In the e-mail content, the threat actors request the targets to open the Excel file containing recommendations on payment methods. The Excel file is password-protected to avoid detection, and the password is included in the text of the e-mail sent to the destinations.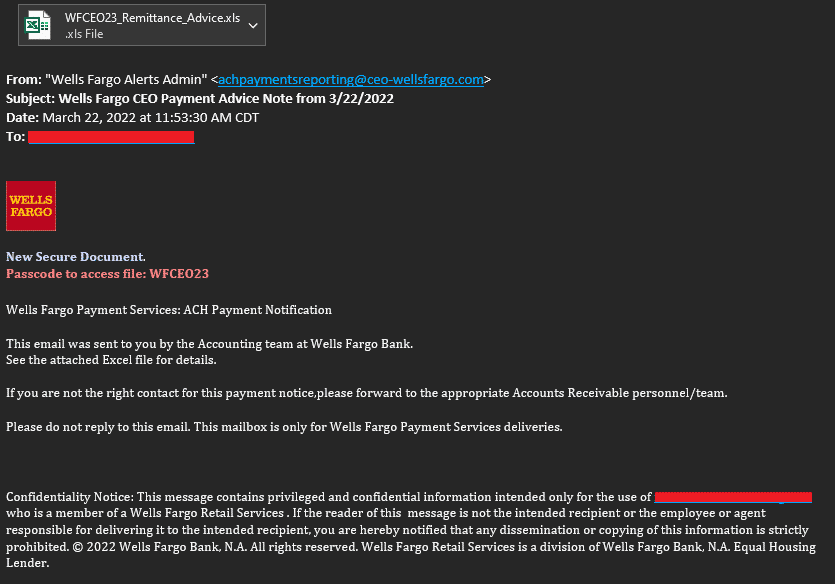 The Excel file contains Visual Basic code that runs when a user opens the file and enables macros. The Visual Basic code in question executes a PowerShell command that downloads another .vbs file from a remote server. Then the newly downloaded and executed .vbs file connects back to the C2 server and fetches a hardcoded PowerShell code. This PowerShell code is responsible for downloading and decoding the next phase. In the final stage, Remcos RAT is injected into the target system.
The Excel file contains Visual Basic code that runs when a user opens the file and enables macros. The Visual Basic code in question executes a PowerShell command that downloads another .vbs file from a remote server. Then the newly downloaded and executed .vbs file connects back to the C2 server and fetches a hardcoded PowerShell code. This PowerShell code is responsible for downloading and decoding the next phase. In the final stage, Remcos RAT is injected into the target system.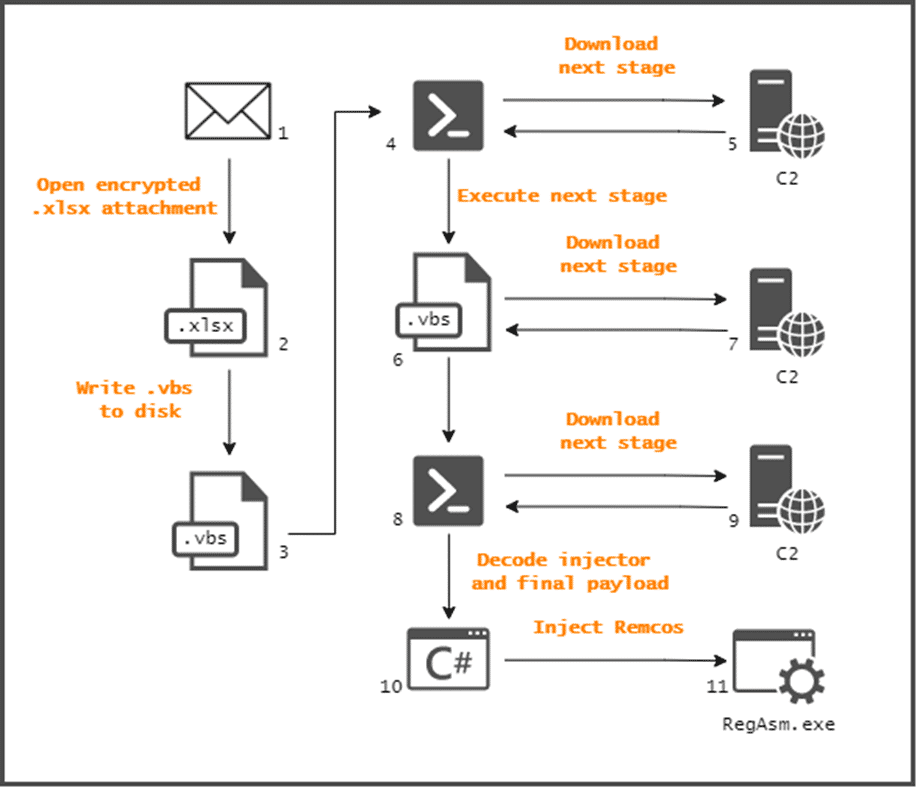
In this context, in order not to be the target of similar malware campaigns, it is recommended to disregard e-mail attachments and links from unknown parties, download files/programs from reliable sources, raise awareness of institution/organization personnel about possible social engineering/phishing attacks, and use reliable security solutions. In addition, it is recommended that the IoC findings related to the campaign be blocked from the security solutions in use.






