Introduction
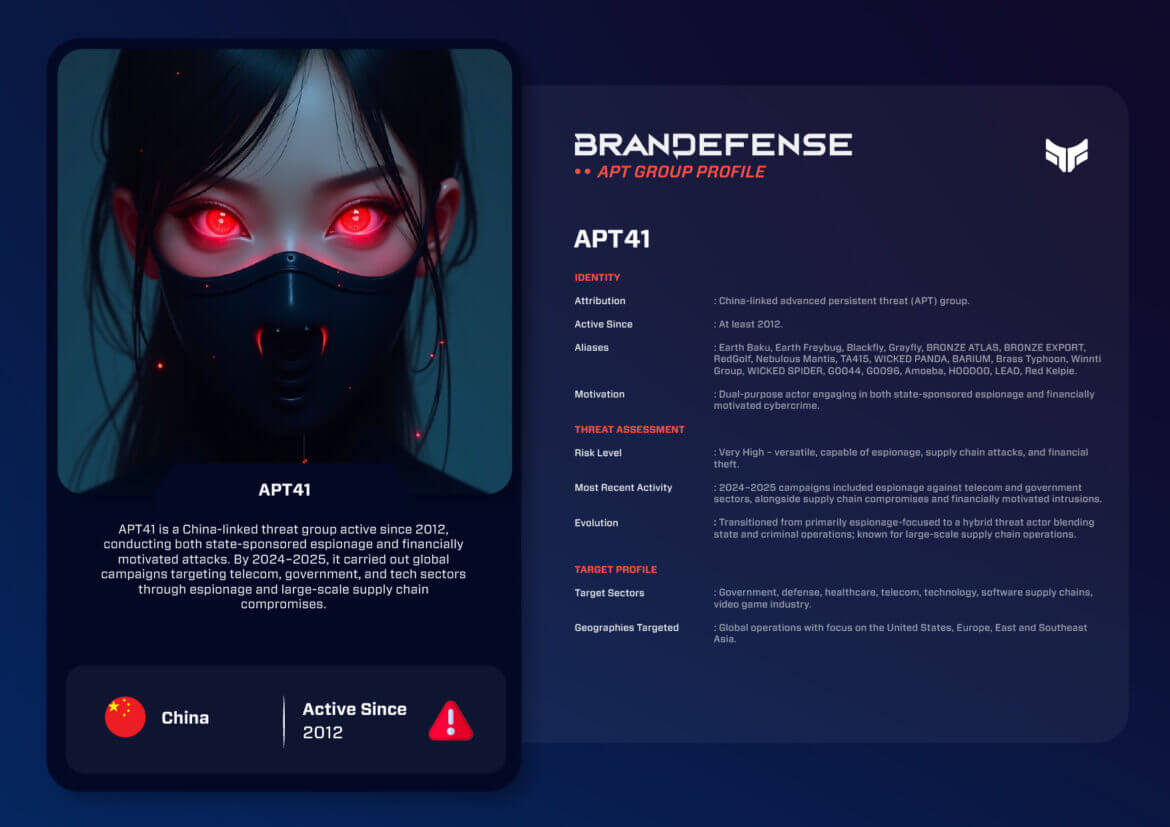
APT41, also operated under names like Earth Baku, Blackfly, Grayfly, RedGolf, Winnti Group, Wicked Panda, and Brass Typhoon, is among the most flexible and menacing advanced persistent threats (ATPs) associated with the Chinese threat actor landscape. Active at least since 2012, APT41 is uniquely characterized by its capability for government-sponsored espionage, accompanied by operations oriented around financial cybercrime. The blending of state-sponsored political agenda, consequential altruism, and financially motivated cybercrime provides the peace of mind that APT41 is a global adversary.
This blog post will provide a short overview of APT41’s identity, approach, targets, operations, and the unfolding of APT41 into one of the most disruptive threat actors active on the cyber environment.
Identity and Motivation
Attribution: China-linked APT group
Active Since: At least 2012
Aliases: Earth Baku, Earth Freybug, Blackfly, Grayfly, BRONZE ATLAS, BRONZE EXPORT, RedGolf, Nebulous Mantis, TA415, WICKED PANDA, BARIUM, Brass Typhoon, Winnti Group, WICKED SPIDER, G0044, G0096, Amoeba, HOODOO, LEAD, Red Kelpie
Motivation: Due to duality state espionage (political, defense, telecom, healthcare) and cybercrime (gaming industry, financial theft)
At the core of APT41’s appearance is the group’s dual mandate, which allows it to both serve Beijing’s strategic interests and financially benefit the operators of the group. The actors behind APT41 have the distinction of stealing intellectual property, spying on governments, compromising critical infrastructure, and executing operations that would generate fiduciary gains all at the same time.
TTPs (Tactics, Techniques & Procedures)
Initial Access
- Malicious phishing emails with malware attachments
- Supply chain compromise (trojanized updates, vendor software)
- Exploiting vulnerabilities in Internet facing applications (Citrix, VPNs, web servers)
Persistence
- Web shells
- Scheduled tasks and registry changes
- Trojenized legitimate apps
Command & Control (C2)
- HTTP/S
- DNS tunneling
- Abuse of cloud services and dynamic DNS
Malware & Tools
- Winnti malware family: modular espionage backdoors
- ShadowPad: modular backdoor used globally from supply chain compromises
- PlugX RAT
- Crosswalk malware
- Credential dumpers, keyloggers, customized loaders
Techniques
- Living-off-the-land binaries (LOLbins)
- Scale for supply chain compromises
- Dual use approach: espionage and theft of financial gain
Target Profile
APT41 has a global footprint with a varied targeting profile.
- Government & Defense: Espionage, policy monitoring, and stealing intelligence.
- Telecom: Tracking communications and surveillance opportunities.
- Healthcare: Intellectual property and sensitive research (especially from COVID-19 response).
- Technology & Software Supply Chains: Compromises vendors to reach downstream victims.
- Video Game Industry: Steal intellectual property and virtual currency for profit.
Geographies Targeted: United States, Europe, East Asia, Southeast Asia, South Asia – truly global in scope.
Notable Operations (2012–2025)
Recent intelligence assessments emphasize a marked change in APT36’s activity patterns. Though India continues to be the main threat vector, the group has also added to its models and regional targeting.
2012–2015: Intellectual property and financial theft in the video game sector, targeting virtual currencies and digital assets.
2017–2019: Significant compromises in the supply chain, notably CCleaner and ShadowPad malware operations.
2020: The United States Department of Justice indicted APT41 members for a decade of cybercrime and espionage activities.
2021–2022: Exploited vulnerabilities in Citrix and VPN technologies, specifically targeting health care and telecom providers.
2023: Observed the RedGolf cluster targeting government and telecom throughout Asia and Europe.
2024–2025: Ongoing supply chain compromises, increased espionage against telecom and defense, and continued financially motivated operations.
Recent Developments (2024–2025)
APT41 appears adaptable in recent years:
- Supply Chain Attacks Intensified: Continuing to use vendor compromises to target thousands of downstream victims.
- Espionage Focus: Renewed activity in targeting telecoms and government networks across Asia, Europe, and the U.S.
- Financially Motivated Intrusions: Continued interest in the gaming industry and cryptocurrency thefts.
- Advanced Persistence: Use of ShadowPad and other modular backdoors for longer-term, stealthy breaches of cyber systems.
APT41’s recent activity shows their ability to balance state directed activities with independent financial gain.
Strategic Impact
The hybrid model used by APT41 has significant importance it undermines global security from numerous facets:
- National Security Risk: Espionage against government and defense organizations gives China an important strategic advantage.
- Economic Threat: The theft of intellectual property and financial assets threatens industries from gaming to healthcare.
- Supply Chain Vulnerability: Trojanized vendor (third-party) software updates exemplify systemic risks to global cybersecurity.
The APT41 hybrid model guarantees that the group will remain a high-risk and enduring adversary for the foreseeable future.
Defensive Takeaways
Organizations can reduce their risk of APT41 incidents:
- Supply Chain Security: Vet vendors and actively monitor for trojanized software updates.
- Vulnerability Management: Quickly patch any internet agencies (VPNs, Citrix, etc.; at risk for internet access visits).
- Threat Hunting: Detecting for Winnti, ShadowPad, PlugX and Crosswalk.
- Zero Trust Architecture: Limit opportunities for lateral movement within the environment.
- Incident Response Preparedness: Rapid containment and forensics on suspected compromises.
Conclusion
APT41, also referred to as Wicked Panda, RedGolf, Winnti Group, and Brass Typhoon, is recognized as one of the most sophisticated, disruptive, and persistent APTs currently known “. It operates with a hybrid mission of espionage and financial gain that allows it to simultaneously affect governments, critical infrastructure, and global businesses in the private sector.
APT41 continues to evolve as of 2025, continuing to perfect its supply chain compromises, while striking a balance between state-sponsored and criminal objectives. Defenders need to be aware — APT41 requires multi-layered, resilient security, robust supply chain security, and continual intelligence-based monitoring.
You can download and review the sheet for all the details!






