry to download a package that does not exist or is set as private, the website returns a 404 HTTP error code stating that the package could not be found.
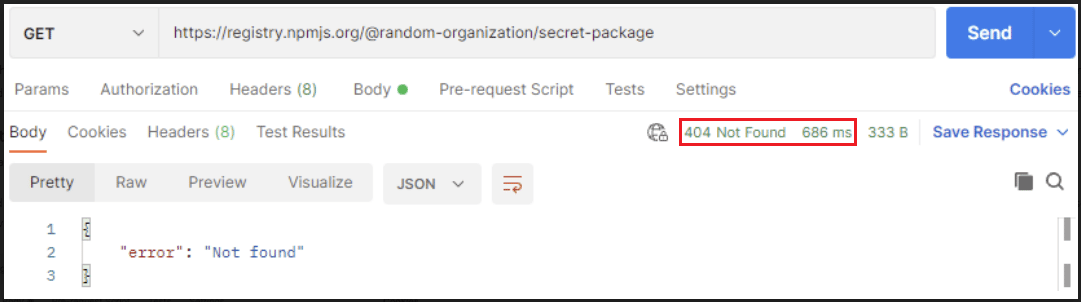
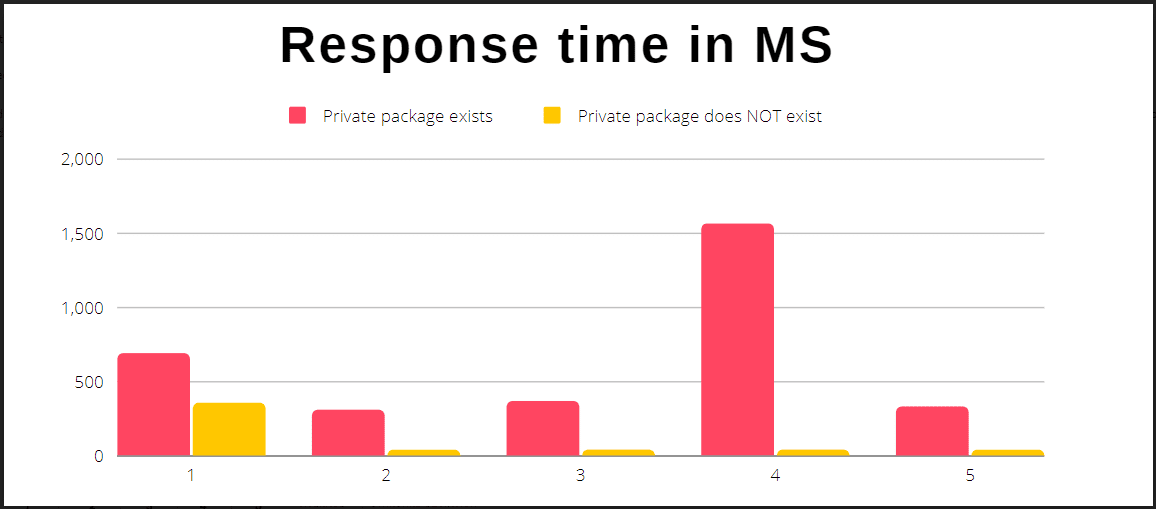
After detecting the private packages of the organizations, the threat actors can create fake malicious packages with the same name and trick the public/organizational employees into downloading them. It is predicted that such an attack could be linked to wider supply chain attacks. In this context, it is recommended to take the following security measures in order to reduce the risk of attacks that can be carried out using the said method.
- Organizations should take preventive measures by frequently searching npm for suspicious packages that spoof their custom packages with similar names,
- Because npm doesn’t allow same-named packages to be installed in public repositories, organizations should create public packages that emulate their private packages as placeholders,
- If similar packages are found, it should be ensured that they do not contain malware, and relevant stakeholders should be informed.






