Introduction: Why Shadow IT Matters Today
Shadow IT is a security issue, and a problem for IT governance. It exponentially increases the external attack surface. Any untracked SaaS account, any unclaimed subdomain, any unmanaged API is a potential access point. If you can’t see it, you can’t protect it. In this post, we’ll look at how attackers find shadow IT, what kind of risks they pose, and how organizations can mitigate their exposure through continuous monitoring.
The Expanding Digital Perimeter
The traditional IT perimeter is a relic of the past. Businesses operate in the cloud, with SaaS products and are increasingly reliant upon APIs and remote endpoints. Each of these introduces internet-facing assets. Shadow IT further expands this perimeter without any visibility or authorization. Employees deploy tools, register domains, or connect services that IT has little to no control over. Accordingly, there is an expanding attack surface with unknown systems displayed on the internet!
How Attackers Find Shadow IT
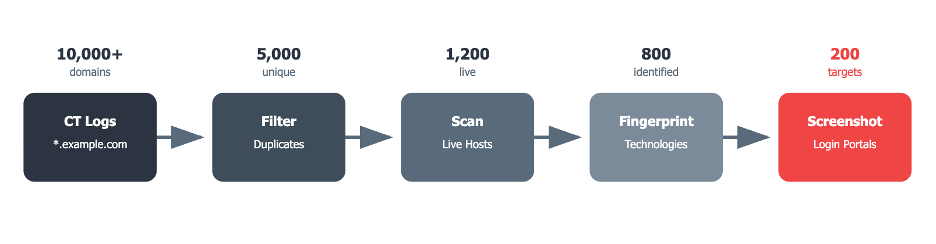
Attackers employ straightforward techniques to identify Shadow IT. One of the most common techniques is Certificate Transparency (CT) logs. All TLS certificates are logged in public CT logs. Attackers can run wildcard queries on CT logs, such as *.example.com, and amass thousands of subdomains.
Attackers automate the actions above and follow some variations of the following steps:
- Collect the hostnames from CT logs.
- Remove duplicates and systems that are not active.
- Scan for live hosts and open ports.
- Fingerprint technologies and software versions.
- Capture screenshots of login portals and admin pages.
In the end, they will have a shortlist of high-value targets that are often not visible to defenders.
The Hidden Risks You’re Missing
Shadow IT usually leads to huge blind spots. Instances include:
- Forgotten domains pointing to old servers.
- Cloud storage buckets where there is no authentication.
- Legacy VPN gateways that still exist, remain unpatched, and are still online.
- SaaS apps that place sensitive customer data beyond official monitoring.
Risks that security teams typically cannot see because they are outside of governance. Attackers can easily exploit them. A single misconfigured asset is enough to facilitate a serious incident.
Common Findings in 2025: What Shadow IT Exposes Most
Recent attack surface monitoring data shows that the same categories of exposures keep coming up over and over again. In 2025, the most common items found during external asset discovery include:
- Misconfigured cloud storage: Open S3 buckets, Azure Blob containers, or Google Cloud Storage with public access allowed.
- Exposed admin portals: Forgotten subdomains that contain login pages but no multi-factor authentication.
- Out-of-date VPNs and remote access gateways: Legacy systems with known CVE vulnerabilities that are still publicly exposed.
- Unpatched web frameworks and libraries: WordPress, Drupal, or older JavaScript frameworks running on forgotten sites.
- Leaked development environments: Test servers with weak or default credentials.
- Abandoned DNS records: Sub-domains pointing to decommissioned infrastructure that are still vulnerable to takeover.
These results show how Shadow IT increases the attack surface. Often, these are not sophisticated vulnerabilities but simple oversights. Attackers know how prevalent these items are because organizations usually can’t or don’t track them or remediate them.
Turning Discovery into Continuous Defense
One-time assessment is insufficient. The attack surface evolves constantly. Assets arise, change, go away. Attackers search the Internet continuously; therefore, defenders need to assess continuously.
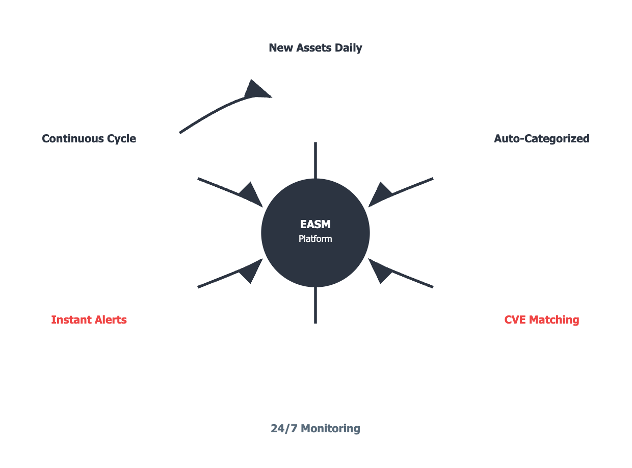
External Attack Surface Management (EASM) provides this visibility and automates:
- Enumeration of new assets
- Classification of systems by type
- Vulnerability scanning for exposures
- Tracking changes with time
- Alerts and remediation workflows
This process transitions the organization from a discovery process into a continuous attack defense cycle. When done properly, it guarantees that Shadow IT is detected and remediated before attackers take advantage.
Building a Proactive Strategy
Technology and process must be aligned. Technical controls include continuous monitoring of the CT log, automated asset inventory, integration with IAM systems, and a Zero Trust access model.
With that said, human factors matter. Staff need to properly understand the risks of using unapproved tools. Explicit policies and secure usage alternatives can limit shadow IT and technology risks. Education will also build awareness and support compliance while ensuring none of your users or infrastructure is excluded by default.
Zero Trust should be the ultimate goal. No user, device, or service is trusted. Even if Shadow IT presents itself, verification limits its impact.
Conclusion
Shadow IT is a constant in the modern organization. It doesn’t have to be a mystery anymore. We can harness the same methods that attackers use to also assist defenders. By leveraging continuous monitoring, automated discovery, and as part of a proactive strategy, organizations can include Shadow IT as part of their external attack surface. Attackers already see these assets; the only question is whether you do.






