DirtyCred – A Critical Linux Kernel Security Vulnerability
A new Linux Kernel vulnerability called “DirtyCred” was disclosed at the Black Hat security conference on August 10, 2022. The vulnerability, which is similar to the notorious DirtyPipe vulnerability and is tracked as CVE-2022-0847, was discovered by Ph.D. and detected by student Zhenpeng Lin and his team.
DirtyCred is a kernel exploit that replaces non-privileged kernel credentials with privileged ones to escalate privileges on vulnerable systems. Instead of overwriting any critical data area in the kernel stack, DirtyCred abuses the stack memory reuse mechanism to gain privileges. It can overwrite all files with reading permission that affects kernel version 5.8 or higher. The vulnerability allows a local threat actor to crash the system or execute arbitrary code on the vulnerable system.
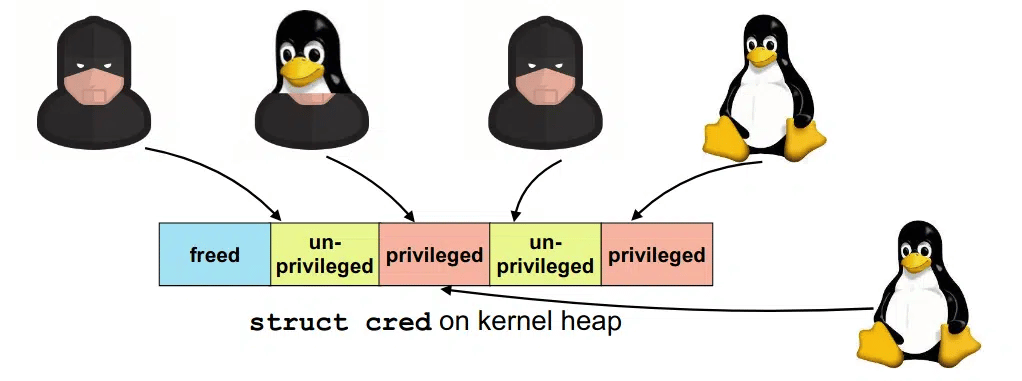
This Thursday @BlackHatEvents , I will be presenting our research on a kernel exploitation method named #DirtyCred. With DirtyCred, you could write an #DirtyPipe liked exploit that works on different kernels and ARCHs without code changes. Check it out https://t.co/Qip23PSHl7 pic.twitter.com/jdopannoBO
— Zhenpeng Lin (@Markak_) August 7, 2022
A Phishing Campaign Targeting Hotels and Travel Companies Detected
A phishing campaign targeting multiple hotels and travel companies has been detected running by the TA558 group. In the campaign, it was observed that RAT malware was exploited, allowing threat actors to access targeted systems, monitor the system regularly, capture critical data and carry out fraudulent activities with the captured data. In addition, it is seen that RAR and ISO file attachments have started to be used in this campaign instead of macro-content documents sent by phishing e-mails.
The chain of infection starts with the sending of phishing e-mails with message text in English, Spanish and Portuguese to the associated destinations. The main topic covered in the e-mails is to make a reservation at the targeted establishment. Such e-mails are sent purporting to come from key sources such as conference organizers and tourist office agents that are hard for recipients to ignore.
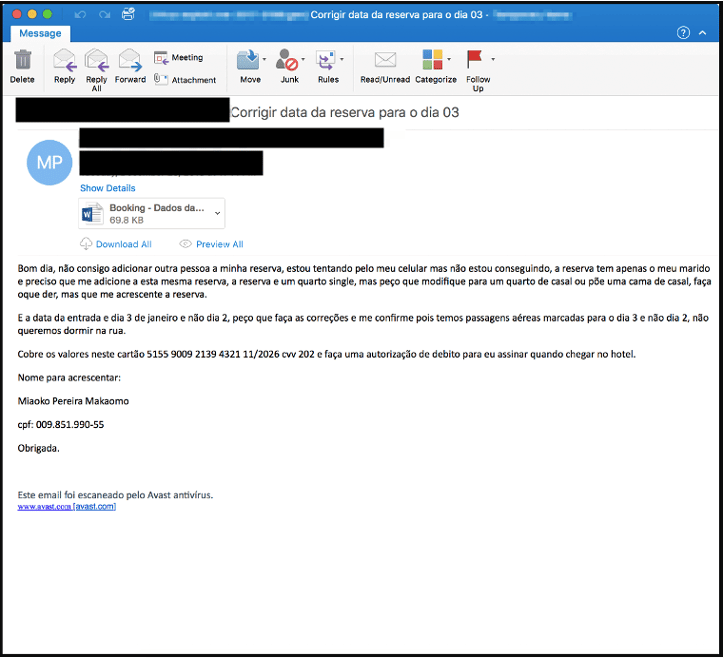
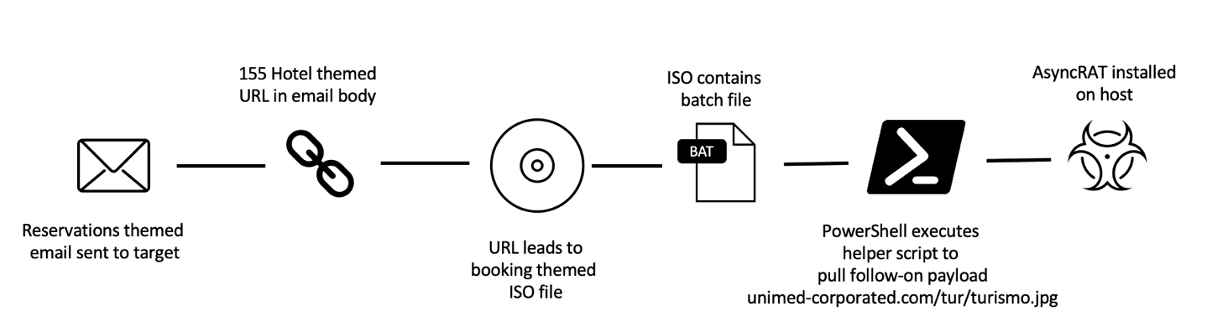
TA558 has been an active threat actor targeting the hospitality, travel, and related industries since 2018. The activities carried out by this actor lead to the capture of corporate and customer data and possible financial losses. For example, in July 2022, the Booking.com account of The Marino Boutique Hotel in Lisbon, Portugal, was targeted by this hacking campaign. It is known that threat actors caused a financial loss of € 500,000 through a compromised hotel account in just four days. In this context, it is recommended to consider the following security practices to avoid being the target of similar attack campaigns.
- E-mails, attachments, and links from unknown, suspicious parties should not be respected.
- File/Program or application downloads should be made from legitimate and reliable sources.
- Comprehensive Anti-Virus/Anti-Malware security solutions should be used.
- Institution/organization personnel should be made aware of potential phishing/social engineering attacks.
- IOC findings related to the campaign should be blocked from security solutions.
Zoom Releases Updates Fixing A Critical Vulnerability Affecting macOS
Zoom has released security updates that fix a vulnerability in the macOS operating system that could allow a threat actor to take control of a user’s system. (Reference Link)
The security vulnerability with code CVE-2022-28756 affects the automatic update feature of the application. A low-privileged threat actor can exploit the vulnerability to gain root privileges on the vulnerable operating system during the automatic update process of versions 5.7.3 to 5.11.3. The vulnerability was identified by Patrick Wardle, founder of the Objective-See Foundation, and presented at the annual world-known Def Con Hack conference.
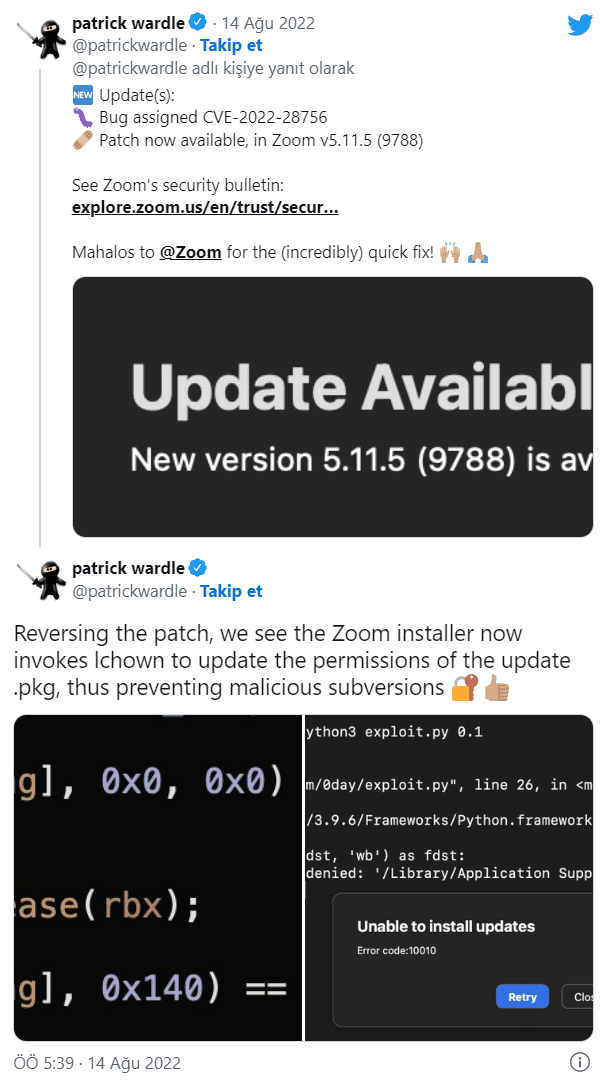
The vulnerability has been fixed in version 5.11.5 of the currently available Zoom app for macOS.
It is recommended that users using vulnerable versions of the Zoom App for macOS immediately apply the updates that fix the vulnerability so that they are not the target of attacks that can be carried out using the vulnerability.






