The Linux encryptor is designed to focus on VMware ESXi servers and has command line parameters that allow threat actors to shut down running virtual machines before encrypting the file. The malware, which has been observed to use the NTRUEncrypt algorithm for encryption operations, only targets files associated with VMware ESXi servers, such as log files (.log), swap files (.vswp), virtual disks (.vmdk), and memory files (.vmem).
In the sample analyzed by security researchers, it was observed that the Ransomware software added the “.crypt658″ extension to the filenames of encrypted files. A ransom note named HOW_TO_RESTORE, which is observed to be added to each folder by the ransomware, contains a description of the data compromised and a Tor link that directs victims to the ransom payment site. The payment page on the Tor network is similar to other Ransomware operation pages where a ransom demand is shown, and options are offered to negotiate with threat actors. RedAlert/N13V threat actors only accept Monero cryptocurrency for ransom payment.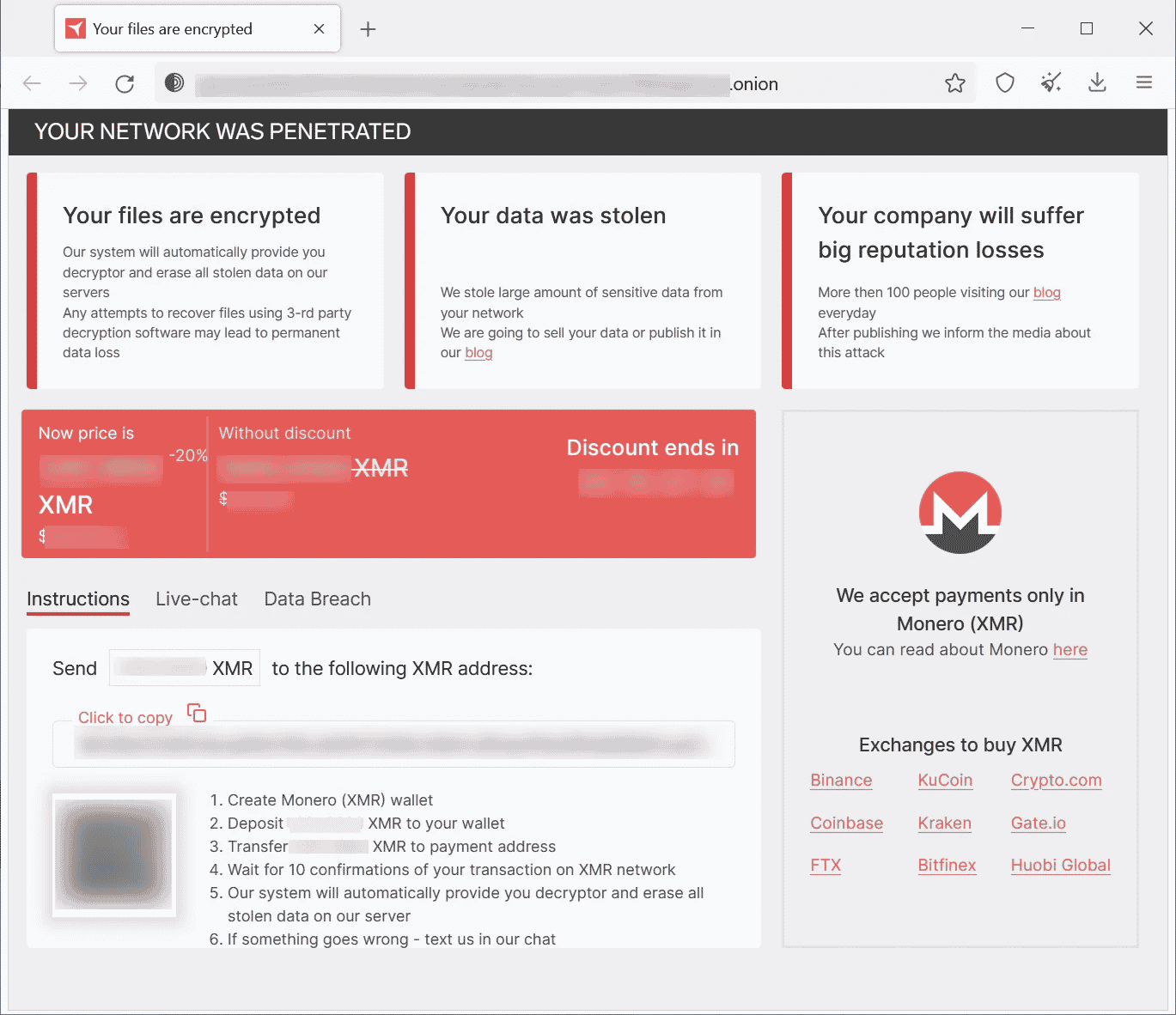 A leak site called “Board of Shame” has been created by RedAlert threat actors to leak data of compromised institutions/organizations and to announce breaches. The last post shared by the threat actors on the leak site stated that a corporate firm providing cloud computing services was targeted. In the alleged breach, it was announced that more than 300 GB of data, including social security numbers, driver’s licenses, financial documents, payrolls, and bank statements of the company personnel, was seized.
A leak site called “Board of Shame” has been created by RedAlert threat actors to leak data of compromised institutions/organizations and to announce breaches. The last post shared by the threat actors on the leak site stated that a corporate firm providing cloud computing services was targeted. In the alleged breach, it was announced that more than 300 GB of data, including social security numbers, driver’s licenses, financial documents, payrolls, and bank statements of the company personnel, was seized. In order not to be the target of similar ransomware attacks that may be carried out in this context, it is recommended to take the following actions;
In order not to be the target of similar ransomware attacks that may be carried out in this context, it is recommended to take the following actions;
- Beware of unreliable e-mail contents,
- Suspicious e-mail attachments and links should not be respected,
- Using reliable Anti-Malware solutions,
- Using licensed and up-to-date technologies,
- Used security solutions should block shared IOC findings regarding the malware campaign.






