Introduction
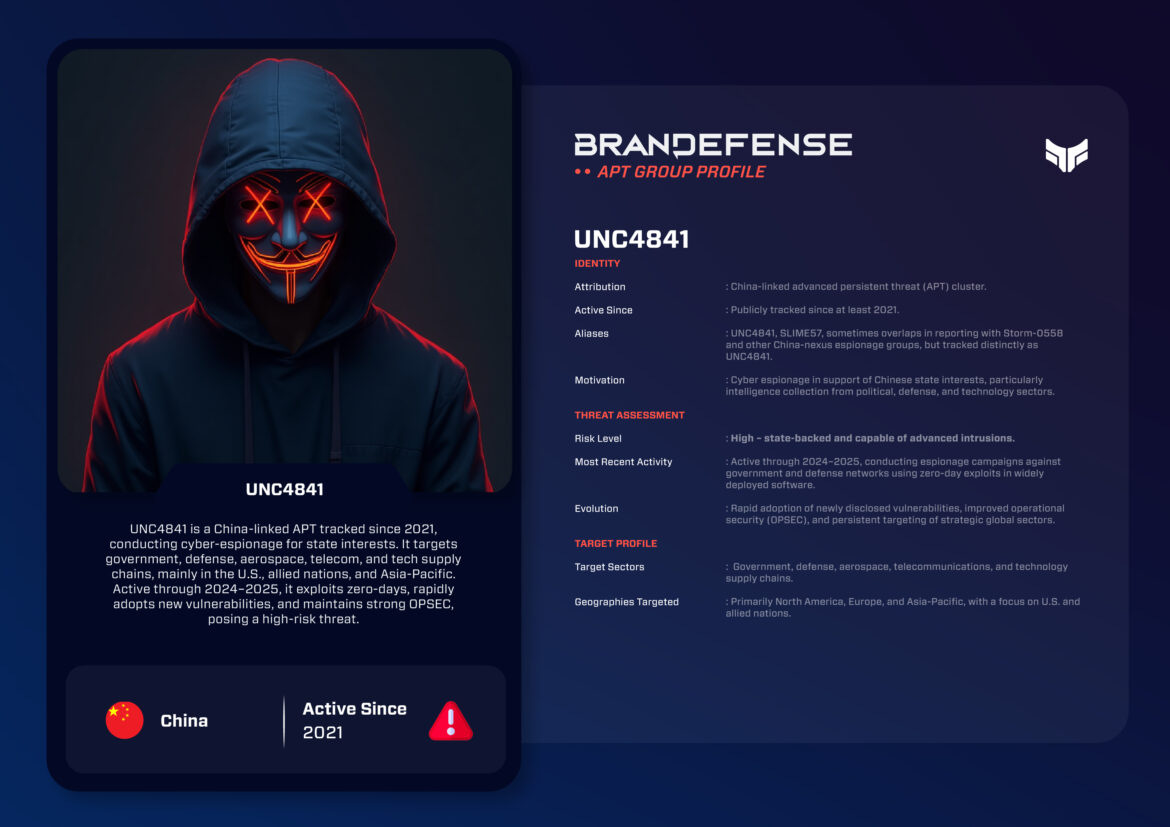
UNC4841, also identified as SLIME57, is a China-linked and emerging advanced persistent threat (APT) cluster that has been more notable over the last several years. At least since 2021, the group has been recognized as a high-risk espionage actor utilizing zero-day vulnerabilities, compromising the supply chain, and deploying malicious spear-phishing to breach sensitive networks around the world. NC4841/SLIME57 focuses predominantly on the government, defense and technology sectors. The actions of UNC4841/SLIME57 illustrate Beijing’s continued deployment of cyber operations as an approach to project power and gather intelligence.
This blog explores the group’s identity, focus, motivations, tactics, noteworthy operations, and developments over the past year, with some defensive recommendations for organizations that find themselves at risk of UNC4841/SLIME57.
Identity and Motivation
UNC4841/SLIME57 operations are largely attributed to state-sponsored APT espionage originating from China. The group is engaged in activity that supports Beijing’s strategic directive to collect intelligence on political, military, and technology from their adversaries.
The group’s motivation is based around three lines of effort:
1. Political intelligence: Tracking discussions of policy, government-to-government engagements, and international negotiations.
2. Military and defense data: Targeting defense ministries, contractors, and aerospace programs to discern a state’s military readiness and military technology capabilities.
3. Technology acquisition: Targeting telecoms, software, and supply chain actors to close the technological gap between China and its competitor.
Aliases: Also known as UNC4841, SLIME57 is sometimes associated with groups such as Storm-0558, but remains classified separately as its own operational cluster.
TTPs (Tactics, Techniques & Procedures)
UNC4841/SLIME57 stands out for their speed in adopting newly disclosed vulnerabilities, and stealthy intrusions against difficult targets. TTPs include:
Techniques: leverages living-off-the-land binaries (LOLBins), credential dumping, lateral movement, and stealthy exfiltration of sensitive datasets.
Initial Access: exploits zero-day vulnerabilities of enterprise applications, and delivers spear-phishing emails with weaponized attachments.
Persistence: maintains long-term access through compromised VPN credentials, scheduled tasks, registry changes, and web shells.
Command & Control (C2): communicates with custom malware families using HTTPS and DNS tunneling channels; rotates domains often and frequently to evade detection.
Malware & Tools: utilizes custom implants, credential stealers, exploitation frameworks, backdoors specific to the environments of their victims.
Notable Operations
- 2021:UNC4841 became the first publicly identified group to exploit enterprise software vulnerabilities as a means to target government and defense targets.
- 2022: UNC4841 performed spear-phishing campaigns aimed at Asia-Pacific defense contractors and ministries, and began demonstrating its developing capability to penetrate secure networks.
- 2023: UNC4841 exploited zero-day vulnerabilities in collaboration and messaging platforms, gaining access to the sensitive communications of U.S. and European government agencies.
- 2024: UNC4841 attracted the attention of a new group of victims, engaging in expanded operations into supply chain compromises by targeting software vendors and telecommunications infrastructure providers within a supply chain to provide indirect access.
- 2025: UNC4841 and SLIME57 were active with campaigns exploiting new zero-day vulnerabilities against enterprise applications. They continued to target NATO member countries, defense supply chain organizations, and sensitive research organizations.
Recent Developments
By 2025, UNC4841/SLIME57 has evolved into a highly capable and mature APT organization. Reports from security reports indicate the group has made significant improvements in its operational security practices, increasing stealth and survivability within compromised environments. The use of supply chain attacks indicates a substantive operational change to indirect infiltration methods resembling those executed by other state-sponsored groups like APT10.
The group’s efforts have become increasingly global in nature. While the U.S. and its allies are still primary targets of their efforts, evidence of their operations have also been seen in the Asia-Pacific region and even Europe, at governments and defense contractors who are openly supporting Ukraine or working with other partners on Indo-Pacific defense. These activities show how UNC4841’s operations coincide with Beijing’s military objectives.
Conclusion
UNC4841/SLIME57 is one of the most dangerous espionage groups with a China nexus operating today. Their innovation in rapidly adopting zero-day exploits, persistence in overcoming supply chain compromise, and operational tradecraft flexibility set them apart as a key adversary and a significant challenge, for some of the best organizations’ defenses are yet to be thwarted.
For defenders, it reinforces the need for vigilance, rapid vulnerability management, and the ability to detect and respond to advanced threats.
Defensive Takeaways
- Patch Management: Apply security patches quickly when it comes to Internet-facing applications experiencing zero-day exploits.
- Phishing Defense: Increase employee awareness programs and implement an email security stack.
- Access Control: Watch for unauthorized VPN logins, suspicious scheduled tasks, or registry changes.
- Network Monitoring: Monitor for DNS tunneling or unusual outbound traffic indicative of potential C2 actions.
- Threat Intelligence: Keep an eye out for indicators of compromise (IOCs) associated with campaigns linked to
UNC4841/SLIME57 will remain a key cyber-espionage threat while tensions between China and the West continue. The further campaigns issued by UNC4841/SLIME57 highlight a trend of Chinese APTs that are both persistent and adaptive, using cyber operations as a key enabler to further their national interests. Organizations around the world must remain vigilant, as UNC4841/SLIME57 targets expand its reach in 2025 and beyond.
You can download and review the sheet for all the details!







