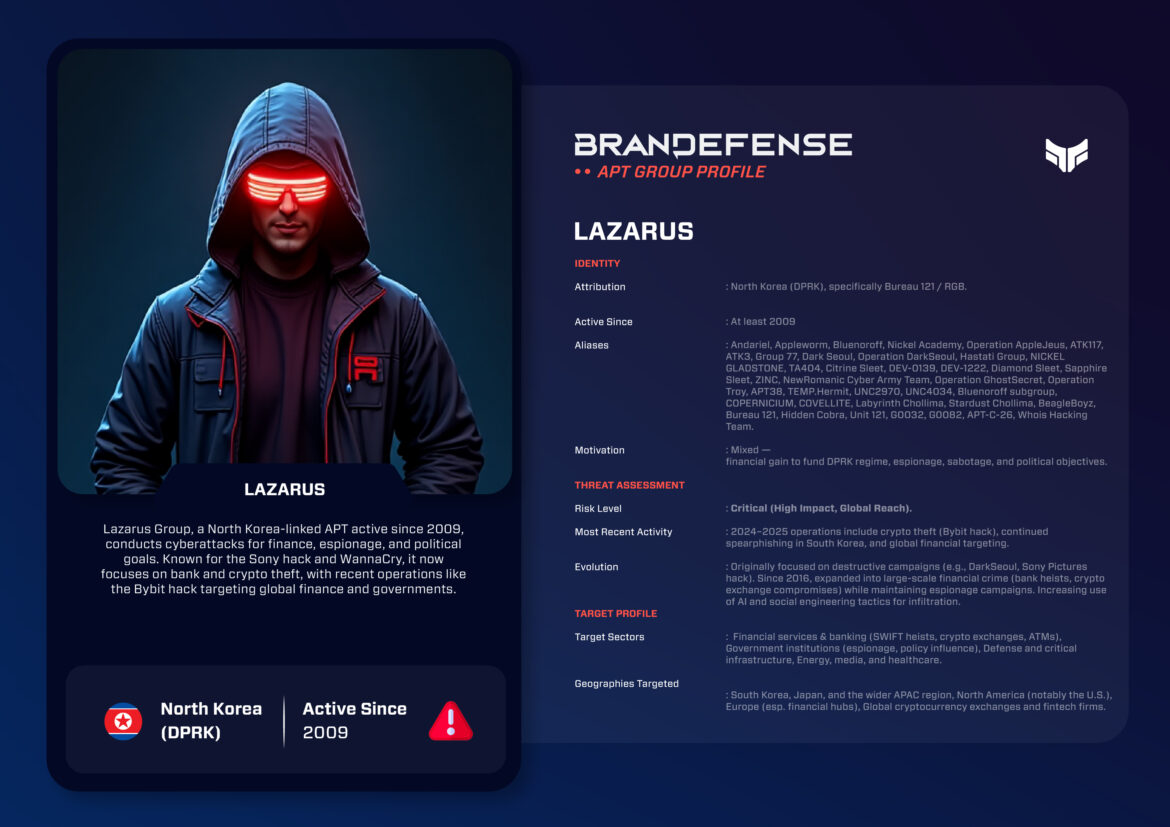
There are a handful of state-sponsored adversaries that replicate the persistence, reach, and audacity of the Lazarus Group. The Lazarus Group has been active since at least 2009, and although it is widely tied to North Korea’s Reconnaissance General Bureau, it has left a trail through some of the most notable disruptive cyber events of the last decade. The Lazarus Group has displayed a wide range of activities from headline-producing sabotage, stealthy long-haul espionage, and unabashed revenue creation. From Sony Pictures to billion-dollar bank heists and broad-ranging cryptocurrency thefts, the Lazarus Group has become a euphemism for a highly capable, shape-shifting adversary that learns rapidly and rarely, if ever, relinquishes its grip.
Identity and Motivation
You will encounter Lazarus under a veritable tangle of labels such as Hidden Cobra, Zinc, Bluenoroff, Andariel, APT38, and BeagleBoyz, because the umbrella crosses sub-groups with different tasks. The logic is simple: one group, many specialties. Some units focus on the traditional intelligence work associated with ministries, militaries, and defense corporations; others focus on cash, raiding banks, ATM networks, and crypto exchanges, facilitating the regime to acquire hard currency as it operates outside the usual channels.
This dual-hatted function is what makes Lazarus curious as an advanced persistent threat, in that it acts as a spy service, sabotage team, and cash cow, sometimes even in the same campaign. This hybrid model allows Lazarus to pivot when necessary. If political tensions are on the rise, it can duck into its sabotage or disruptive roles. If it needs cash, it can focus on theft, either slowly gaining access into existing crime networks or quickly exploiting a careless configuration at a cryptocurrency company.
And because its sub-groups share the same tools, infrastructure, or tradecraft, Lazarus can also borrow the strengths of its internal partners without taking the fall of being identified as the threat actor. Lazarus’ structure is resilient and obscures attribution, frustrating defenders who look for neat, linear connections.
Tradecraft and Tactics
Initial access follows a fairly consistent route, but it requires precision. Spear-phishing remains the bread-and-butter: fake emails that are expertly designed, believable lures, and malicious documents in trusted file formats. The Lazarus Group also uses watering-hole sites, compromising pages that the targets regularly visit, and it has developed supply-chain compromises that turn a benign software update into a means of delivery. Public infrastructure is thoroughly probed for weaknesses, from VPN gateways to badly patched servers, to misplaced public-facing RDP surfaces, and simple reuse or brute-forcing of exposed credentials.
Once inside, persistence is made habitual with custom families of malware such as DTrack, Manuscrypt, and FALLCHILL, complemented with common admin tools to blend in with all the noise. Credential theft is normal; think mimikatz-style dumping, token-based abuse, and password spraying to spread access without being detected or reported. Registry keys, scheduled tasks, and hijacking services keep the beachheads for future callback usage on managed or minted credentials. Remote access may ride over RDP, but the group also uses other methods of command-and-control connection to the malware: compromised servers, fast-flux DNS that constantly rotates infrastructure, and layers of anonymity such as TOR. The point is not creativity; the point is reliability and endurance.
Where Lazarus really stands out is in tailored tooling aligned to its mission. Financial theft operations include FASTCash, which abuses payment switches to coordinate ATM cash-outs, and SWIFT manipulation playbooks that produce fraudulent transactions in a way that masks all traces. The AppleJeus family targets cryptocurrency traders by trojanising apps and wallets, usually under the front of legitimate websites and fake companies. In espionage, they use implants including NukeSped and KEYMARBLE to allow recon, data theft, and long-term surveillance. And when they want to cause disruption, there is no hesitation to use wipers or ransomware. WannaCry, built on a leaked exploit that could spread almost like a worm, demonstrated how one tool could tie up hospitals, factories, and governments over the weekend.
Technically, Lazarus prefers multi-stage intrusions: commit, lateral movement, privilege escalation, network mapping, and quietly laying the groundwork for exfiltration. Exfiltration occurs through services like cloud storage or less obvious C2 channels all of which look and feel like normal traffic patterns. When the op burns, or the mission shifts, they can deploy wipers to destroy evidence and cripple systems for good measure. It isn’t reliant on any one strain of malware or tool; it’s a playbook whose obfuscation and reach have been honed with years of trial, error, and successes.
Operations That Shaped Its Reputation
- 2013: DarkSeoul. South Korean banks and broadcasters discovered that their systems had been wiped and operations had been suspended, making it clear that destructive capability was firmly part of Lazarus’ bag of tricks.
- 2014: Sony Pictures. In retaliation for The Interview, the attackers dumped a treasure trove of internal data, destroyed workstations, and humiliated a Hollywood studio on the international stage. It highlighted how geopolitics, cyber troops, and pop culture interact.
- 2016: Bangladesh Bank. Lazarus utilized access to SWIFT in attempts to move nearly $1 billion; while $81 million moved successfully, the remaining funds were disrupted by errors and suspicion. It was demonstrated here that trust can be worth more than a zero-day if trust is abused.
- 2017: WannaCry. A worm that leveraged a leaked NSA exploit spread across networks in over 150 countries, freezing hospitals and factories alike. Ransomware provided the cover story; the scale of disruption delivered the message.
- 2018: AppleJeus. Trojanised crypto tools integrated into the workflows of traders and exchanges, siphoning keys and funds with the polish of a legit fintech product.
- 2020: FASTCash 2.0. Coordinated ATM drainings occurred across parts of Africa and Asia with reckless speed, turning network access into physical cash in real-time.
- 2023–2024: Crypto and fintech spree. With digital assets booming, Lazarus focused its attention on exchanges, market-makers, and DeFi infrastructure, chaining social engineering with supply-chain compromise.
- 2025: Bybit and beyond. Reporting linked Lazarus to a major crypto theft at Bybit while also identifying new spear-phishing in South Korea and espionage activities targeting Western defense organisations. The message: the group can multitask, globally.

What’s New
Lazarus appears to be getting more sophisticated in using AI-assisted social engineering, where actors assuming fake identities (with résumés, portfolios, and interview skills) have already made it into hiring pipelines. Likewise, the Bluenoroff subgroup has continued constant pressure wherever there is liquidity in crypto, while other units are buying or bartering initial access from the entire “access-as-a-service” market.
Countries like South Korea and Japan appear to have the most pressure on them, but the US and Europe are also frequently in the sights of Lazarus hackers when the mission calls for it. As this indicates, Lazarus is both opportunistic and patient, willing to make investments (such as advancing in the chain of access) in games that may or may not pay off.
How to Defend Pragmatically
While perfect security can never be achieved, diligent fundamentals can not only make it more difficult for Lazarus but also give your organization a considerable buffer between their intent and actual impact.
Start at the perimeter: test and patch your VPNs, gateways, and internet-facing applications especially against vulnerabilities known to be under active exploit. Begin adopting and enforcing multi-factor authentication on any viable remote access (VPN, admin and cloud control consoles), and turn off any protocols with weak or vulnerable identity protections.
When on your networks, plan for credential leakage now and prepare for it. While monitoring for current Lazarus families (DTrack, AppleJeus, FASTCash), focus on behaviours over signatures: unusual or unexpected lateral movement, anomalous PowerShell and abuse via WMI, spikes in outbound cloud storage traffic, or unusual behaviour on SWIFT or payment switches.
Certainly segment the networks they should not be all or nothing; both to ensure a compromised workstation does not bring down an entire factory, and especially worse, an entire enterprise. Lock down backup infrastructure; regularly test restores with reliable processes that do not impact production. Maintain offsite, offline, or immutable copies to mitigate adequately against wipers and ransomware.
Cryptocurrency organizations should adopt extra safeguards: hardware security modules, multi-signature policies with segregated duties, and offline treasury processes. Don’t let marketing timelines and launch events outweigh security. That “partnering tool” or update server could easily end up as a Lazarus entry point.
Conduct incident response like fire drills tabletop exercises that simulate real-life crises, including legal, communications, and executive stakeholders. Time is of the essence; you’re more likely to have pre-emptive decisions to push out during a crisis rather than trying to form them for the first time under pressure.
The Bottom Line
The Lazarus organisation is arguably the clearest example to date of the blurry line between state-sponsored espionage and cybercrime. It is funding a sanctioned regime, facilitating strategic intelligence objectives, and doing so with a level of patience and audacity that few actors can match.
The group has no plans to disappear it is evolving into new spaces, improving existing techniques, and adopting whatever else works. The best response is not glamorous: put in place identity and edge controls, hunt behaviours not binaries, improve backup and treasury processes, and rehearse your bad day before it happens.
These measures will not eliminate risk, but they can convert a headline-making crisis into a manageable reality. And sometimes, that is the most valuable win there is.
You can download and review the sheet for all the details!







