What Happened in Manufacturing Sector in Q3 – Q4 of 2022?
In recent years, ransomware attacks have become frequent and severe. The onslaught has concentrated on the manufacturing sector, with producers providing easy targets for bad actors. In this industry, it’s vital to recognize the latest trends and defend yourself accordingly.
The manufacturing sector comprises establishments engaged in the mechanical, physical, or chemical transformation of materials, substances, or components into new products. Establishments in the manufacturing sector are often described as plants, factories, or mills and characteristically use power-driven machines and materials-handling equipment. However, establishments that transform materials or substances into new products by hand or in the worker’s home and those engaged in selling to the general public products made on the same premises from which they are sold, such as bakeries, candy stores, and custom tailors, may also be included in this sector.
As the manufacturing sector increasingly relies on software and digitization, it becomes a common target for ransomware attacks that can compromise data security and cause costly disruptions. To prevent these issues, many companies in this sector are prioritizing cybersecurity measures to protect their data and operations.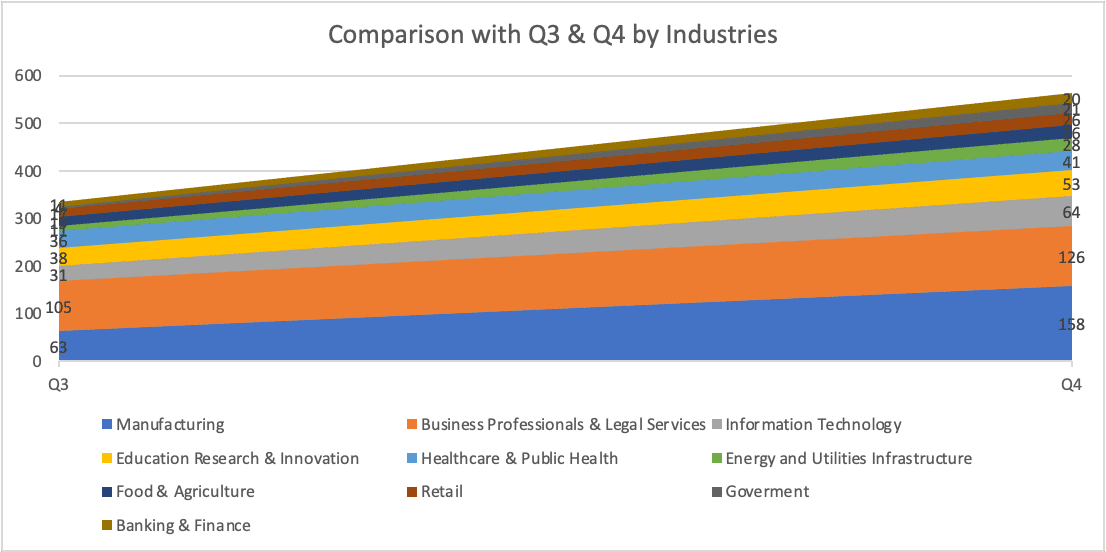
A Conceptual Look About Ransomware Attacks in Other Sectors
Ransomware attacks increased substantially in 2022 across multiple sectors, with the government sector experiencing the highest increase at 425%. Other sectors, such as energy and utilities, manufacturing, banking and finance, and IT, also saw notable increases. However, some sectors saw less of an increase, with business professionals and legal services seeing only a 20% increase and retail only seeing a 53% increase. The healthcare and public health sector were the least affected, with a 14% increase. This data emphasizes the importance of cyber security for all industries.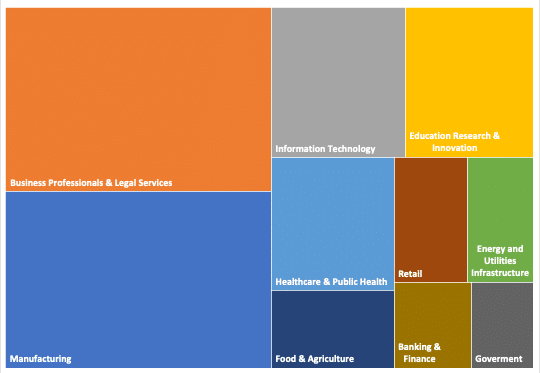
Why Are Ransomware Attacks on the Rise?
The COVID-19 pandemic has put a strain on IT workforces and made it difficult for companies to keep up with the constantly changing tactics of cybercriminals. As a result, factories, which often have large computer systems with inadequate security measures in place, have become vulnerable targets for attacks. The limited size of many security teams only compounds this problem, making it difficult for these organizations to effectively defend against these threats.The graphic shows the attacks received by the sectors in the last 6 months of 2022. Especially Manufacturing and Business, Professionals % Legal (such as law office, hotels insurance companies) sectors the biggest share of the pie. Moreover, the education, health and information technologies sectors are among the sectors most preferred by threat actors.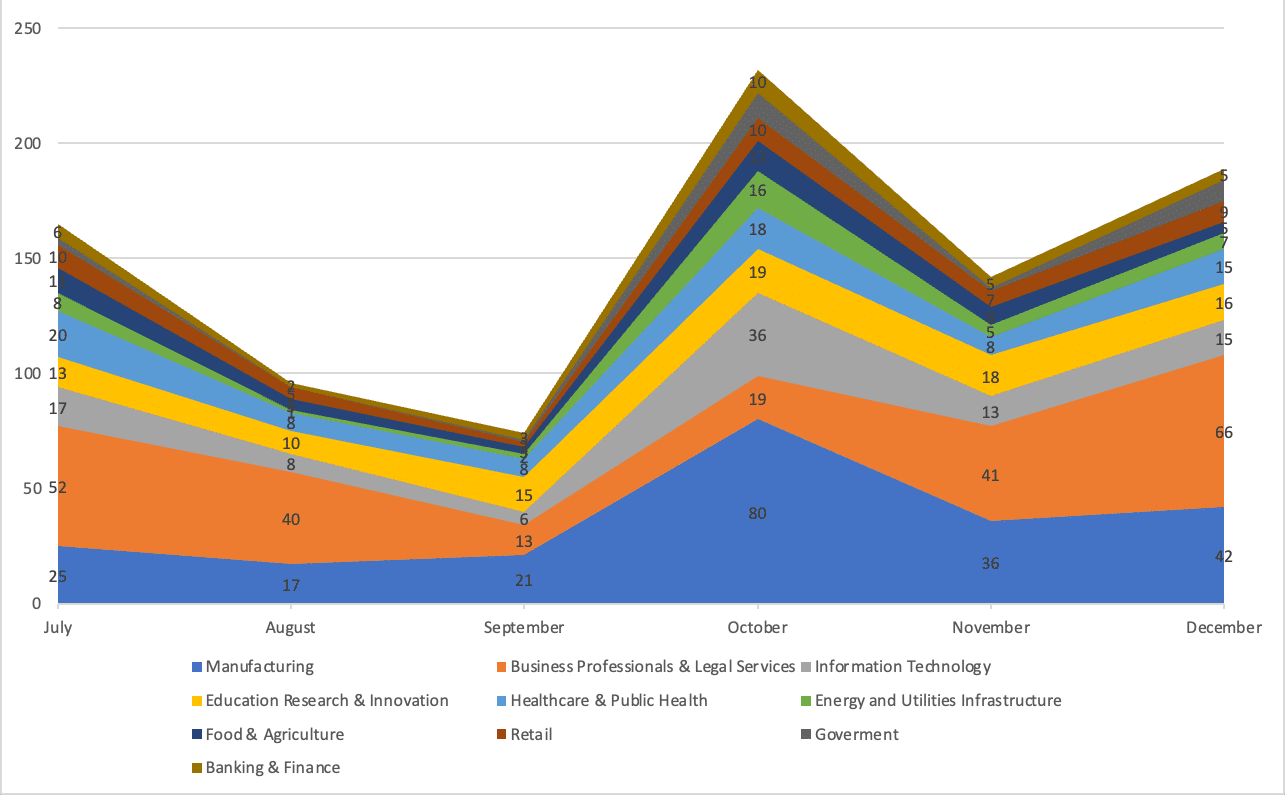
In 2021, the technology manufacturer Acer suffered a massive cyber assault. The criminals, who call themselves REvil, claimed credit for the disruptions. While the route of entry remains unknown, experts have speculated that a Microsoft Exchange vulnerability might be to blame. REvil demanded $50 million to release the locked data, more than any previous ransom in the history of cybercrime. To prove their involvement in the assault, the group posted pictures of sensitive files online.
How to Brandefense Can Help You?
When it comes to cybersecurity, the “attack surface area” refers to the various points within a system that could potentially be targeted by malicious actors. It is the sum total of all potential entry points or attack vectors into a system, application or network. It includes all the various ways an attacker can access sensitive information or disrupt the normal functioning of the system. The attack surface can encompass a wide range of entry points, such as network ports, services, software vulnerabilities, user credentials, and more. In general, the larger the attack surface, the more potential vulnerabilities there are that can be exploited by an attacker.
Attack Surface Management (ASM) is the process of identifying, analyzing, and reducing the attack surface of a system, application or network. It involves identifying all entry points, or attack vectors, that a potential attacker could use to gain access to sensitive information or disrupt the normal functioning of a system. The goal of ASM is to reduce the risk of security breaches by identifying and mitigating vulnerabilities in systems and applications.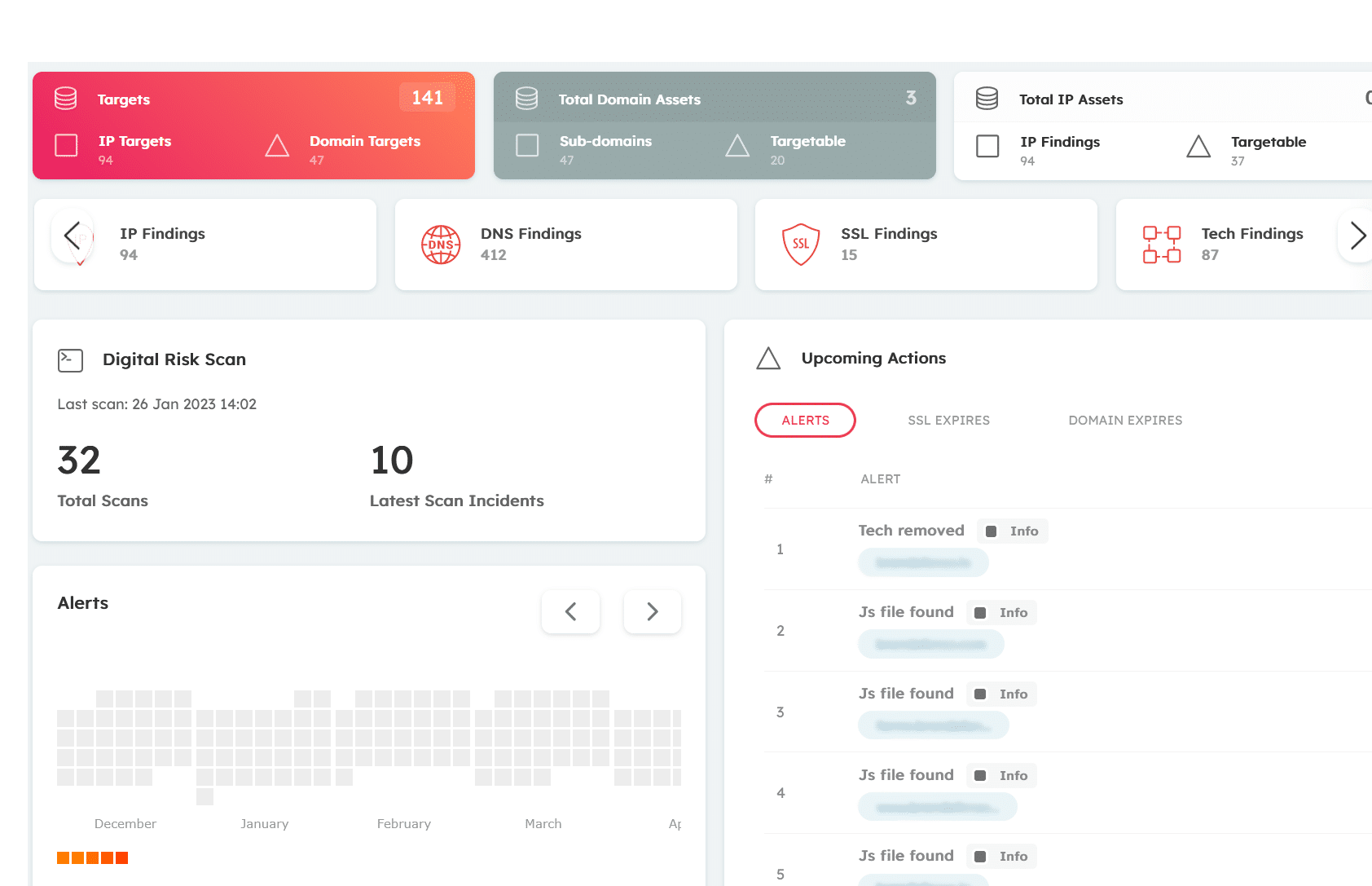
Conclusion, Mitigations & Recommendations
There are several steps that companies can take to protect themselves, such as;
- Improving email security,
- Regularly backing up data,
- Keep systems and applications up to date by scanning for security vulnerabilities,
- Do not access links in unsafe spam messages or unknown websites,
- Do not provide personal information to untrusted sources,
- Never use USB sticks obtained from unknown sources,
- Use VPN services on public Wi-Fi networks,
- Institutions and organizations should provide awareness training to their employees against cyber security threats,
- Up-to-date security solutions should be used in systems and e-mail mail servers.
By taking these measures, companies can significantly reduce their risk of falling victim to a cyberattack.






