Anonymous Sudan: Unleashing Cyber Chaos with Massive DDoS Attacks in June and July 2023
In June and July 2023, Anonymous Sudan shook the cyber world with a series of powerful DDoS attacks, significantly impacting various industries and online platforms, including Microsoft, SWIFT, and Riot Games.
Since January 2023, the hacktivist group Anonymous Sudan, or Storm-1359, has been grabbing global attention. With their infamous Distributed Denial of Service (DDoS) attacks, they’ve disrupted critical infrastructure and diverse industries across the globe, reaching countries such as Denmark, the UAE, the US, Australia, Sweden, the Netherlands, Israel, Germany, France, Kenya, and Iran. From financial services to aviation, education, healthcare, software, and government entities, their operations have left a significant impact.
Despite the name, there is no apparent connection between the group and Sudan or its previous Anonymous group. Recent findings indicate a concerning affiliation between Anonymous Sudan and the pro-Russian hacktivist collective, Killnet. There are strong indications that the group might be state-sponsored Russian actors adopting the facade of Sudanese actors with religious motives, possibly to obscure their actions against Western targets. While the hacktivist group predominantly operates in English and Russian, their recent posts in Arabic appear to make cultural and nationalistic references to Sudan. Nevertheless, the timing of their first Arabic post coincided with security researchers questioning the group’s true ideological affiliations, raising doubts about their true motivations and origins.
Different Attacks by Anonymous Sudan in 2023
We warned you! A week ago! #Microsoft claimed that #DDoS attacks caused disruptions and remarked on the threat actors as Storm-1359 in the blog post about the attack. Storm-1359 calls themselves “#AnonymousSudan“#cybersecurity https://t.co/2EpvyBQ0xi
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) June 19, 2023
#AnonymousSudan on the move! After targeting 🇦🇺 Australia’s aviation, health, & education sectors, they now set sights on 🇩🇰 Denmark. Sectors in Denmark should be cautious & prioritize services like @Cloudflare protection for #DDoS. Stay vigilant, prioritize #opAustralia 🔐🌐💻 pic.twitter.com/n2y8iUsHw6
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) March 29, 2023
🔥🌐 Anonymous Sudan & KillNet launch DDoS attacks on 🇫🇷🇧🇾 Airports & hospitals. One target, https://t.co/GqsoNjyzrD, experienced a brief outage as proof of the attack. We’re sorry to hear of these incidents. Stay vigilant, #security pros!💻🛡️ #DarkWeb #CyberSecurity #DDoSAttack. pic.twitter.com/yS64XYmJxg
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) March 22, 2023
Details of Attacks
Strikes to the Giants: Microsoft and SWIFT
In June 2023, Anonymous Sudan targeted Microsoft with a massive DDoS attack, causing significant disruptions and outages across various Microsoft services, including Azure, Outlook, and OneDrive.
The group launched multiple Layer 7 DDoS attacks against the tech giant to exhaust system resources with high loads of SSL/TLS handshakes and processing HTTP(S) requests. Although Microsoft confirmed the service disruptions, the company stated that no customer data had been accessed or compromised.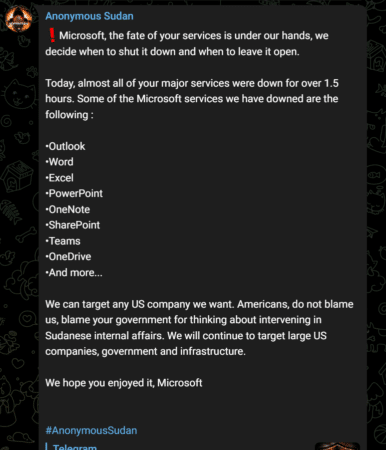
The group announced its intentions on its official Telegram channel, stating plans to launch a “massive attack” on European and US financial institutions in collaboration with the pro-Russian hacktivist collective Killnet and the infamous Russian cybercriminal group REvil. The motivation behind this attack was to protest against what they perceived as the West’s financial and military support of Ukraine.
Taking on US Companies: Riot Games and More
Making a daring decision, Anonymous Sudan also declared war against the US companies by citing America’s attitude towards Sudan. The group launched a DDoS attack against Riot Games, a renowned video game developer, and publisher famous for its multiplayer online battle arena game, League of Legends.
The hacktivist group announced the attack on their Telegram channel, boasting that it lasted between 30 minutes to one hour.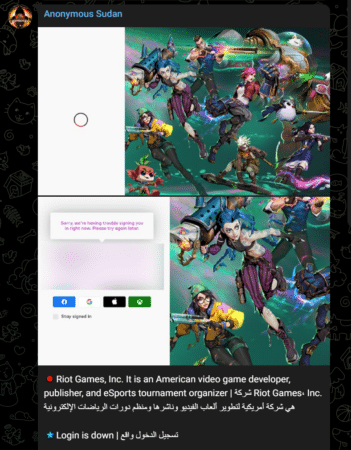
Brandefense Dark Web Monitoring Solution
Our innovative service offers a range of benefits that can help you stay ahead of cybercriminals and protect your brand reputation. With early detection of cyber threats, you’ll have more time to respond and prevent potential data breaches or other attacks. Our dark web monitoring can enhance your overall security posture and protect your sensitive data and assets.
Our Dark Web Monitoring service offers;
Early Detection of Cyber Threats: Dark web monitoring allows businesses to detect cyber threats early on, giving them more time to respond and prevent potential data breaches or other attacks.
Enhanced Security: By monitoring the dark web for potential threats, businesses can stay ahead of cybercriminals and protect their sensitive data and assets.
Brand Protection: Dark web monitoring can also help businesses protect their brand reputation by detecting any attempts to sell counterfeit products or impersonate their brand.
Cost-Effective: The cost of a data breach can be substantial in terms of financial losses and damage to brand reputation. Dark web monitoring is a cost-effective way to mitigate these risks and prevent costly cyber attacks.
Contact us today to learn more about how Brandefense’s dark web monitoring service can help you protect your business and achieve peace of mind.






