Critical RCE Vulnerabilities Affecting F5 Products Detected
Application service provider F5 has issued a security notice for two critical security vulnerabilities that allow an unauthenticated threat actor with network access to remote code execution in BIG-IP systems, a combination of software and hardware designed around access control, application availability, and security solutions.
In the statement made by F5, it was stated that the security vulnerabilities detected were found in the representative state transfer (REST) interface for the iControl framework used to communicate between F5 devices and users.
The identified security vulnerabilities are:
The vulnerability, code CVE-2022-41622, is caused by cross-site request forgery (CSRF) that affects BIG-IP and BIG-IQ products, allowing threat actors to gain root access to a device’s management interface.
The vulnerability code CVE-2022-41800 allows a threat actor with administrative privileges to execute code remotely on vulnerable systems via an RPM file.
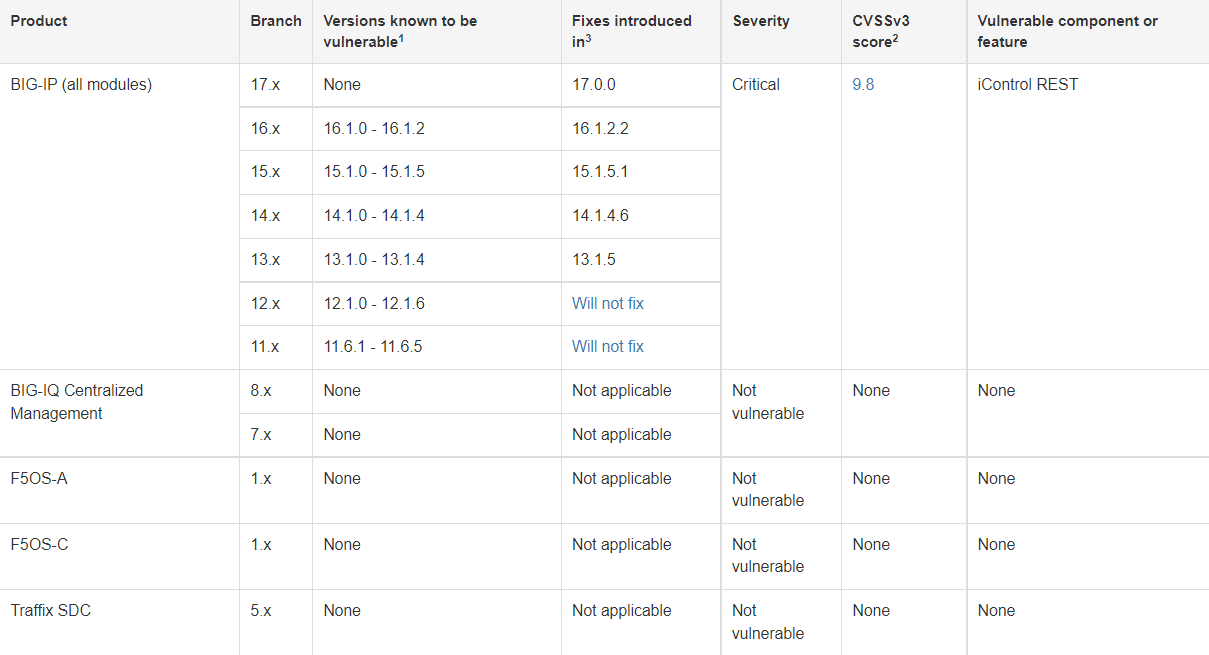
BIG-IP product versions affected by these security vulnerabilities are as follows;
- 1.0 – 16.1.2
- 1.0 – 15.1.5
- 1.0 – 14.1.4
- 1.0 – 13.1.4
- 1.0 – 12.1.6
- 6.1 – 11.6.5
Reflected XSS Alarm in ProfileGrid WordPress Plugin
A security vulnerability has been detected, allowing threat actors to perform Reflected XSS attacks in the ProfileGrid WordPress plugin, which offers features such as creating and managing user groups on WordPress websites. A Reflected XSS attack is carried out by injecting malicious scripts directly into an HTTP request by threat actors and executing them in the target user’s browser.
The vulnerability, tracked as CVE-2022-3578, is caused by the ProfileGrid WordPress plugin insufficiently clearing parameters sent to the page in versions before 5.1.1. As a result, a remote threat actor can direct users to open a malicious link, and they can execute arbitrary HTML code and script in the user’s browser in the context of the vulnerable website.
In order not to be the target of attacks that can be carried out using the security vulnerability in question, it is recommended to immediately upgrade the vulnerable ProfileGrid versions to the current versions (5.1.1) that fix the vulnerability.
Multiple Vulnerabilities Detected in IT Management Solution GLPI
Multiple security vulnerabilities have been identified in GLPI, an open-source web application that helps institutions/organizations and companies manage their IT infrastructure and inventories. These vulnerabilities allow threat actors to execute SQL queries against the application database and to perform Cross-Site Scripting (XSS) and Server-Side Request Forgery (SSRF) attacks.
The details of the detected security vulnerabilities are as follows;
- The security vulnerability tracked as CVE-2022-39375 is due to insufficient cleaning of user-supplied entries in the RSS Feed function. A remote threat actor can execute arbitrary HTML code and script in the user’s browser in the context of the vulnerable website via a malicious link. Successful exploitation of this vulnerability allows remote threat actors to obtain sensitive information, alter the web page’s appearance, and carry out phishing attacks.
- The security vulnerability tracked as CVE-2022-39234 is due to insufficient session expiry time. This vulnerability allows threat actors to access users’ accounts by reusing users’ old session credentials (Cookies) and thus may lead to the capture of users’ sensitive information.
- The security vulnerability tracked as CVE-2022-39323 is due to insufficient sanitization of user-supplied data in the API REST user_token component. A remote threat actor can execute arbitrary SQL commands in the application database by sending a specially crafted request to the affected application.
- The security vulnerability, tracked as CVE-2022-39276, is due to insufficient validation of user-supplied inputs in RSS feeds. A remote threat actor can direct the application to initiate requests to arbitrary systems (SSRF) via a specially crafted HTTP request.
- The vulnerability security, tracked as CVE-2022-39277, is due to insufficient sanitization of user-supplied data on external connections. A remote threat actor can run arbitrary HTML code and script in the user’s browser in the context of the vulnerable website via a specially crafted link.
These vulnerabilities affect specific versions of GLPI, and security updates have been released that fix the vulnerabilities. In this context, it is recommended to immediately upgrade vulnerable installations to the current versions published in order not to be the target of attacks that can be carried out using vulnerabilities.






