Introduction
The energy sector is confronted with an unprecedented convergence of risk, as nation-state APT groups, ransomware as a service operators, and opportunistic cybercriminals exploit any weakness in an exposed infrastructure. The rise of interconnected OT and IT networks and the increase in internet-facing assets have made energy providers to targets of choice. External Attack Surface Management (EASM) is no longer a luxury; it is a requirement to defend against the continued detection and exploitation of shadow IT, vulnerable remote access systems, and unpatched ICS elements by attackers.
Mapping the Expanding Attack Surface
Key Challenge:
Energy organizations frequently have inadequate visibility into their external-facing assets, which may comprise legacy SCADA, cloud workloads, third-party portals, or contractor VPNs. Research firms have found that more than 80% of incidents occur through unmanaged external assets.
Best Practices:
- Implement continuous asset discovery to gain visibility into exposed endpoints, APIs, and cloud services that may have been forgotten.
- Identify exposed high-risk assets (e.g., legacy VPNs, ICS gateways, remote desktop services, etc.) and prioritize them.
- Automatically enrich your SIEM and SOAR platforms with EASM data for incident response automation.
Defending Against APT Campaigns
Primary Threats:
- China-affiliated groups (e.g., Mustang Panda, DigitalRecyclers): Attackers targeting European energy and maritime sectors using loaders and backdoors.
- Russia-affiliated groups (e.g. Sandworm, Gamaredon): Attackers using wipers and remote monitoring tools whether targeting OT environments.
- Iran-affiliated groups (MuddyWater, OilRig sub-groups): Attackers target energy firms by exploiting VPNs and some form of remote management.
Recommendations:
- Implement strong zero-trust segmentation between IT and OT.
- Use behavioral analytics to catch wipers and abusive use of remote admin tools.
- Conduct red-team testing of APT-style intrusions on ICS systems.

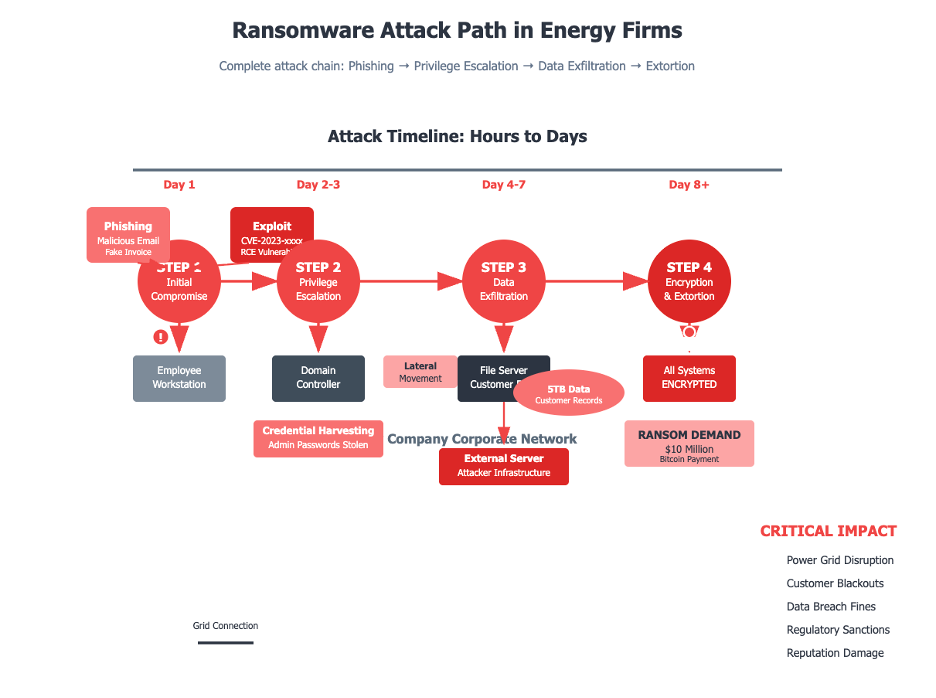
Ransomware Evolution and Energy Risks
Trend: Ransomware operators now prioritize data theft and extortion over encryption, with groups like CL0P, Akira, and Qilin dominating global activity. Energy providers are especially attractive due to their operational criticality. Triple extortion—data theft, encryption, and DDoS—has become standard.
Best Practices:
- Harden file transfer systems and patch enterprise software vulnerabilities (frequent ransomware entry points).
- Deploy deception technologies to detect lateral movement.
- Establish robust offline backups with frequent integrity testing.
4. AI-Enhanced Attacks and Threat Actor Innovation
Emerging Risks:
- AI-enabled phishing and disinformation: Using both APTs and eCrime actors
- Infostealers: Up 58% in 2024–2025, often as initial access brokers for ransomware attacks
- Supply chain attacks: Massive uptick in 2025, software update attacks poisoning, managed file transfer abuse
Best Practices
- Deploy anti-phishing with AI anomaly detection across both email and collaboration tools.
- Enforce third-party risk management and include software bill of materials (SBOM) verification
- Monitor access broker marketplaces for indications of compromised credentials in the energy sector.
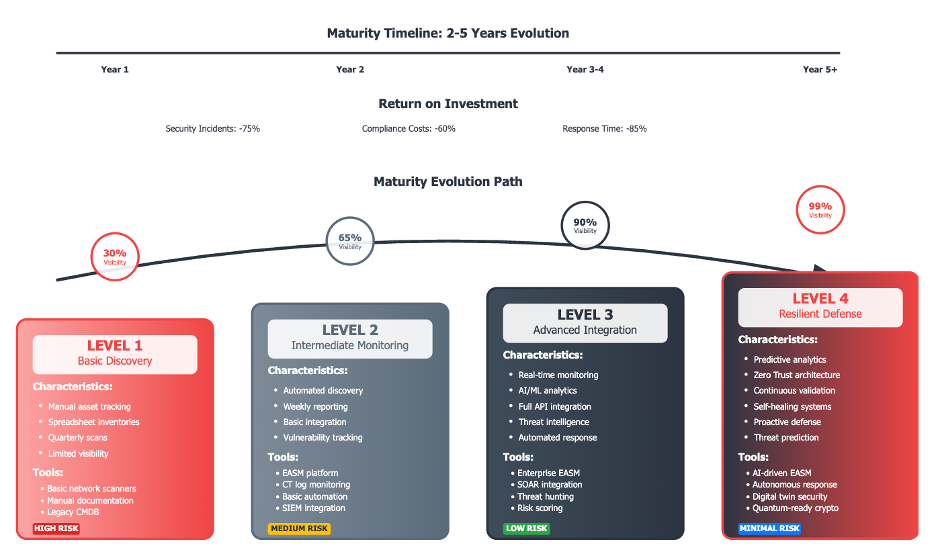
5. Building a Resilient EASM Program for Critical Infrastructure
Strategic Suggestions:
- Governance: Form an EASM task force that consists of cross-functional stakeholders (CISO, OT security, vendor risk).
- Automation: Automate the EASM with threat intelligence feeds to proactively identify new exposures.
- Resilience Testing: Conduct purple-team exercises against both IT and OT cyber attack surfaces on a quarterly basis.
- Incident Readiness: Pre-stage play-books for ransomware attacks on ICS, supply chain compromise, and wiper attacks.
Conclusion
Energy providers are in the middle of national resilience, which makes their attack surfaces attractive targets for attackers from state-sponsored APT groups to ransomware cartels. The best defense is to employ a proactive EASM program that includes asset discovery, APT defense, ransomware resiliency, continuous monitoring powered by AI-based threat intelligence, and a readiness for incident responses. The only way to stay ahead of the ever-present threats in 2025 and to be resilient is to keep reducing the unknown attack surface and responding to the most advanced adversaries.







