Critical XSS Alert Affecting Zyxel’s Specific Firewall Models
Zyxel has released updates for a critical XSS (Cross Site Scripting) vulnerability that affects specific models of firewalls.
The vulnerability, tracked as CVE-2022-40603, affects the CGI program of firewall versions and is caused by insufficient sanitization of user-supplied data. A remote threat actor can direct targeted users to visit an XSS-loaded URL and execute a malicious script in the user’s browser. A threat actor who successfully exploited the vulnerability could access sensitive browser-based information.
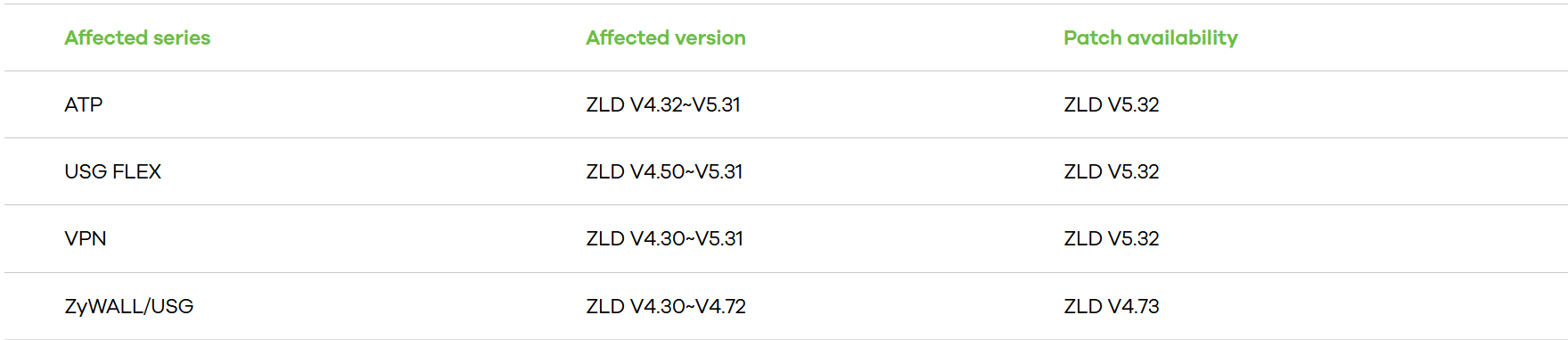
The firewall models and versions affected by the security vulnerability are as follows;
Critical RCE Alarm in FreeBSD Ping
A critical security vulnerability has been identified in the ping module of the open-source FreeBSD operating system that threat actors could potentially exploit to gain remote code execution.
The Stack Buffer Overflow vulnerability, tracked as CVE-2022-23093, is caused by a boundary error in the ping module’s pr_pack() function and affects all supported versions of FreeBSD. The ping module allows testing the accessibility of a remote host using ICMP messages and reads raw IP packets to process responses in the pr_pack() function. The pr_pack() function copies the received IP and ICMP headers to the stack buffers for further processing. A remote threat actor could exploit this vulnerability to trigger a boundary fault, crash the ping program, and execute code remotely on the affected system.
There has yet to be an update that fixes the vulnerability. In this context, in order not to be the target of attacks that can be carried out using the vulnerability, it is recommended that the updates to be published should be implemented immediately if they are followed and published.
LastPass Suffers A Data Breach
LastPass, a popular password management service, suffered a data breach that resulted in threat actors gaining unauthorized access to a certain number of customer information.
The data breach targeting LastPass and its subsidiary, GoTo, is known to have been carried out using information obtained in the August 2022 security breach. There are no details about the breach, but the statement made by LastPass officials stated that the unauthorized parties only gained access to some aspects of the customers with the said data breach attempt.
LastPass has launched a comprehensive investigation into the breach through the well-known security firm Mandiant and law enforcement. LastPass reported that its Zero-Knowledge architecture securely encrypts and stores customers’ passwords and that LastPass products and services continue to be available. Therefore, there is no action for customers to take.






