We’ve gathered darkweb insights and news for you. Enjoy!
Deep Dive at The Dark Web
Here are the insights & security news from the darkweb. Learn and protect yourself before threats reach you. If you want to get more insight, follow us on Twitter and Subscribe to our Ransomware Newsletter!
Opengear Server Keys on Dark Web: A Threat to Critical Infrastructure Security
Our latest findings on the dark web revealed an alarming discovery of Opengear server product keys on the dark web, reportedly sold for €150. The threat actor claims a 60-day uptime, raising concerns about the security of the critical infrastructure. These keys could have been obtained from Opengear itself or companies’ servers. If they belong to companies using Opengear services, monitoring systems closely to prevent potential data breaches is crucial.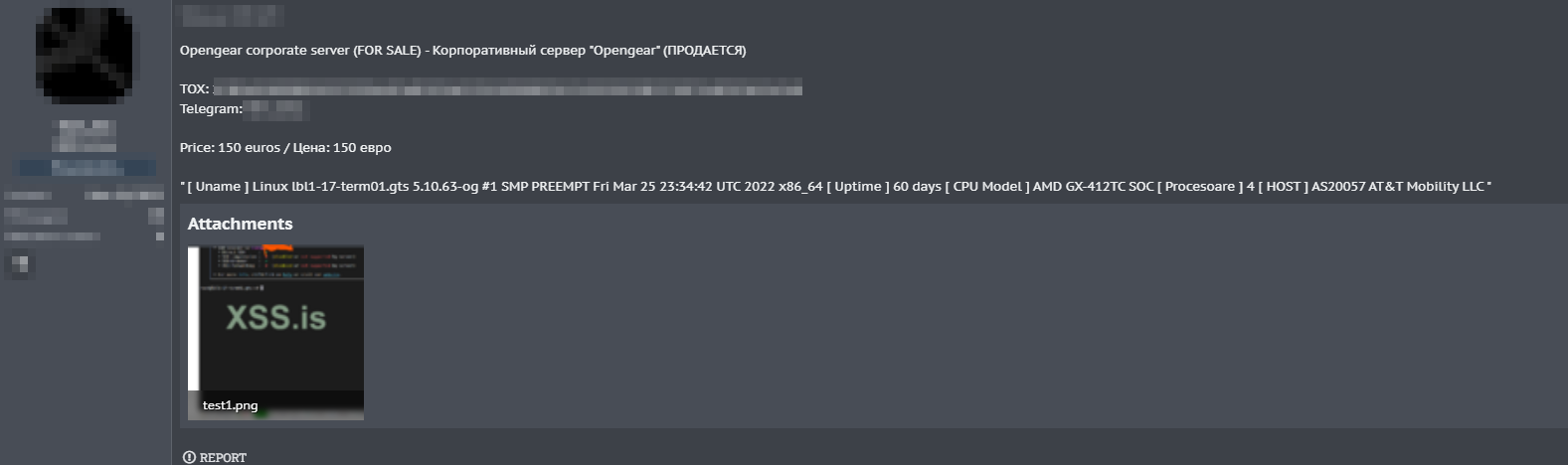
In light of these findings, it’s essential for businesses using Opengear services to monitor their systems and ensure that unauthorised access doesn’t compromise their critical infrastructure. Encryption alone might not be enough to protect sensitive data; staying vigilant and implementing additional security measures can safeguard against potential ransomware and data breaches.
AnonGhost Hacktivist Group Targets Israeli Defense Forces and Claims Access to Thousands of Bank Accounts
Last month, AnonGhost Official, a pro-Palestinian hacktivist group, claimed to have targeted the Israeli Defense Forces (IDS) by sharing an IP address list of remote access credentials for certain servers in Israel. The group had previously declared its intention to target Israel.
AnonGhost claims to have used a 0-day exploit to launch ransomware attacks on some RDP servers in Israel, sharing images as evidence. This is a bold claim for a hacktivist group. They assert that they have conducted the attacks using their own custom-written scripts and have gained unauthorized access to several servers. However, the extent of their activities remains unclear.
The hacktivist group also alleges having access to thousands of Israeli bank accounts, including accounts at Bank Hapoalim. As proof, they shared a screenshot taken from the online banking portal of Bank Hapoalim. Hacktivist group claims to have bypassed Bank Hapoalim’s 2FA security. However, this evidence is insufficient to support their claims. The hackers may have acquired access to these accounts through phishing campaigns and malware, though the information provided remains unreliable.
⚠️ Israeli banks targeted: #AnonGhost group alleges breach, circumventing Bank Hapoalim’s 2FA.
Proof: portal screenshot.
Possible phishing & malware, accounts compromised with username & password only. 🛑 Unconfirmed. #cyberattack #israelibanks #hacktivist pic.twitter.com/VcAnN7L3Bw
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) April 3, 2023
Short-Cuts
- PrintNightmare resurfaces on the dark web! Windows systems are at risk as threat actors spread malware via leaked passwords. Find more details: https://eu1.hubs.ly/H03lYWm0
- A threat actor’s selling a $30 stealer malware targeting your gallery. It snatches ALL photos & sends them via Telegram. Keep devices updated, use trusted sources for apps, and avoid sketchy links!
- Sophos EDR & Checkpoint Harmony EDR security software found for sale on the deep web! In nature, these products are used for malware detection. Threat actors may use them to test & evade the detection of their own malware.
🚨 Fortinet VPN users, beware! Threat actors are on the prowl, and we’ve recently discovered that some are selling tools to exploit the CVE-2022-40684 vulnerability. it’s time to take action and protect your organization. #FortinetVPN #CyberSecurity #ThreatActors #CVE-2022-40684 pic.twitter.com/pnPHEFOmOe
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) April 4, 2023
- In a Russian dark web forum, threat actors are targeting the China-based EPC company, Sinoma, which provides R&D, and engineering services. The hackers are demanding $10,000 for the RAT they used in the attack.
- A new MacOS secure-Websocket HVNC malicious tool was discovered on the dark web, using port 443 for authentication, which is concerning, ’cause this port is typically open by default!
Anonymous Sudan Does Not Stop!
Anonymous Sudan does not stop. The Group is attacking #airway companies in Israel 🇮🇱 now. Be careful, and stay safe💻! These attacks seem to continue.#CybersecurityAwareness #AnonymousSudan #DigitalSecurity #ISRAEL #cyebrsecurity #darkweb pic.twitter.com/I7ok10GKNU
— BRANDEFENSE | Digital Risk Protection Service (@Brandefense) April 7, 2023
Get more insight from the darkweb, follow us on Twitter and Subscribe to our Ransomware Newsletter!






