Executive Summary
Data breaches are a continuing critical challenge for cybersecurity. Sensitive information can now be spread rapidly on the dark web for malicious purposes with targeted, fraud, and ransomware proliferation. Over the last two years, there have been a number of standalone traumas, including data breaches which have stood out for their scale and unique lessons. Here are the 10 most critical breaches, and what they mean for businesses and individuals.
Key Findings
- Credential Supply Chain is Mature: Info‑stealer logs + breach dumps + combolists power a constant stream of valid logins (post‑Genesis: Russian Market, Styx, Telegram subscriptions).
- Industrialization via RaaS/IAB: First access is commoditized; brokers sell VPN/RDP/SaaS footholds or share revenue for high‑privilege creds.
- Kill Chain Bypassed: Adversaries skip Weaponization/Delivery and enter with T1078 Valid Accounts/T1133 External Remote Services, blending in as normal users.
- Case Corroboration: BlackBasta chat leak (2023–2024) shows systematic use of combolists, self‑run stealers (e.g., Lumma), and third‑party logs (e.g. Meduza), plus coordination around brute force targets.
- Ecosystem Resilience: Genesis takedown accelerated decentralization (more markets, more Telegram), not deterrence.
Why It Matters
- Faster, Quieter Breaches: Shorter time‑to‑initial‑access; reduced detection opportunities.
- Scalable Operations: Low-cost, repeatable campaigns across many victims.
- Third-Party Blast Radius: Trusted relationships (T1199) create lateral risk via suppliers/partners.
- Compliance & Reputation: Identity-led incidents drive notification, penalty, and brand damage costs.
MITRE ATT&CK Quick Map
- Resource Development: Acquire/compromise accounts — T1650, T1586
- Initial Access: Valid Accounts — T1078; External Remote Services — T1133; Trusted Relationship — T1199.
- Post-Access: Persistence/PE/Defense Evasion through the same valid accounts.
- Credential Access: T1003, T1555, T1552, T1056, T1040, T1557
- Lateral Movement: T1021, T1550, T1563
Case Insight: Black Basta
- Even “advanced” actors heavily use combolist + brute force for first access.
- Mixed sourcing: IAB + own stealer (Lumma) + third‑party logs (Meduza)
- Centralized operational leadership (targeting, password lists, tasking) enables scale.
Implication: Basic identity gaps (password reuse, weak MFA coverage, exposed RDP) are enough for a major breach—unless identity controls and analytics are first‑class.
Introduction
For decades, cybersecurity has been a game of perimeter defense—building higher walls and stronger gates to keep intruders out. But what happens when the attacker doesn’t bother breaking down the gate, and instead, simply walks through the front door with a stolen key?
This isn’t a hypothetical scenario; it’s the new reality driving modern ransomware attacks. A sprawling, industrialized cybercrime economy has emerged, centered on a single commodity: your credentials. From vast dark web credential markets to specialized Initial Access Brokers (IABs), a sophisticated supply chain now exists to harvest, package, and sell stolen logins to Ransomware-as-a-Service (RaaS) affiliates on demand. This commoditization of access fundamentally changes how attacks begin, shifting the primary battleground from the network edge to the user’s identity.
This deep dive explores the mechanics of this credential-fueled ecosystem. We will dissect how info-stealer logs and massive data breaches feed the ransomware machine, map the new attack chain using the MITRE ATT&CK® framework, and analyze leaked chats from the Black Basta ransomware group to reveal how these tactics work in practice. Ultimately, this analysis illustrates why defending against today’s threats requires a strategic shift from perimeter security to an identity-first approach.
Info-Stealer Logs and Credential Broker Markets
Before its takedown in 2023, Genesis had about 80 million stolen credentials from over 2 million people, making it one of the most significant illicit credential markets.
These types of credential-as-a-service platforms significantly lowered the barriers to entry for ransomware groups by offering ready-made access packages. Genesis “enabled many cybercriminals to rapidly expand their operations and carry out targeted attacks,” fueling ransomware campaigns.
Beyond Genesis, numerous other marketplaces (e.g. Russian Market, 2Easy, and invite-only forums) continue to sell stolen account logs and even direct network access, enabling ransomware affiliates to shop for victims’ credentials and sessions at scale.
Access is usually restricted through registration steps such as invitation codes or upfront fees. Users fund internal wallets with cryptocurrency deposits and then use these balances to purchase individual data listings. The platform itself often acts as an escrow agent, releasing data only once payment is verified. Interfaces are most often accessible via Tor, but sometimes clearnet mirrors or I2P-based alternatives are provided for redundancy.
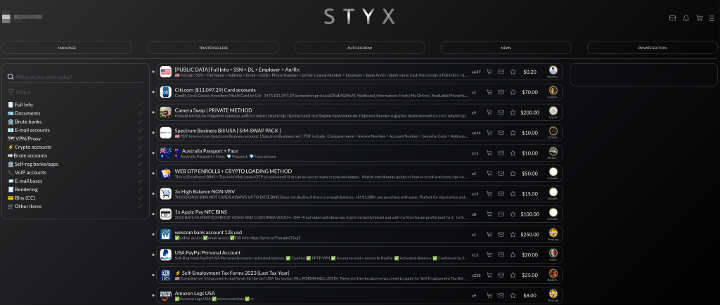
Figure 1: STYX dark web market screenshot.
Transactions are facilitated through Telegram bots or manual interactions with administrators. Buyers can issue predefined commands (for example, /buy [listing_id]) and complete payments using cryptocurrencies such as Bitcoin or Tether. Once the payment is confirmed, data is typically delivered via direct file transfer or through download links. Some channels operate on a subscription model, giving paying members regular access to bulk dumps of newly stolen data.
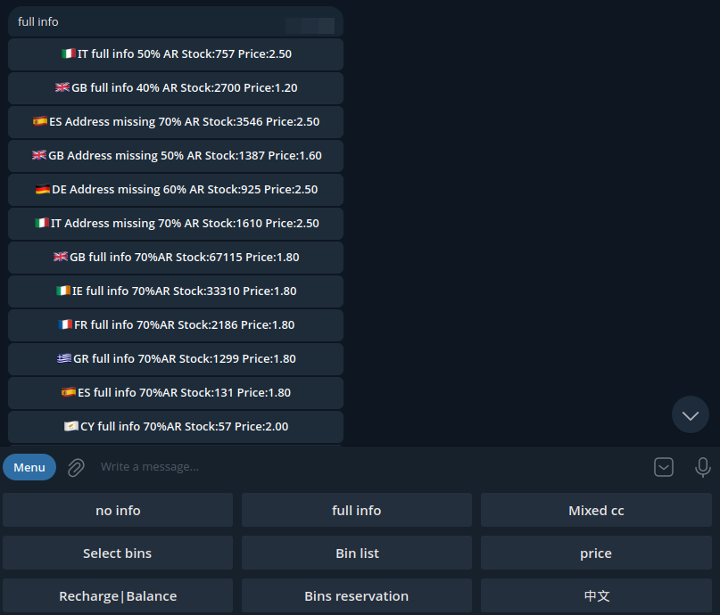
Figure 2: A Telegram-based marketplace screenshot.
Both operational models emphasize efficiency, anonymity, and scalability, enabling threat actors to quickly monetize stolen information. The Telegram-based model, in particular, reflects an ongoing shift toward leveraging mainstream communication platforms to bypass traditional barriers associated with dark web commerce.
Victim Data Breaches and Large Credential Dumps
In addition to malware logs, ransomware actors harvest credentials from public data breaches and “combolists” (combined credential lists). When organizations or online services suffer data breaches that leak usernames/passwords, those credentials often circulate on dark web forums or get compiled into massive lists. Over time, billions of credentials from breaches have been aggregated into wordlists (e.g. Collection#1-5, RockYou2021) and sold or shared openly. These large-scale leaks (often containing millions or even billions of username-password pairs) have an operational impact: ransomware operators or their partners can use them for credential stuffing and brute-force attacks to infiltrate networks.
If employees reuse passwords across systems, a password leaked from a security breach could become the key to accessing the corporate VPN, RDP server, or email account. Eventually, much of this stolen data moves into the public domain, where it is cross-referenced and recombined into targeted password dictionaries.
Attackers assemble combolists tailored to certain technologies or services – for example, extracting VPN or Citrix-specific credential sets – to maximize their success in brute-forcing enterprise systems.
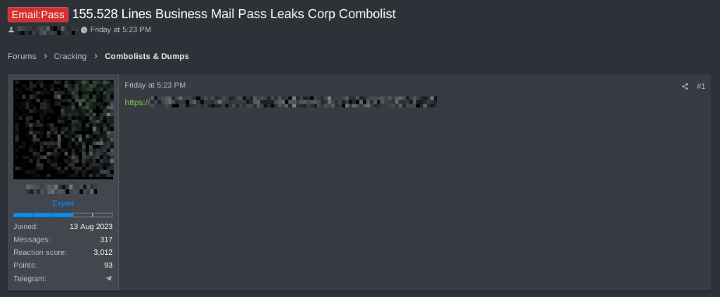
Figure 3: An underground-forum post titled “155,528 Lines Business Mail Pass Leaks Corp Combolist,” shared for free.
This abundance of leaked credentials provides a “fertile ground” for attackers: even relatively unsophisticated threat actors can attempt widespread logins with automated tools, aided by giant credential lists gleaned from past breaches and stealer logs.
In short, the continuous spill of passwords from data leaks and malware infections has created an environment where ransomware groups have no shortage of valid logins to try across potential victims.
Initial Access Brokers and the RaaS Model
The rise of Ransomware-as-a-Service (RaaS) has further industrialized credential abuse, by enabling a division of labor among cybercriminals. In the RaaS model, core developers maintain the ransomware payload and payment infrastructure, while affiliates (often independent hackers) carry out the breaches and share a cut of the profits. This specialization gave birth to Initial Access Brokers (IABs) – threat actors who focus on obtaining footholds in targets (via stolen credentials, web shell backdoors, vulnerable RDP/VPN servers, etc.) and then sell that access to ransomware affiliates.
An IAB might, for instance, use phishing or an infostealer to compromise an employee’s account, establish persistent access in the network, and quietly offer that access for sale on hacker forums.
Ransomware affiliates can simply purchase ready access rather than breaching the network themselves. This outsourcing has greatly expanded the scale of attacks – a skilled social engineer or credential thief can feed many ransomware operations without ever deploying malware themselves.
Criminal forums have teemed with offers for RDP login pairs or VPN accounts to corporate networks, often for modest prices depending on the company’s size. Some IABs operate on a profit-sharing model with ransomware gangs instead of fixed prices: for example, a broker might negotiate to receive 30% of any ransom paid if they provide a domain admin credential for initial access. This highlights how valuable high-privilege credentials are in the underground economy. The RaaS ecosystem’s affiliate structure means a wide variety of actors – from seasoned exploit developers to low-skill credential harvesters – can all play a role in ransomware attacks. Figure 4 highlights how leaked credentials act as a central enabler, reducing the technical threshold for affiliates and sustaining the broader RaaS ecosystem.
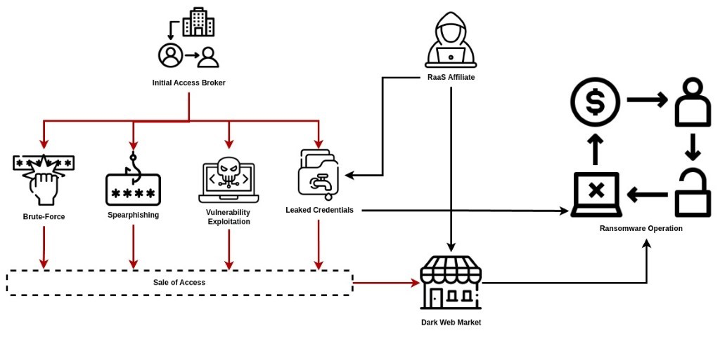
Figure 4: Credential Supply Chain Feeding Ransomware Operations.
Ransomware affiliates also exploit known vulnerabilities to obtain credentials or bypass logins. Overall, the RaaS model supercharges credential abuse by matching credential suppliers with ransomware deployers. The affiliate diversity ensures that any exposed credential – whether from a malware log, a phishing kit, or a database leak – can quickly find its way into an attack. This “cybercrime supply chain” has made initial access a commodity. The net result is a more efficient and scalable ransomware operation, where credentials are currency.
Initial Access Brokers (IABs) obtain entry through brute-force attacks, spear phishing, vulnerability exploitation, or leveraging leaked credentials. These accesses are monetized via direct sales or dark web markets, where RaaS affiliates purchase them to launch ransomware operations. Some ransomware operators, however, bypass IABs altogether by directly analyzing leaked credentials and using them to gain initial access.
Attack Chain and MITRE ATT&CK Mapping
Traditional cyberattacks typically begin with malware delivery or an exploit to breach a network’s perimeter. However, the availability of leaked credentials provides a shortcut, fundamentally altering this process by shifting the primary attack surface from the network perimeter to the identity layer. This allows adversaries to bypass the noisy initial stages of an attack and operate from a position of presumed trust. This analysis maps this unique attack vector using both the Cyber Kill Chain® and the MITRE ATT&CK® frameworks to illustrate the strategic shift and the need for identity-centric defense strategies.
The Traditional Attack Chain
To understand the advantage of using compromised credentials, it’s useful to first review the standard cyberattack progression. The Lockheed Martin Cyber Kill Chain® outlines the initial, noisy stages an attacker must complete externally: Weaponization and Delivery. In the Weaponization phase, the adversary crafts a malicious payload, such as malware, designed to exploit a known vulnerability. The Delivery phase involves transmitting this payload to the target, often via phishing emails or compromised websites. These steps are resource-intensive and must cross the network perimeter, creating clear opportunities for defenders to detect and block the attack.
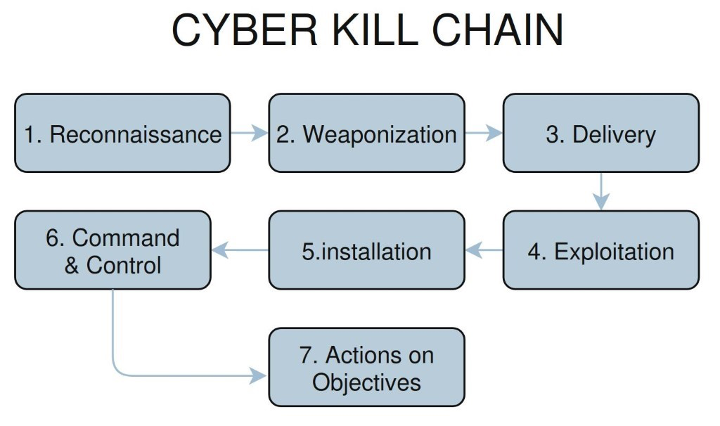
Figure 5: The Cyber Kill Chain outlining the seven stages of a typical cyber attack.
Leaked Credentials Hijack the Kill Chain: A MITRE ATT&CK Analysis
Initial Access: Walking Through the Front Door
An attack using leaked credentials bypasses the traditional Weaponization and Delivery stages entirely. The adversary uses a stolen key to unlock the front door, beginning their attack inside the perimeter as an authenticated user.
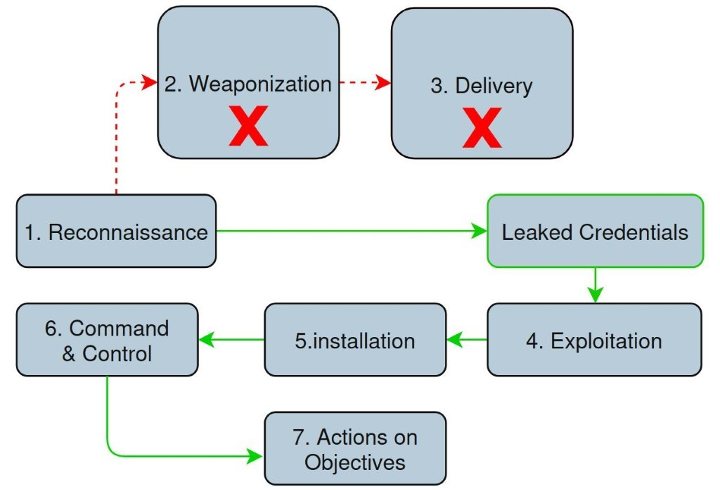
Figure 6: Attack using leaked credentials to bypass initial stages and infiltrate as an authenticated user.
This approach is best analyzed through the MITRE ATT&CK® framework, which details post-access adversary behaviors.
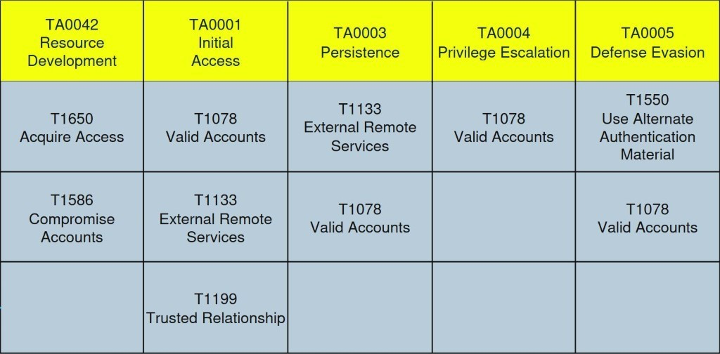
Figure 7: MITRE ATT&CK table illustrating how leaked credentials facilitate every attack step.
- Resource Development: In a typical attack, Resource Development consists of techniques that involve adversaries creating, purchasing, or compromising/stealing resources that can be used to support targeting. When leveraging stolen credentials, the credential is the primary resource. Adversaries obtain these through various channels, including purchasing them from criminal marketplaces—a behavior mapped to T1650 (Acquire Access)—or by harvesting them from previous breaches and testing them against new targets, a technique known as credential stuffing, which aligns with T1586 (Compromise Accounts). This dramatically reduces the attacker’s upfront investment of time and Effort.
- Initial Access: This tactic is where the most significant advantage is realized. By using legitimate credentials, adversaries can circumvent perimeter security controls designed to stop inbound threats. This behavior is cataloged as T1078 (Valid Accounts) and is frequently used against public-facing applications or T1133 (External Remote Services) like VPNs and RDP gateways. This allows an attacker to establish a foothold silently, appearing as legitimate user traffic. In other scenarios, an attacker might leverage T1199 (Trusted Relationship) by compromising a third-party vendor with legitimate access to the target network.
- Persistence, Privilege Escalation, and Defense Evasion: A valid account is a powerful, multi-purpose tool that inherently aids three crucial post-access tactics. It provides an immediate method of Persistence, as the attacker can simply continue to log in via T1078 (valid account) without needing to install persistent malware. The account also serves as a platform for Privilege Escalation, allowing the adversary to explore the network for misconfigurations from a seemingly legitimate position. Finally, all actions taken under the guise of a valid user serve as a powerful form of Defense Evasion, blending malicious activity with routine network traffic and making detection significantly more challenging.
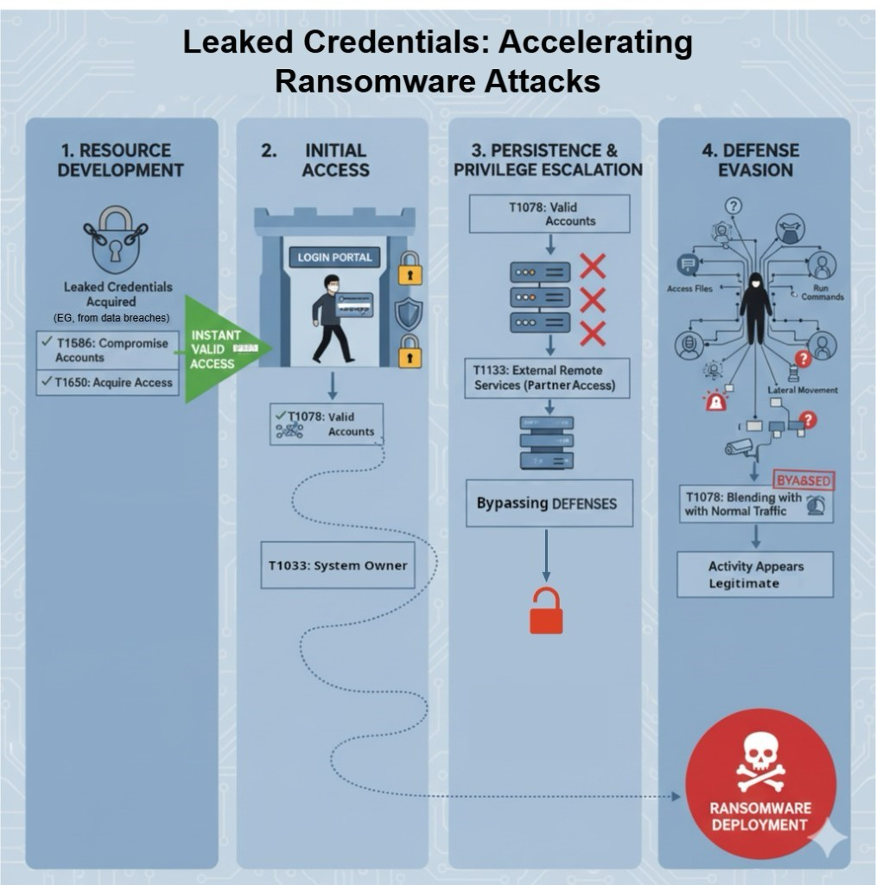
Figure 8: Diagram illustrating how leaked credentials accelerate a ransomware attack.
The Credential Cascade: Full-Scale Network Compromise
Once an initial foothold is established, the adversary’s focus shifts to internal proliferation. The goal is to leverage the initial access to acquire more credentials, escalate privileges, and move laterally through the network until control over high-value assets is achieved.
Credential Access: The first post-exploitation objective is to harvest more credentials from within the compromised environment. Adversaries employ a suite of techniques for this, including T1003 (OS Credential Dumping) to extract hashes and cleartext passwords from system memory. They also target credentials stored in applications using T1555 (Credentials from Password Stores) and scan for T1552 (Unsecured Credentials) stored in configuration files or scripts. To capture credentials in real-time, they may use T1056 (Input Capture) via keyloggers, listen to network traffic with T1040 (Network Sniffing), or intercept authentication attempts using T1557 (Adversary-in-the-Middle) tactics.
Discovery: With a growing cache of credentials, the adversary begins building situational awareness of the internal network. This reconnaissance phase utilizes techniques like T1087 (Account Discovery) to identify user and administrative accounts, T1083 (File and Directory Discovery) to search for sensitive information on file shares, and T1217 (Browser Information Discovery) to find internal websites and service portals. This intelligence informs the next stage of the attack.
Lateral Movement: Using the knowledge and credentials acquired, the attacker pivots from the initial entry point to other systems on the network. This lateral movement often relies on legitimate administrative protocols to remain undetected. Common techniques include T1021 (Remote Services), which abuses protocols like RDP and PowerShell Remoting, T1550 (Use Alternate Authentication Material) to authenticate with stolen hashes or Kerberos tickets, and T1563 (Remote Service Session Hijacking) to take over active user sessions.
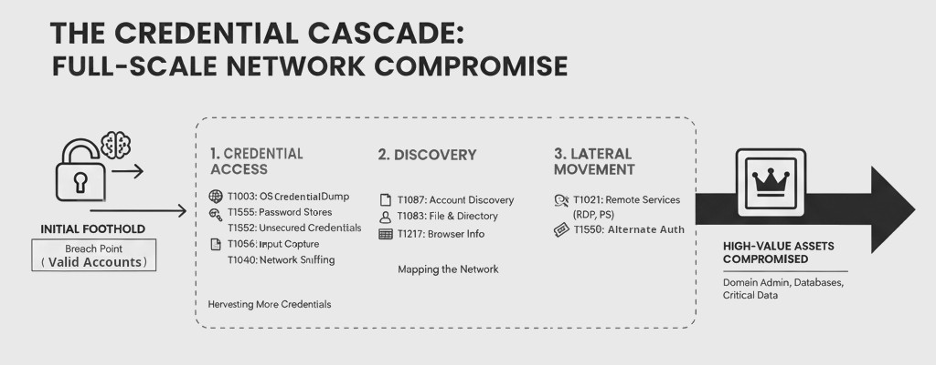
Figure 9: Diagram showing how leaked credentials enable a full-scale network compromise.
Case Study
Black Basta: Credential-Fueled Tactics from Leaked Chats
In early 2025, an unexpected leak of Black Basta’s internal Matrix chat logs (over 180,000 messages spanning Sept 2023 to Sept 2024) provided fresh insight into their operations. A core theme in these chats is Black Basta’s pervasive use of stolen credentials and how their tactics evolved when certain malware was taken down. Black Basta “levera In other words, at virtually every phase of an attack, they would try to utilize some set of credentials – whether it was logging into a compromised VPN account to get in, or using dumped admin passwords to propagate across systems, or even maintaining access by creating hidden accounts. ged stolen credentials from multiple sources for initial access, persistence, and lateral movement” in their ransomware incidents.
Black Basta’s leader (alias “GG”) and members organized campaigns to brute force internet-facing servers (like VPN gateways, RDP servers, and enterprise web apps) by trying credentials from combolists. These combolists were often compiled from infostealer logs (also called Login:Password – lists) and other leaked databases.
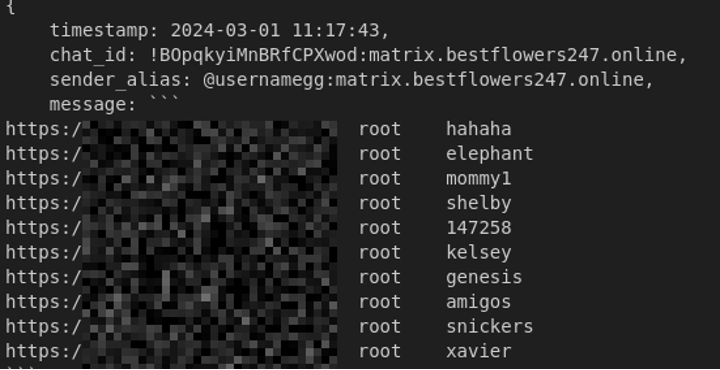
Figure 10: @usernamegg and team brute-forcing an ESXi panel using passwords generated from combolists.
Despite being a “sophisticated” group, Black Basta found plain credential guessing to be one of the most reliable ways in – highlighting that simple weaknesses (like weak or reused passwords on external systems) remain a critical risk for organizations.
In many messages, GG issues operational direction: sharing credential lists, assigning targets to specific operators, and reviewing brute-force outcomes. This suggests GG functioned as the operational lead or at least coordinated initial-access activity.
There are also direct references to using Initial Access Broker (IAB) channels.
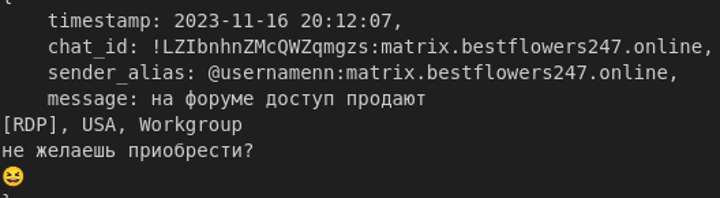
Figure 11: Post on an underground forum advertising RDP access to a U.S.-based company (“Workgroup” environment), offering to sell access.
Black Basta did not rely solely on IABs. The chats show the group distributing its own infostealers most notably Lumma to harvest fresh credentials for operations.
Figure 12: Lumma infostealer binary shared by GG.
Follow-up messages reference an “encrypted LummaC2.exe,” described as extracting “everything” i.e., harvesting credentials and other data at scale.
The chats also include examples of logs from other stealers being used for sensitive targets. For instance, a Meduza log was circulated to access a panel on a .gov domain.
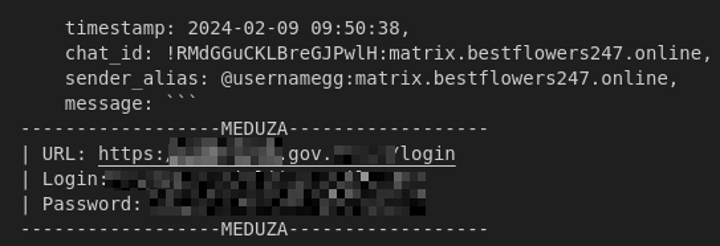
Figure 13: Meduza infostealer log shared by GG to access a government-domain panel.
Trends After the Genesis Market Shutdown
The takedown of Genesis Market in April 2023 marked a pivotal moment in the cybercrime ecosystem. As one of the largest and most structured platforms for stolen data transactions, its closure sent shockwaves throughout the underground economy. The event significantly influenced threat actor behavior and reshaped market structures across 2023 and into 2024.
Figure 14: Surface-web homepage after the FBI seizure banner replaced Genesis, April 2023.
Following Genesis Market’s shutdown, threat actors quickly migrated to alternative marketplaces. Marketplaces that came to the fore after the closure of Genesis:
- Russian Market
A dark web marketplace accessible via Tor, specializing in logs collected by various information-stealing malware families. Listings typically include account credentials, browser cookies, autofill data, saved payment information, system metadata, and sometimes cryptocurrency wallet seeds. Each listing often previews data attributes such as the number of credentials, cookie counts, operating system details, and browser types.
- BidenCash
A carding-focused market operating since 2022. On June 4–5, 2025, U.S. authorities seized ~145 darknet and clearnet domains and associated funds tied to BidenCash; seized domains now redirect to a law-enforcement banner. This operation substantially disrupted BidenCash’s infrastructure. (Any reappearing mirrors have been unreliable/short-lived.)
- Styx Marketplace
An English-language darknet market active since 2023, offering infostealer logs and other illicit data. It targets a broader, non-Russian-speaking audience compared to traditional markets.
Simultaneously, Telegram channels emerged as significant distribution hubs for stolen data. Subscription-based credential dump services proliferated, lowering barriers to entry for less experienced threat actors. The decentralized nature of Telegram operations enhanced their resilience against takedown efforts.
Without Genesis’s advanced browser fingerprinting tools, threat actors were forced to adapt. Manual methods for exploiting stolen cookies and credentials became more prevalent. The absence of Genesis spurred the development and commercialization of auxiliary tools that enhanced the processing and exploitation of raw infostealer data.
The post-Genesis landscape for infostealer data trading evolved into a more decentralized, fragmented, yet resilient ecosystem. Major platforms like Russian Market expanded their dominance, Telegram-based operations flourished, and threat actors swiftly adapted their operational security practices and exploitation techniques. The underground economy proved highly agile in the face of disruption.
Conclusion
The emergence of info-stealer logs in credential broker markets has drastically shifted the ransomware threat landscape and established a cybercrime ecosystem where compromised credentials are the currency of compromise. What began as a centralized platform in the form of Genesis Market has evolved into a resilient, decentralized network of marketplaces, Telegram channels, and Initial Access Brokers that collectively lower the barrier to entry for ransomware operations to unprecedented levels.
The evidence presented, from the industrial-level operations discovered in Black Basta’s leaked communications to the rapid adaptation after Genesis Market’s takedown, demonstrates that credential abuse has become the attack vector of choice for today’s ransomware groups. By exploiting stolen credentials, threat actors can entirely bypass traditional perimeter security and enter networks as authenticated users, operating from a position of inherent trust. This evolution represents a strategic shift from noisy, detectable intrusion methods to silent infiltration methods blending malicious behavior with legitimate network traffic.
The RaaS model has further industrialized this threat by establishing specialized roles in the cybercrime ecosystem. Initial Access Brokers have commoditized network entry points, allowing ransomware affiliates to focus on deploying the payload and encryption rather than worrying about the various hurdles that need to be overcome for the initial compromise. This division of labor has expanded the scale and frequency of attacks and democratized access to advanced attack capabilities for a much broader set of threat actors.
Perhaps the most troubling evidence is the demonstrated resilience of this underground economy. When Genesis Market was taken down, it merely accelerated the ecosystem’s evolution toward more distributed and harder-to-take-down models. Telegram-based operations, many marketplace options, and the continuous flow of fresh credentials provided by ongoing malware campaigns ensure that this threat will persist and evolve regardless of individual platform takedowns.
For defenders, this reality necessitates a fundamental shift in security strategy. A security strategy focused on perimeters is still needed, yet it is not enough when the threats begin with valid credentials. Organizations must adopt identity-centric security strategies that assume compromise and focus on detecting anomalous behavior rather than preventing initial access. This includes implementing robust credential hygiene practices, multi-factor authentication, privileged access management, and behavioral analytics that can identify and distinguish between legitimate user activity and credential abuse.
The credential supply chain feeding ransomware operations will continue to grow as long as password reuse remains commonplace, as long as data breaches continue to leak authentication materials, and info-stealer malicious software continues to proliferate across the threat landscape. The underground economy has proven its ability to rapidly adapt to disruptions, suggesting that sustained pressure across multiple fronts technical countermeasures, law enforcement action, and fundamental changes in authentication practices will be necessary to meaningfully impact this threat.
In the end, the development of credential markets represents a maturation of cybercrime into a sophisticated, resilient industry. As this ecosystem continues to evolve, defenders must remain equally adaptive, moving beyond reactive security measures toward proactive, intelligence-driven approaches that account for the reality that in today’s threat environment, credentials represent currency, and every leaked password is a potential ransomware incident waiting to happen.







