The fixing of this vulnerability by 7-Zip and Microsoft has led threat actors to look for another file format to use in attacks, and as a result, they started using the Microsoft OneNote file format. The campaign chain begins with threat actors creating a OneNote document that includes a design element with a ‘Double Click’ message to view the content.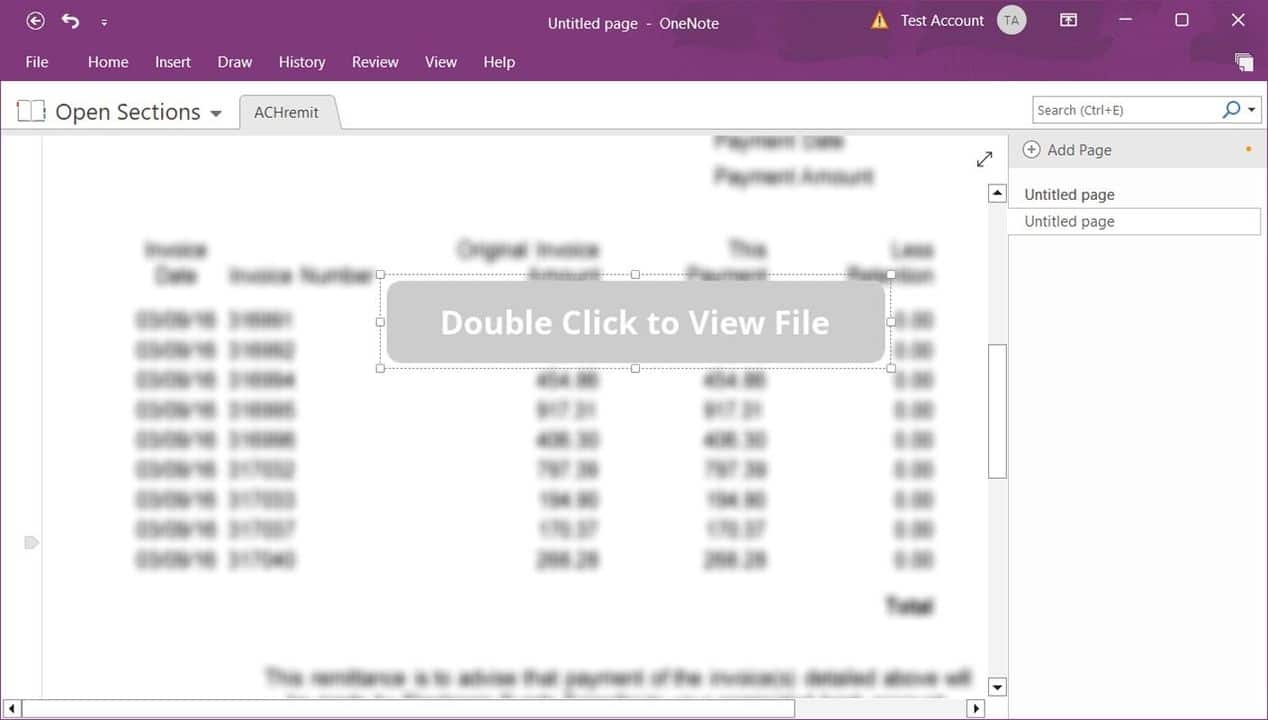
The Malware Campaign in Microsoft OneNote Is Running Various Ransomware
The file appears to be a protected document, as shown above, but contrary to what is visible, a malicious software file that will run when the user double-clicks is hidden under the “Double Click to View File” message. In observed campaigns, it was determined that the software running in the background dropped various Ransomware malware, such as BlackBasta, onto the targeted system.
To avoid being targeted by campaigns using the aforementioned malicious OneNote attachments on Windows systems, it is recommended to:
- Block the ‘.one’ file extension from secure mail gateways or mail servers,
- Use Microsoft Office group policies to restrict the execution of malicious file attachments in OneNote files,
- Use comprehensive security solutions, and
- Educate organization personnel on this and similar attack methods.






