Monitor, Identify, Analyze
Take Action to Cybersecurity Threats
Every day, hundreds of companies have been under cyber-attacks. However, when a general analysis is made, most companies cannot detect these attacks and generate alerts. Even if they can detect it, they cannot make the necessary investigation and take action.
One Complete Platform for Digital Risk Protection
We will eliminate the noise and be your eyes and ears by focusing on cyber threats. Your mission is ours.
With Brandefense, companies can monitor, identify, analyze and take action on the cyber world, crime/criminal psychology, and their identities. Security professionals' workload makes it hard to keep up with cybercriminals' newest TTPs. Brandefense meets security professionals' needs and simplifies the process of collecting actionable cyber intelligence. By solving SOC's complex challenges, we aim to be the global leader in cyber threat intelligence and brand monitoring services. We are here to help Brandefense customers to protect their brands and reputations against cyber threats.
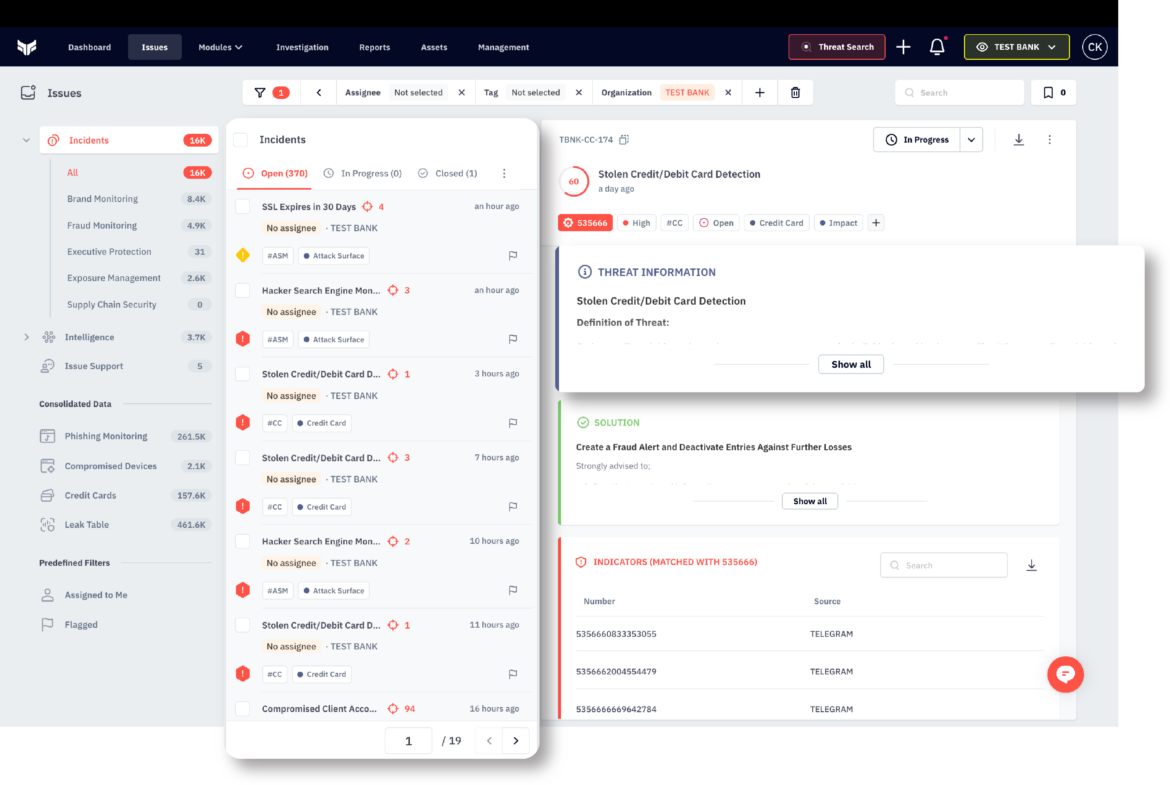
All you need in one platform with Brandefense, you can monitor and identify advanced threats and take early action.
Brand Monitoring
Brand Monitoring employs cutting-edge methodologies to identify and counteract a diverse range of threats to your brand's digital presence.
Attack Surface Management
Attack surface management is the proactive identification, assessment, and mitigation of an organization's attack surface to defend against attacks.
Cyber Threat Intelligence
Staying ahead of cyber threats is not just a necessity; it's a strategic imperative. Effective threat intelligence is the cornerstone of a robust security posture.
Fraud Protection
In the digital age, it's crucial to prioritize fraud protection. Cyber criminals can easily access personal information with a click and cause havoc on an unsuspecting victim's life.
Third-Party Risk Management
Strengthening your organization requires understanding gaps, implementing processes, and addressing third-party risk management for sustainable growth. Our approach involves continuous monitoring, advanced threat detection, and proactive defense to ensure the integrity, availability, and confidentiality of your operations.
Vulnerability Intelligence
Vulnerability Intelligence is a solution designed to equip you with the insights and tools needed to proactively identify, assess and mitigate vulnerabilities.
Why Do You Need a Digital Risk Protection Services?
In the complex and ever-evolving digital landscape, companies often face several challenges in their journey to protect their assets, data, and brand image. Some of these challenges include rapidly emerging threats, diverse digital touchpoints, complex compliance requirements, scalability, and integration with existing systems. Brandefense has been designed with these challenges in mind, offering effective solutions for each one.
Monitor, Identify and Takedown
All you need in one platform with Brandefense, you can monitor and identify advanced threats and take early action.
AI Enabled Intelligence
Brandefense offerings Enabling AI-driven Cyber Security for Threat Intelligence and Phishing Detection Operations and Analytics Solutions.
Real Time Protection
Brandefense keeps track of all the news and incidents that may be relevant to your brand’s value. It allows you to take early action based on the insights of real-time cases.
Reduce False Positive Incidents
We eliminate junk intelligence and focus on cyber threats.
Actionable Intelligence Feeds
Brandefense meets security professionals’ needs and simplifies the process of collecting actionable cyber intelligence.
Digital Risk Protection Services FAQs
Digital Risk Protection, or DRP, is a type of online security that helps protect individuals and businesses from online risks. It can help identify and block potential threats, as well as provide guidance on how to respond to an incident. DRP can also monitor online activity to help detect and prevent future risks.
Individuals and businesses face a variety of risks when they go online. These include phishing attacks, malware, and data breaches. DRP can help protect against these risks by providing tools and services that can identify and block potential threats. In addition, DRP can provide guidance on how to respond to an incident.
As the dark web becomes more accessible to people all over the world, the need for digital risk protection services is increasing. There are a number of reasons why you might need such a service, but some of the most common include:
- To protect your online identity and personal information
- To prevent cybercriminals from accessing your devices or networks
- To avoid being victimized by online scams or fraudsters
- To ensure that your confidential data remains private and secure
Digital risk protection services can provide you with the peace of mind knowing that your online presence is safe and secure. If you are concerned about the dark web and what it could mean for you or your business, then consider investing in a quality digital risk protection service.
There are many types of digital risks that can cause damage to individuals, businesses, and organizations. These risks can come in the form of malware, phishing attacks, data breaches, and more. Malware is a type of malicious software that can infect computers and devices, causing them to malfunction or giving attackers access to sensitive information. Phishing attacks are attempts by criminals to obtain personal or financial information by posing as a trustworthy source in an email or other communication. Data breaches occur when sensitive information is leaked or stolen from a business or organization, often through hacking. These breaches can put customers and employees at risk of identity theft and fraud. Other risks include online scams, cyberbullying, and sextortion. Each of these risks can have serious consequences for those who are affected.
Cyber threat intelligence (CTI) is information that organizations use to understand the nature and scope of current and future cyber threats. CTI can include data about attackers, their tools and tactics, vulnerabilities, and indicators of compromise. Organizations use CTI to inform their security decisions and strategies.
There are many sources of CTI, including commercial vendors, government agencies, open-source intelligence (OSINT), and first-party intelligence gathered by an organization itself. To be useful, CTI must be timely, accurate, actionable, and relevant to the organization’s needs.
Organizations may collect and analyze CTI using a variety of methods, including manual analysis, automated analysis, or a combination of both.
A cyber threat intelligence feed can provide your organization with actionable, real-time information about the latest threats and vulnerabilities. This type of intelligence can help you to quickly and effectively respond to attacks, and to protect your systems and data from future threats.
A cyber threat intelligence feed can also help you to understand the motivations and methods of your attackers, so that you can better defend against future attacks. Additionally, a cyber threat intelligence feed can provide insights into emerging trends in the cybersecurity landscape, so that you can stay ahead of the curve.
Overall, a cyber threat intelligence feed can be an invaluable tool for protecting your organization from cybersecurity threats. If you are not already utilizing a feed, we encourage you to consider doing so.
Cyber threat intelligence (CTI) is critical for organizations in today’s digital age. CTI can help organizations identify, assess and respond to cyber threats. It can also help them improve their overall cybersecurity posture and better protect their systems and data.
Organizations that use CTI can more effectively defend against cyberattacks and other online threats. CTI can also help organizations investigate and prosecute those responsible for attacks. In addition, CTI can help organizations understand the motivations behind attacks and the methods used to carry them out.
CTI is an important part of any organization’s security strategy. It can help organizations make informed decisions about how to best protect their systems and data.
1. Planning and target identification: The first step in any intelligence operation is to identify the targets that you want to collect information on. This process includes considering what information would be most valuable, who are the likely sources of that information, and what methods can be used to collect it.
2. Data collection: Once the targets have been identified, the next step is to collect data on them. This data can come from a variety of sources, including open-source intelligence (such as news reports or social media posts), human intelligence (through informants or espionage), or electronic interception (such as hacking into email accounts or phone records).
3. Data analysis: Once the data has been collected, it must be analyzed in order to extract the useful information from it. This process can involve using a variety of techniques, such as link analysis (to identify relationships between people or organizations) or pattern analysis (to find trends or commonalities).
4. Dissemination: The final step is to disseminate the intelligence that has been collected and analyzed to those who need it. This can be done through written reports, verbal briefings, or even secure online portals.
There are three main types of cyber threat intelligence:
- Strategic Intelligence
- Tactical Intelligence
- Technical Intelligence
Strategic intelligence is high-level information that helps organizations make decisions about long-term planning and strategy. It includes information about an organization’s goals, objectives, and overall direction.
Tactical intelligence is information that helps organizations make decisions about short-term actions and operations. It includes detailed information about specific threats and how to defend against them.
Technical intelligence is information that helps organizations understand the technical details of threats and how to mitigate them. It includes information about vulnerabilities, exploits, and malware.
Attack Surface Management (ASM) is the proactive process of identifying, assessing, and reducing an organization’s exposure to cyber threats. ASM helps reduce an organization’s “attack surface” by eliminating potential entry points for adversaries. This, in turn, makes it more difficult and costly for attackers to successfully compromise systems and data.
ASM is a key component of a comprehensive cybersecurity program. When combined with other security measures such as vulnerability management, incident response, and user education, ASM can significantly reduce an organization’s risk of suffering a damaging cyber attack.
Botnets are networks of computers that have been compromised by malware and can be controlled remotely by hackers. Botnet intelligence is the process of collecting information about these networks in order to understand their structure and capabilities better and, ultimately, to thwart their activities.
An Advanced Persistence Threat (APT) is a type of cyber attack in which an attacker establishes a foothold on a victim’s system and then uses that foothold to launch further attacks, usually for the purpose of stealing sensitive data.
APT attacks are often highly targeted and tailored to the specific needs of the attacker, making them difficult to detect and defend against. APT attacks typically involve several stages, including reconnaissance (gathering information about the target), initial entry (gaining access to the target system), lateral movement (moving around within the target system to gain further access and privileges), and data exfiltration (stealing sensitive data from the target system).

